Message distribution method and device based on multiple hashes
A shunting device and re-hashing technology, which is applied in the computer field, can solve problems such as conflicts and long time-consuming shunting and filtering, and achieve the effects of improving construction efficiency, submitting shunting efficiency, and improving shunting efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
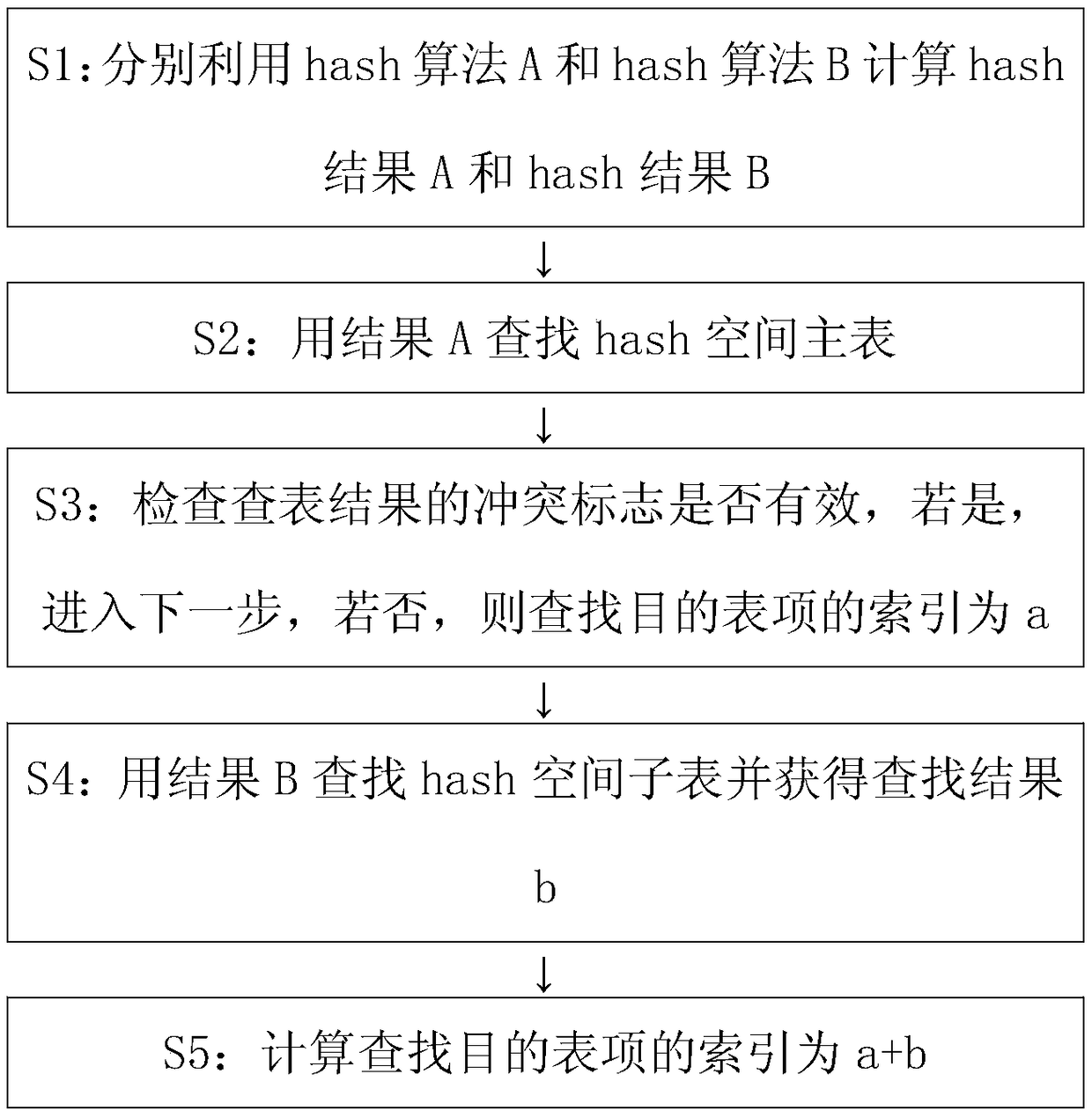
[0041] like figure 1 As shown, Embodiment 1 of the present invention provides a method for distributing packets based on multiple hashing, and the method includes the following steps:
[0042] S1: For the values in the table to be looked up, use hash algorithm A and hash algorithm B with orthogonal relationship to calculate respectively, and obtain hash results a and b respectively.
[0043] S2: Use the hash result a as an index to search the main table of the hash space.
[0044] S3: Check whether the conflict flag of the table lookup result is valid. If the conflict flag bit of the table lookup result is valid, it means a conflict occurs, and go to the next step. If the conflict flag of the main table lookup result indicates that no conflict occurs, it is used to look up the target table item The index is a.
