Authentication method, apparatus, server, and storage medium
A storage medium and server technology, applied in the direction of electrical components, transmission systems, etc., can solve problems that affect the service or system security in the enterprise or platform, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
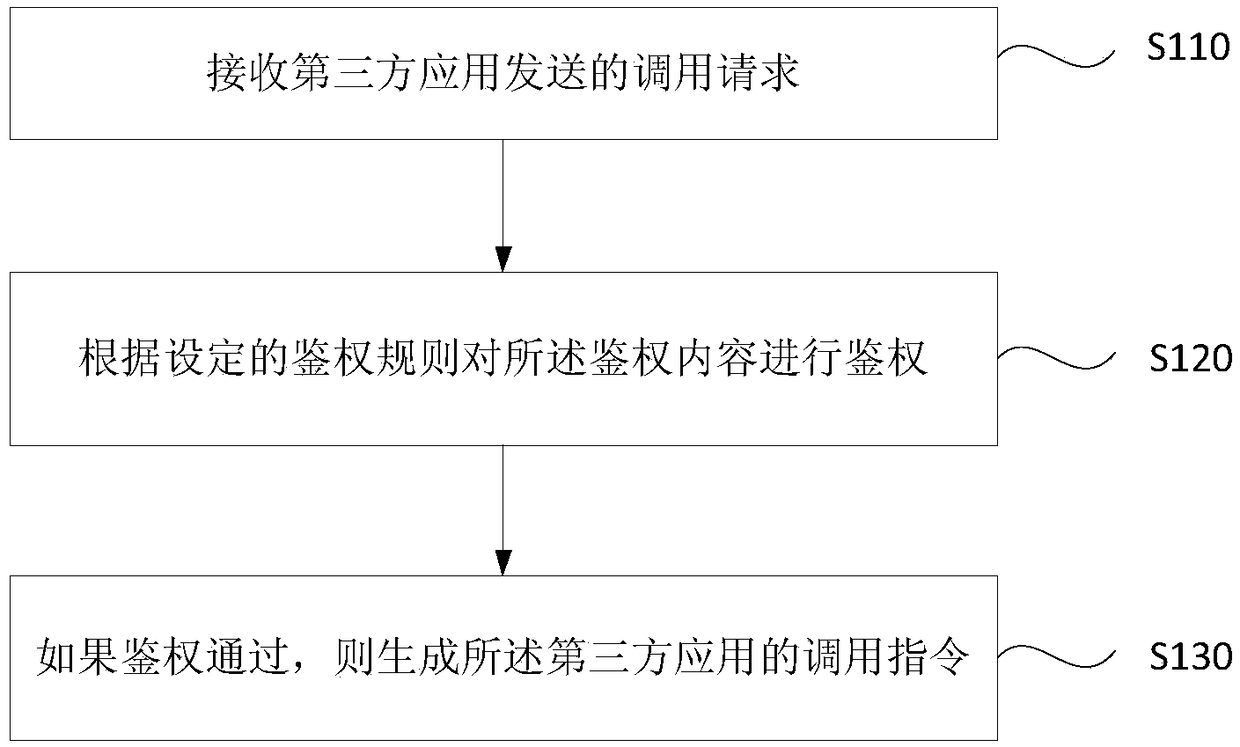
[0041] figure 1 This is a flowchart of an authentication method provided in Embodiment 1 of the present invention. This embodiment can be applied to a situation in which the security of the enterprise or platform is ensured by authenticating third-party applications that access services or systems in the enterprise or platform. The method can be performed by an authentication device, which is integrated in an authentication system. Specifically, the authentication system includes a unified authentication system and a basic service module, wherein the basic service module is used to receive a call request from a third-party application, Send the authentication content in the call request to the unified authentication system, and the unified authentication system is used to authenticate the received authentication content to identify whether the third-party application has the right to call the service provided by the basic service module, wherein , the authentication content ca...
