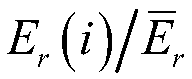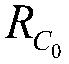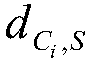Multi-path safety topology control method with intrusion tolerance capacity
A topology control, multi-path technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as wireless communication being easily interfered, computing power, memory, energy resources being limited, and the network being vulnerable to malicious attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] In order to describe the technical content of the present invention more clearly, further description will be given below with reference to specific embodiments.
[0050] In order to solve the above technical problems, the present invention provides a multi-path security topology control method with intrusion tolerance, including cluster head selection, clustering, route establishment and data transmission. Combine below Figures 1 to 3 These three steps are introduced separately.
[0051] like figure 1 As shown, the multi-path security topology control method with intrusion tolerance of the present invention, after the preprocessing is completed from the network operation, selects the cluster head according to the following steps:
[0052] Step 1: Calculate the optimal number of clusters k of the network using the N-order nearest neighbor analysis method opt ;
[0053] Step 2: Calculate the cluster head selection probability of nodes according to the parameters inc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com