Cross-site scripting attack defense method, device, apparatus and storage medium
A cross-site scripting attack and variant technology, applied in the field of network security, can solve problems such as inability to dynamically defend against XSS attacks, and achieve the effect of preventing XSS attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
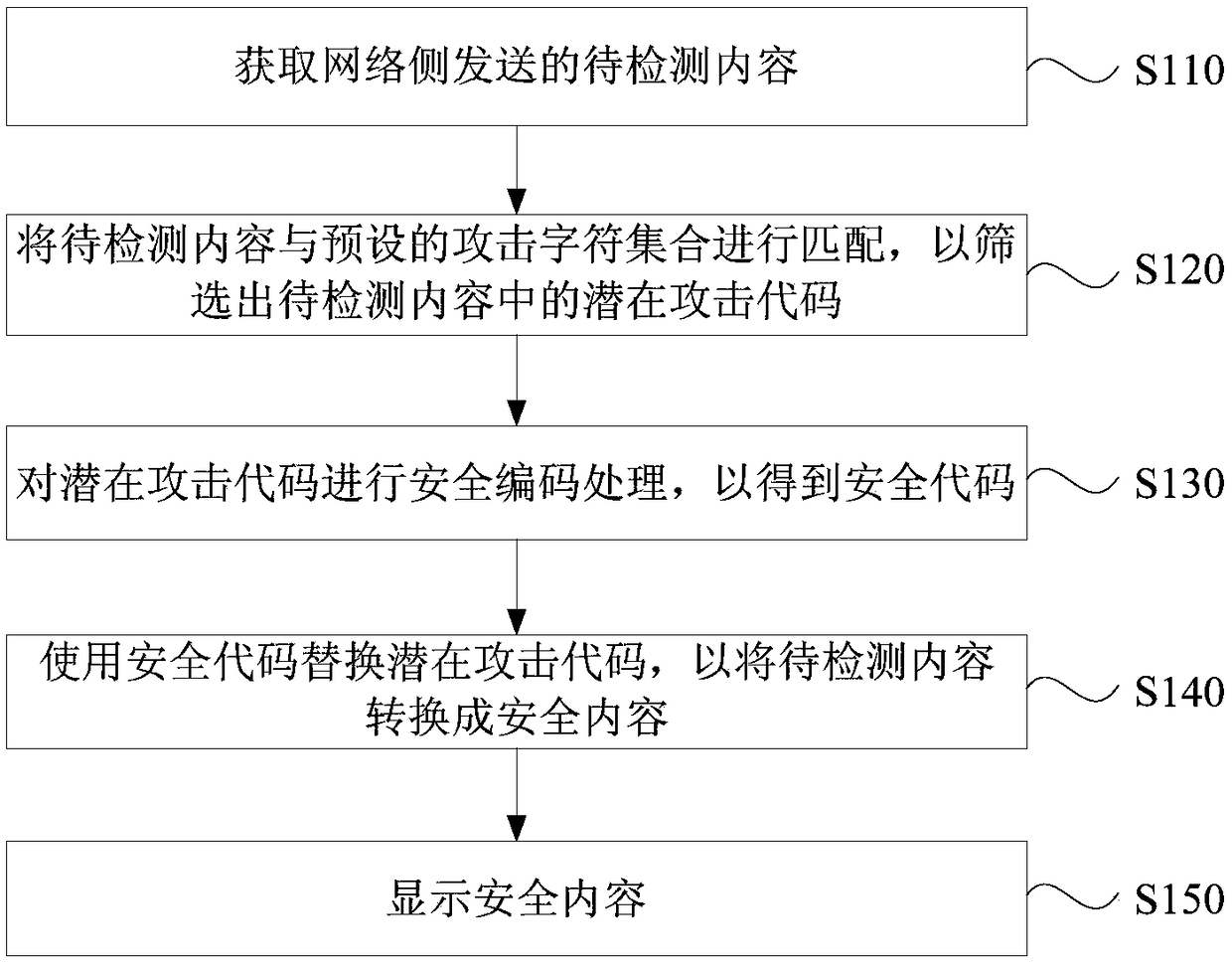
[0030] figure 1 It is a flow chart of a method for defending against cross-site scripting attacks provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of defending against cross-site scripting attacks. The method can be executed by a defense device for cross-site scripting attacks The cross-site scripting attack defense device may be realized by software and / or hardware, and the cross-site scripting attack defense device may be composed of two or more physical entities, or may be composed of one physical entity.
[0031] Generally speaking, XSS attacks include: reflection type (Non-persistent) XSS attack, storage type (persistent) XSS attack and DOM-base type XSS attack. Specifically, the malicious code of the reflected XSS attack generally exists in the address bar used to input the URL, and the attack is carried out when the user clicks a malicious link to the target website. The malicious code of the stored XSS attack is general...
