Patents
Literature
65 results about "De-identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
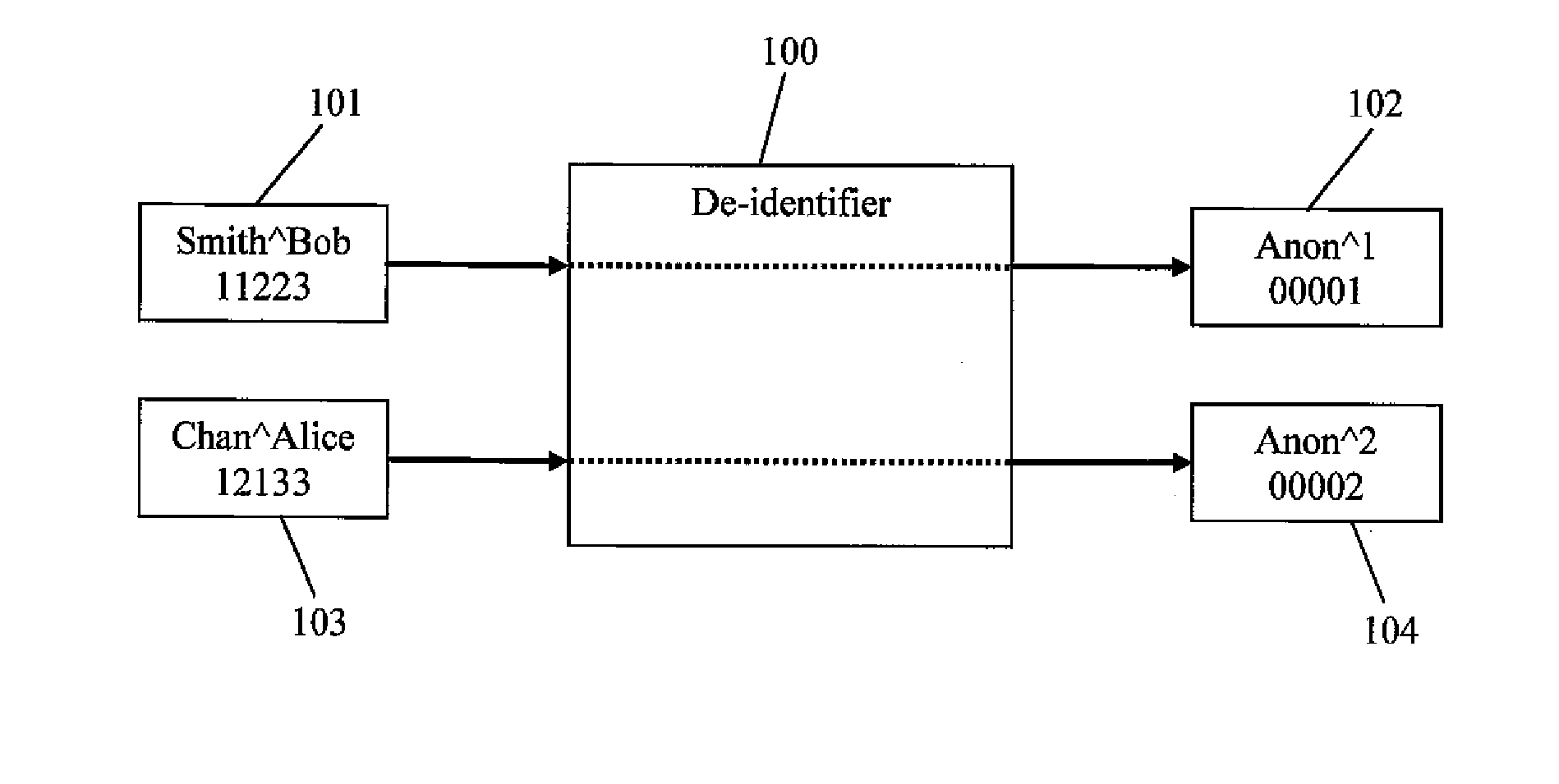
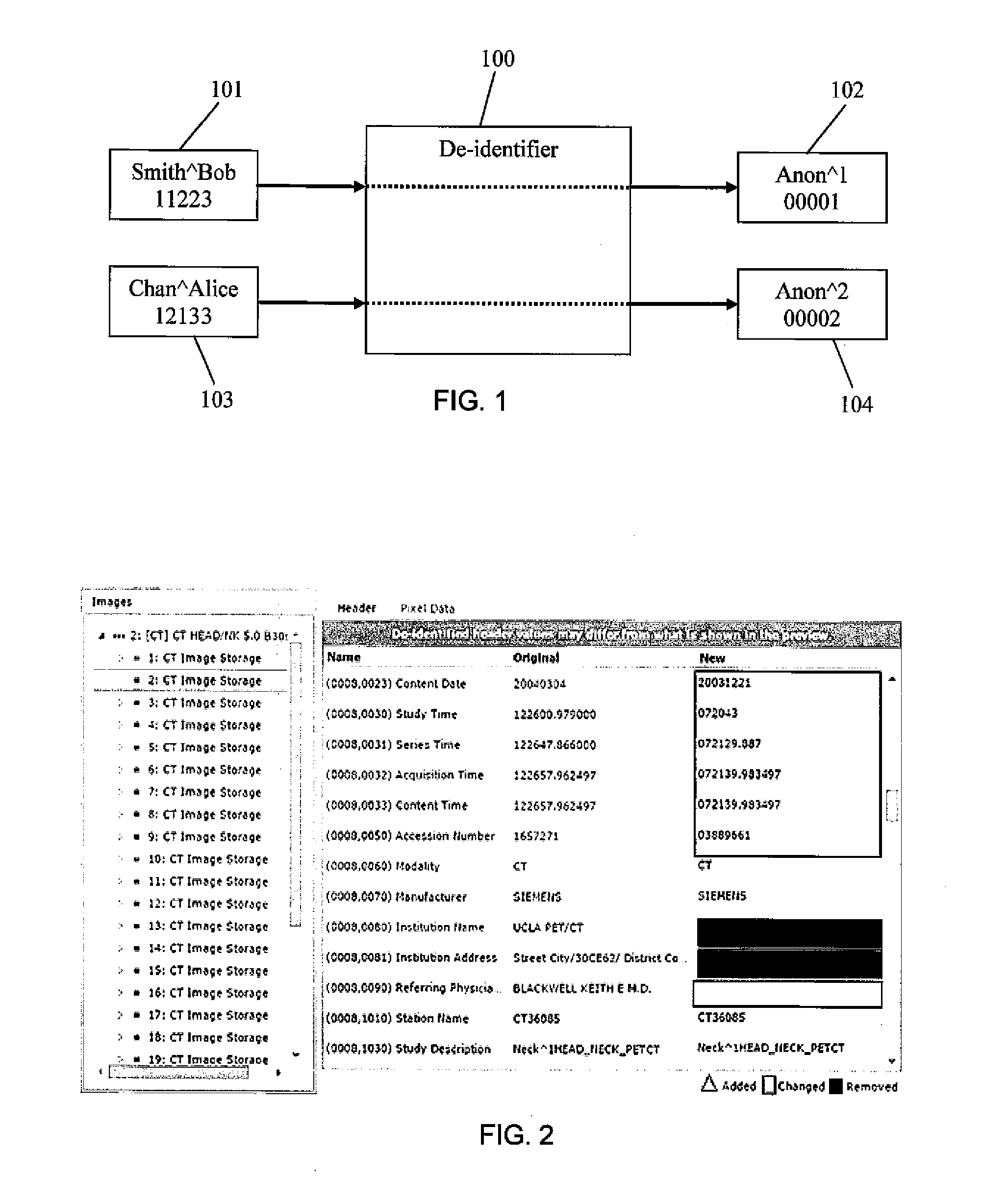
De-identification is the process used to prevent someone's personal identity from being revealed. For example, data produced during human subject research might be de-identified to preserve privacy for research participants.
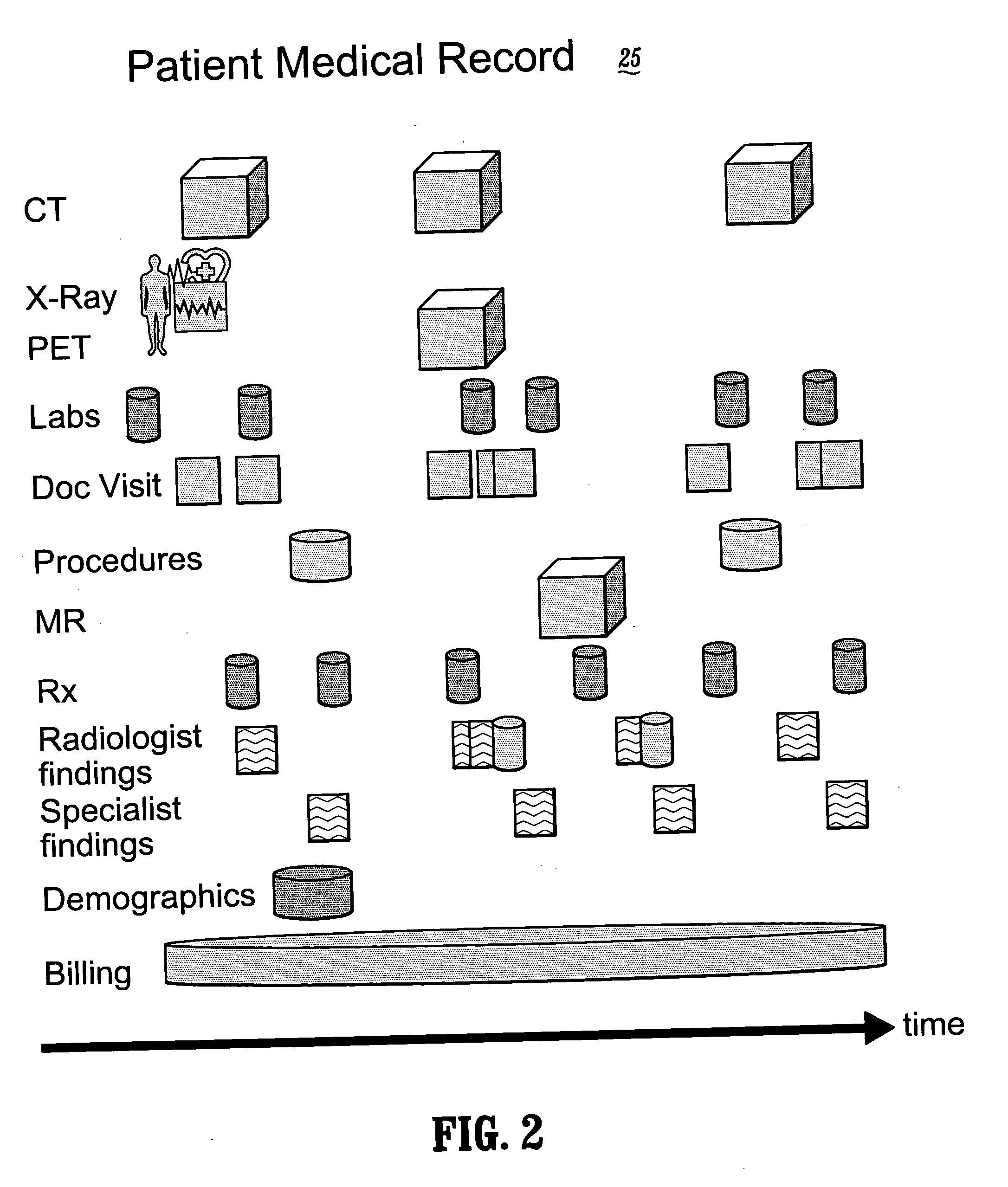
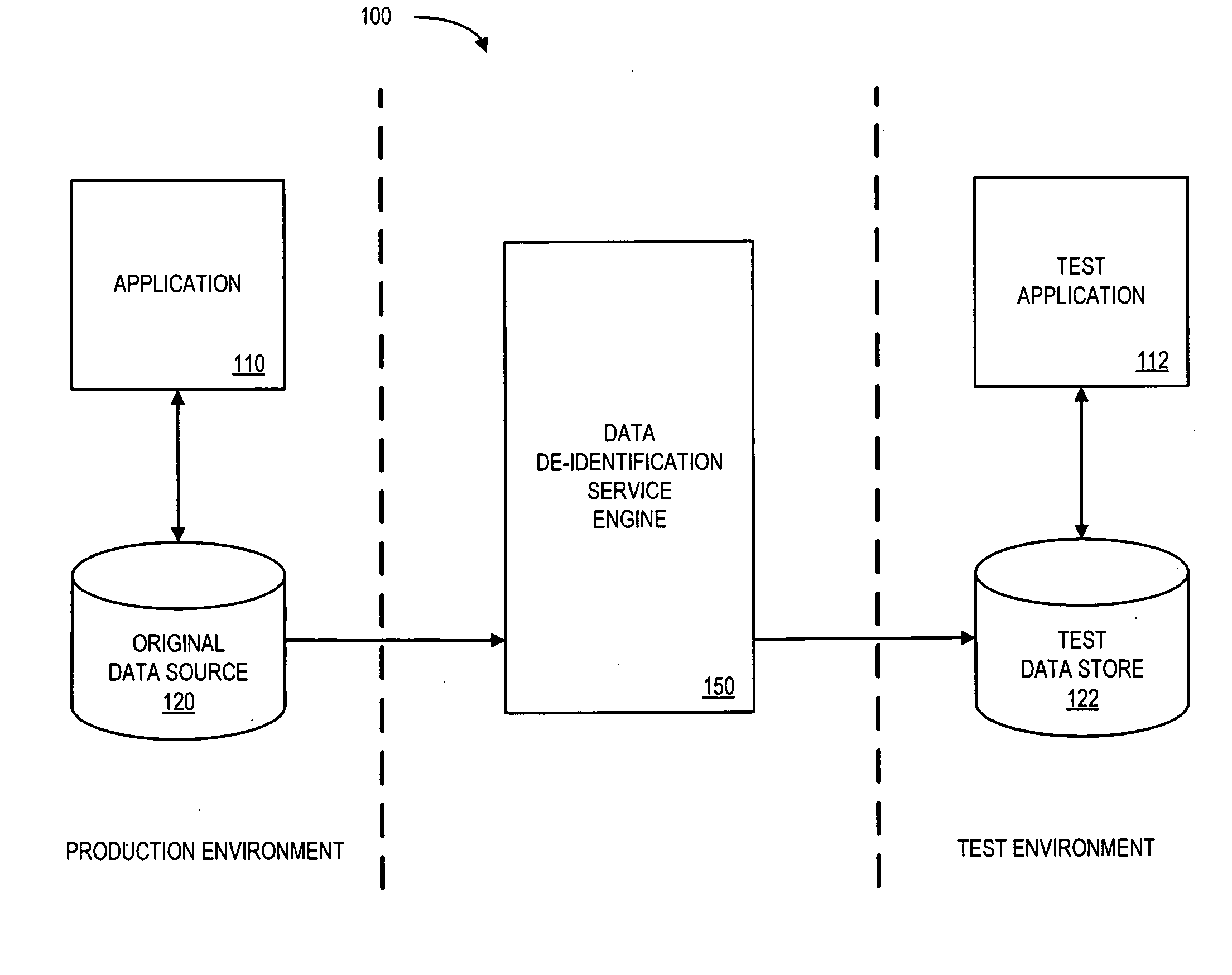
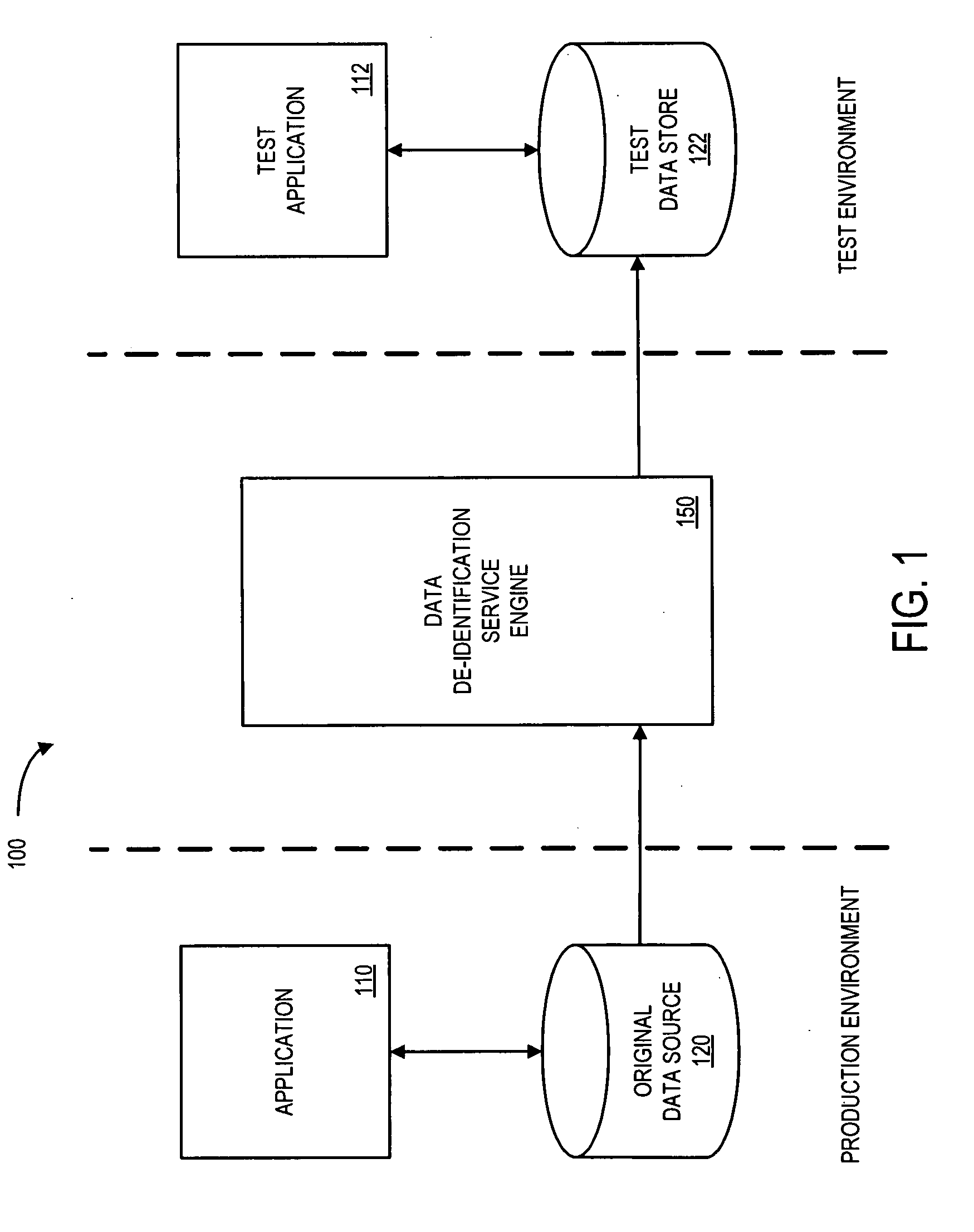
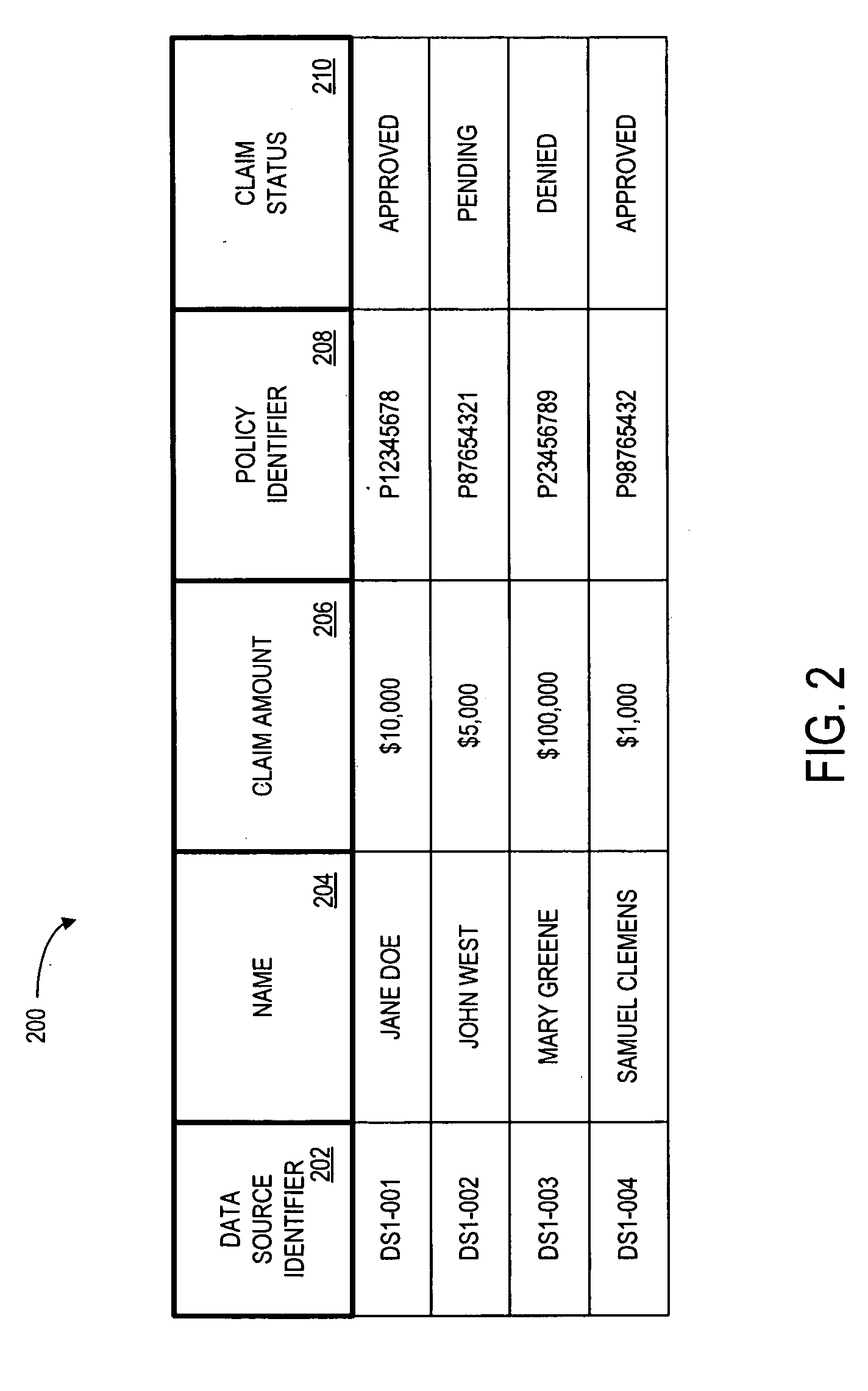
System and method for controlling access and use of patient medical data records
