A confidential coordinate transmission method, system and system usage method
A transmission method and coordinate technology, applied in the transmission system, electrical components, etc., can solve the problems of increasing fixed constants, damage, slow transmission speed, etc., and achieve the effect of saving time and cost and improving real-time performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0074] Embodiment 1, a confidential coordinate transmission method, including:
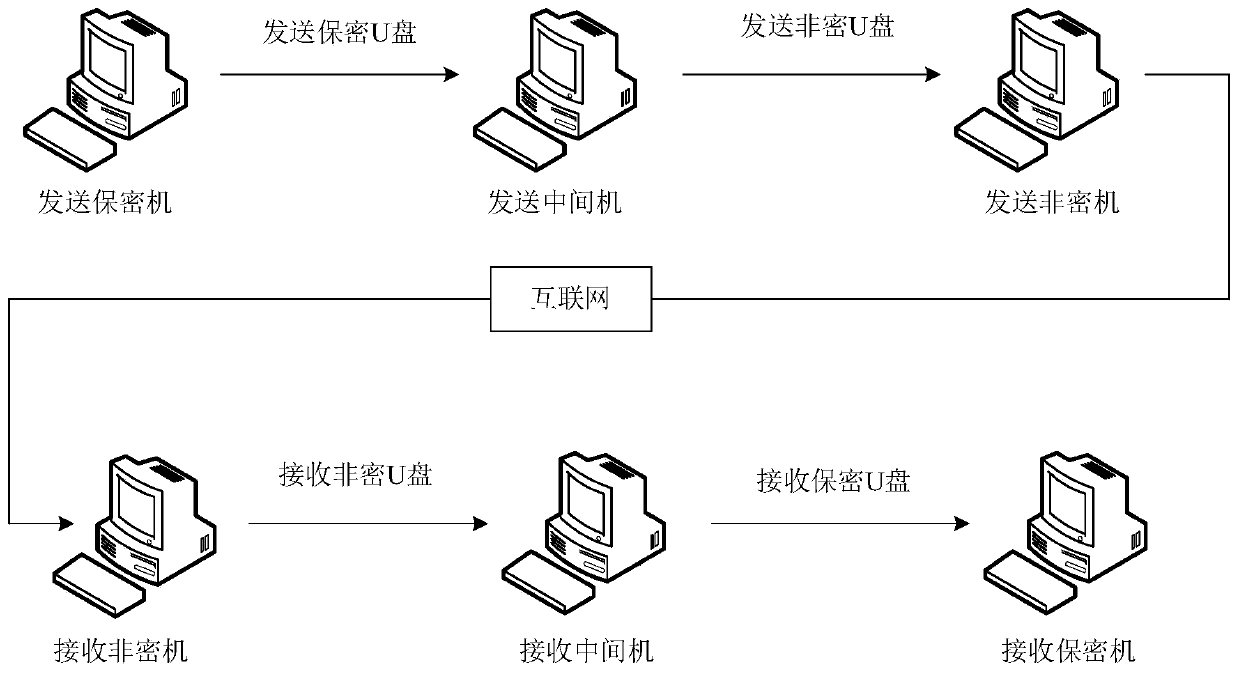
[0075] Step 1: Store the confidential coordinates of the pipeline facilities collected on-site and the result table of surveying and mapping control points in the transmitting security machine, which are respectively recorded as the first data and the second data, and the transmitting security machine calculates the first data and the second data as having relative The non-confidential data of the relationship is recorded as the third data, and the third data is transmitted to the sending intermediate machine by sending the confidential U disk;
[0076] Step 2, receiving and sending the third data transmitted by the confidential U disk in the middle of sending, and transferring the third data to the sending non-confidential U disk;
[0077] Step 3, the sending non-confidential computer receives and sends the third data transmitted by the non-confidential U disk, and sends the third data to the Int...
Embodiment 2
[0112] Example 2, such as figure 1 As shown, a confidential coordinate transmission system includes:
[0113] Sending security machine, which is used to store the confidential coordinates of the pipeline facilities collected on site and the result table of surveying and mapping control points, which are respectively recorded as the first data and the second data, and the first data and the second data are calculated as non- The encrypted data is recorded as the third data, and the third data is delivered to the sending intermediate machine by sending the confidential U disk;
[0114] Sending intermediate machine, it is used for receiving and sending the 3rd data that transmits confidential U disk, and the 3rd data is sent to send non-secret U disk;
[0115] Sending non-confidential machine, which is used to receive and send the third data transmitted by the non-secret U disk, and send the third data to the Internet;
[0116] A receiving non-confidential machine, which is use...
Embodiment 3
[0125] Embodiment 3, a method for using a secure coordinate transmission system, comprising:
[0126] Step S1, compiling the control point file, which is the second data;
[0127] Step S2, bringing the control point file to the construction site;
[0128] Step S3, taking the control point file to other office locations that need to receive confidential coordinates;
[0129] Step S4, collect the confidential coordinate points of the pipeline facilities at the construction site, and compile the collection point file, which is the first data;
[0130] Step S5, storing the second data and the first data in the sending security machine;
[0131] Step S6, calculating the relational data file in the sending security machine, which is the third data;
[0132] Step S7, the third data is connected to the sending intermediate machine through the sending confidential U disk;
[0133] Step S8, disinfecting the sending confidential U disk and the sending non-confidential U disk on the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com