Embodiment 2
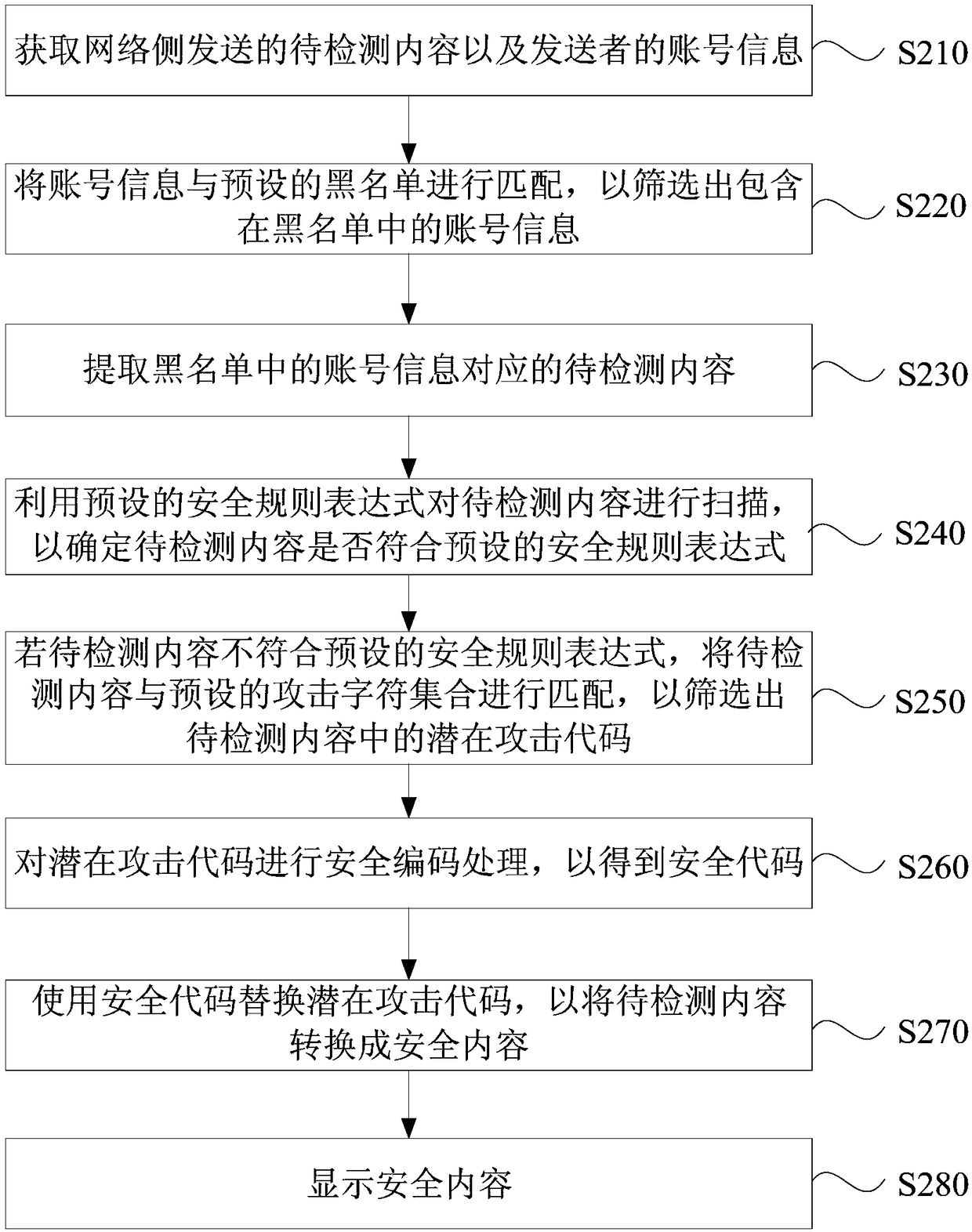
[0069] figure 2 It is a flowchart of a method for defending against cross-site scripting attacks provided by Embodiment 2 of the present invention. This embodiment is based on the foregoing embodiments, and further specifies the defense method for cross-site scripting attacks. Such as figure 2As shown, the defense method of the cross-site scripting attack in this embodiment specifically includes the following steps:
[0070] S210. Obtain the content to be detected and the sender's account information sent by the network side.
[0071] Wherein, the sender's account information can be understood as the user's account information on different network platforms of the client, for example, the user's account information on self-media platforms such as blogs, microblogs, and post bars. In this embodiment, the sender's account information can be listed as a blacklist or a whitelist. Wherein, the object of the blacklist or the whitelist is the sender's account information or IP ...
