Method and device for allocating context resources to terminal
A terminal allocation and context technology, applied in electrical components, wireless communication and other directions, can solve the problems of MSG1 burst, inability to allocate context resources, and reduce LTE system performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
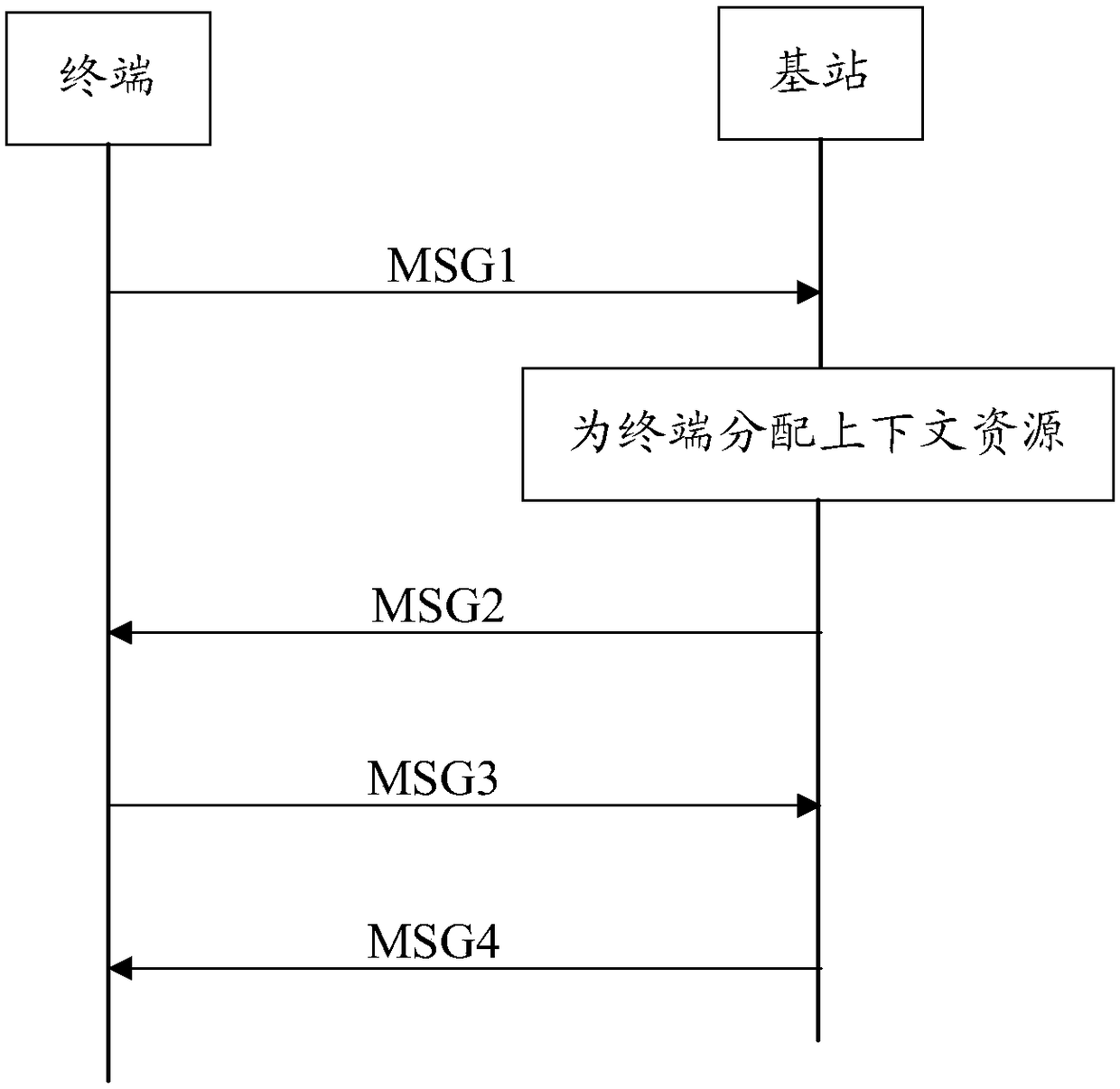
[0055] The present invention provides a method for allocating context resources for a terminal, such as figure 2 As shown, the whole process is as follows:
[0056] Step S21: the terminal sends MSG1 (MESSAGE1, the first message) to the base station;
[0057] Step S22: the base station sends MSG2 (MESSAGE2, the second message) to the terminal;
[0058] In the embodiment of the present invention, when the base station receives the MSG1 sent by the terminal, it can specifically allocate an access identifier and air interface resources for the base station, and encapsulate the access identifier and air interface resources allocated for the terminal to generate a MSG2 message, And send the MSG2 message to the base station.
[0059] Step S23: the terminal sends MSG3 (MESSAGE3, the third message) to the base station;
[0060] In the embodiment of the present invention, when the terminal receives the MSG2 message sent by the base station, it can decapsulate the MSG2 message, and o...
Embodiment 2
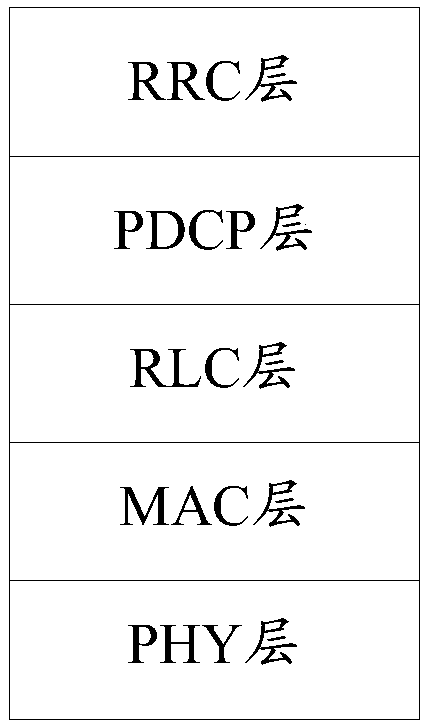
[0073] In the LTE (Long Term Evolution, long-term evolution) system, the terminal and the base station can specifically use the Uu interface for communication, and in practical applications, such as image 3 As shown, the Uu interface protocol stack can be specifically divided into PHY layer (Physical Layer, physical layer), MAC layer (Medium Access Control Layer, medium access control layer), RLC layer (Radio LinkControl Layer, radio link control layer), PDCP layer (Packet Data Convergence Protocol Layer, packet data convergence protocol layer) and RRC layer (Radio Resource Control Layer, radio resource control protocol layer).
