An authentication method and device
An authentication method and technology of an authentication device, applied in the field of communication, can solve problems such as reducing signaling efficiency, and achieve the effect of improving signaling efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
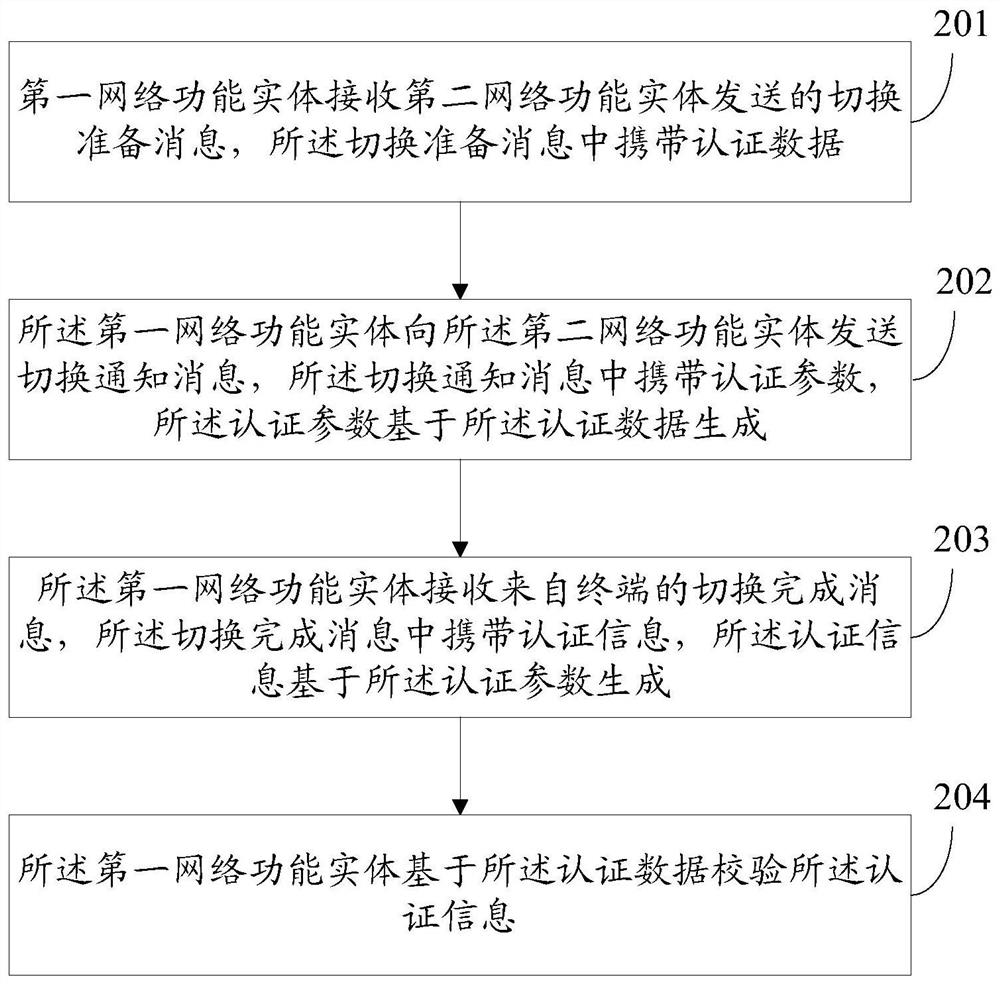
[0071] Embodiment 1 (the first network functional entity is a target base station system, and the second network functional entity is a core network element)
[0072] Figure 4 It is a schematic flowchart of an authentication method based on a core network handover according to an embodiment of the present invention, as shown in Figure 4 As shown, the process includes:
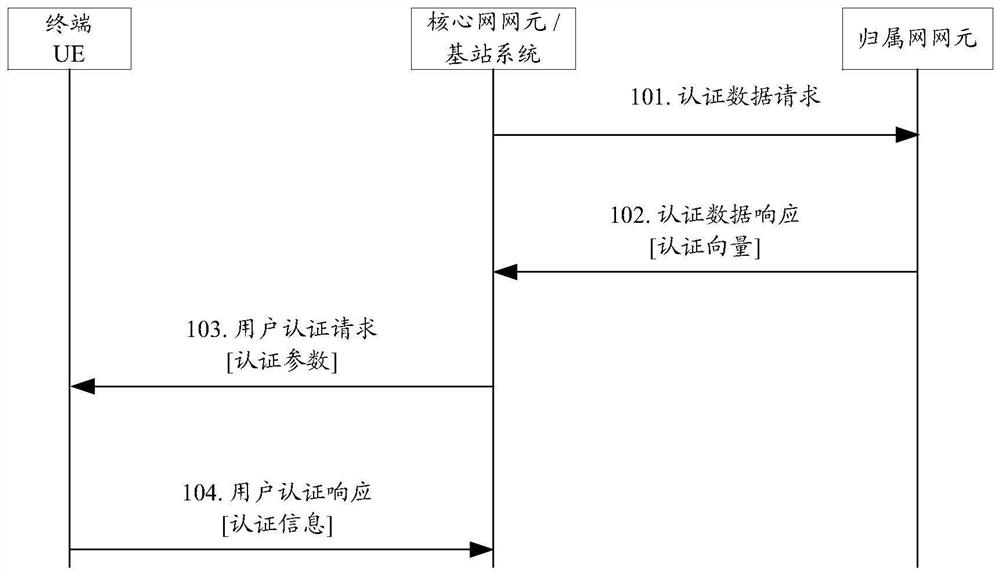
[0073] Step 401: The terminal UE accesses the mobile network, and the authentication data delivery network element initiates the authentication process for the terminal UE through the source base station system, or executes this embodiment or Figure 5 In the handover process in the embodiment, the source base station system caches these authentication data;
