Method and equipment for acquiring symmetric key
A symmetric key and key technology, applied in the field of communication security, can solve the problems of low security, sensitive data such as symmetric keys are easy to be stolen, and the process is cumbersome, so as to achieve the effect of enhancing security, convenient and quick update or upgrade
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0034] Embodiment 1 provides a method for obtaining a symmetric key, including the following steps:
[0035] Step 101: The device receives the key transmission instruction sent by the host computer, parses the key transmission instruction to obtain the key block data;
[0036] Step 102: The device acquires a preset protection key; obtains the first key according to the protection key, first preset data, and second preset data;
[0037] Optionally, in step 102, the first key is obtained according to the protection key, the first preset data and the second preset data, specifically:
[0038] The device calculates the first preset data according to the protection key to obtain the first data, and obtains the first key according to the first data and the second preset data;
[0039] Further, the device calculates the first preset data according to the protection key to obtain the first data, and obtains the first key according to the first data and the second preset data, specifi...
Embodiment 2
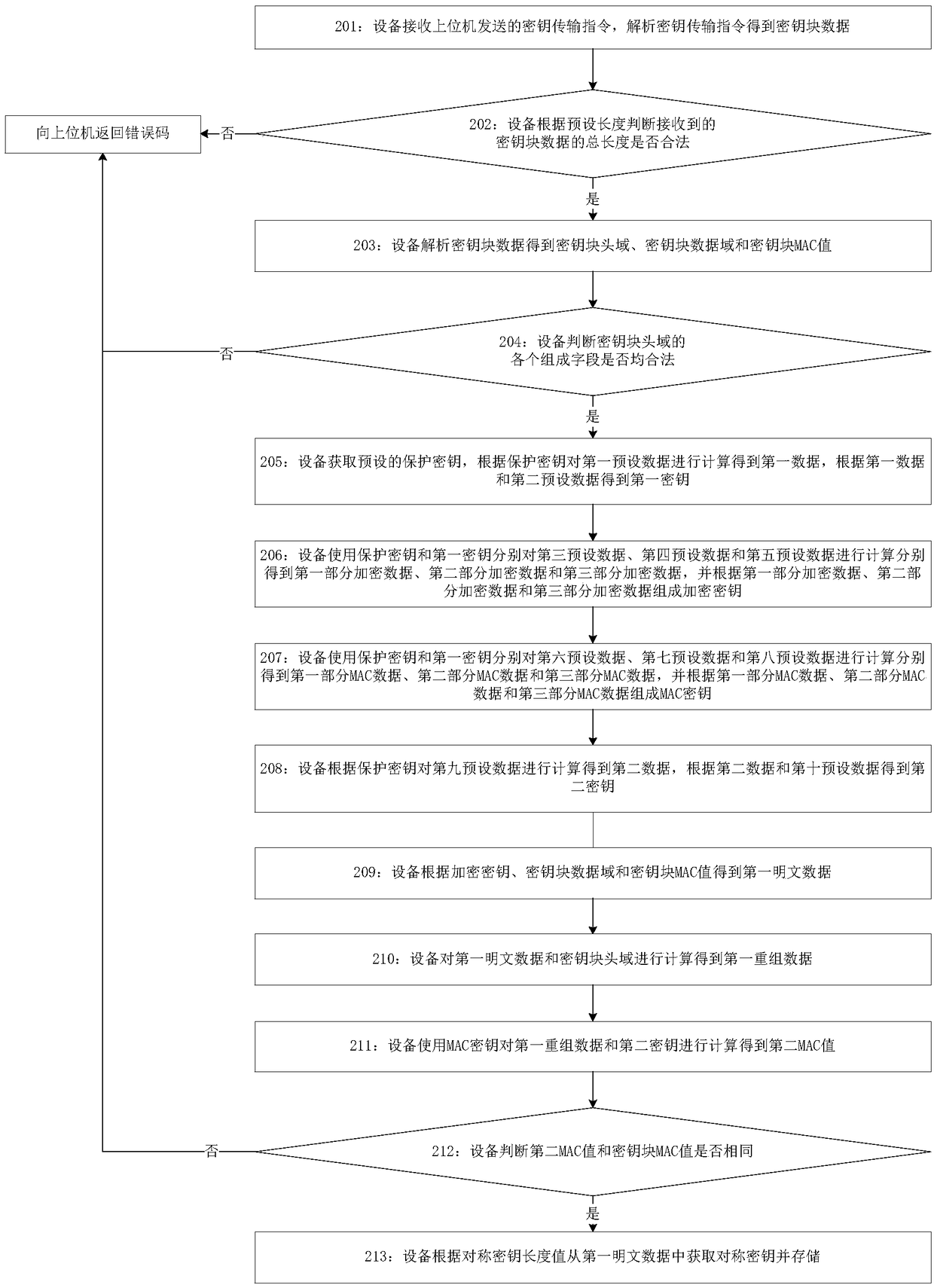
[0069] The second embodiment provides a method for obtaining a symmetric key, which can be performed directly in a public network environment without using special equipment; the method is as follows: figure 2 shown, including the following steps:
[0070] Step 201: The device receives the key transmission instruction sent by the host computer, parses the key transmission instruction to obtain the key block data;
[0071] 例如,密钥块数据为42303043305030544530304530303030364338354246323437383333393938443230394643374341373931453146414135343339433735303039373946413132463943363937334539373639354346323041373137423232 3131373738384437;
[0072] Step 202: The device judges whether the total length of the received key block data is legal according to the preset length, and if so, executes Step 203, otherwise returns an error code to the host computer;
[0073] Specifically, the device judges whether the total length of the received key block data is equal to the preset length, if yes, the t...