[0074] However, the method disclosed in Embodiment 1 can be specifically applied to the random access process of the terminal, such as Figure 4 As shown, the whole process is as follows:
[0075] Step S41: the terminal reports MSG1;
[0076] Step S42: After the MAC layer of the base station receives the above-mentioned MSG1, it allocates an access...
Embodiment 3
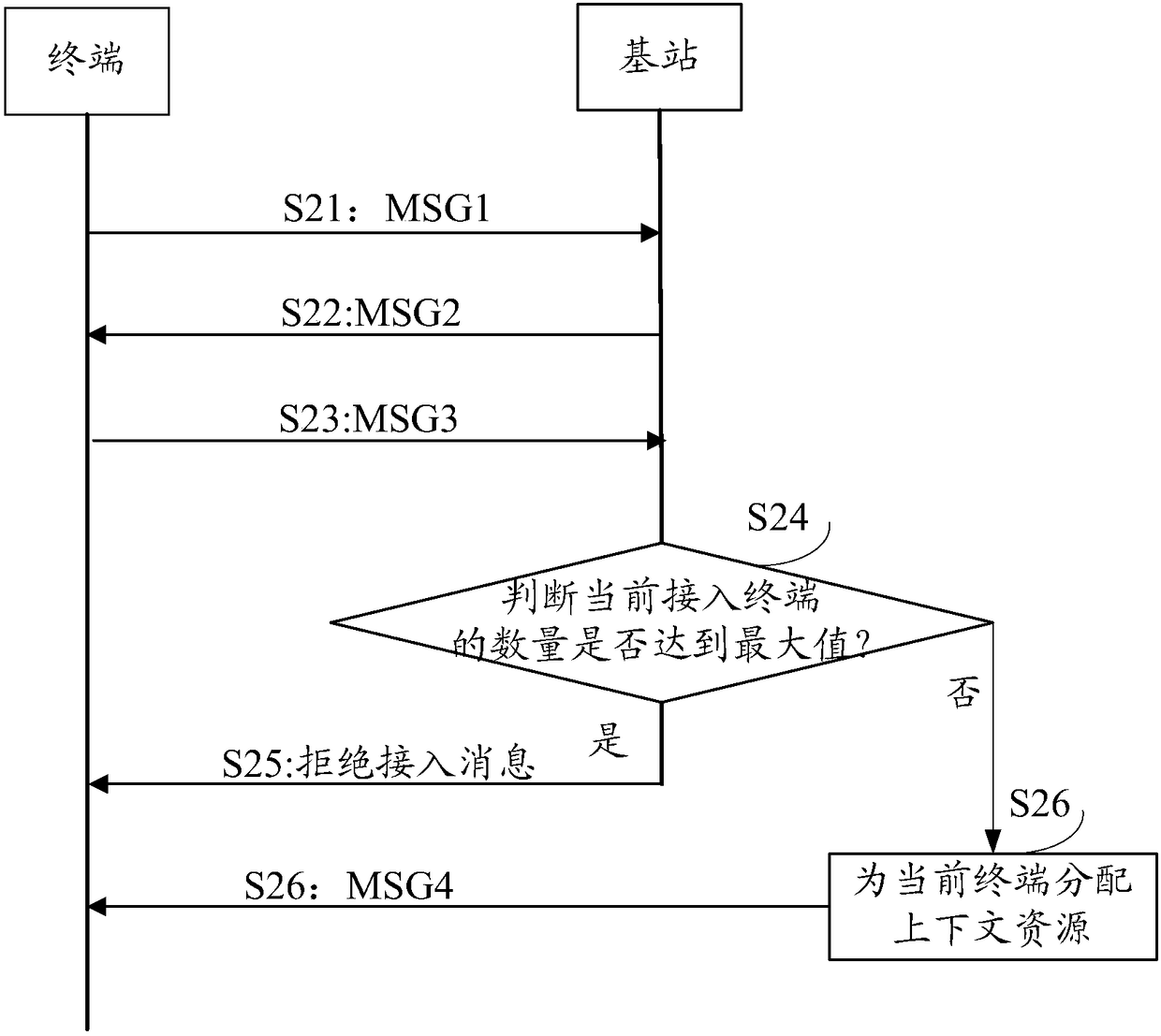
[0091] Corresponding to the above, the present invention also provides a device for allocating context resources for a terminal, such as Figure 5 As shown, the device includes:
[0092] The first sending unit 51 is configured to send a second message MSG2 to the terminal when receiving the first message MSG1 sent by the terminal;
[0093] The judging unit 52 is configured to, when receiving the third message MSG3 sent by the terminal, judge whether the number of terminals currently accessed by the base station reaches a maximum value; wherein, when the number of terminals accessed by the base station reaches a maximum value, the All context resources in the base station have been occupied, and the context resources are used to store information related to terminal communication;
[0094] The second sending unit 53 is configured to send an access rejection message to the current terminal when the number of the current access terminal reaches a maximum value.
[0095] Optiona...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com