Document leak protecting and tracking system
A tracking system and document technology, applied in the field of document leakage protection tracking system, can solve the problems of not being able to identify the document transmission mode, not being able to recognize the operation behavior, not being able to recognize the leakage of sensitive files to the Internet, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
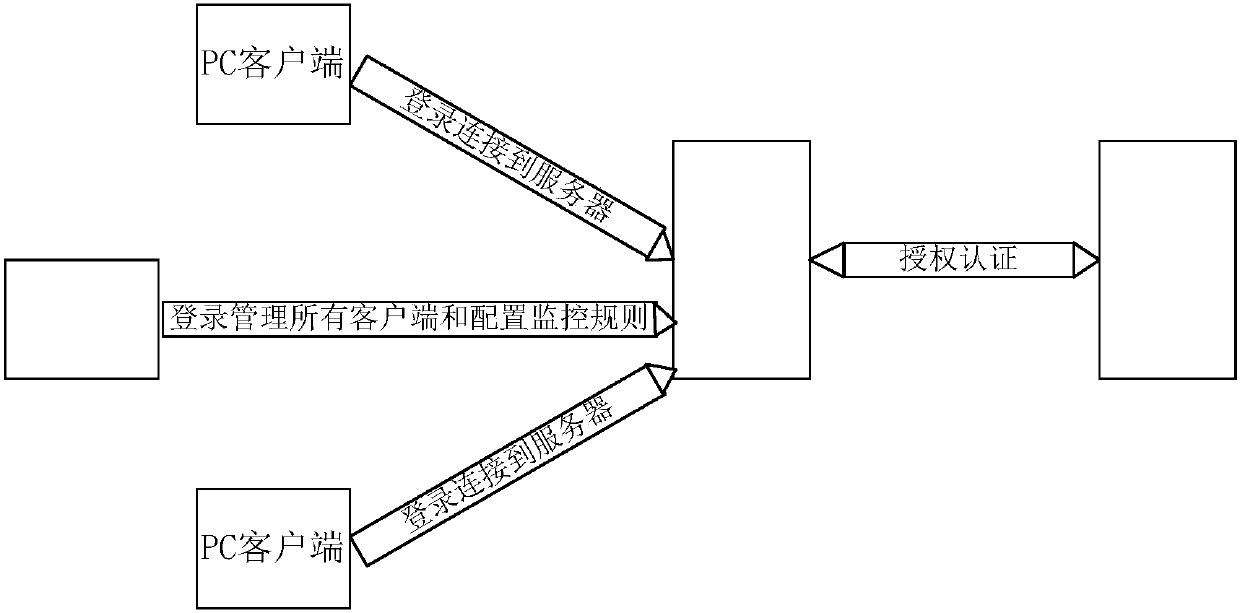
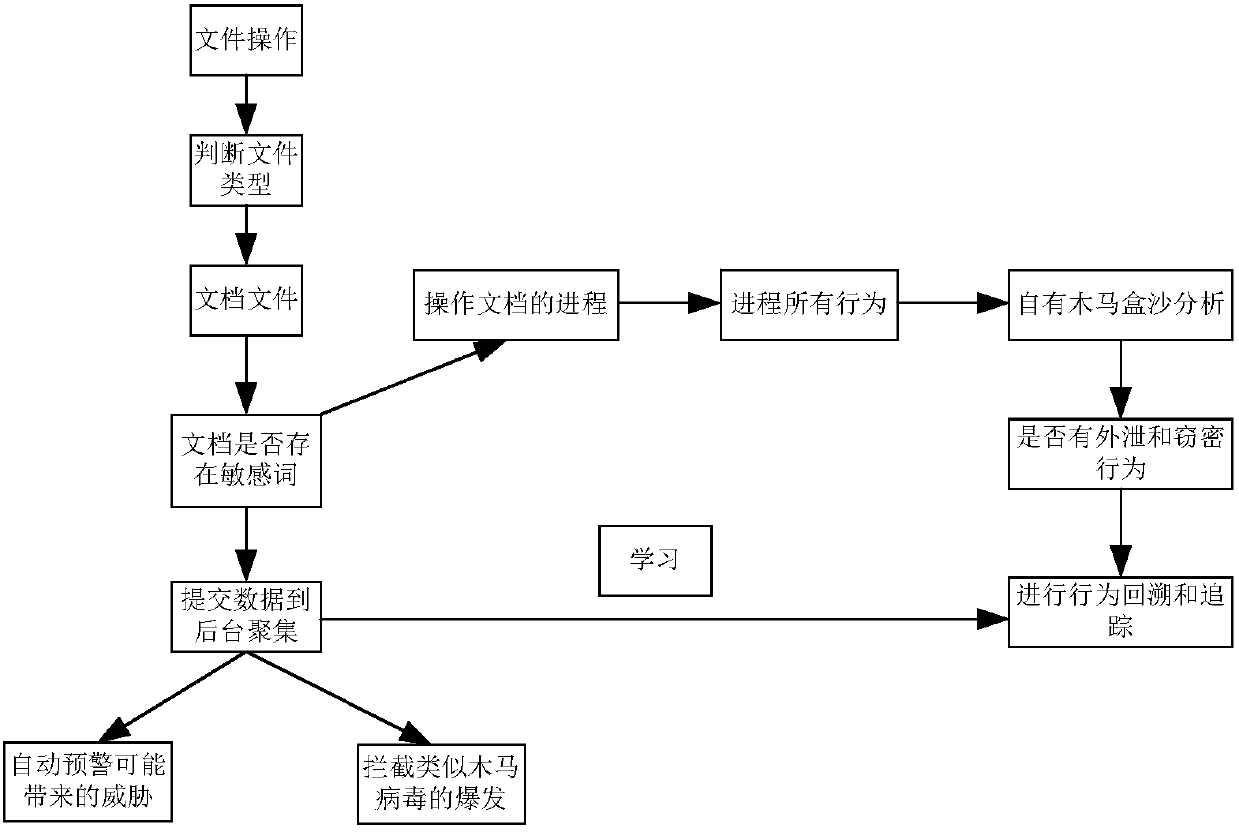
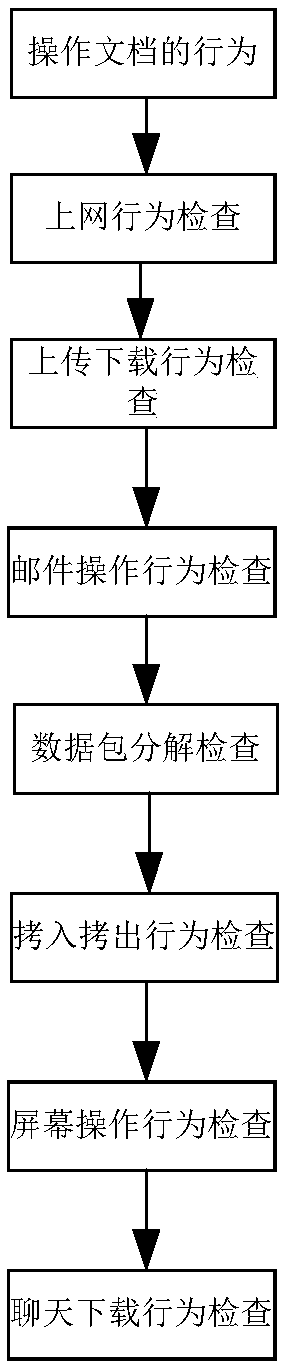
[0026] The present invention provides a document leakage protection and tracking system, which solves the shortcomings of the prior art on whether a document has been stolen or leaked, and can trace the leaked and stolen sensitive files of computers within the deployment range, and identify leaks Ways and ways of stealing, tracking to the leaking source computer, blocking and early warning of explosive Trojan horses and document-stealing programs.
[0027] In order to understand the above-mentioned purpose, features and advantages of the present invention more clearly, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. It should be noted that, under the condition of not conflicting with each other, the embodiments of the present application and the features in the embodiments can be combined with each other.
[0028] In the following description, many specific details are set forth in order to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com