Method for auditing cloud access in real time
An access method and cloud technology, applied in encryption devices with shift registers/memory, instruments, digital transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to describe the technical content, structural features, achieved goals and effects of the present invention in detail, the following examples are given and described in detail with reference to the drawings.
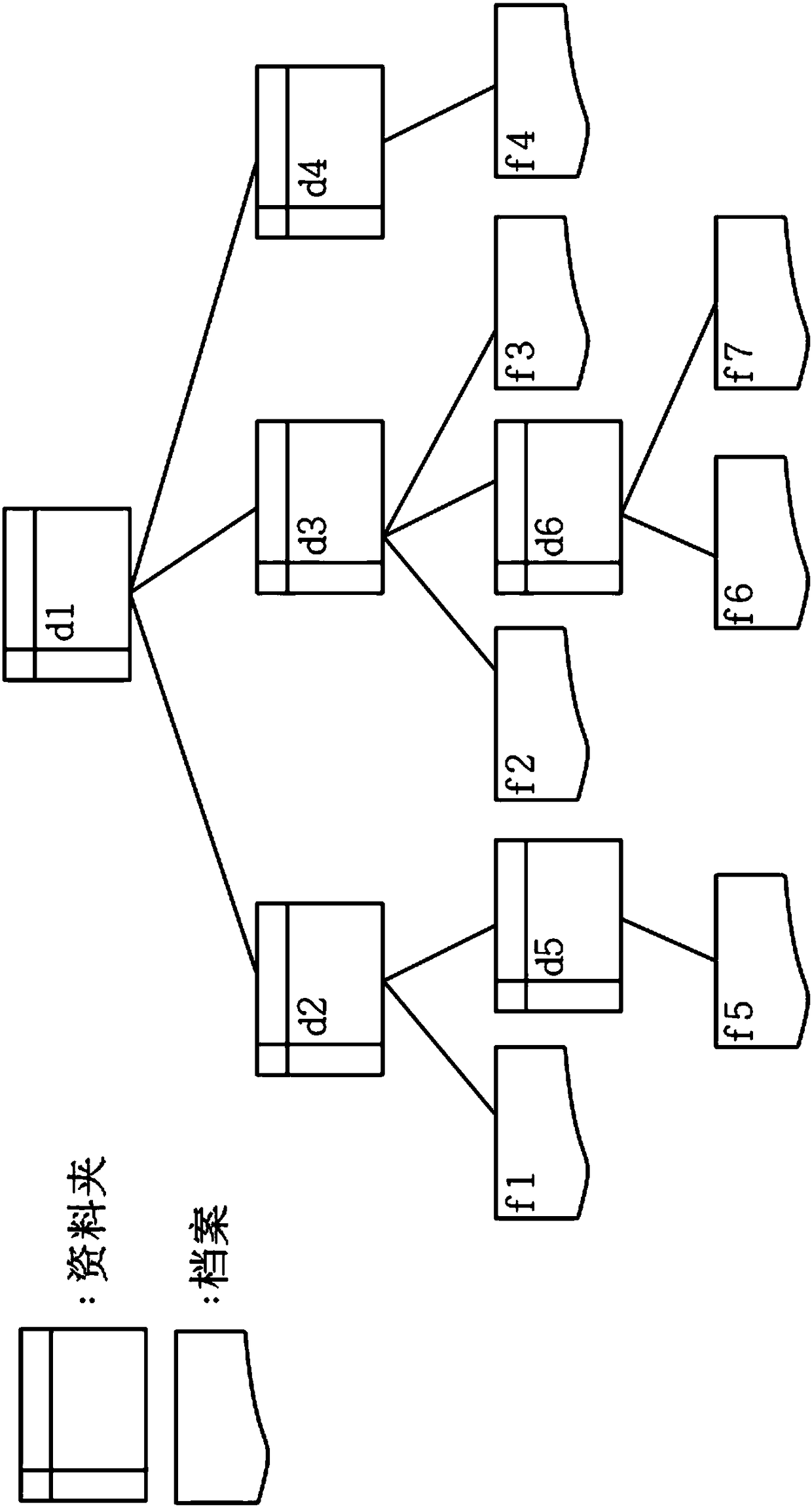
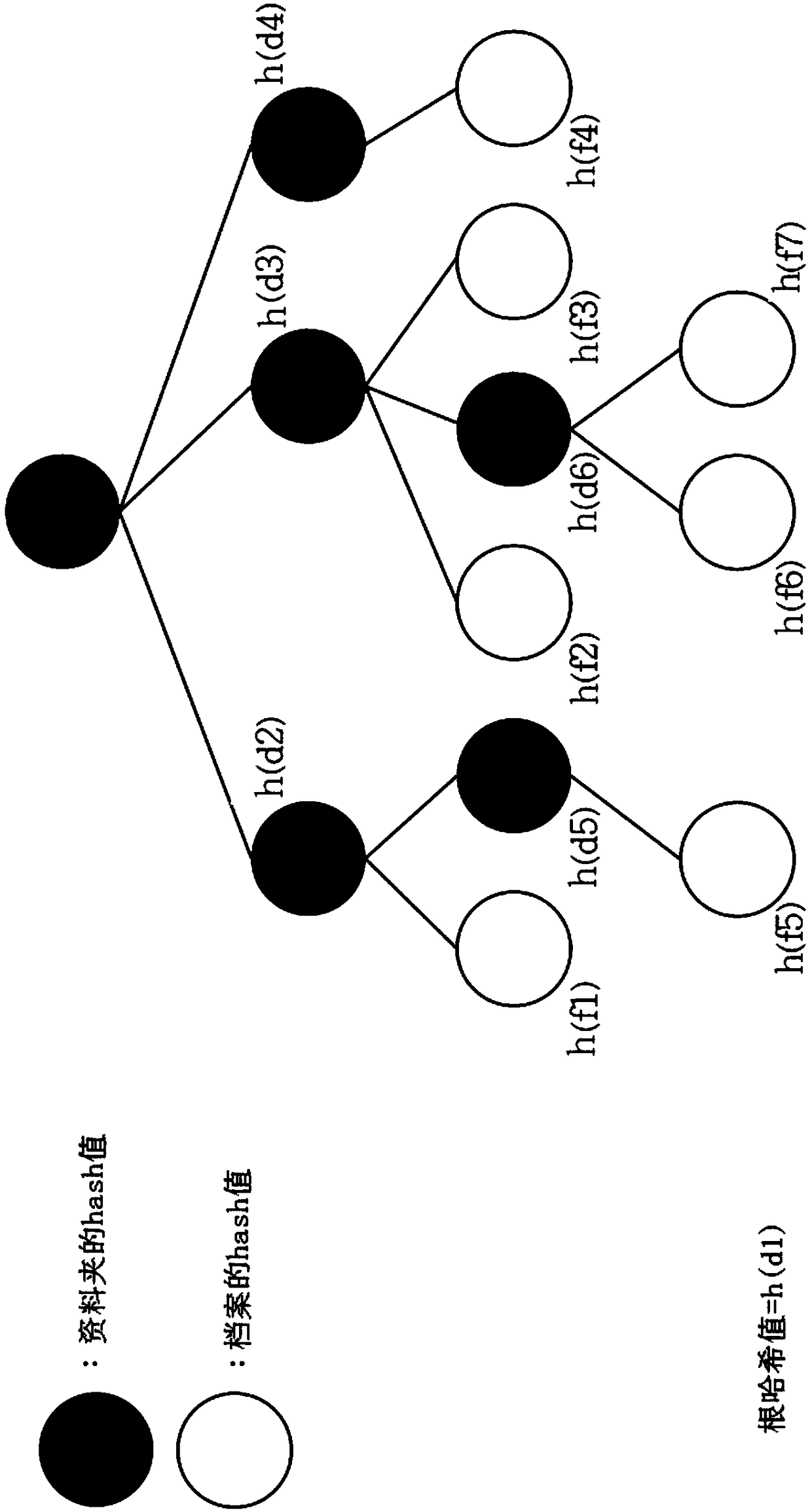
[0022] Such as figure 1 , 2 as shown, figure 1 For the file folder tree structure, figure 2 is a hash value tree structure, composed of figure 1 It is known that when a user client starts to use cloud services, the user client calculates the hash value (Hash value) of each file and folder in the library in its operating system and records it. figure 2 It is known that from the leaf nodes at the bottom of the tree, the files and folders are calculated layer by layer, for example, h(d3)=h(h(f2)|h(d6)|h(f3)), where h ha Hash function, because the hash value at the top is called the root hash value. Due to the characteristics of the cryptographic encryption function, if the value of one of the nodes is modified, a different root hash value will be obtai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com