InactiveUS20050236474A1Prohibitive to printComputer security arrangementsPatient personal data managementConfidentialityPatient database
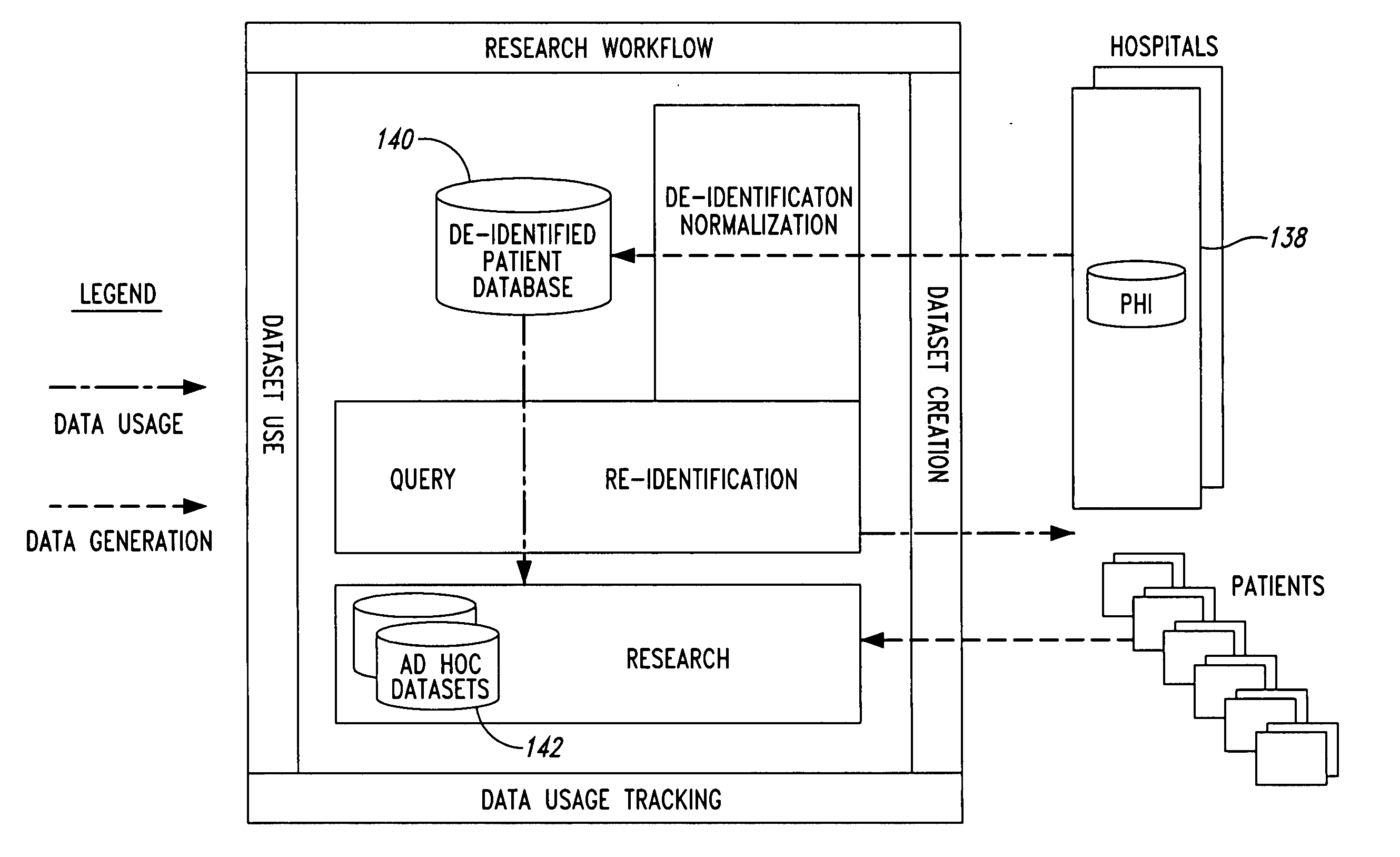
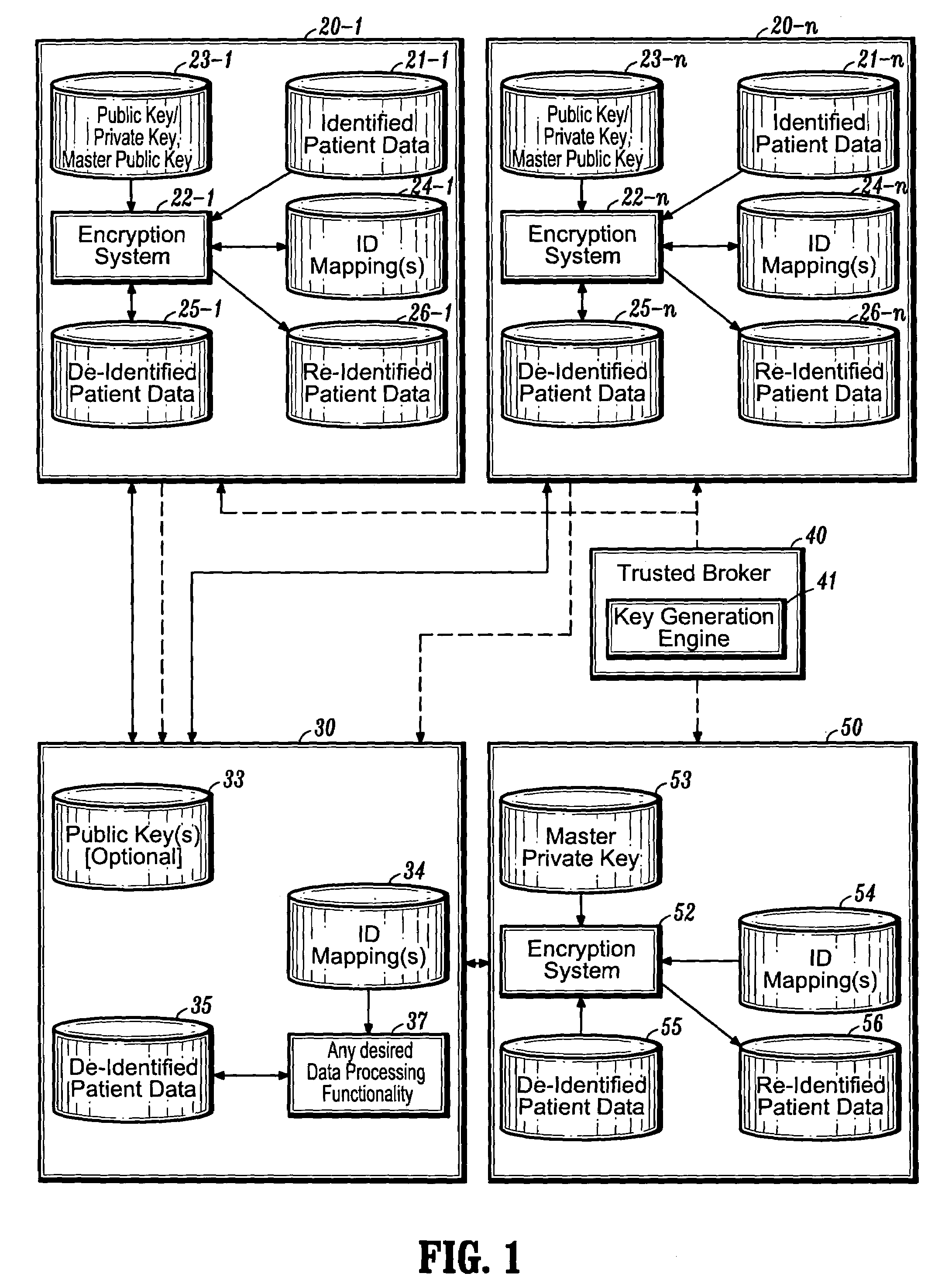
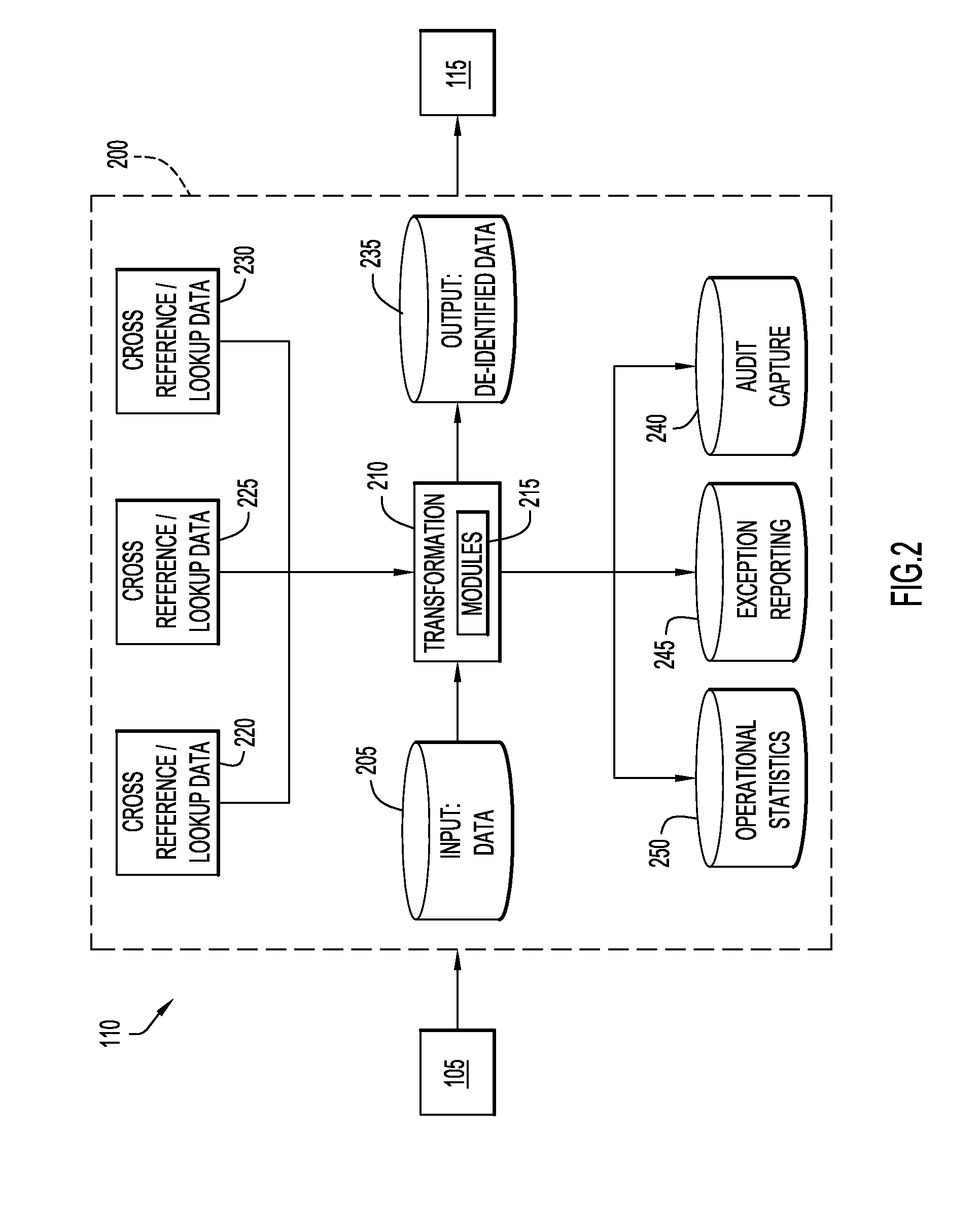
A system for processing patient health information (PHI) protects the confidentiality of PHI to achieve regulatory compliance. The PHI contains patient medical data and associated patient identification data. A de-identification agent extracts patient medical data and separates from all identification data to create de-identified patient data. A key is generated that allows subsequent reassociation of the patient medical data and the patient identification data. The de-identified patient data base may be queried for patient screening purposes. Patient queries are processed only if the study or patient screening has been authorized by appropriate authorities, such as an internal review board. Patients whose medical characteristics conform with the patient query are selected for possible use in a study. If re-identification of the selected patients is necessary, and authorized, the key may be used to provide the necessary reassociation. A data log records all access to patient data.