Embodiment 2
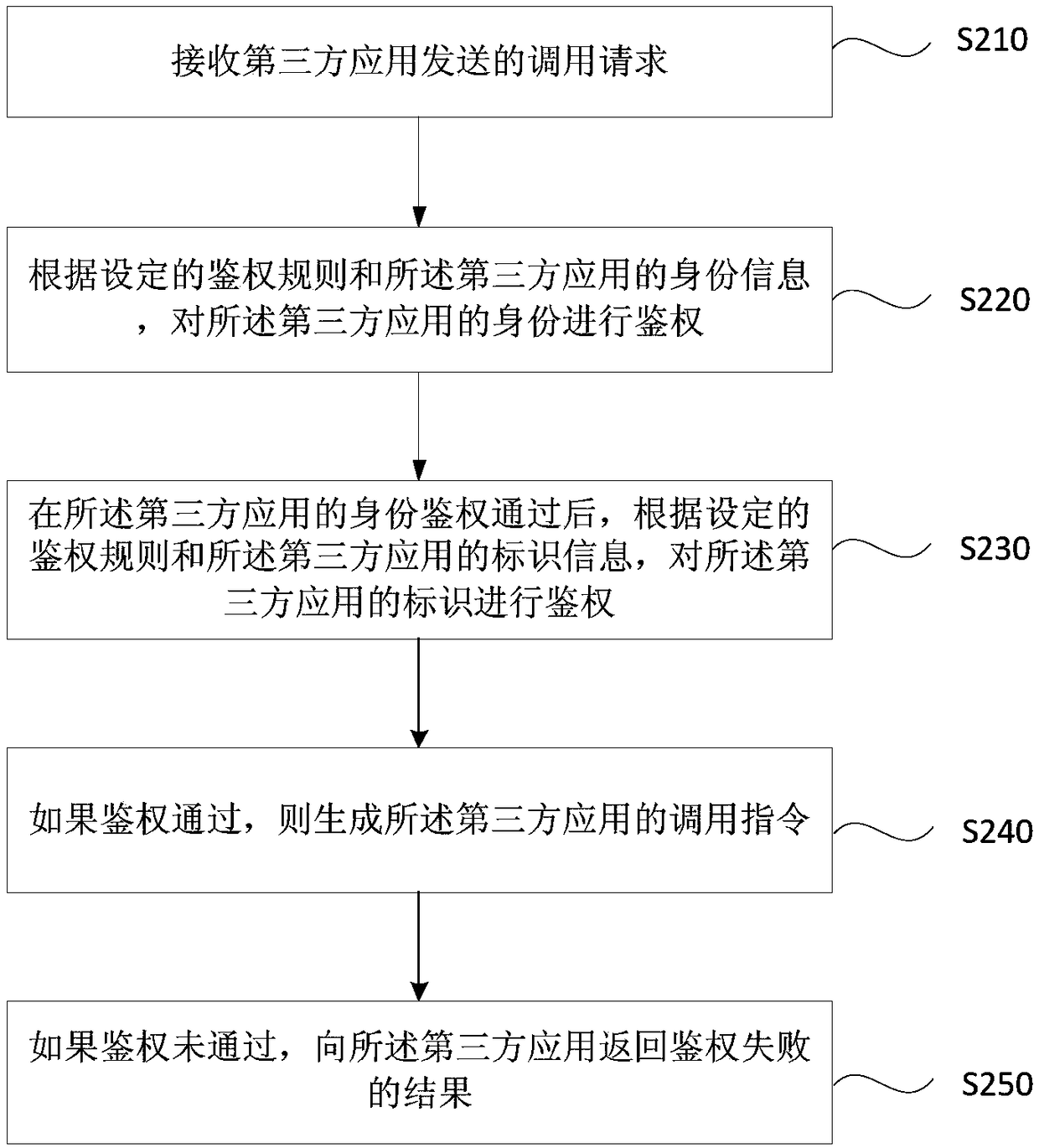
[0056] figure 2 It is a flow chart of an authentication method provided by Embodiment 2 of the present invention. On the basis of the above embodiments, the "authentication of the authentication content according to the set authentication rules" is optimized. Specifically, The method comprises the steps of:
[0057] S210. Receive a calling request sent by a third-party application.
[0058] S220. Authenticate the identity of the third-party application according to the set authentication rule and the identity information of the third-party application.
[0059] Specifically, the embodiment sets the authentication content to include: the identity information of the third-party application. The identity information can be the ID of the third-party application, the access time stamp and the identity authentication string, wherein the identity authentication string is the third-party application. The string used to verify the identity of the third-party application. The specifi...
Embodiment 3
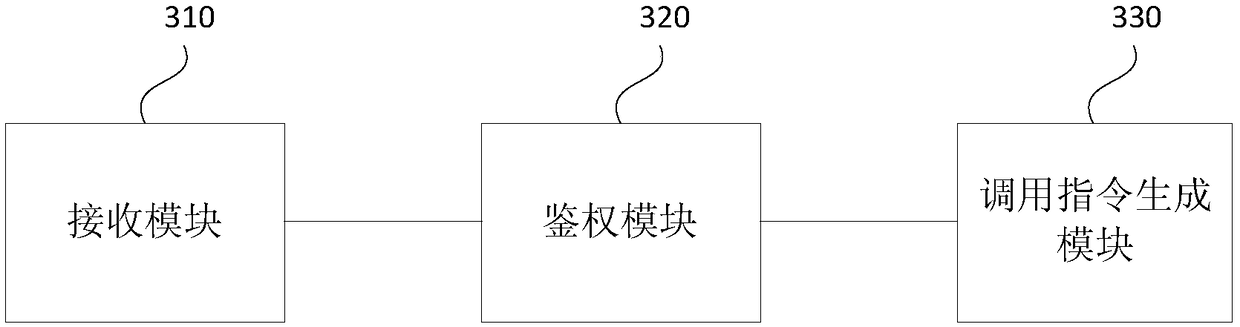
[0068] image 3 It is a structural diagram of an authentication device provided in Embodiment 3 of the present invention. The device can execute the authentication method provided in any of the above embodiments. Specifically, the device includes:
[0069] A receiving module 310, configured to receive a call request sent by a third-party application, where the call request includes authentication content;
[0070] An authentication module 320, configured to authenticate the authentication content according to set authentication rules;
[0071] The call instruction generating module 330 is configured to generate a call instruction of the third-party application if the authentication is passed.
[0072] Embodiment 3 of the present invention provides an authentication device. By receiving a call request sent by a third-party application, the call request includes authentication content, and performs authentication on the authentication content according to the set authentication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com