Fingerprint-based authentication method, fingerprint authentication-based first server and fingerprint authentication-based terminal
An authentication method and server technology, applied in the first server and terminal based on fingerprint authentication, in the field of authentication methods, can solve problems such as inability to log in, multiple user IDs and passwords that are easy to remember and mix
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
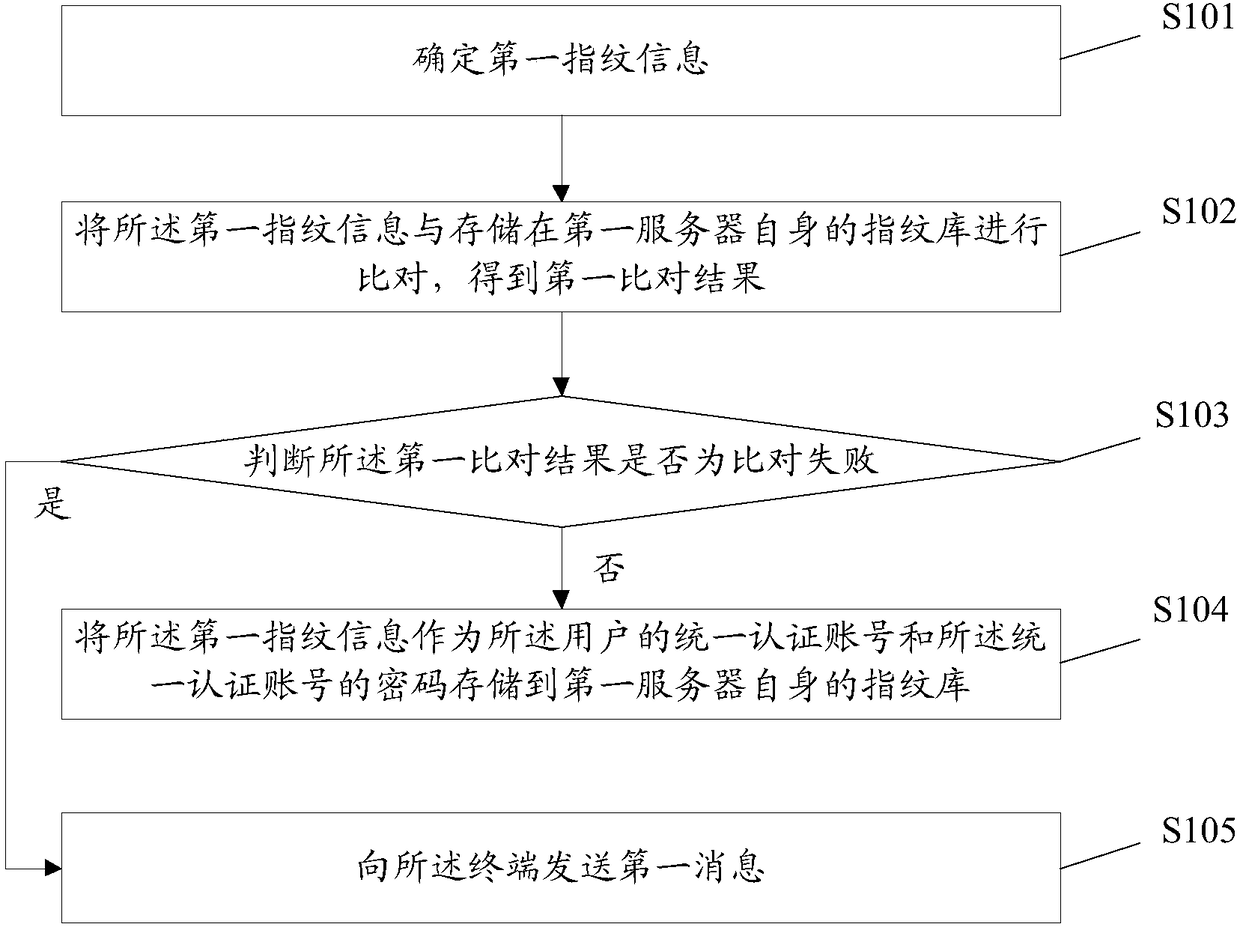
[0045] In order to solve the technical problems existing in the background technology, an embodiment of the present invention provides a fingerprint-based authentication method, which is applied to a fingerprint-based authentication system including at least a first server and a terminal based on fingerprint authentication, figure 1 It is a schematic diagram of the implementation flow of the fingerprint-based authentication method according to the embodiment of the present invention, as figure 1 As shown, the method includes:
[0046] Step S101, determining first fingerprint information;
[0047] Here, the terminal receives the first fingerprint input by the user through the fingerprint entry sensor; judges whether it has received an instruction to confirm the completion of the input sent by the terminal; the second fingerprint until receiving an instruction from the terminal to confirm the completion of the input; determine the first fingerprint information according to the ...
