A method and system for identity authentication on blockchain
A block chain, technology to be certified, applied in the field of block chain, can solve the problems of low security level, copying and embezzlement, no fixed storage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] This embodiment provides a method for identity authentication on a blockchain, which is applicable to a system including an authentication device, an application program, a server, and a blockchain network. The blockchain network includes multiple blockchain nodes, each A blockchain node corresponds to a member of an alliance organization; methods include:
[0036] Step s1: the application obtains the device identifier and data to be authenticated of the connected authentication device;
[0037] Step s2: the application program sends the device identifier and data to be authenticated to the server;
[0038] Step s3: The server sends a request for querying the ledger of the blockchain node to any blockchain node in the blockchain network; the request for querying the ledger of the blockchain node includes the device identifier;
[0039] Step s4: The block chain node obtains the authentication associated data corresponding to the device identifier in the query block chai...
Embodiment 2
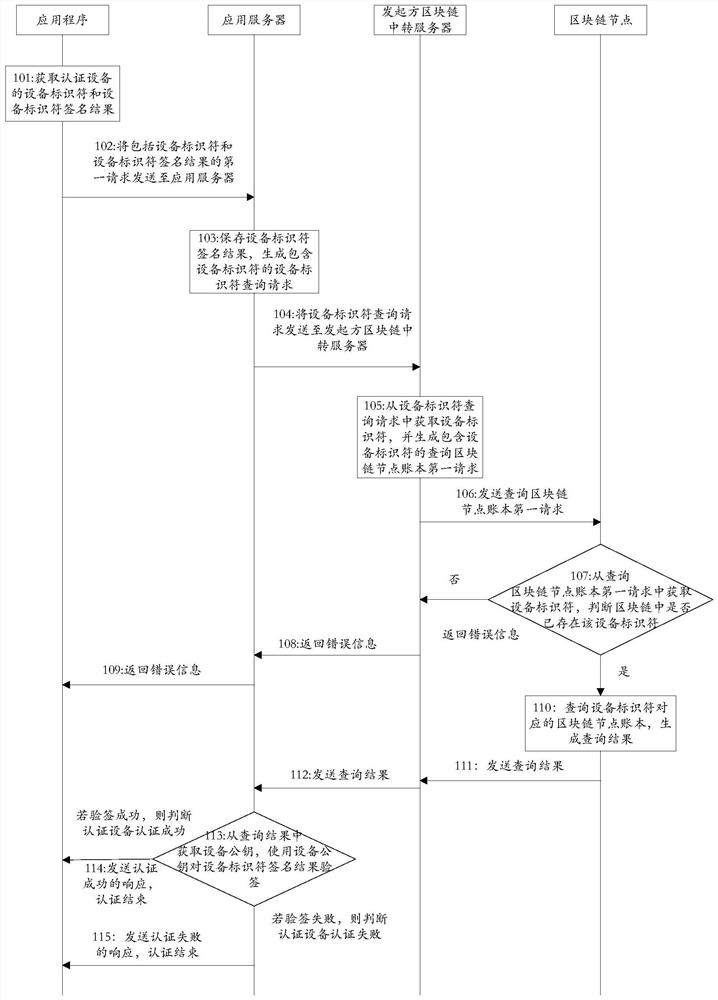
[0101] The second embodiment provides a method for identity authentication on the block chain, such as figure 1 Shown:
[0102] Step 101, the application program obtains the device identifier of the authentication device and the signature result of the device identifier;
[0103] Example: DT is 1000 0000 0000 0000.
[0104] After step 101, it may also include: the application program uses the device identifier to query whether there is an authentication status identifier that matches the device identifier in the program database, and obtains the authentication status of the authentication device according to the authentication status identifier, if the first preset authentication status identifier If the data at the position is the first preset value, it is determined that the authentication device has completed the authentication, and the process ends; otherwise, it is determined that the authentication device has not completed the authentication, and step 102 is performed. ...
