Device sharing method and system, computer device and storage medium
A technology for sharing systems and equipment, applied in the blockchain field, can solve problems such as low GPS positioning accuracy and non-refundable user deposits, and achieve accurate timing and reasonable and fair fees
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
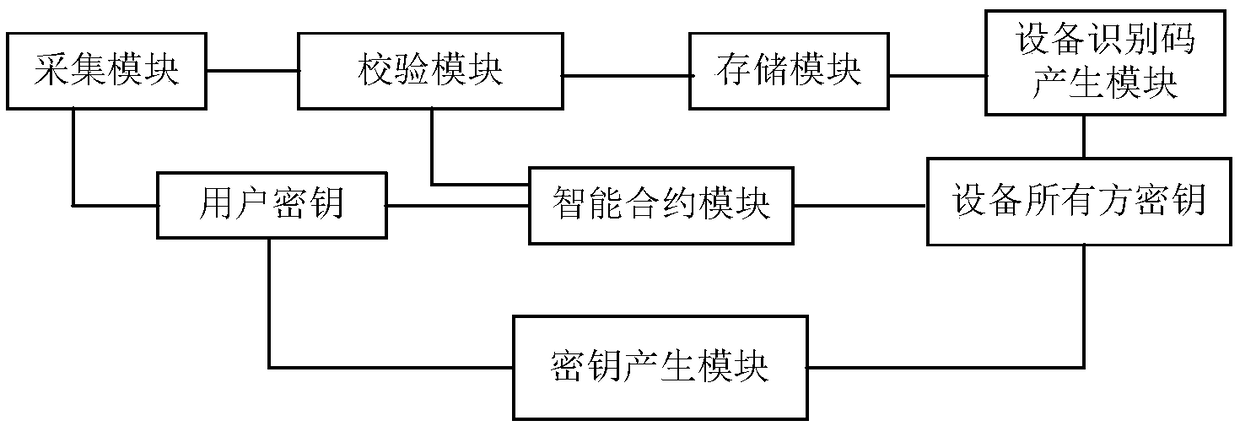
[0038] A device sharing system such as figure 1 As shown, it includes a key generation module, a device identification code generation module, an acquisition module, a storage module, a smart contract module and a verification module; the key generation module generates public keys and private keys on the blockchain for users and device owners. key; the device identification code generation module generates a unique device identification code for the device and stores it on the storage module; the collection module collects the user's voice, image and fingerprint information and stores it on the storage module, and the storage module is used to store the device identification code and user Voice, image and fingerprint information; the smart contract module is associated with the key of the user and the device owner; the verification module is used to verify user information, and the acquisition module, verification module and smart contract module are connected in sequence.
...
Embodiment 2
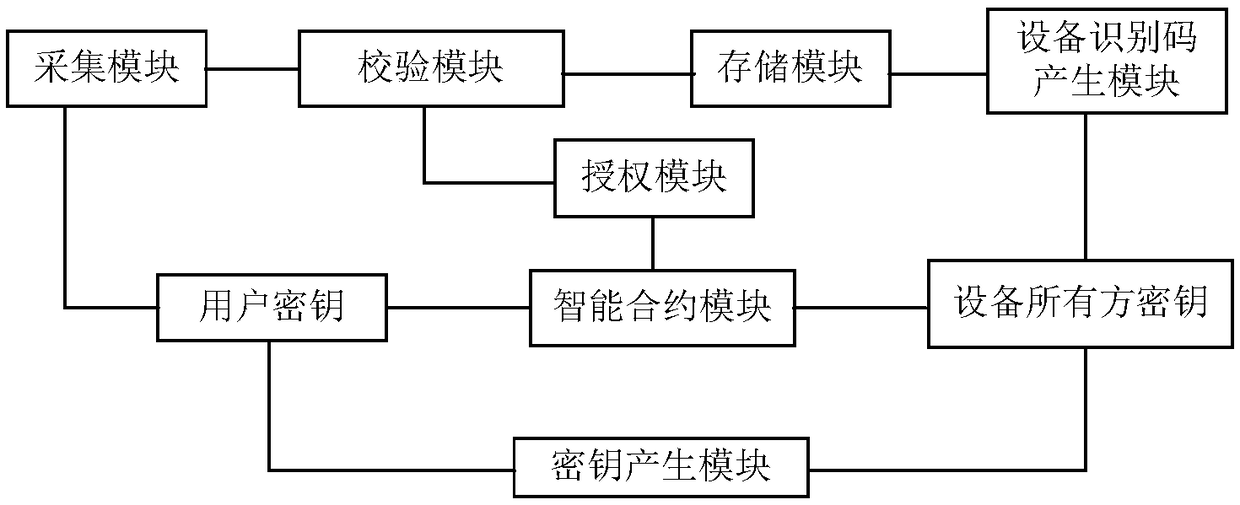
[0044] A device sharing system in this embodiment is further improved on the basis of Embodiment 1, such as figure 2 As shown, it also includes an authorization module. The authorization module interacts with the smart contract module and the verification module. After the user information verification is successful, the device owner authorizes the user to use through the authorization module.