Embodiment 3
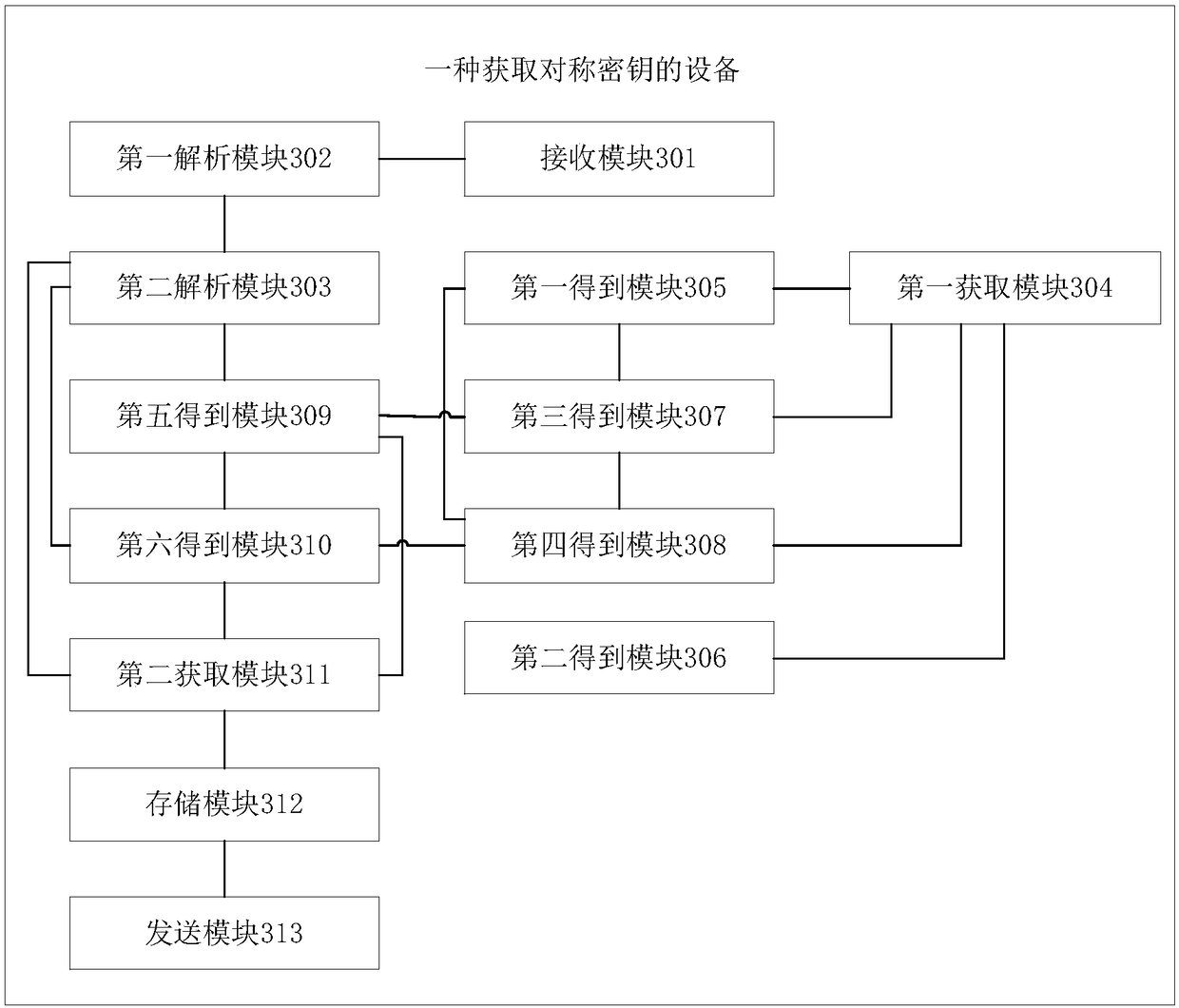
[0188] Embodiment 3 provides a device for obtaining a symmetric key, including a receiving module 301, a first parsing module 302, a second parsing module 303, a first obtaining module 304, a first obtaining module 305, a second obtaining module 306, The third obtaining module 307, the fourth obtaining module 308, the fifth obtaining module 309, the sixth obtaining module 310, the second obtaining module 311, the storing module 312 and the sending module 313;
[0189] The receiving module 301 is used to receive the key transmission instruction sent by the host computer;
[0190] The first parsing module 302 is configured to parse the key transmission instruction received by the receiving module 301 to obtain key block data;
[0191] The second parsing module 303 is configured to parse the key block data parsed by the first parsing module 302 to obtain a key block header field, a key block data field, and a key block MAC value;
[0192] A first obtaining module 304, configured...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com