Embodiment 3
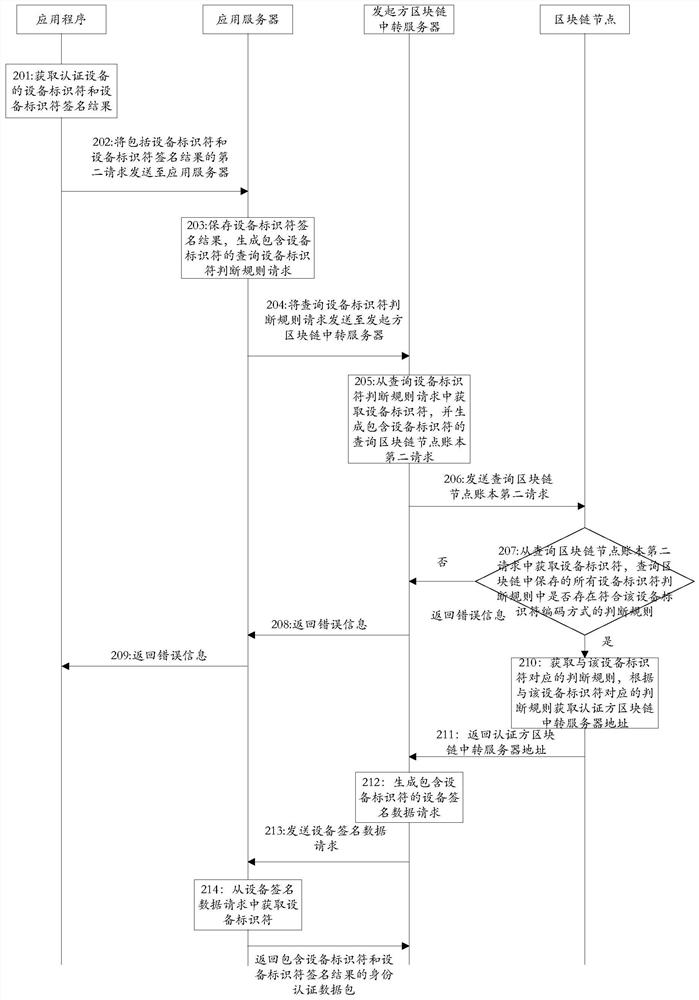
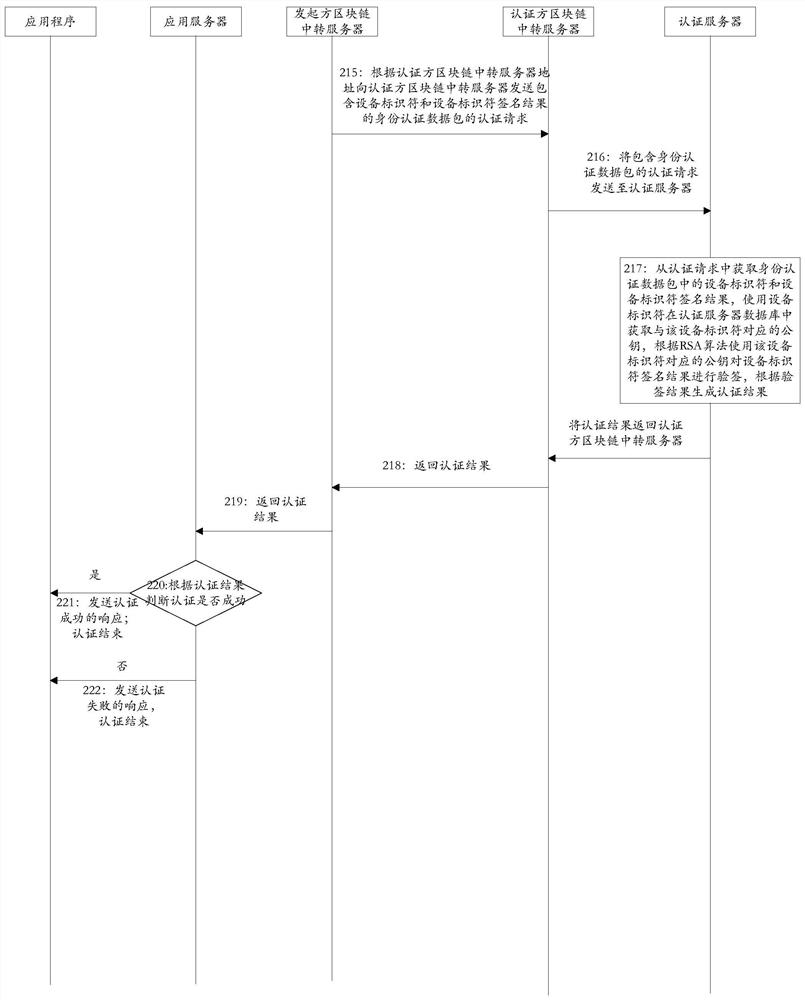
[0134] The third embodiment provides a method for identity authentication on the block chain, such as figure 2 Shown:
[0135] Step 201, the application program obtains the device identifier of the authentication device and the signature result of the device identifier;
[0136] In this embodiment, the device identifier can be: 2000 0000 0000 0000;
[0137] After step 201, it may also include: the application program uses the device identifier to query whether there is an authentication status identifier that matches the device identifier in the program database, and obtains the authentication status of the authentication device according to the authentication status identifier, if the first preset authentication status identifier If the data at the position is the first preset value, it is determined that the authentication device has completed the authentication, and the process ends; otherwise, it is determined that the authentication device has not completed the authenti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com