Control flow integrity checking method and device, and computer storage medium
A technology of integrity verification and control flow, applied in the direction of platform integrity maintenance, computer security devices, computing, etc., can solve problems such as high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
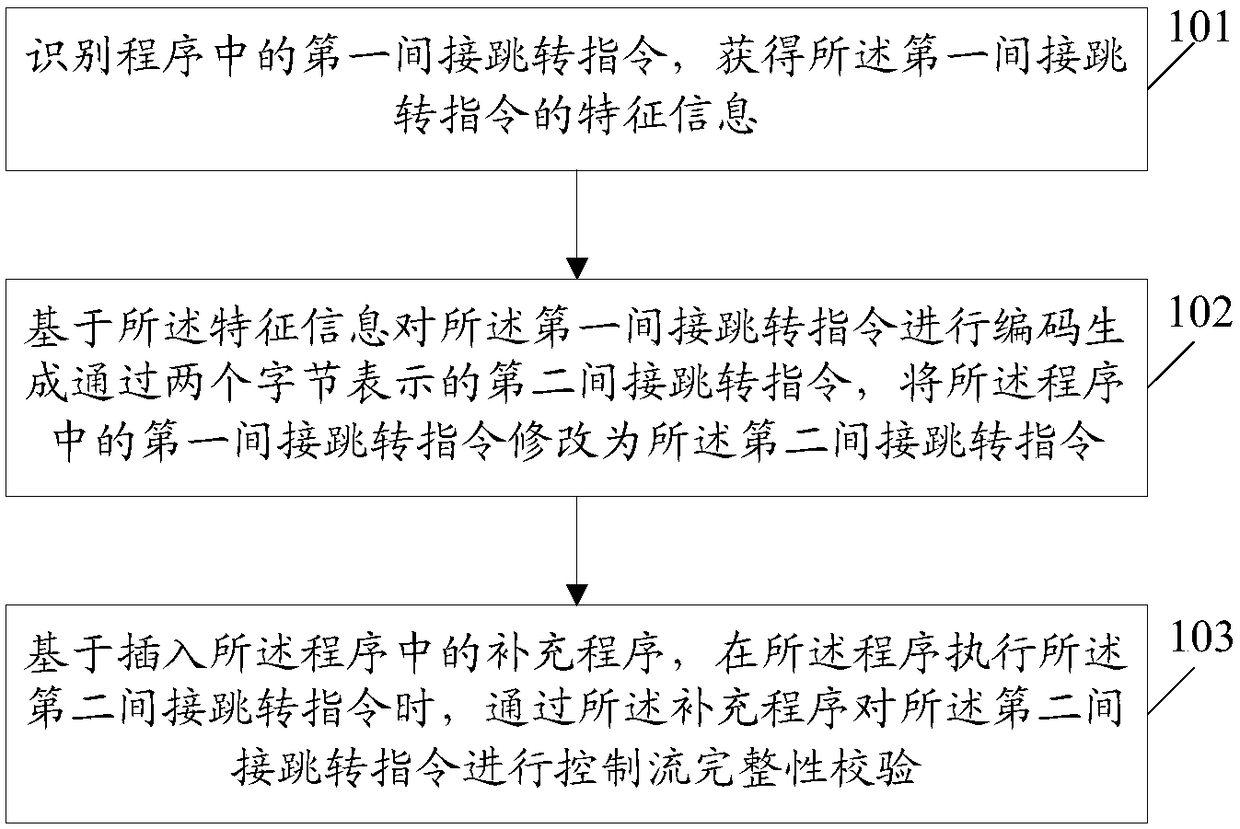
[0044] An embodiment of the present invention provides a control flow integrity verification method. figure 1 It is a schematic flow diagram of a control flow integrity verification method according to an embodiment of the present invention; figure 1 As shown, the method includes:
[0045] Step 101: Identify a first indirect jump instruction in a program, and obtain feature information of the first indirect jump instruction.
[0046] Step 102: Encode the first indirect jump instruction based on the feature information to generate a second indirect jump instruction represented by two bytes, and modify the first indirect jump instruction in the program to the The second indirect jump instruction.
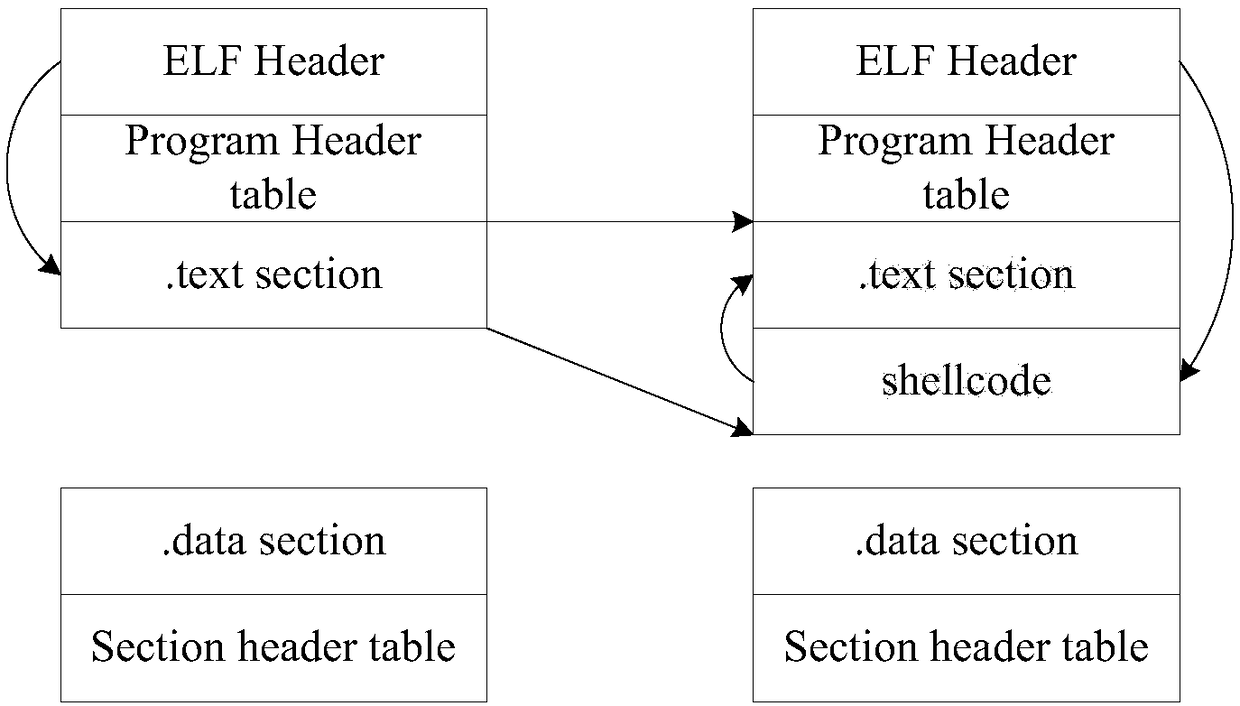
[0047] Step 103: Based on the supplementary program inserted into the program, when the program executes the second indirect jump instructi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com