Data de-identification method, data de-identification apparatus and computer readable storage medium
A technology for converting devices and data, applied in the field of non-volatile computer-readable storage media, and can solve the problems of unable to identify specific individuals and infringing on personal privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
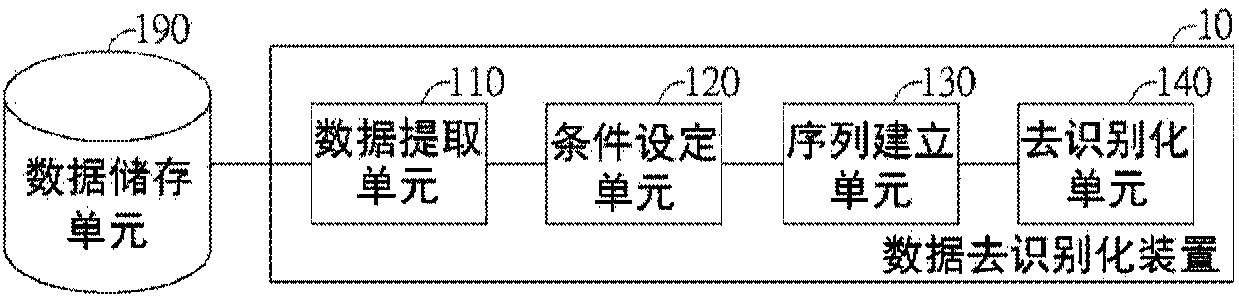
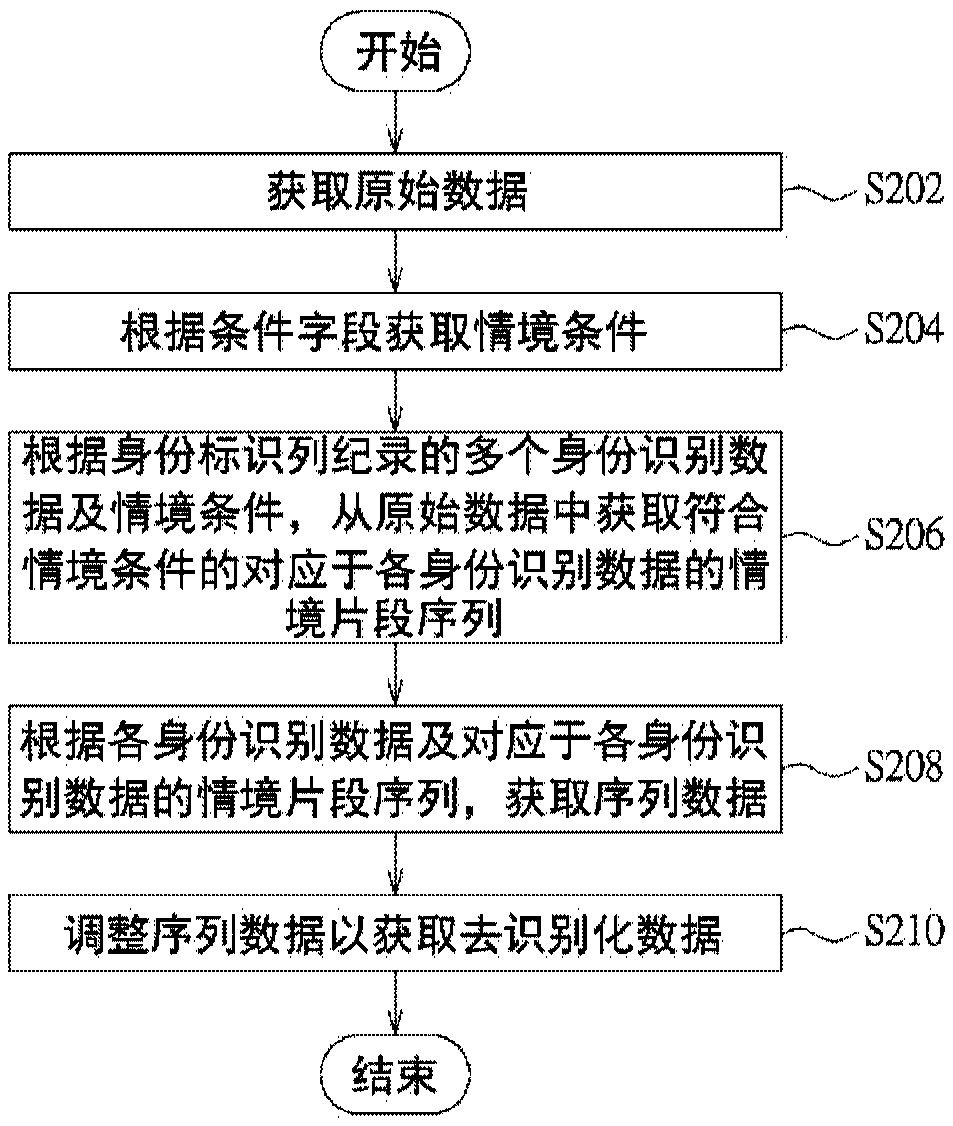
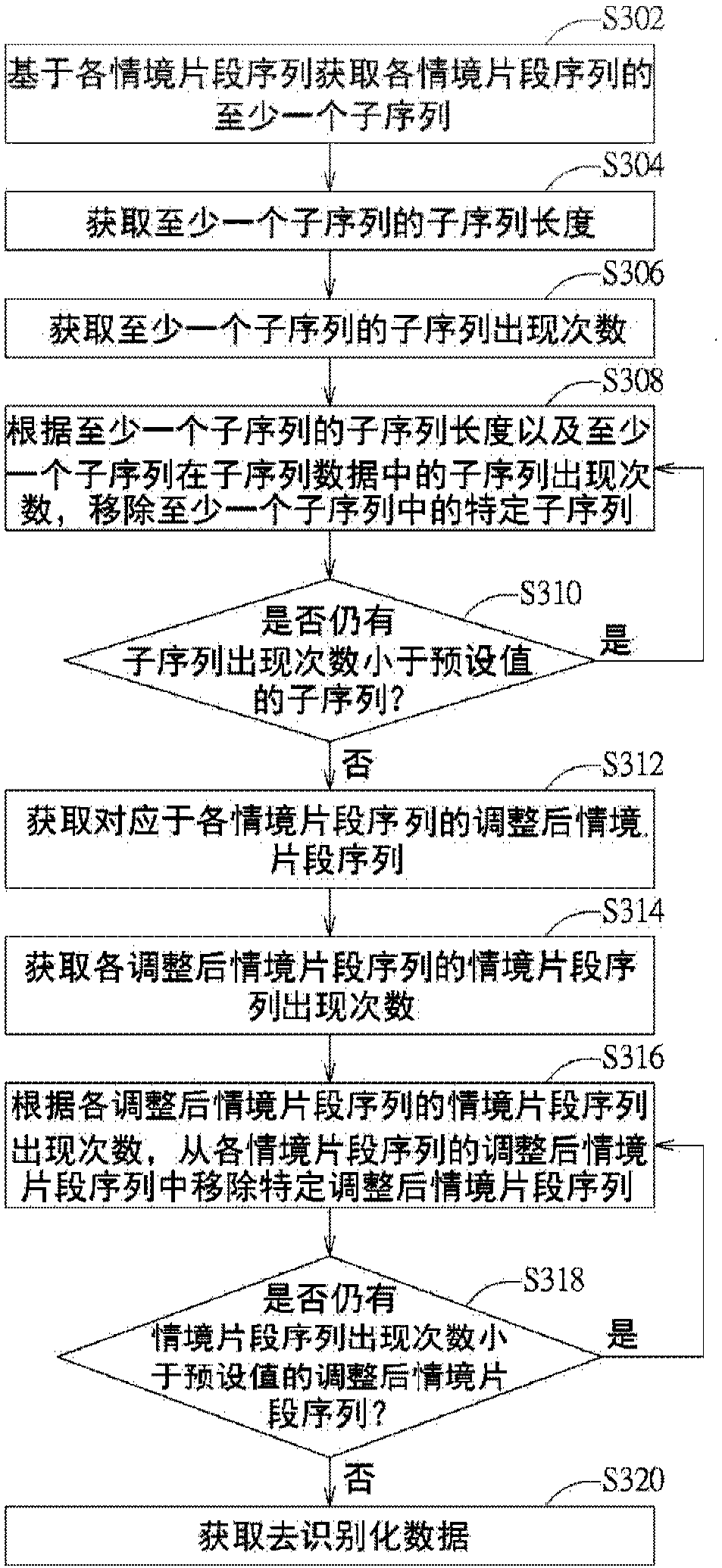
[0021] Various embodiments are proposed below for detailed description. However, the embodiments are only used as examples for illustration and will not limit the scope of protection of the present invention. In addition, some components are omitted from the drawings in the embodiments to clearly show the technical characteristics of the present invention. The same reference numbers will be used throughout the drawings to refer to the same or similar components.
[0022] The rapid development of the network makes information sharing easier and faster. However, data sharing raises user privacy concerns. Malicious users can obtain the user's real life situation by analyzing the data and the correlation between the data, which may cause the user's real loss.
[0023] k-anonymity (k-anonymity) technology is a mechanism to protect data privacy. The k-anonymity technology de-identifies the data before the data is released, so that at least k-1 data in the data cannot be distingui...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com