WPA-based key configuration method and device
A configuration method and key technology, which are applied to security devices, secure communication devices, and key distribution, can solve problems such as packet loss, low key configuration efficiency, and easy occurrence of data, so as to reduce the probability of packet loss, improve user experience, The effect of shortened time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
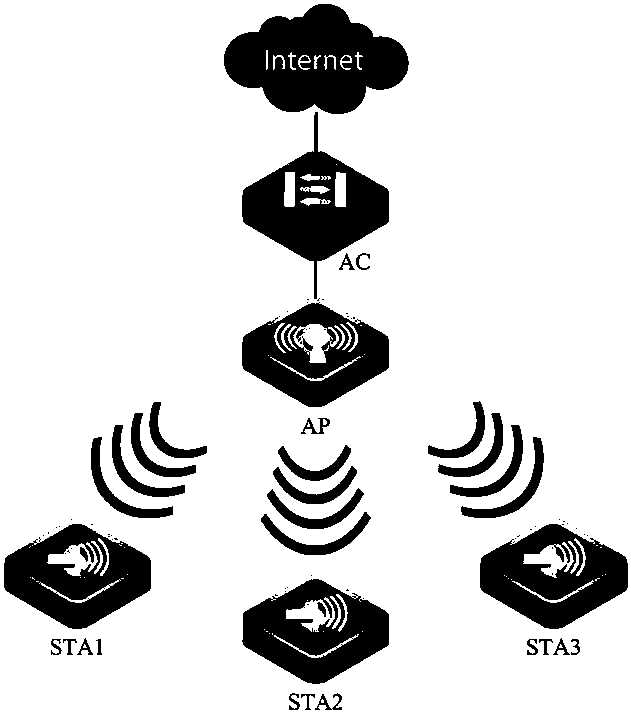
[0053] In view of the low efficiency of key configuration in WPA in the prior art and the problem that data packet loss is more likely to occur, the WPA-based key configuration method provided by the embodiment of the present invention can be applied to thin APs composed of ACs and APs. In the WLAN architecture, AC sends packets to STAs via APs, and STAs sends packets to ACs via APs. The flow process of the inventive method is as figure 1 As shown, this method is applied to the AC side, and the execution steps are as follows:
[0054] Step 101, sending the first message in the four-way handshake to the wireless access point AP, so that the AP sends the first message to the wireless terminal STA;
[0055] Step 102, when receiving the second message in the four-way handshake replied by the STA forwarded by the AP, generate an AP-side unicast key, and send the generated AP-side unicast key to the AP , so that when the AP receives the fourth packet in the four-way handshake repl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com