[0074] Step 402: The source base station system decides to initiate a handover process, and sends a handover request to a core network element (such as a mobility management function MMF, or MME), such as sending a Handover Required message, carrying ...
Embodiment 2
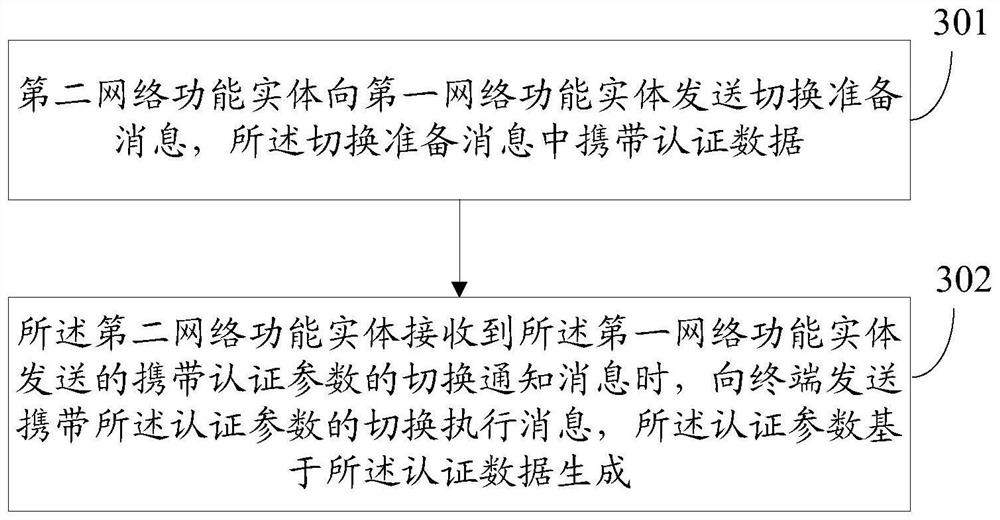
[0081] Embodiment 2 (the first network functional entity is the target base station system, and the second network functional entity is the source base station system)
[0082] Figure 5 It is a schematic flowchart of an authentication method based on an access network handover according to an embodiment of the present invention, as shown in Figure 5 As shown, the process includes:
[0083] Step 501: The terminal UE accesses the mobile network, and the authentication data delivery network element initiates the authentication process for the terminal UE through the source base station system, or executes this embodiment or Figure 4 In the handover process in the embodiment, the source base station system caches these authentication data;
[0084] Step 502: The source base station system decides to initiate a handover process, and sends a handover request to the target base station system, such as sending a Handover Request message, carrying cached authentication data;
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com