A webpage backdoor detection method, device, equipment and storage medium
A web page backdoor and detection method technology, applied in the field of network security, can solve problems such as poor flexibility and difficulty in dealing with web page backdoor variants.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0061] In order to better understand the above technical solution, the technical solution of the present specification will be described in detail below by the drawings and the specific embodiments, and it is understood that the specific features of the present specification and the embodiment of the present specification are DETAILED DESCRIPTION, this specification embodiment and the technical features of the present specification may be combined with each other in the case of unlipped conditions.
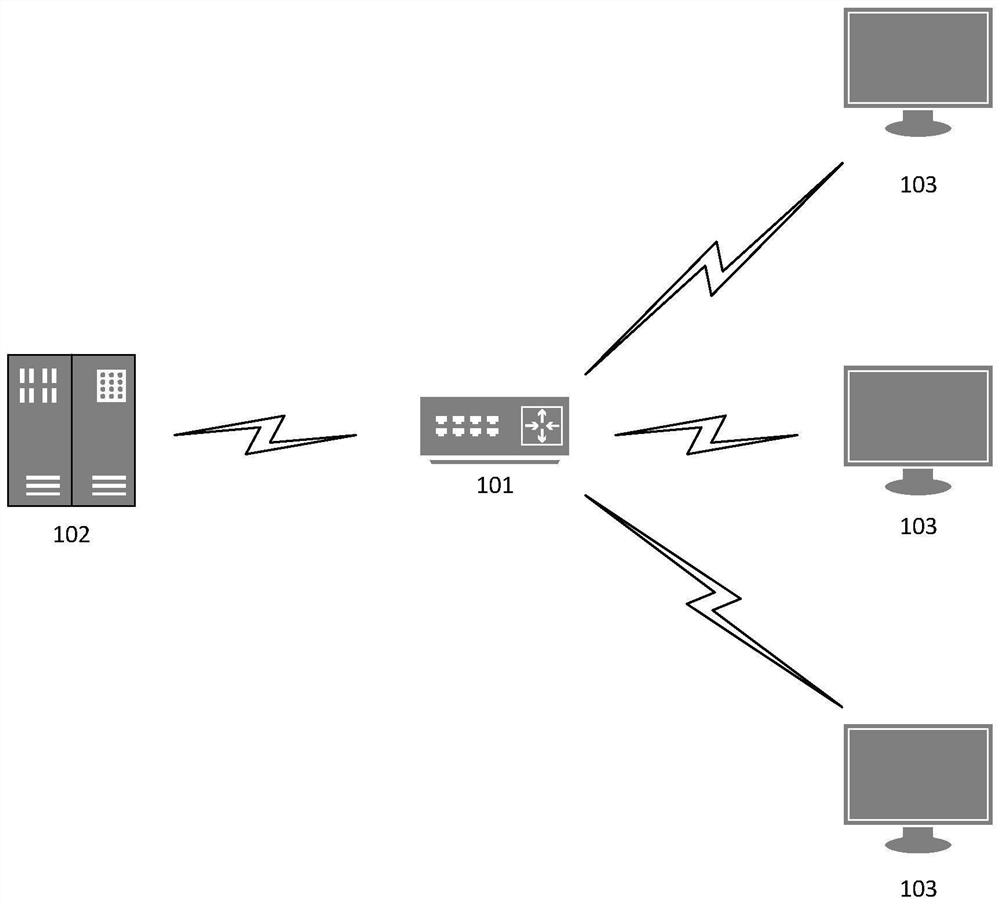
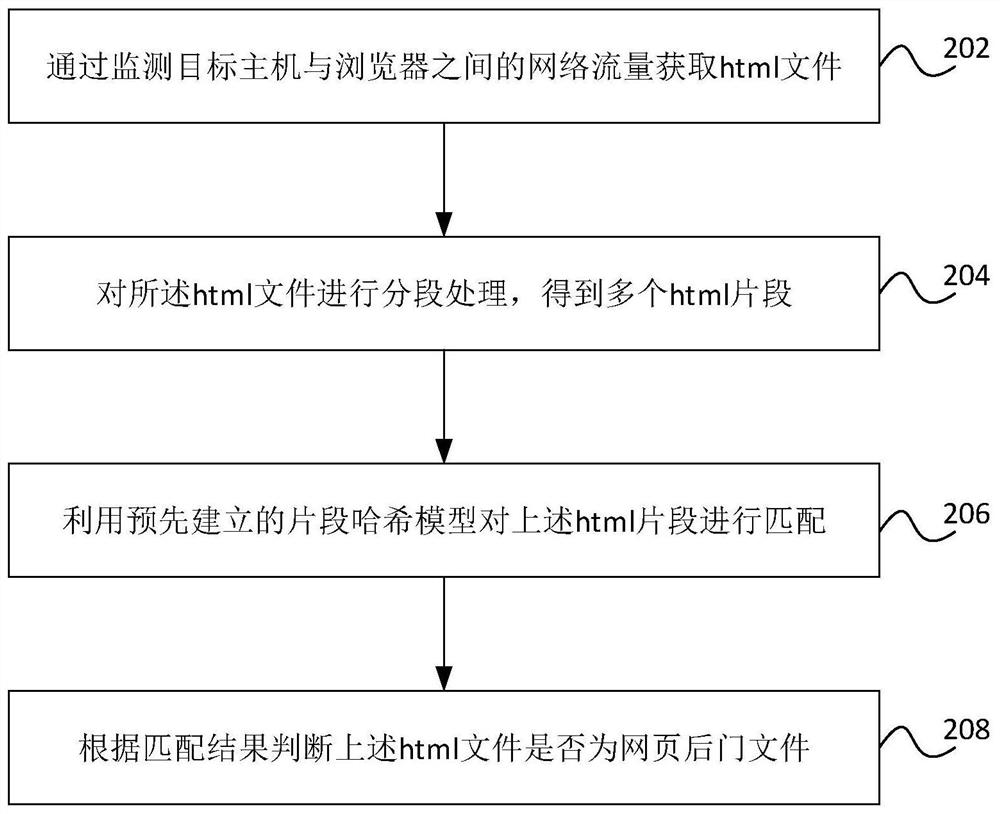
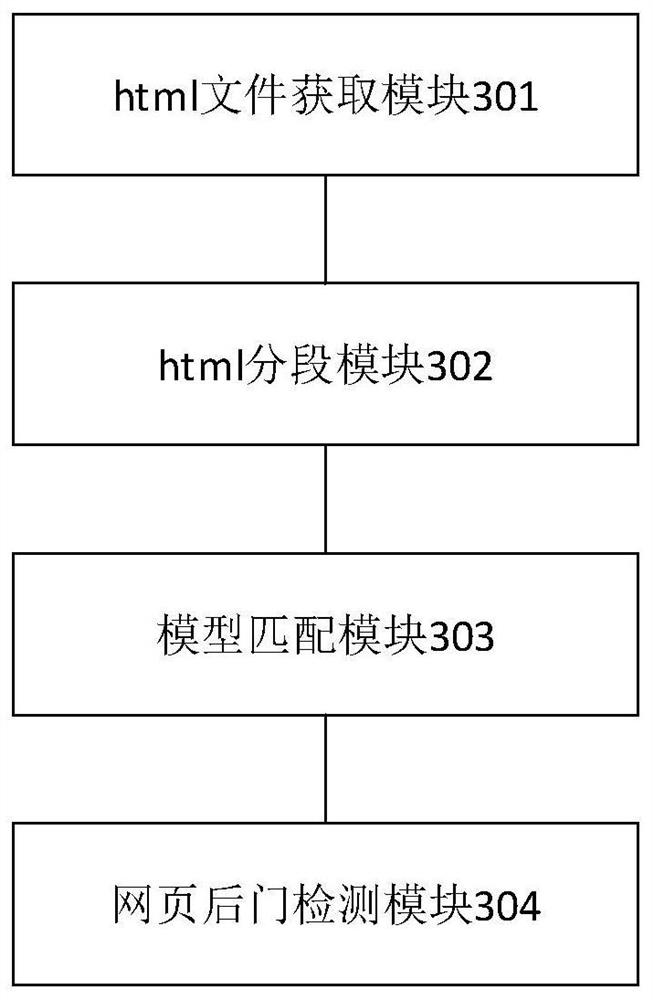
[0062] The technical solution provided in this specification embodiment is applied to the flow layer of the network, and can be implemented at the gateway or on the device including gateway functionality, and can be implemented on any device capable of monitoring network traffic. Take the method provided in the gateway as an example, such as figure 1 As shown, the gateway 101 monitors the network traffic between the target host 102 and the browser 103, which acquires the HTML file fro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com