[0045] S4: Use the hash result b as an index to search the hash space sub-table, and the search result is b.
[0046] S5: Calculate the final destination entry in...
Embodiment 2
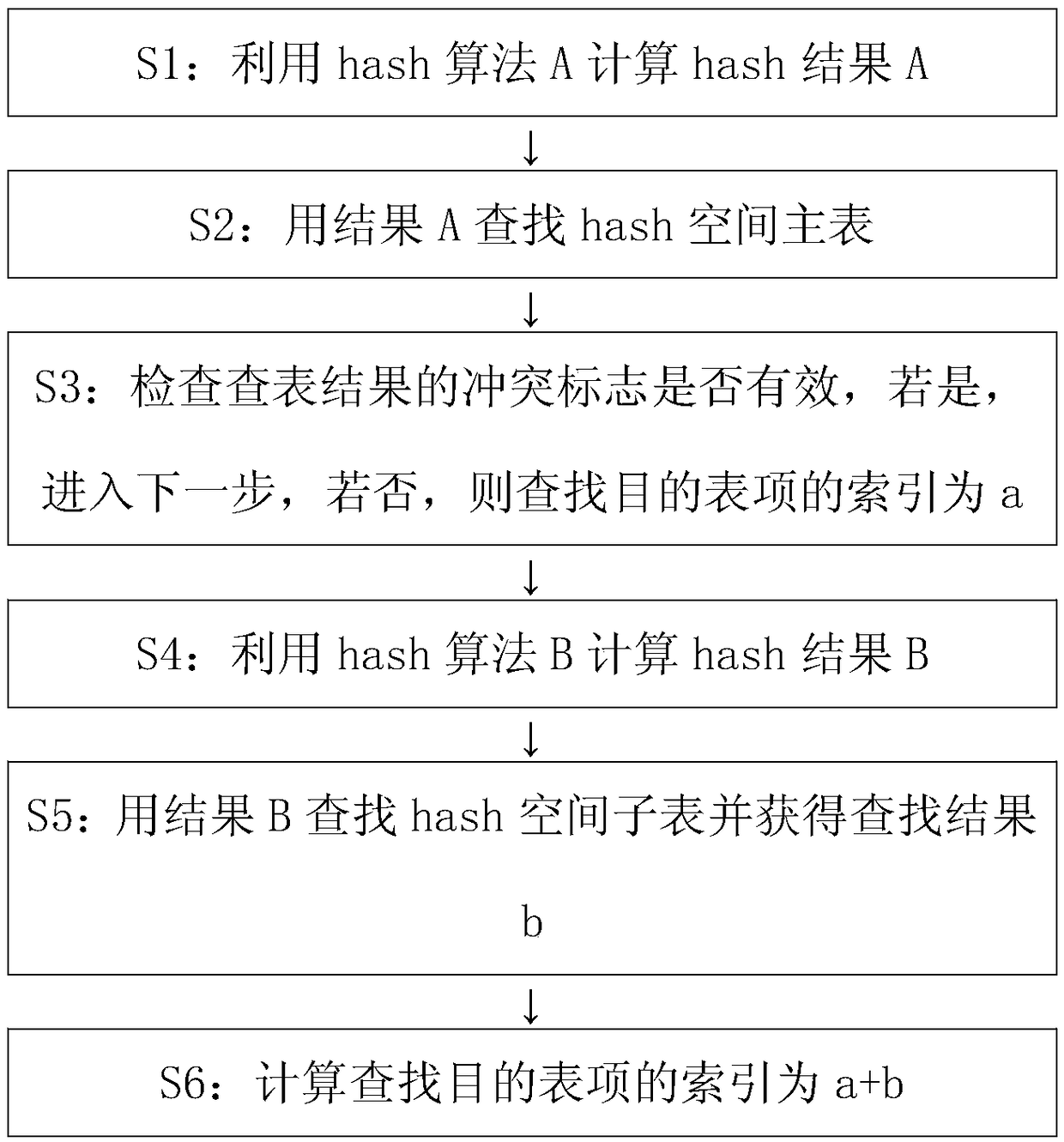
[0055] like image 3 As shown, Embodiment 1 of the present invention provides a method for distributing packets based on multiple hashing, and the method includes the following steps:
[0056] S1: For the value of the table to be looked up, use the hash algorithm A to calculate, and get the hash result a.
[0057] S2: Use the hash result a as an index to search the main table of the hash space.
[0058] S3: Check whether the conflict flag of the table lookup result is valid. If the conflict flag bit of the table lookup result is valid, it means a conflict occurs, and go to the next step. If the conflict flag of the main table lookup result indicates that no conflict occurs, it is used to look up the target table item The index is a.
[0059] S4: For the value of the table to be looked up, use the hash algorithm B which has an orthogonal relationship with the hash algorithm A to calculate, and obtain the hash result b.
[0060] S5: Use the hash result b as an index to search t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com