Visible light communication system and method with security function
A visible light communication and visible light technology, which is applied in the visible light communication system and the field of communication, can solve problems such as easy leakage of user system information, network resource occupation, and active attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
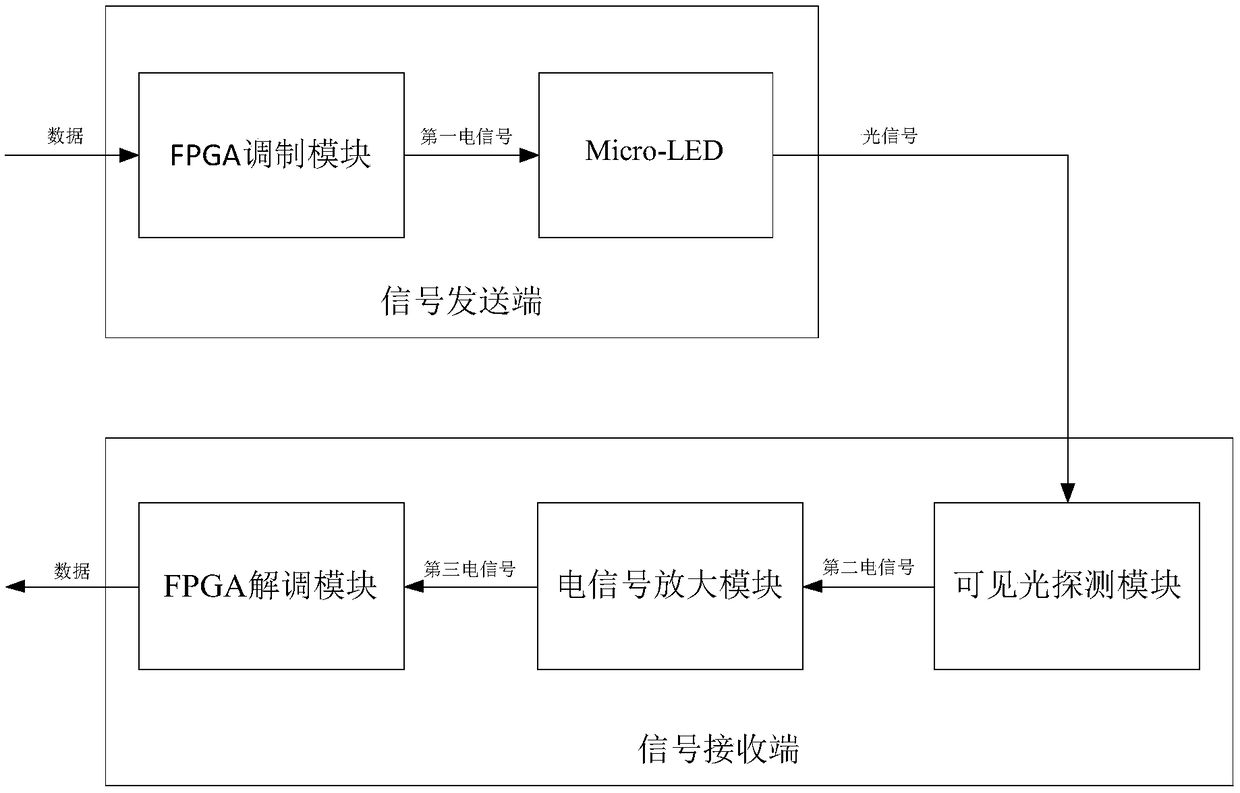
[0039] figure 1 It is a schematic diagram of a visible light communication system with a security function provided in this embodiment. The visible light communication system includes a communication sending end and a communication receiving end, wherein the communication sending end includes a cascaded FPGA modulation module and is used as For the Micro-LED display screen, the communication receiving end includes a cascaded visible light detection module, an electrical signal amplification module, and an FPGA demodulation module.