Embodiment 3
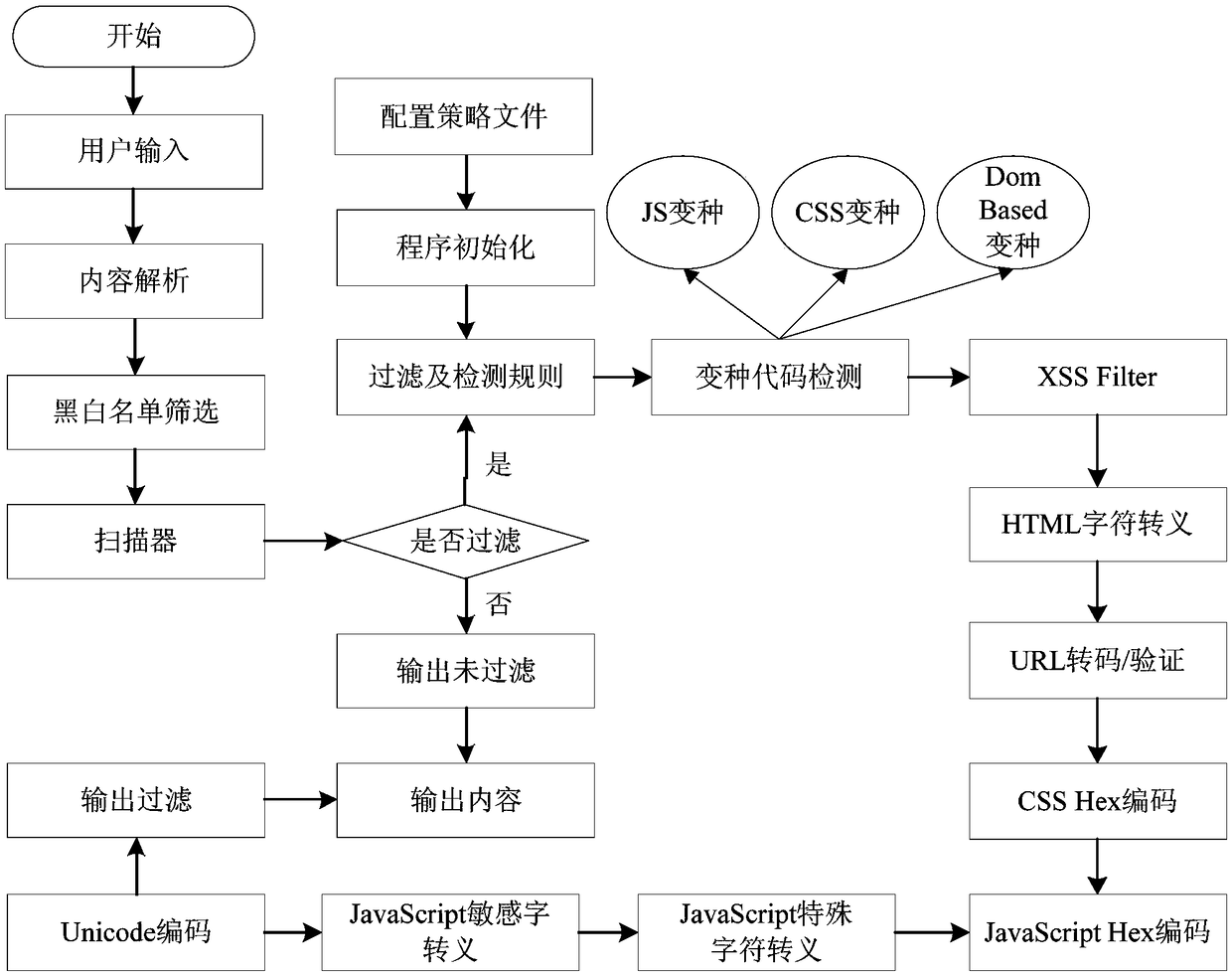
[0096] image 3 It is a flowchart of a method for defending against cross-site scripting attacks provided by Embodiment 3 of the present invention. This embodiment is based on the foregoing embodiments, and is used as a preferred embodiment to specifically describe a defense method for cross-site scripting attacks. Such as image 3 As shown, the specific operation steps of the cross-site scripting attack defense method in this embodiment are as follows:
[0097] Configure the policy file according to user requirements to generate a policy file in XML (eXtensible Markup Language, Extensible Markup Language) format. Specifically, the policy file may include the following three contents: configuring global variables according to global rules; configuring black and white lists; configuring filtering keywords, filtering key characters and filtering labels. Among them, configuring the policy file according to the user's needs can be understood as the customized configuration of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com