Embodiment 2
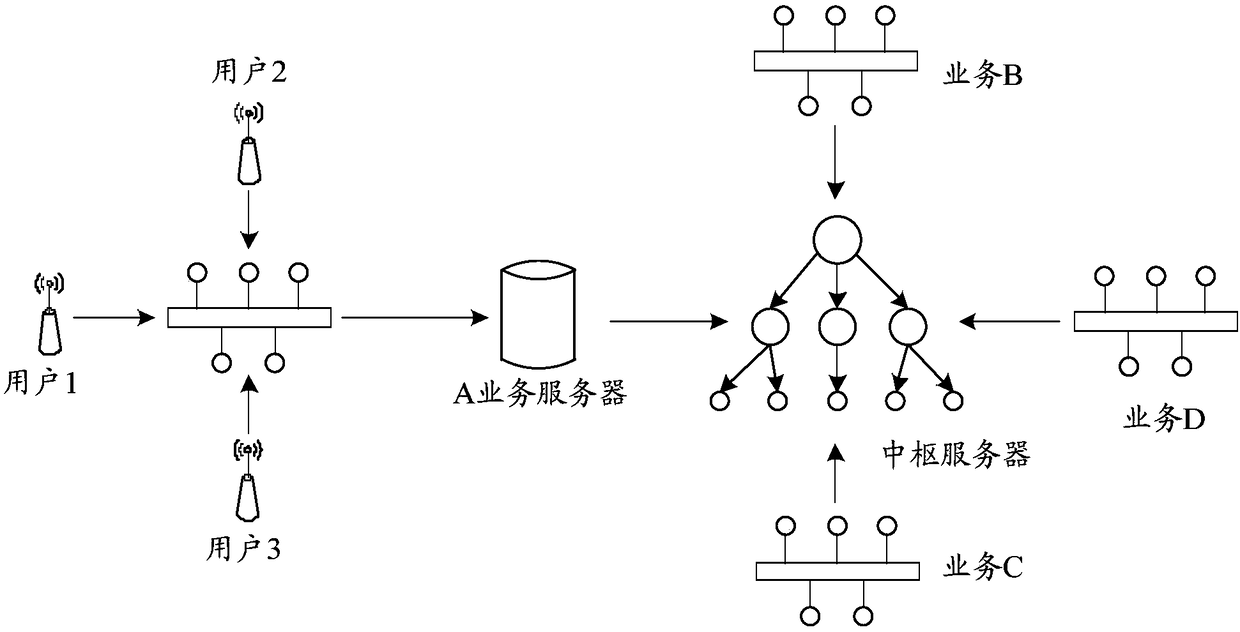
[0059] The embodiment of the present invention further provides a fingerprint-based authentication method, which is applied to a fingerprint-based authentication system, and the authentication system includes at least a first server, a second server, and a third server, and the method includes the following steps:
[0060] In the first step, the first server receives the first request sent by the second server;
[0061] Here, the first request is used to request to log in to the third server; in the embodiment of the present invention, the second server and the third server are business servers that have completed docking with the first server and established a connection. The first server is a hub server.
[0062] The user has completed the login process of unified authentication by using the first fingerprint information on the first client corresponding to the second server, and the user sends a first request to log in to the third server on the first client to the second s...