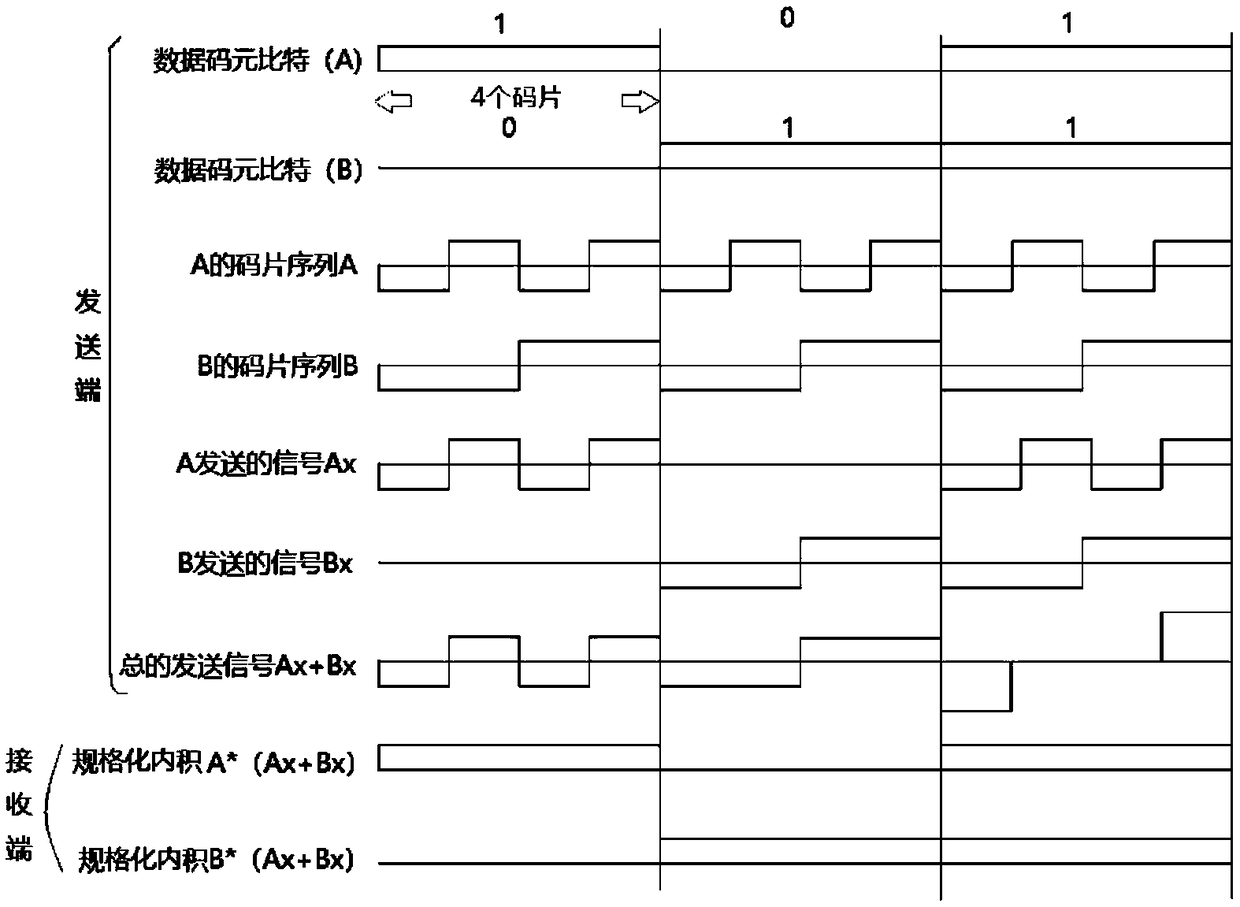
[0040] The visible light communication system adopts physical shading and CDMA encryption technology to achieve the effect of secure communication.
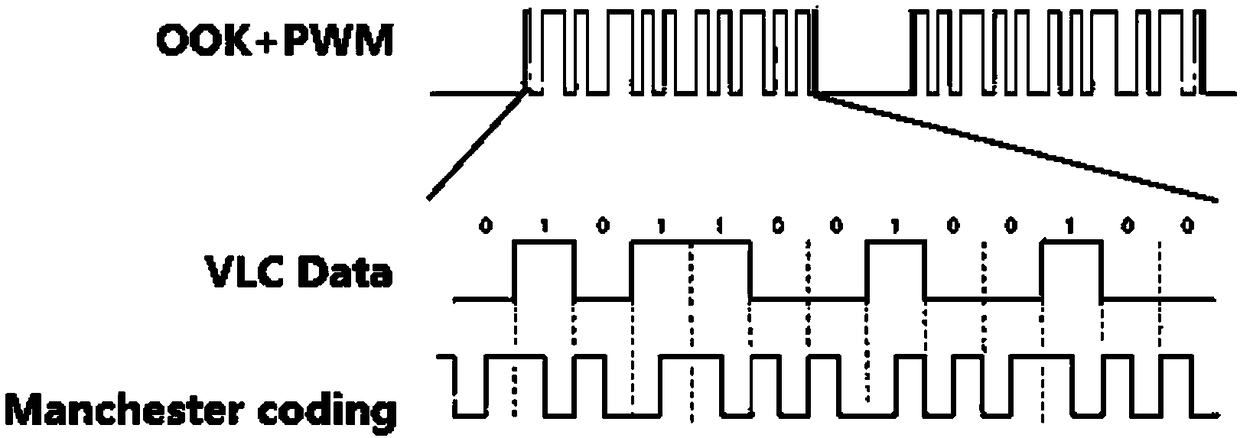
[0041] Wherein, the FPGA modulation module is used to perform modulation and digital-to-analog conversion on the binary sequence to be transmitted, and then combine it with the PWM modulation signal to obtain the first electrical signal, and send the first electrical signal to the Micro-LED;
[0042]...
Embodiment 2
[0062] This embodiment discloses a visible light communication method with a security function, and the steps of the visible light communication method are as follows:
[0063] Step S1, the FPGA modulation module receives the data, selects binary on-off keying to modulate the data, then uses code division multiple access to encrypt the data, finally combines with the PWM modulation signal to obtain the first electrical signal, and converts the first Electrical signals are sent to Micro-LEDs that are used as display screens.
[0064] In step S2, the Micro-LED converts the first electrical signal into electro-optic to generate an optical signal and sends it, and also plays a role of display.
[0065] Step S3, the electrical signal amplifying module adjusts the gain of the second electrical signal according to the optical power of the optical signal to obtain a third electrical signal.
[0066] Step S4, the FPGA demodulation module uses the received pseudo-random code to decrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com