Owner:CONVERGENCE CT
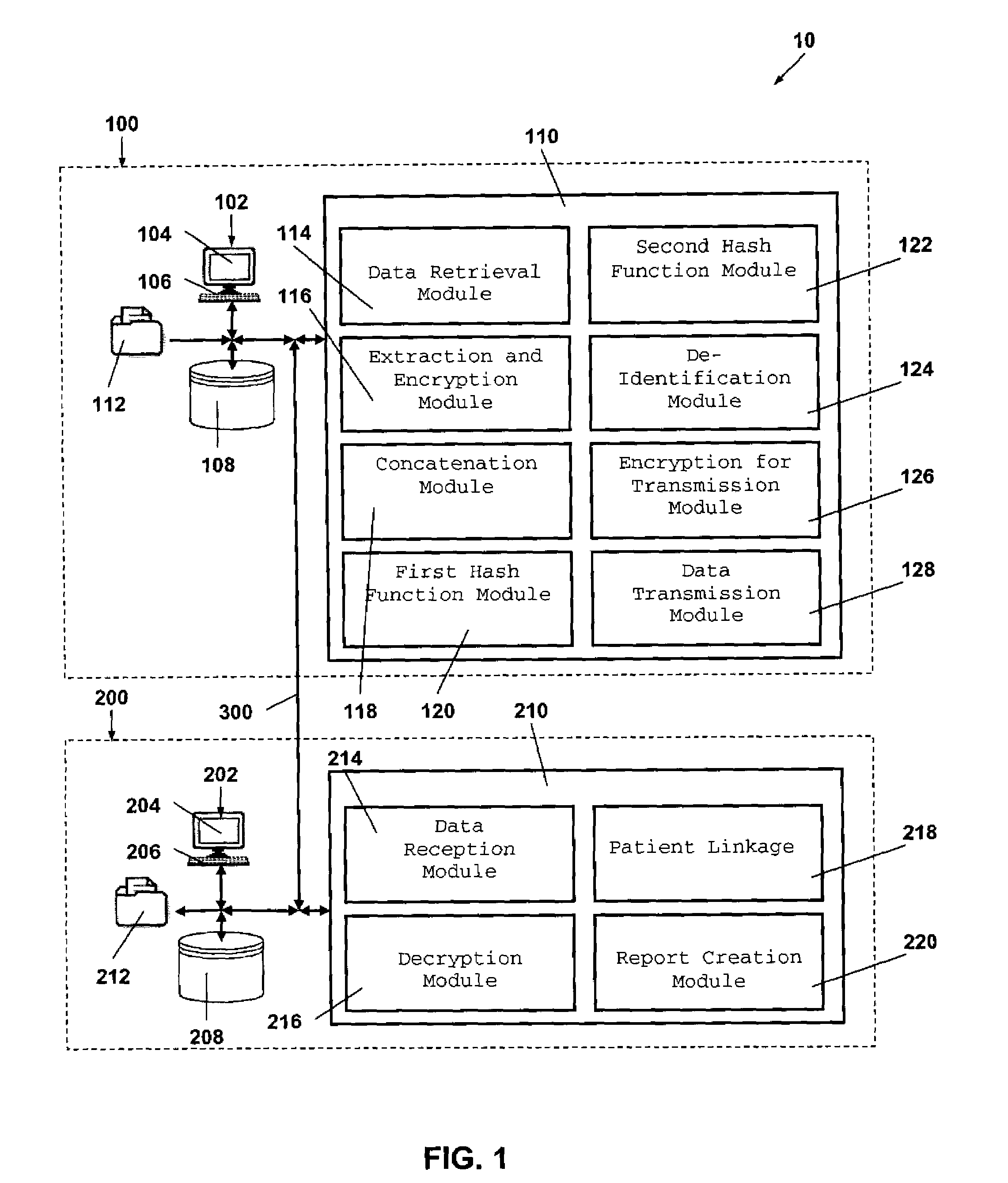
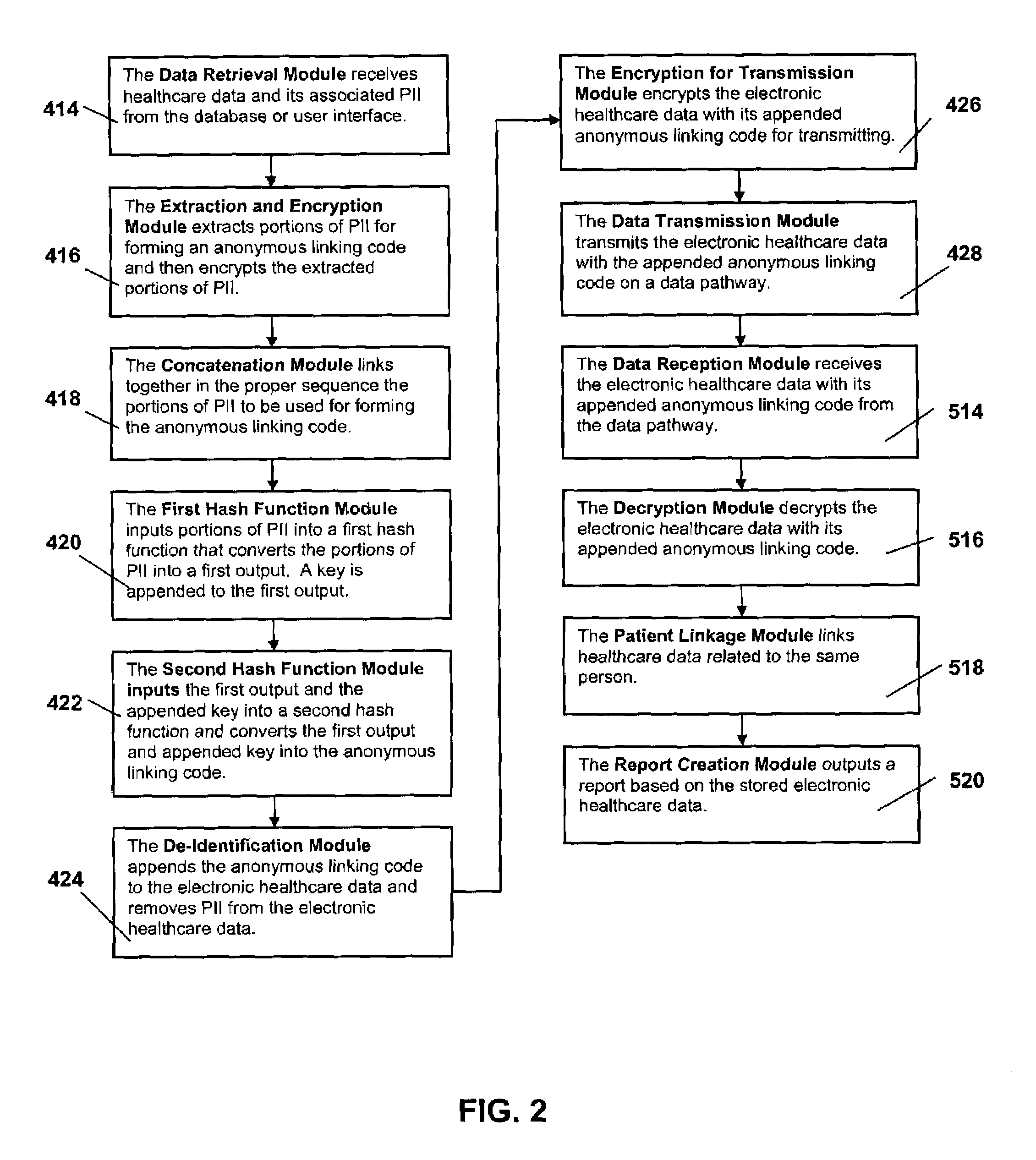
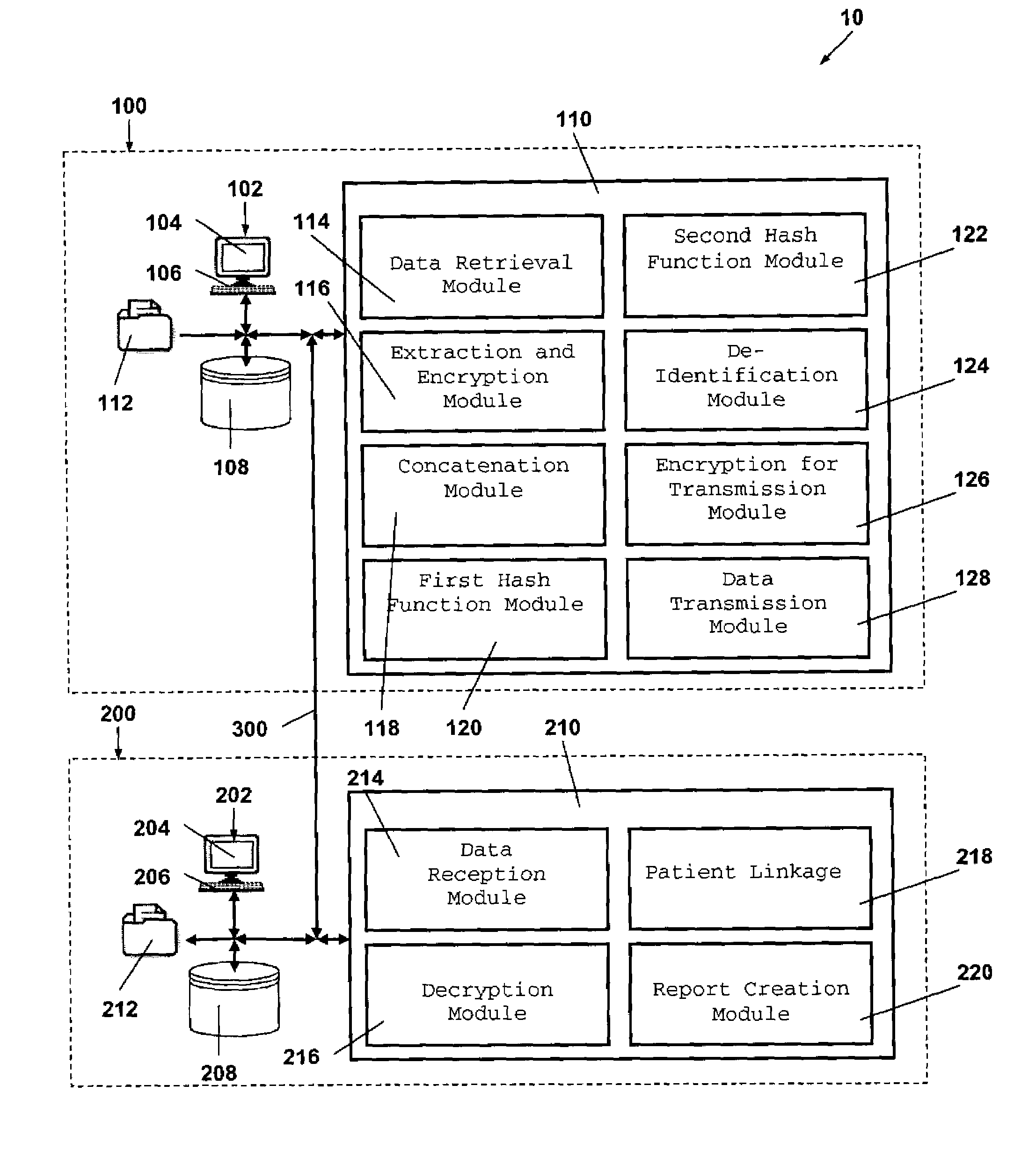
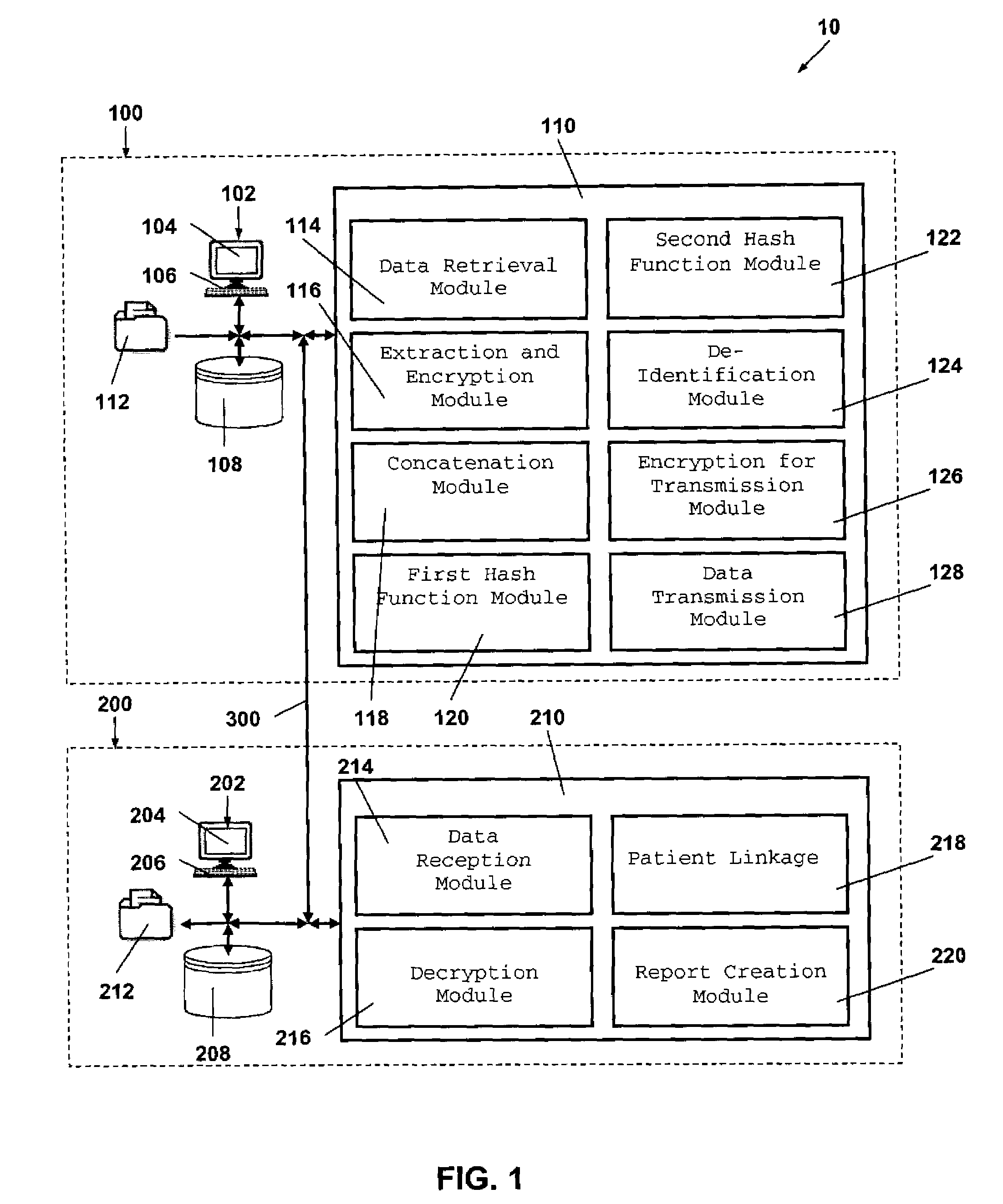
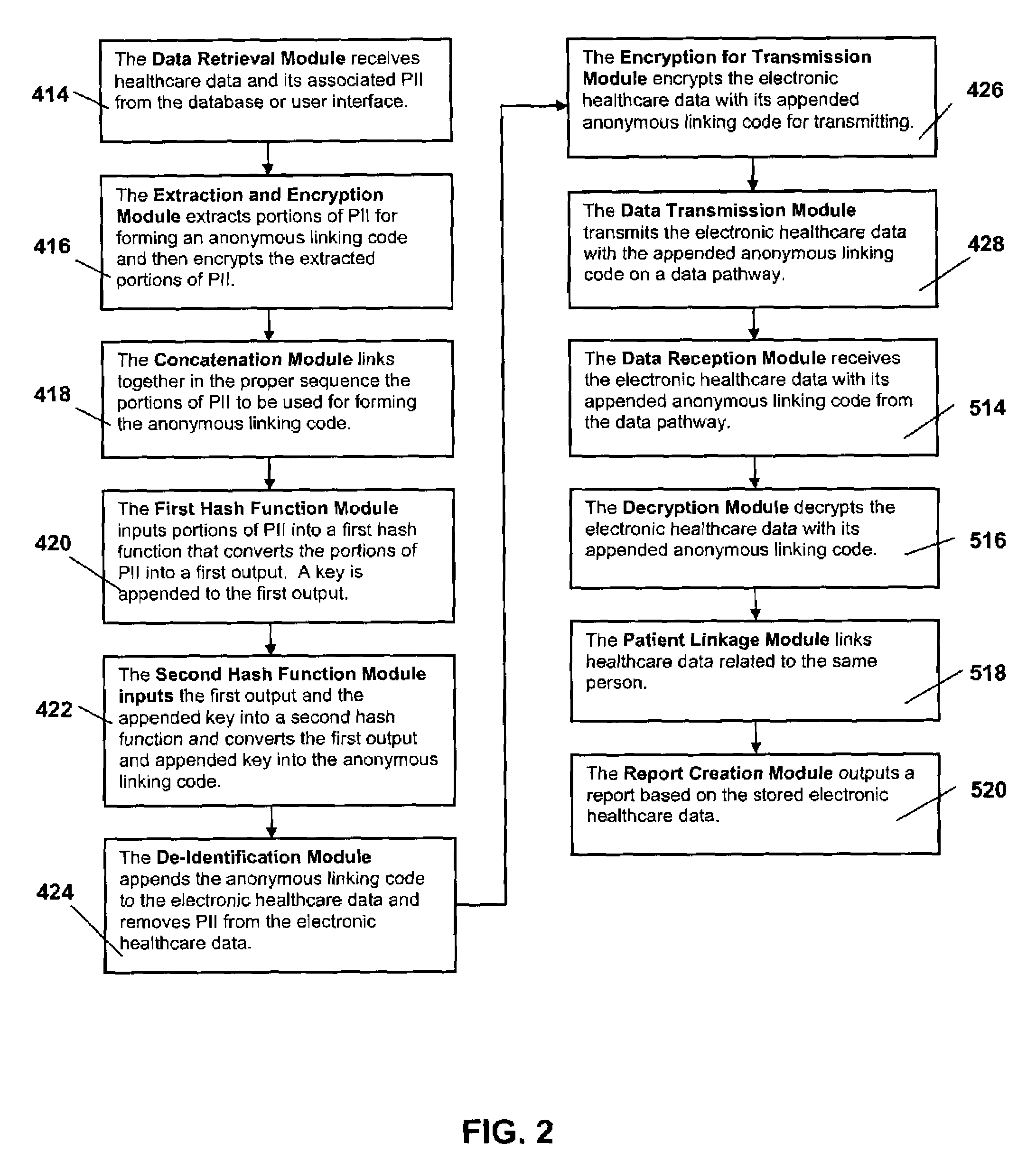
System and method for the protection and de-identification of health care data
ActiveUS20080147554A1Computer security arrangementsPatient personal data managementHash functionInternet privacy
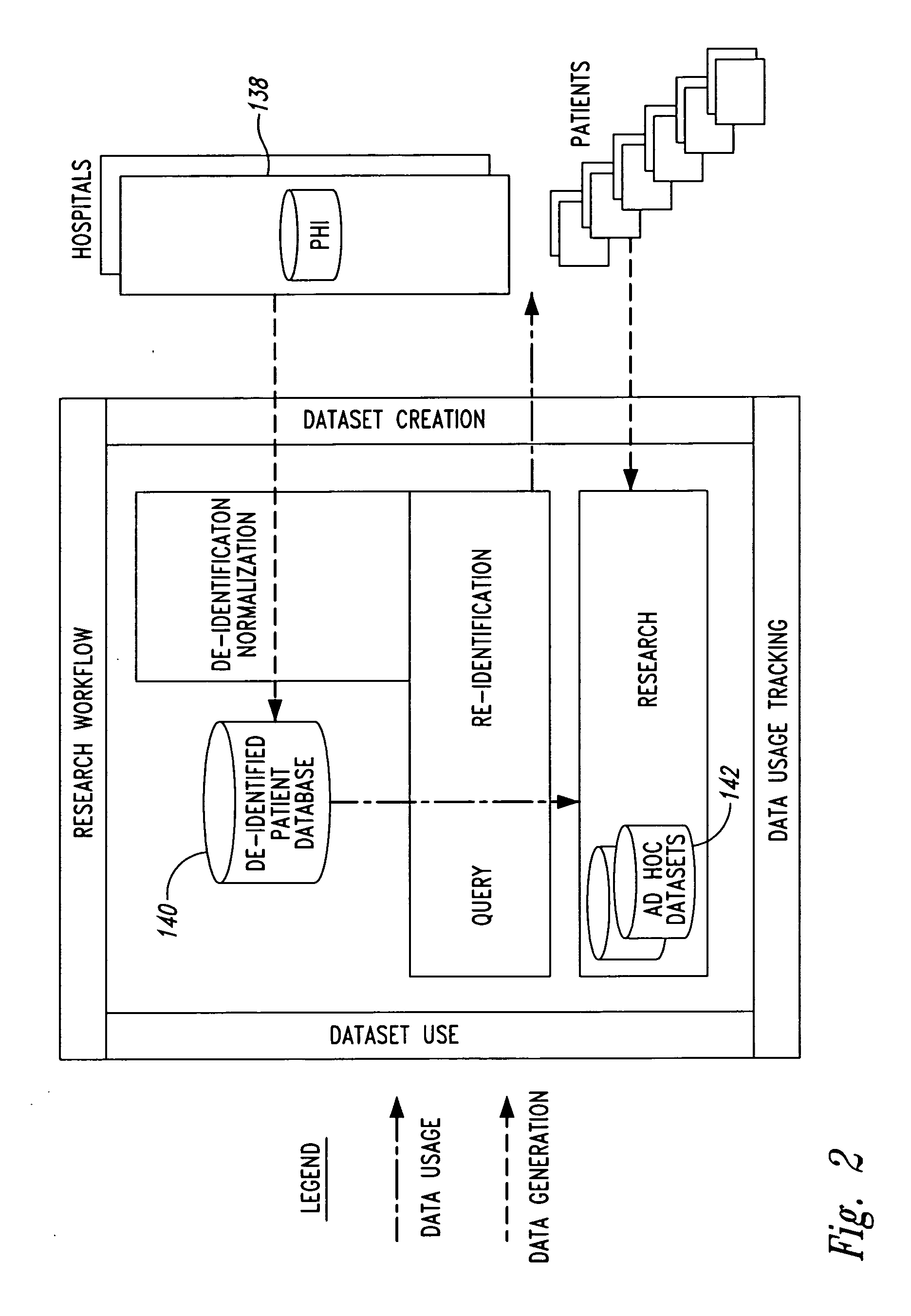
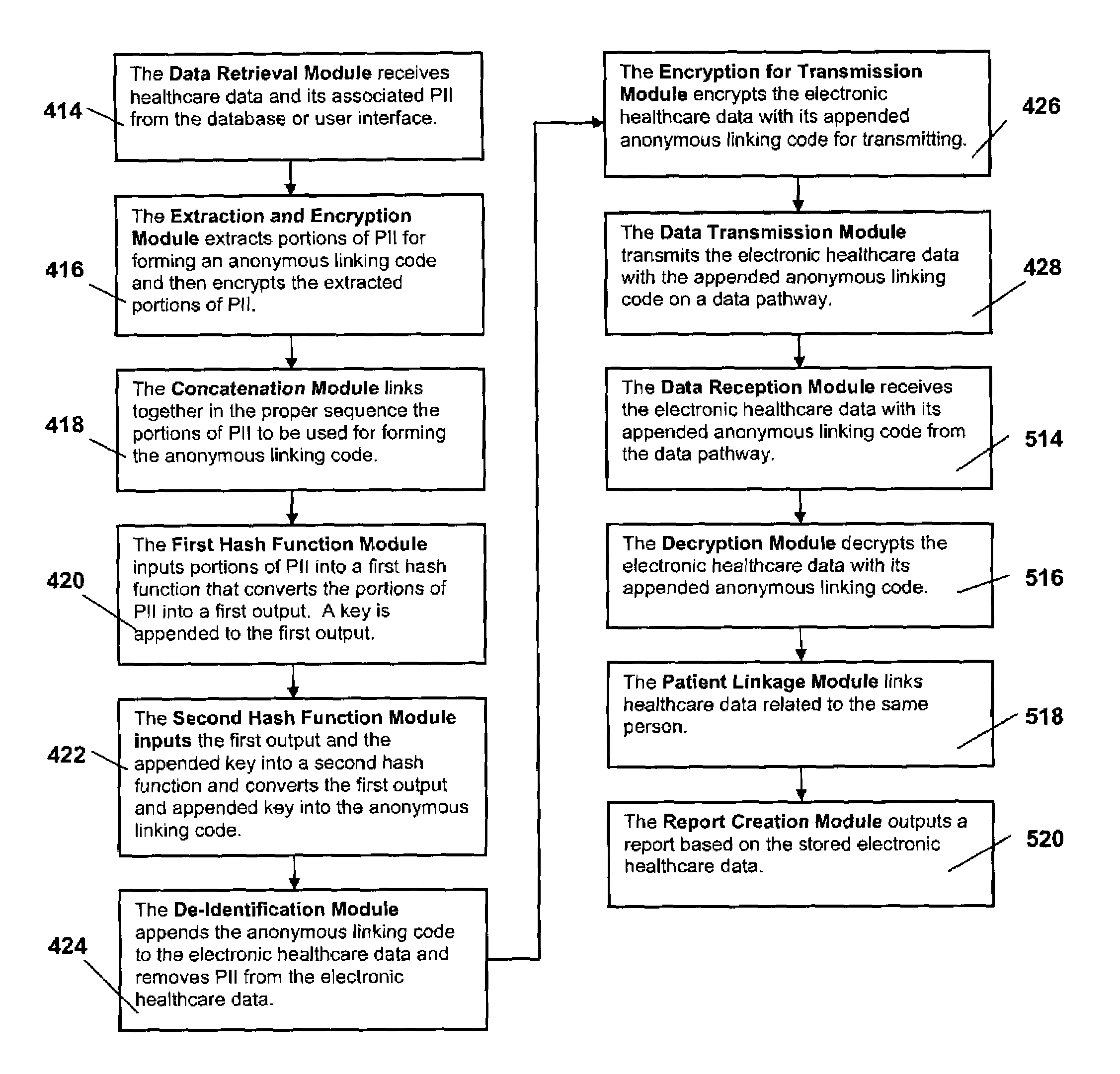
A system for protecting and de-identifying healthcare data includes a storage device for storing the healthcare data and personally identifiable information for a person and a processor in communication with the database. The processor generates an anonymous linking code using a keyed hash function and a second hash function. The anonymous linking code is based at least in part on a portion of the personally identifiable information. The processor further appends the anonymous linking code to the healthcare data for the person.