[0045] In order to further expand the control authority of the device owner, after the verification module is successfully verified, it sends information to the authorization module. After seeing the user's information, the device owner can decide whether the user is free to use or pay, and communicate with the smart contract module Interaction, if the authorization module sends the smart contract module free use, the device starts to use the timer, and the smart contract module enforces the deposit to be frozen. The contract module sends a fee for use, and the device starts to use th...
Embodiment 3
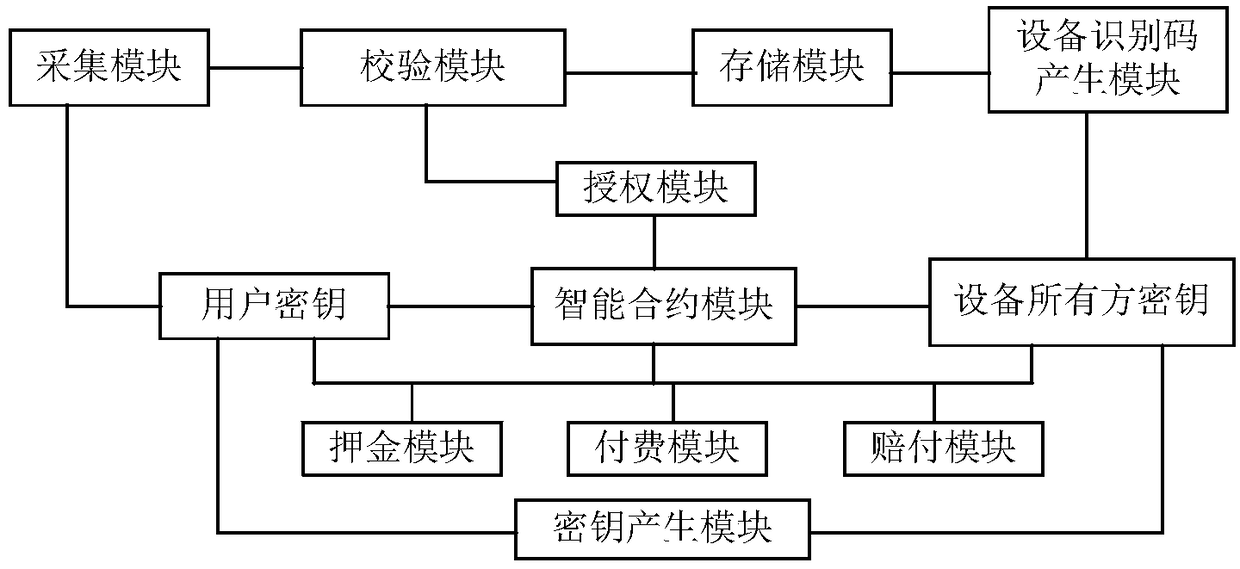
[0048] A device sharing system in this embodiment is further improved on the basis of Embodiments 1 and 2, such as figure 2 As shown, the device owner releases the use rights according to the user's information through the authorization module, and the use rights include free use and paid use. The device owner can authorize specific users to use it for free, and record it in the smart contract module. After the verification is passed, the smart contract module detects the user authorized by the device owner for free use, and automatically executes the smart contract for the user to use.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com