Method for triggering network authentication and related devices
A network device and network authentication technology, applied in the field of triggering network authentication, can solve problems such as terminal security threats, achieve convenient and fast decryption, avoid stealing or tampering, and ensure security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] The embodiments of the present application will be further described in detail below in conjunction with the accompanying drawings.
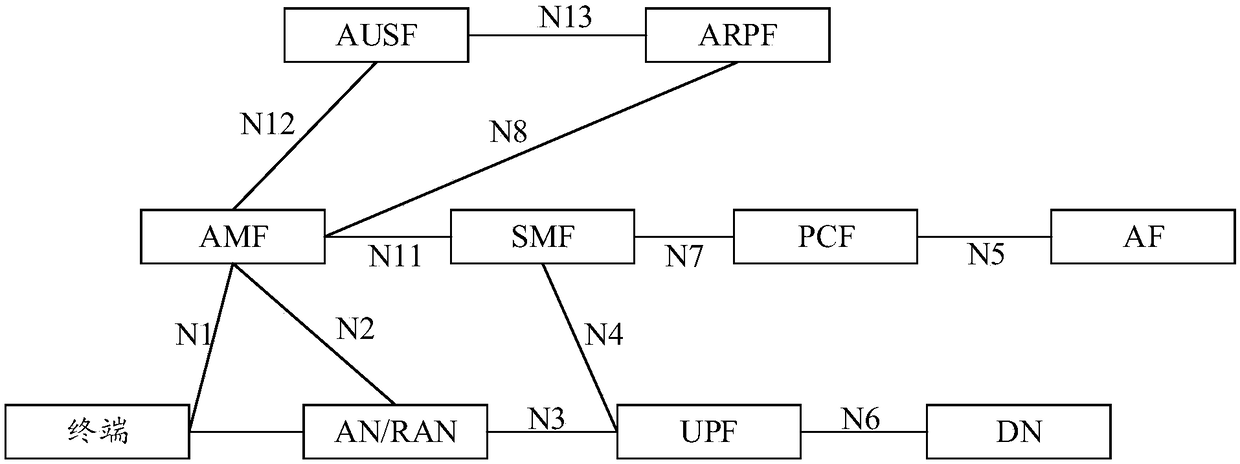
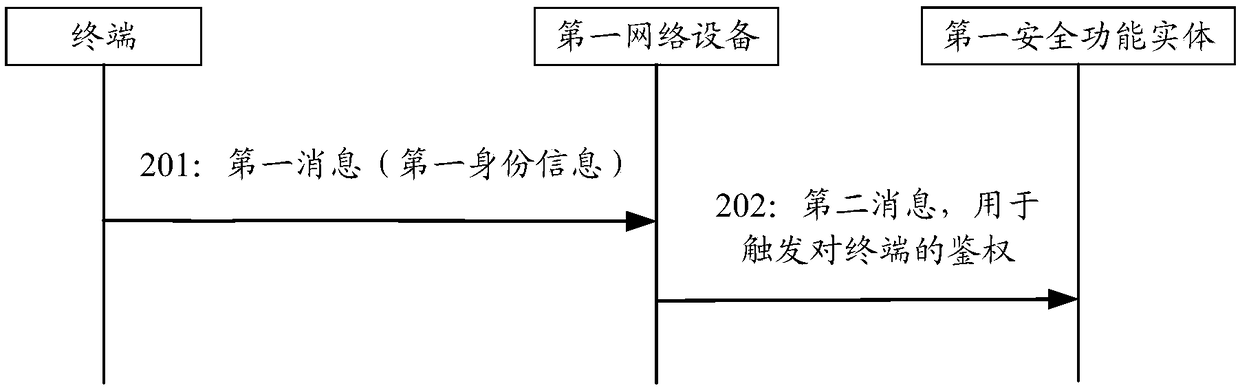
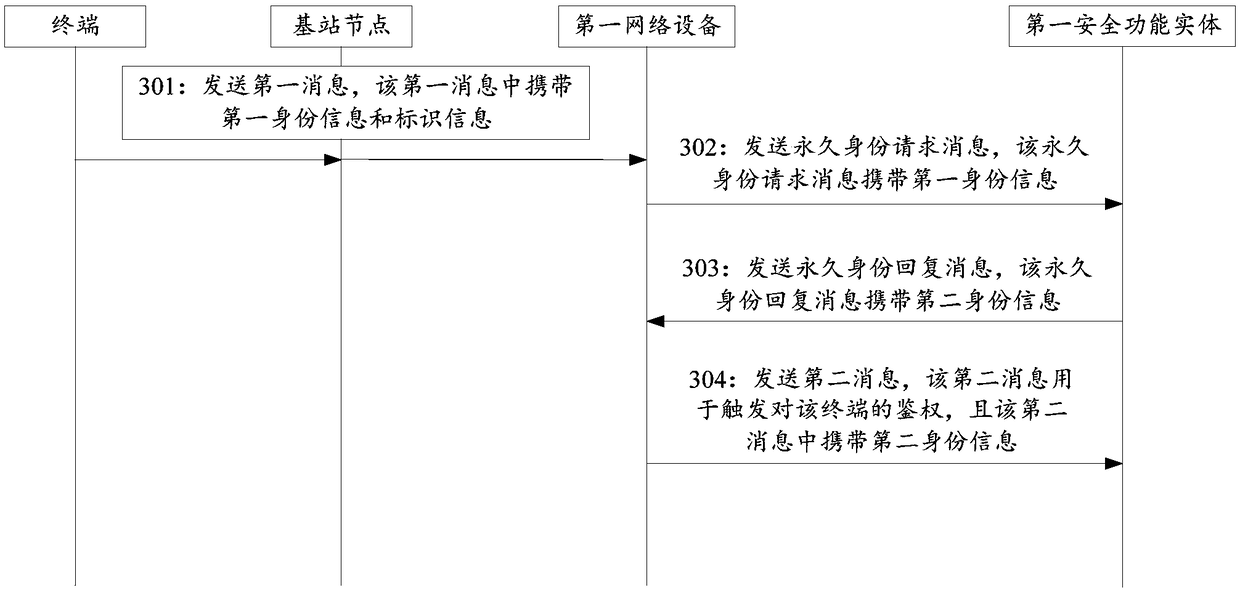
[0074]Before explaining the embodiment of the present application in detail, the application scenarios involved in the embodiment of the present application will be introduced first. Currently, a terminal can access a network through a 3GPP technology or a non-3GPP technology. Among them, 3GPP technology refers to the air interface technology formulated by 3GPP standards. For example, the air interface access technology of our commonly used 3G, 4G and 5G networks is 3GPP technology. The non-3GPP technology refers to an air interface access technology not formulated by the 3GPP standard, for example, an air interface technology represented by wireless fidelity access point (WIFI AP). When a terminal accesses a 5G network, whether it is accessed through 3GPP technology or non-3GPP technology, the terminal needs to send an attach message ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com