Risk behavior recognition method, storage medium, device and system
A recognition method and behavior technology, applied in the transmission system, electrical components, etc., can solve the problems of complex cheating methods and poor recognition effect of strong rules, and achieve good recognition effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
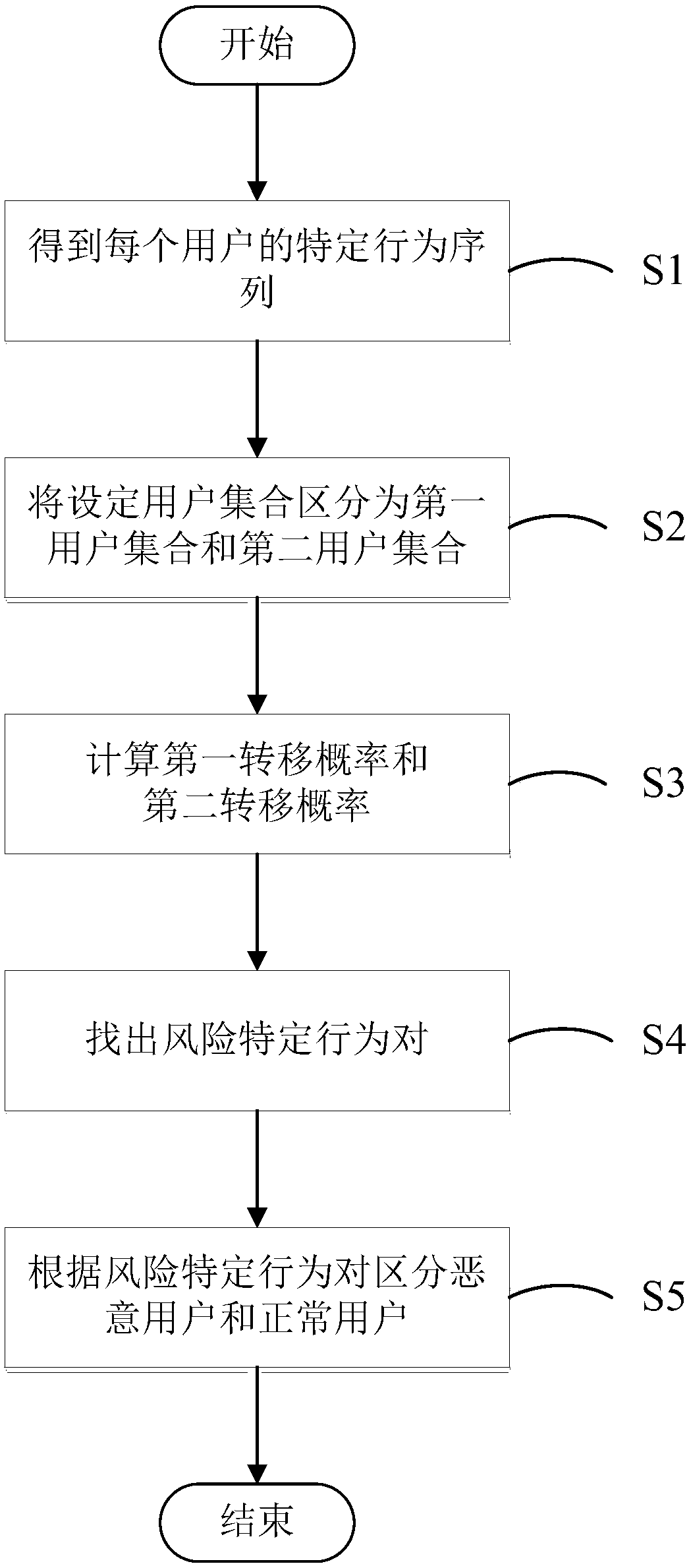
[0042] see figure 1 As shown, the embodiment of the present invention provides a risky behavior identification method, the method includes the following steps:
[0043] S1. According to the behavior log data, extract the specific behaviors of each user in the set user set, and sort all the specific behaviors of each user in time within the time window to obtain the specific behavior sequence of each user;
[0044] Among them, specific behaviors include registration, login, watching live broadcast, posting barrage, etc. These behaviors are for states in a Markov chain, a stochastic process that describes a sequence of states whose value for each state depends on a finite number of previous states. The Markov transition probability is the possibility of the transition of adjacent states before and after the Markov chain. Specific behaviors ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com