Cluster key generation method and device, and storage medium
A key generation device and key generation technology are applied to secure communication devices, public keys for secure communications, and key distribution, which can solve problems such as unsuitability for distributed environments, low efficiency and limitations of group keys, and achieve Improve resource sharing efficiency, improve key generation efficiency, and improve security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
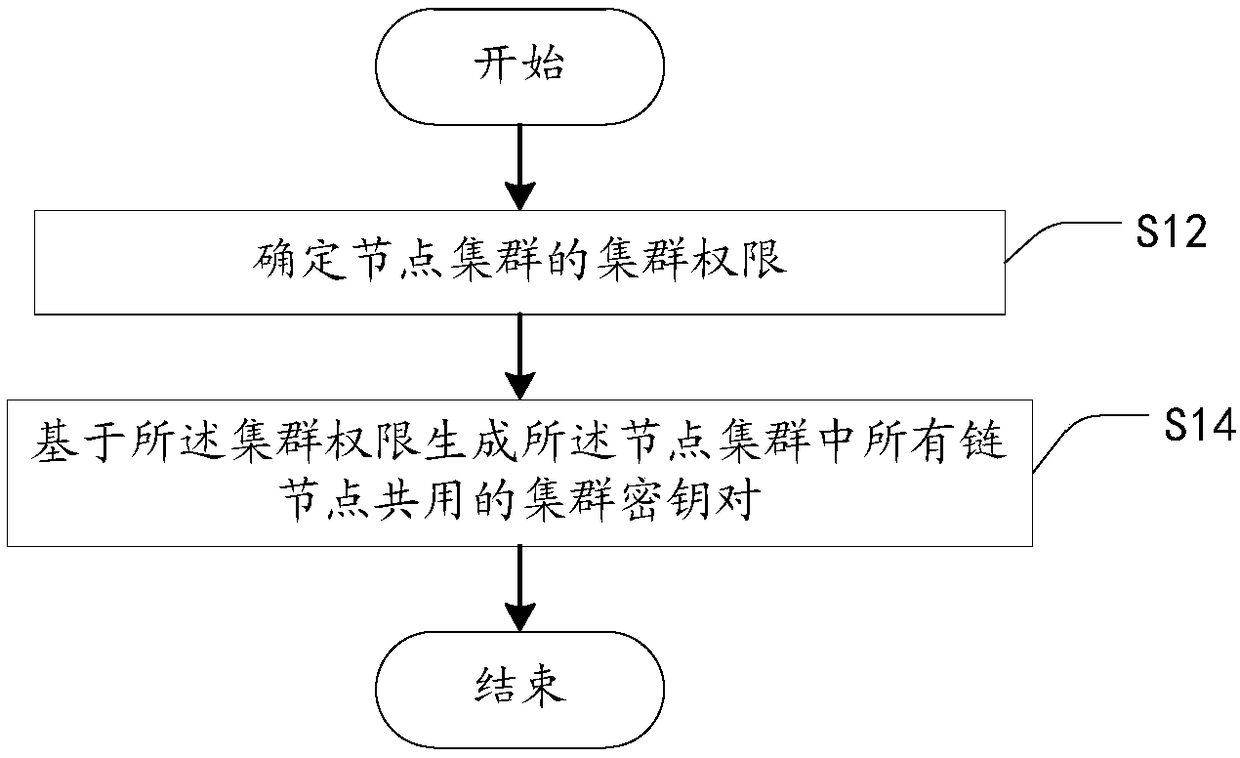
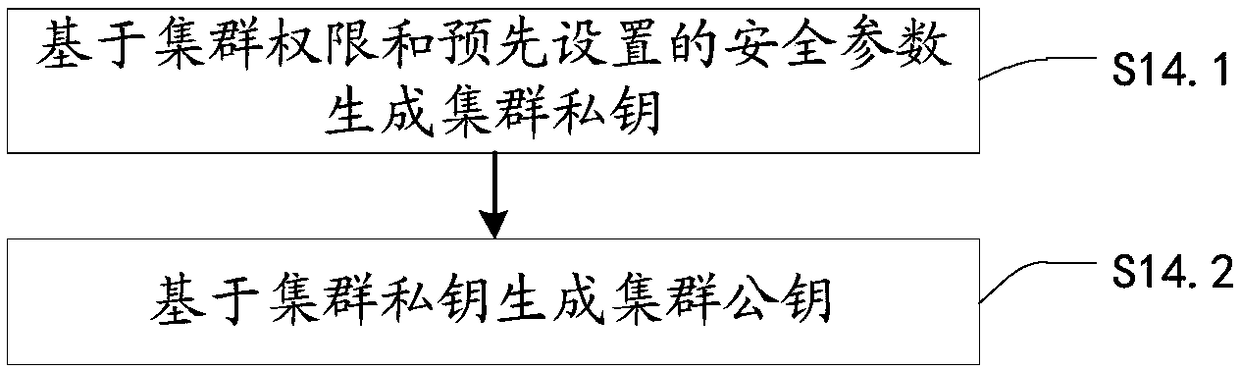
[0036]According to the applicant's research, it is found that the group key management method in the prior art is as follows: the security agent of the first cluster master node sends a key agreement request message containing the key seed to the second cluster master node security agent, so that The second cluster master node security agent responds to the key negotiation request message and sends a key negotiation response message to the first cluster master node security agent and synchronizes the key seed to the second cluster slave node, wherein the key seed is used to generate key; the security agent of the first cluster master node responds to the key negotiation response message and synchronizes the key seed to the first cluster slave node; the first cluster master node security agent judges that the key seed is synchronized to the first cluster slave node and synchronized to Whether the second cluster slave node is successful; if so, the security agent of the first clu...
no. 2 example
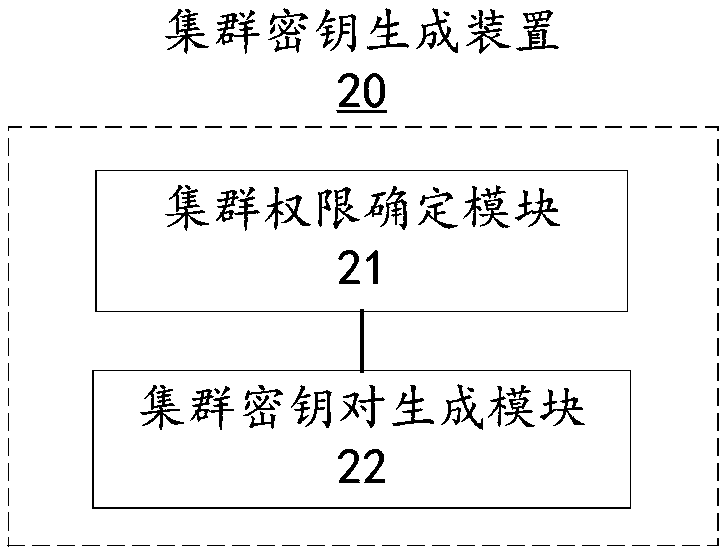
[0064] In order to cooperate with the cluster key generation method provided in the first embodiment of the present invention, the second embodiment of the present invention further provides a cluster key generation device 20 .