Embodiment 3
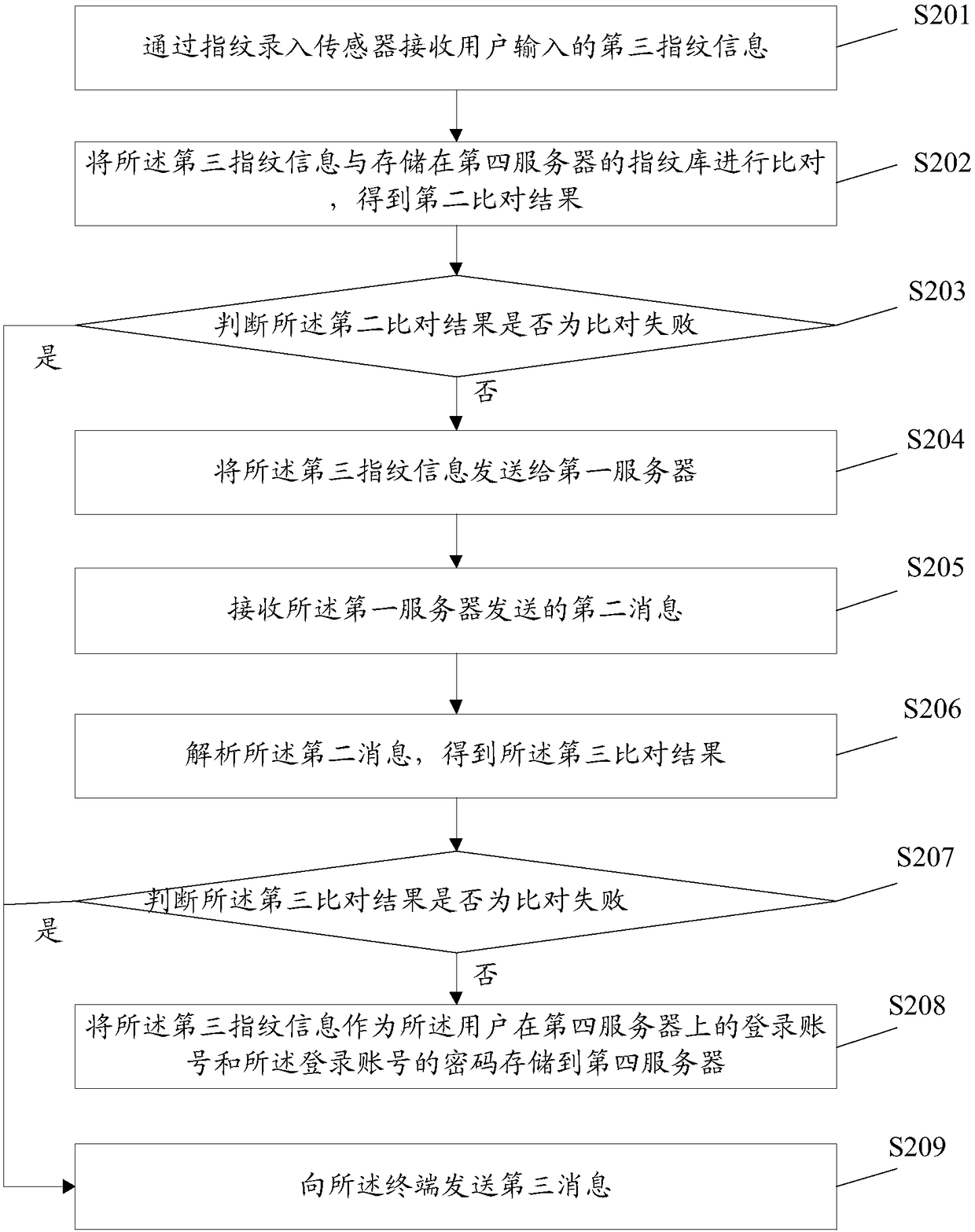
[0070] An embodiment of the present invention further provides a fingerprint-based authentication method applied to a fingerprint-based authentication system, wherein the system includes at least a first server and a fourth server, figure 2 It is a schematic diagram of the implementation flow of the fingerprint-based authentication method in Embodiment 3 of the present invention, as figure 2 As shown, the method includes:
[0071] Step S201, receiving the third fingerprint information input by the user through the fingerprint input sensor;
[0072] Step S202, comparing the third fingerprint information with the fingerprint library stored in the fourth server to obtain a second comparison result;
[0073] Here, the fourth server is a service server that has been docked with and established a connection with the first server.
[0074] Step S203, judging whether the second comparison result is a comparison failure;
[0075] Step S204, if the second comparison result is a com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com