Owner:IQVIA INC
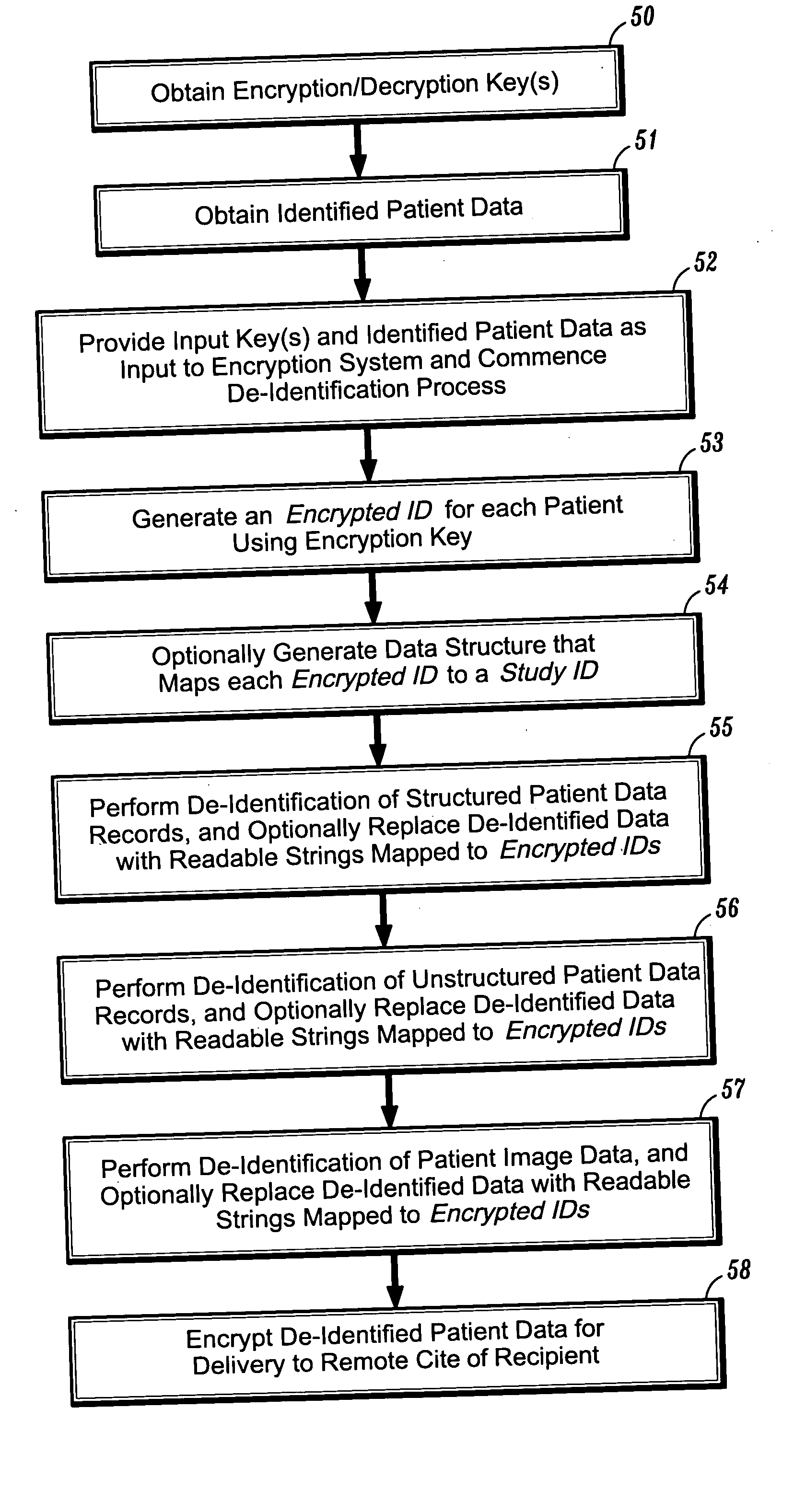
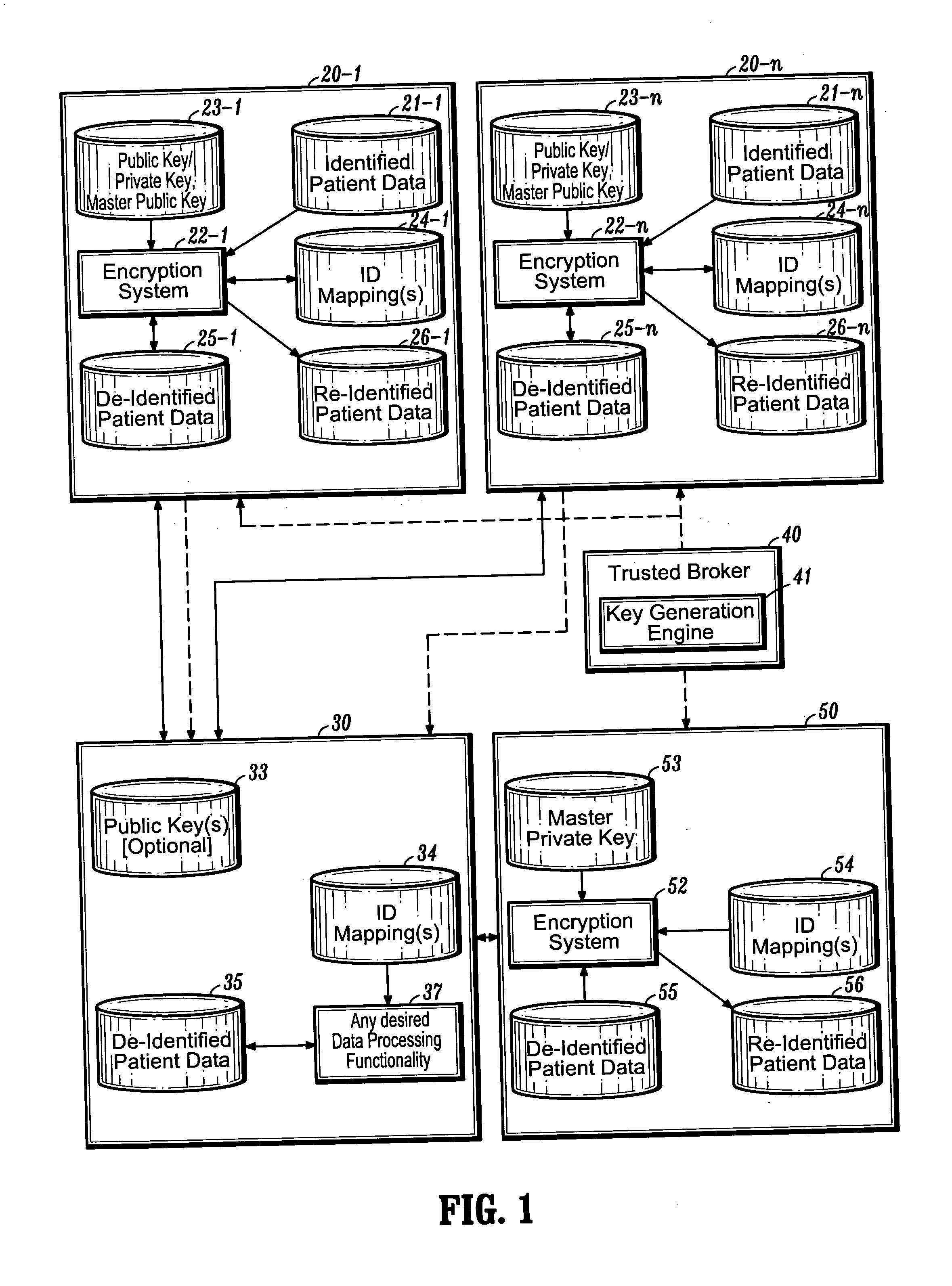
Systems and methods for encryption-based de-identification of protected health information
ActiveUS20050165623A1Ensuring privacyData processing applicationsMultiple keys/algorithms usagePatient dataProtected health information
Systems and methods are provided for protecting individual privacy (e.g., patient privacy) when individual data records (e.g., patient data records) are shared between various entities (e.g., healthcare entities). In one aspect, systems and methods are provided which implement secured key encryption for de-identifying patient data to ensure patient privacy, while allowing only the owners of the patient data and / or legally empowered entities to re-identify subject patients associated with de-identified patient data records, when needed.
