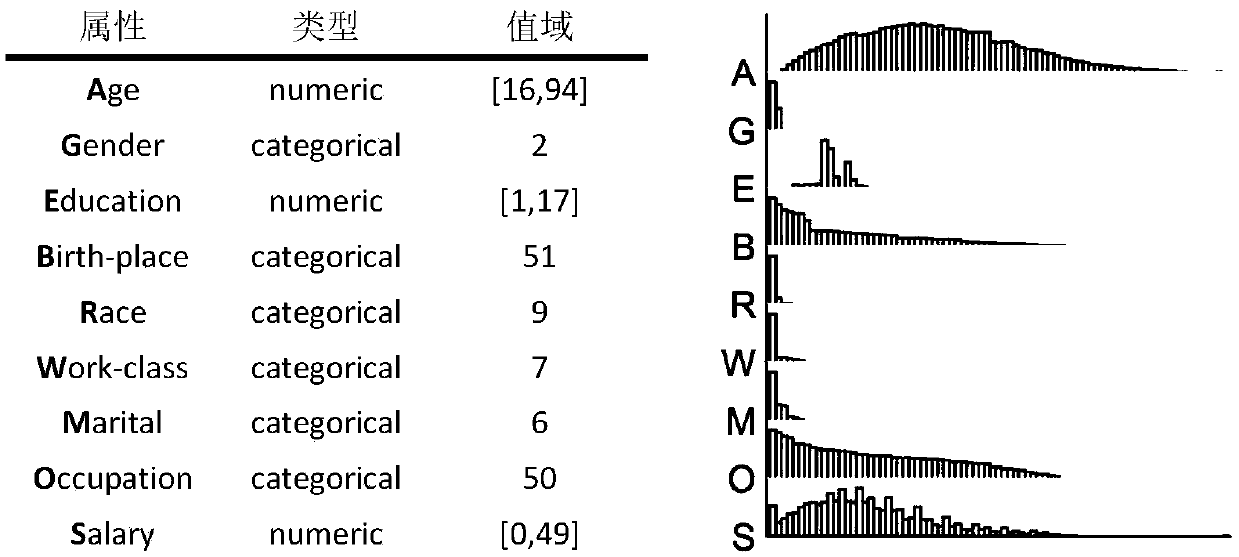
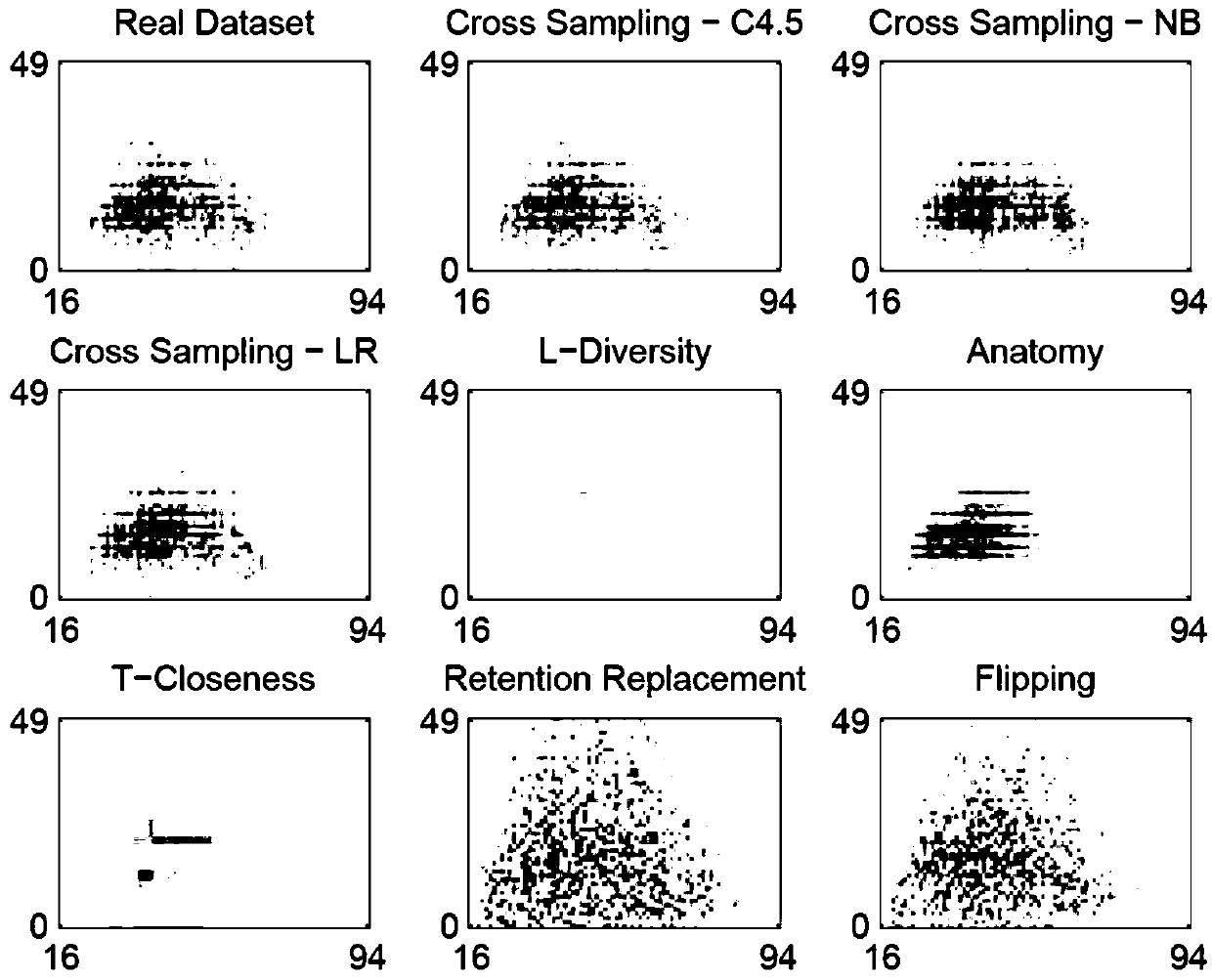
A privacy protection data publishing method based on conditional probability distribution
A technology of conditional probability distribution and data release, which is applied in the field of information security and privacy protection, can solve problems such as restricting the flexibility of data space division, privacy leakage, and large data distribution errors, so as to protect user data privacy, protect data privacy, and control distribution effect of error
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be further introduced below from three aspects: single-sensitive attribute algorithm, multi-sensitive attribute algorithm and multi-sensitive attribute improved algorithm.
[0028] 1. Single sensitive attribute algorithm
[0029] Only the case where the dataset has a sensitive attribute is considered here (ie: d S = 1). The algorithm consists of two stages (see Appendix 1 for the algorithm code).
[0030] In the first stage, each record in the input dataset T is traversed and the corresponding benchmark distribution is calculated. Taking record t as an example, based on the conditional probability distribution p(A S |A QI ), learn the prior knowledge model M from the dataset T\{t} (t) , and M (t) (A S|t[A QI ]) as the benchmark distribution for record t;
[0031] In the second stage, using the benchmark distribution M (t) (A S |t[A QI ]), randomly sample a sensitive attribute value for each record, and replace the original sensitiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com