[0065] Please refer to image 3 , image 3 It is a schematic diagram of modules of a cluster key generation device 20 provided in the second embodiment of the present invention.
[0066] The cluster key generation device 20 includes a cluster authority determination module 21 and a cluster key pair generation module 22 .
[0067] The cluster authority determination module 21 is used to determine the cluster authority of the node cluster. The node cluster includes at least one chain node of the consortium chain. The cluster authority is used to indicate whether the node cluster has the authority to obtain the corresponding resources in the consortium chain.
[0068] The cluster key pair generation module 22 is configured to generate a cluster key pair ...
no. 3 example
[0075] Please refer to Figure 4 , Figure 4 The third embodiment of the present invention provides a structural block diagram of an electronic device 30 applicable to the embodiments of the present application. The electronic device 30 provided in this embodiment may include a cluster key generating device 20 , a memory 31 , a storage controller 32 , a processor 33 , a peripheral interface 34 , an input and output unit 35 , an audio unit 36 , and a display unit 37 . As an optional implementation manner, the electronic device 30 may be a certain chain node device in the consortium chain.
[0076] The memory 31, storage controller 32, processor 33, peripheral interface 34, input and output unit 35, audio unit 36, and display unit 37 are electrically connected to each other directly or indirectly to realize data transmission or interact. For example, these components can be electrically connected to each other through one or more communication buses or signal lines. The cl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com