Owner:CERNER INNOVATION
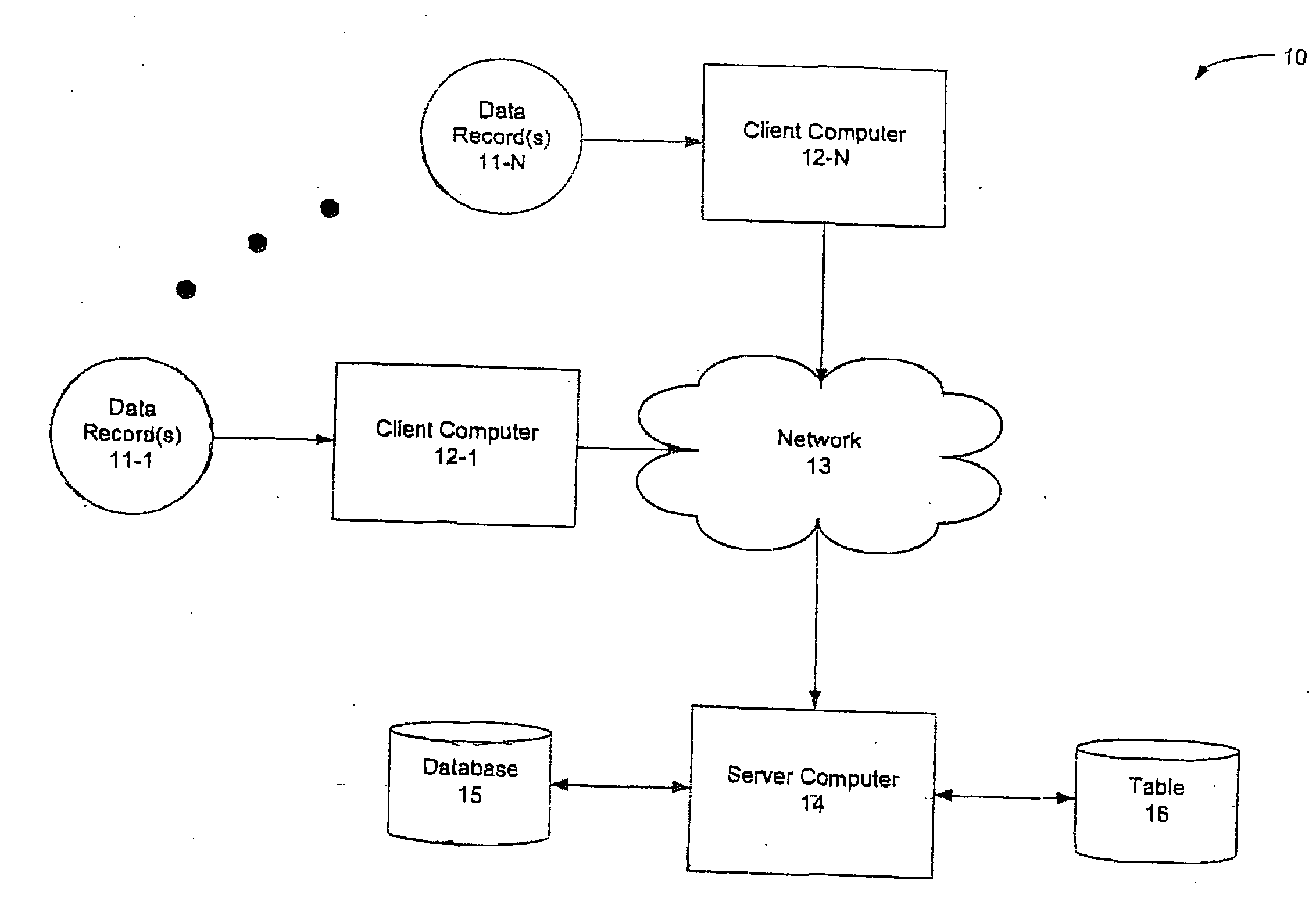
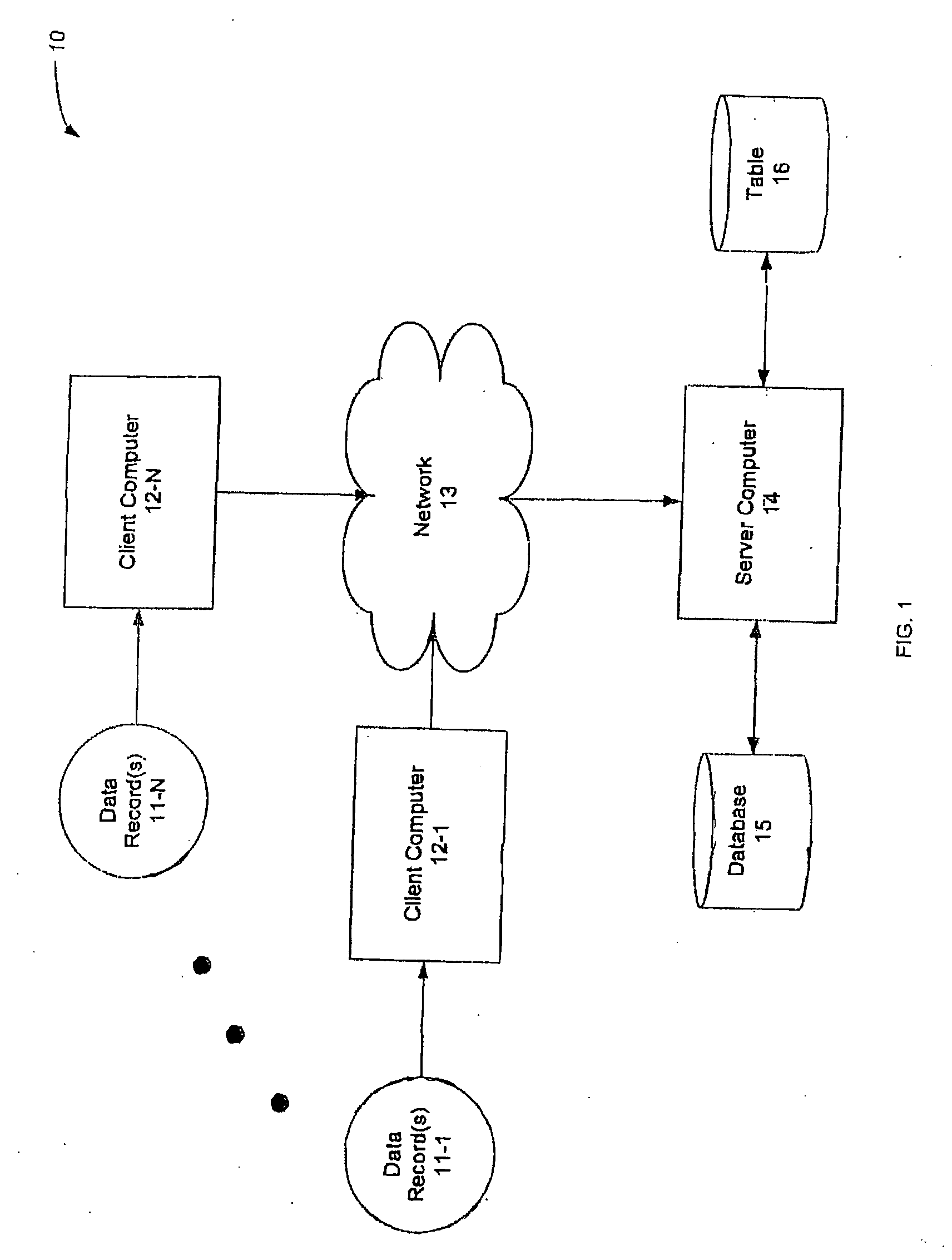
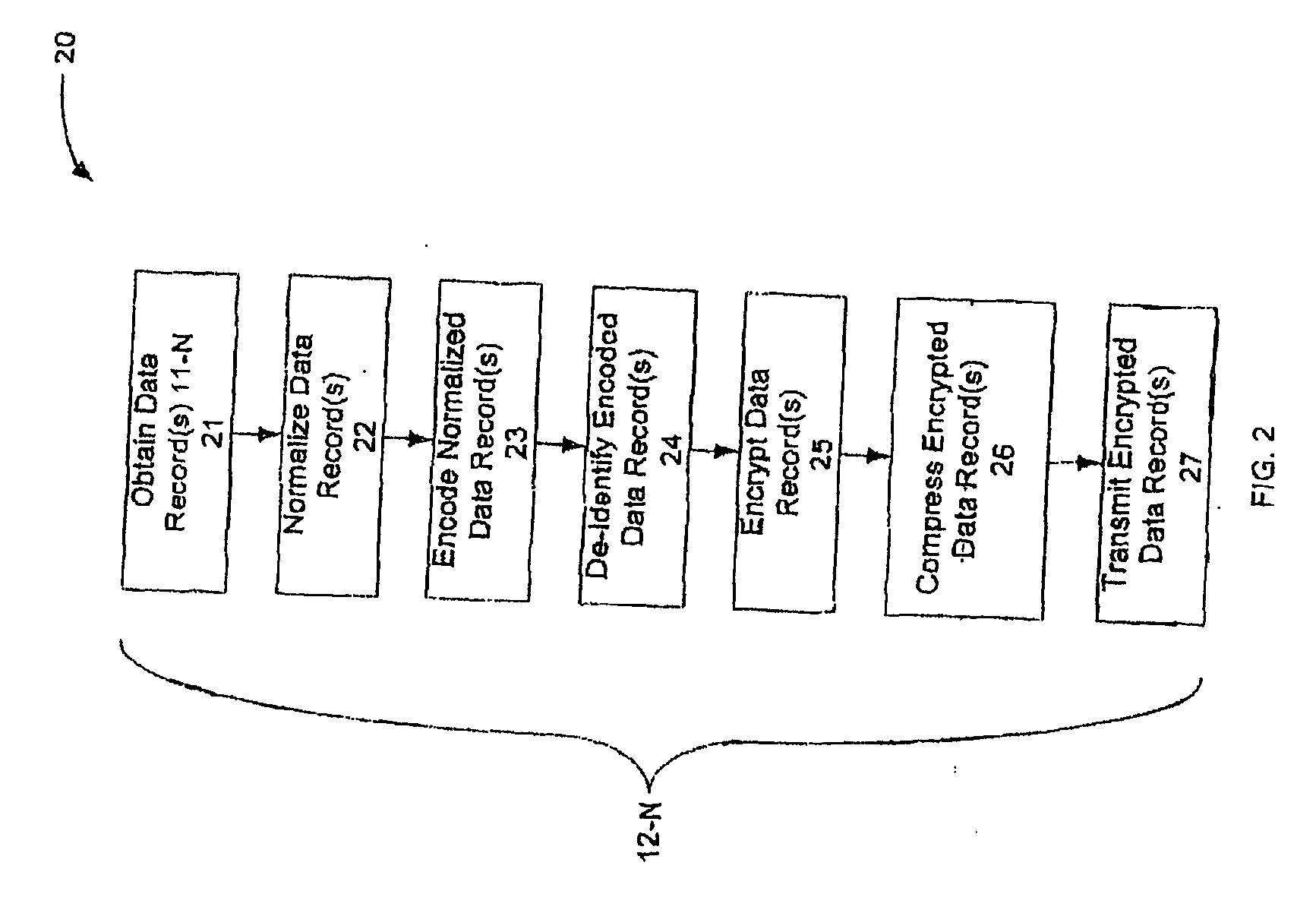
De-identification and linkage of data records
InactiveUS20060020611A1Improve protectionDigital data information retrievalDigital data processing detailsClient-sideDe-identification
Apparatus and method for creating de-identified and linked records is described. More particularly, data records are de-identified at a client computer. De-identification includes field-level one-way encryption. De-identified records may then be sent to a server computer for linkage. Linkage is done using match codes created for such data records at the client computer. The server computer is configured to provide longitudinal linkage of de-identified client records to de-identified master records. In this manner, privacy may be maintained at the client computer prior to transmission of information, and longitudinal linkage of records may occur without exposing personally identifying information.
Owner:PROFESSIONAL SOLUTIONS
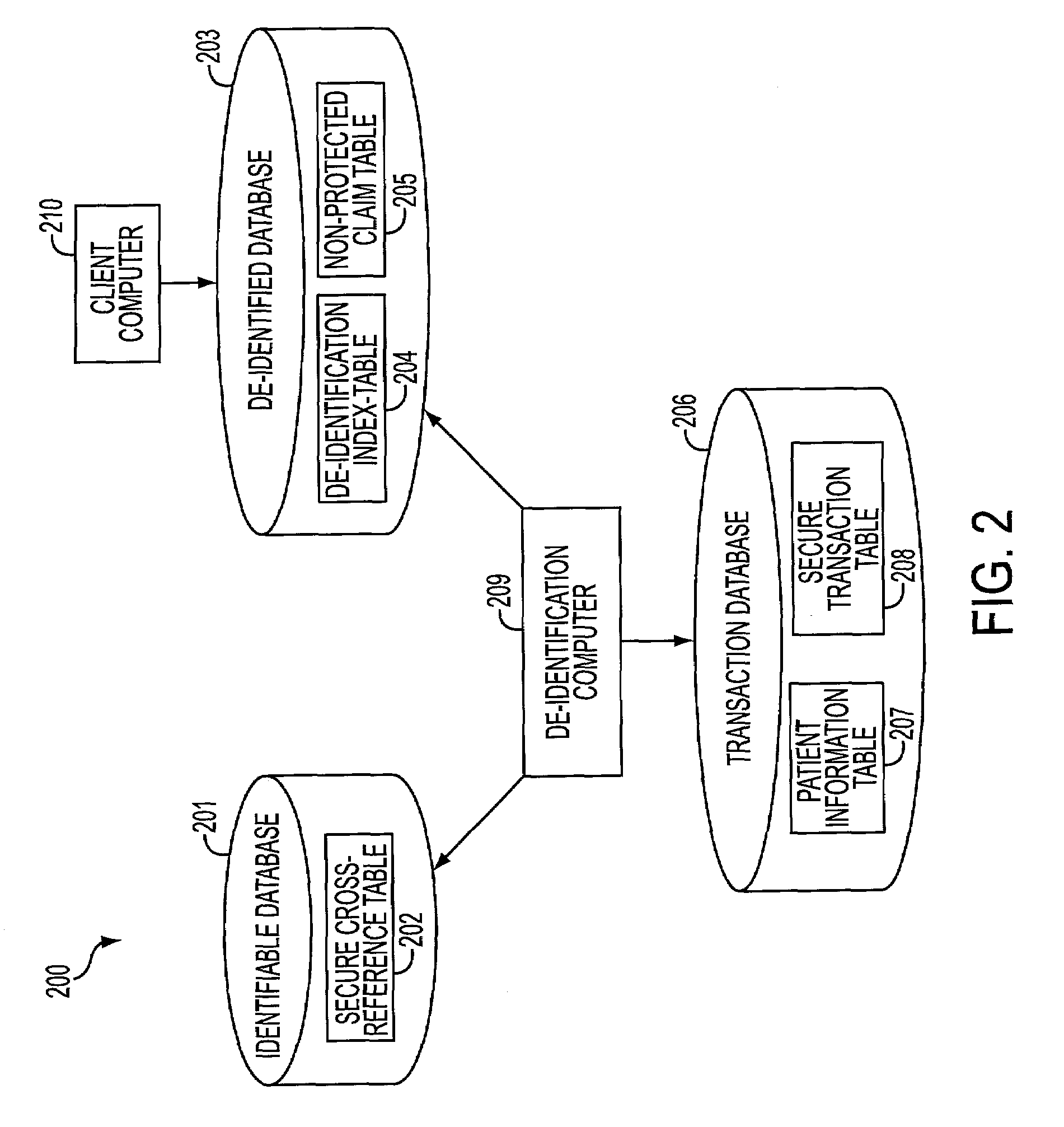
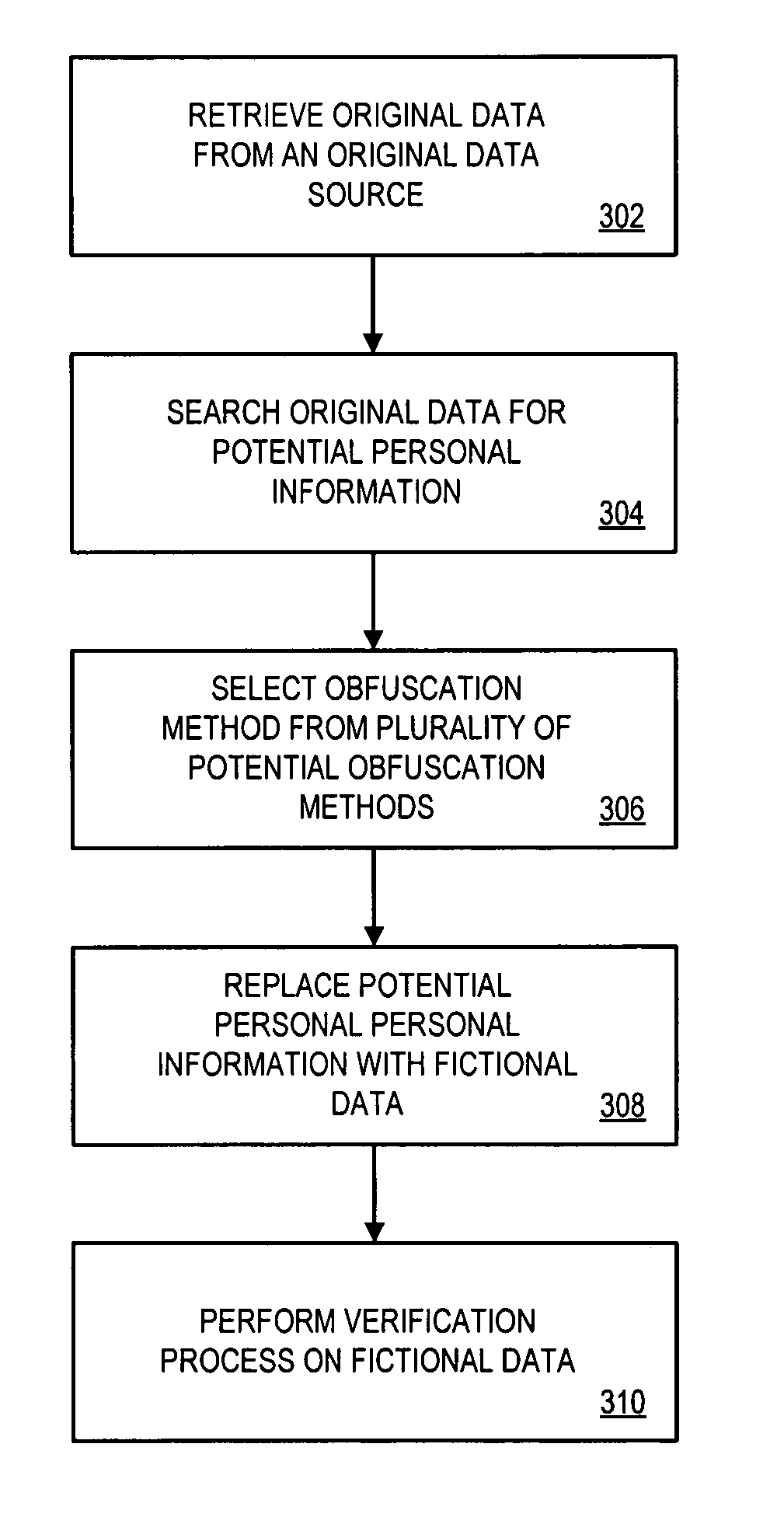
Systems and methods for de-identification of personal data
According to some embodiments, original data is retrieved from an original data source. The original data may be automatically searched for potential personal information, such as a person's name, address, or Social Security number. An obfuscation method may be selected from a plurality of potential obfuscation methods. The potential personal information in the original data may then be automatically replaced with fictional data in accordance with the selected obfuscation method.
Owner:HARTFORD FIRE INSURANCE
Systems and methods for encryption-based de-identification of protected health information
ActiveUS7519591B2Data processing applicationsMultiple keys/algorithms usageInternet privacyPatient data
Owner:CERNER INNOVATION
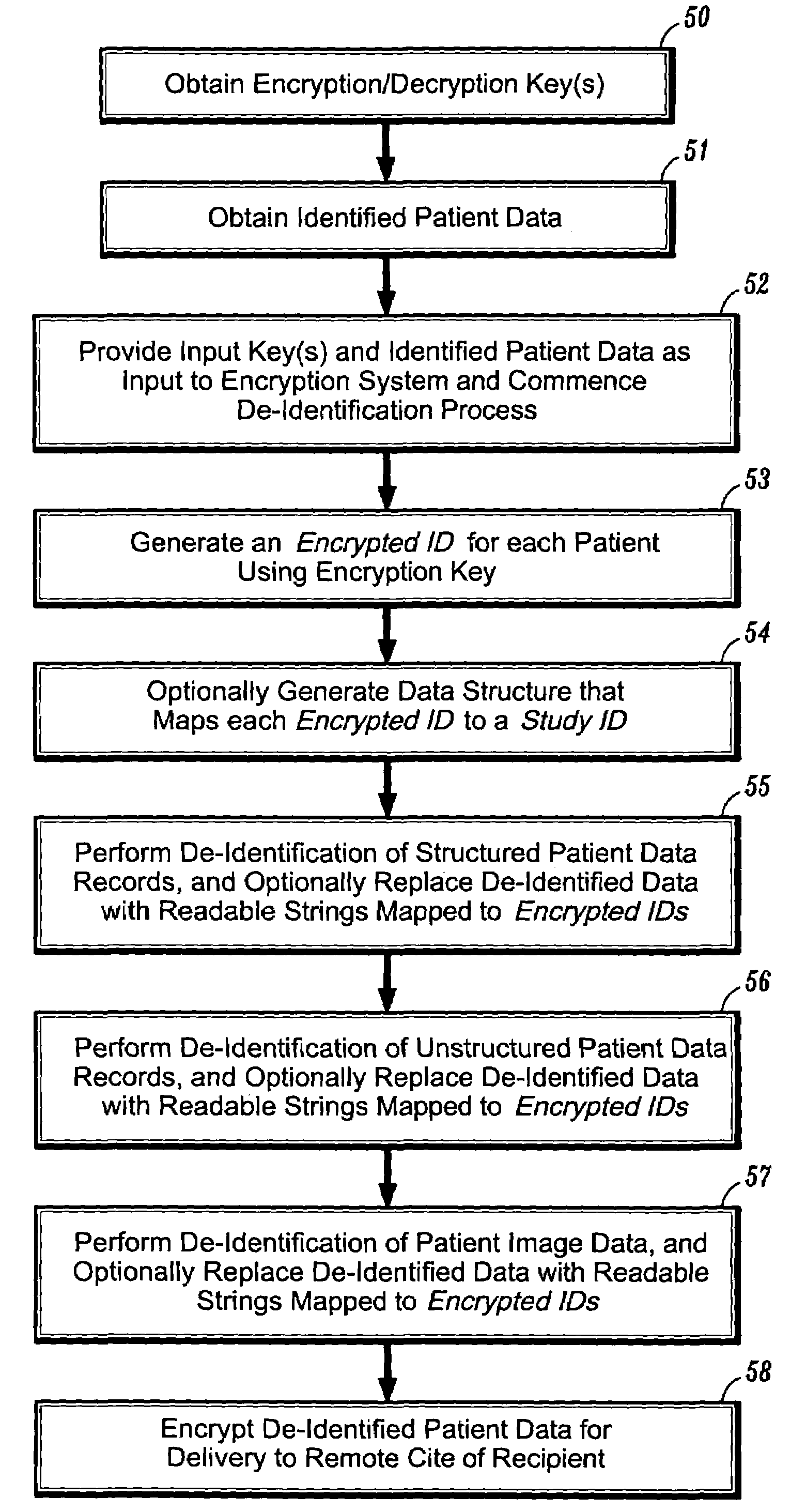
Method and system of de-identification of a record
InactiveUS20070255704A1Digital data information retrievalComputer security arrangementsUnstructured dataDe-identification
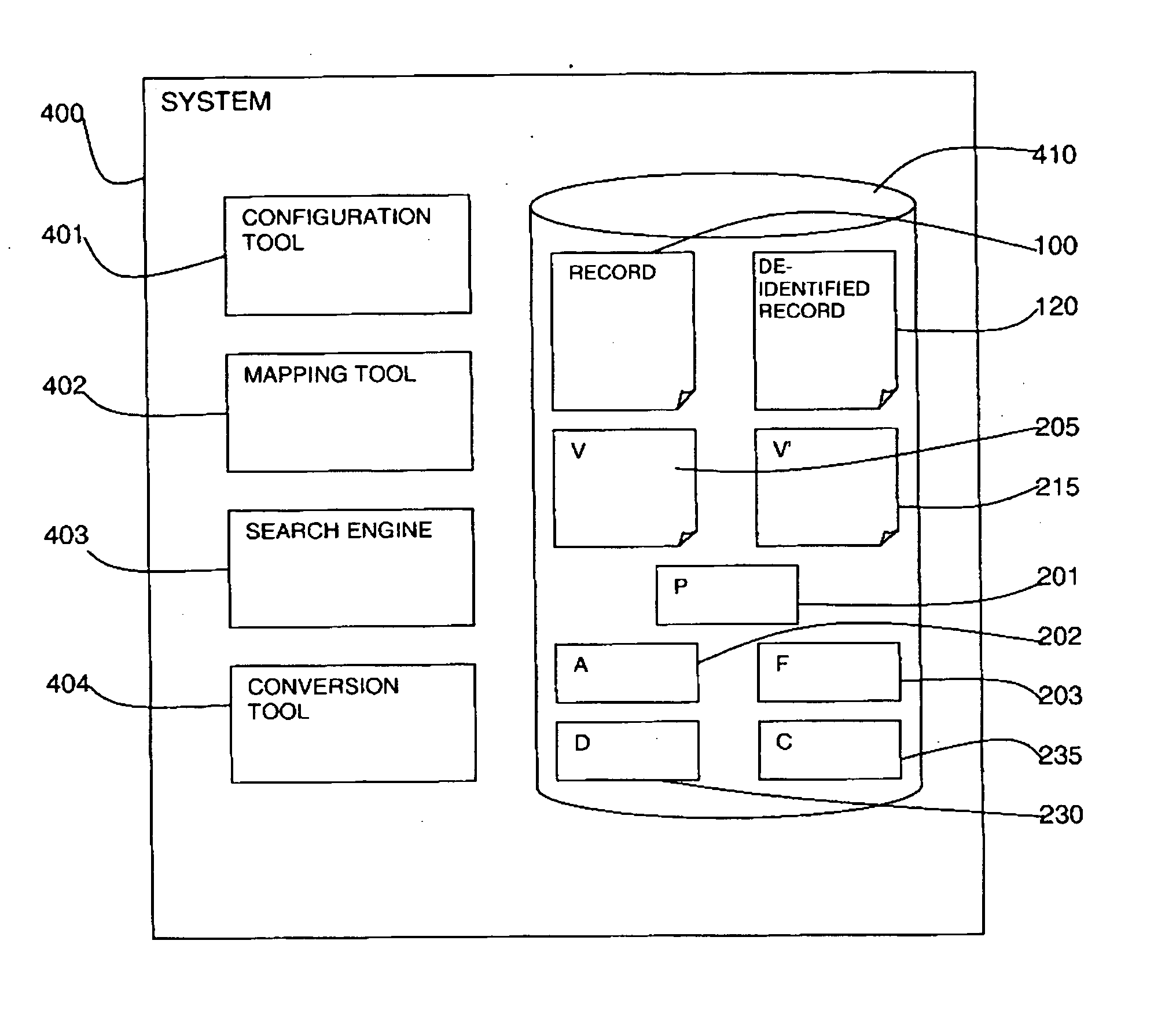
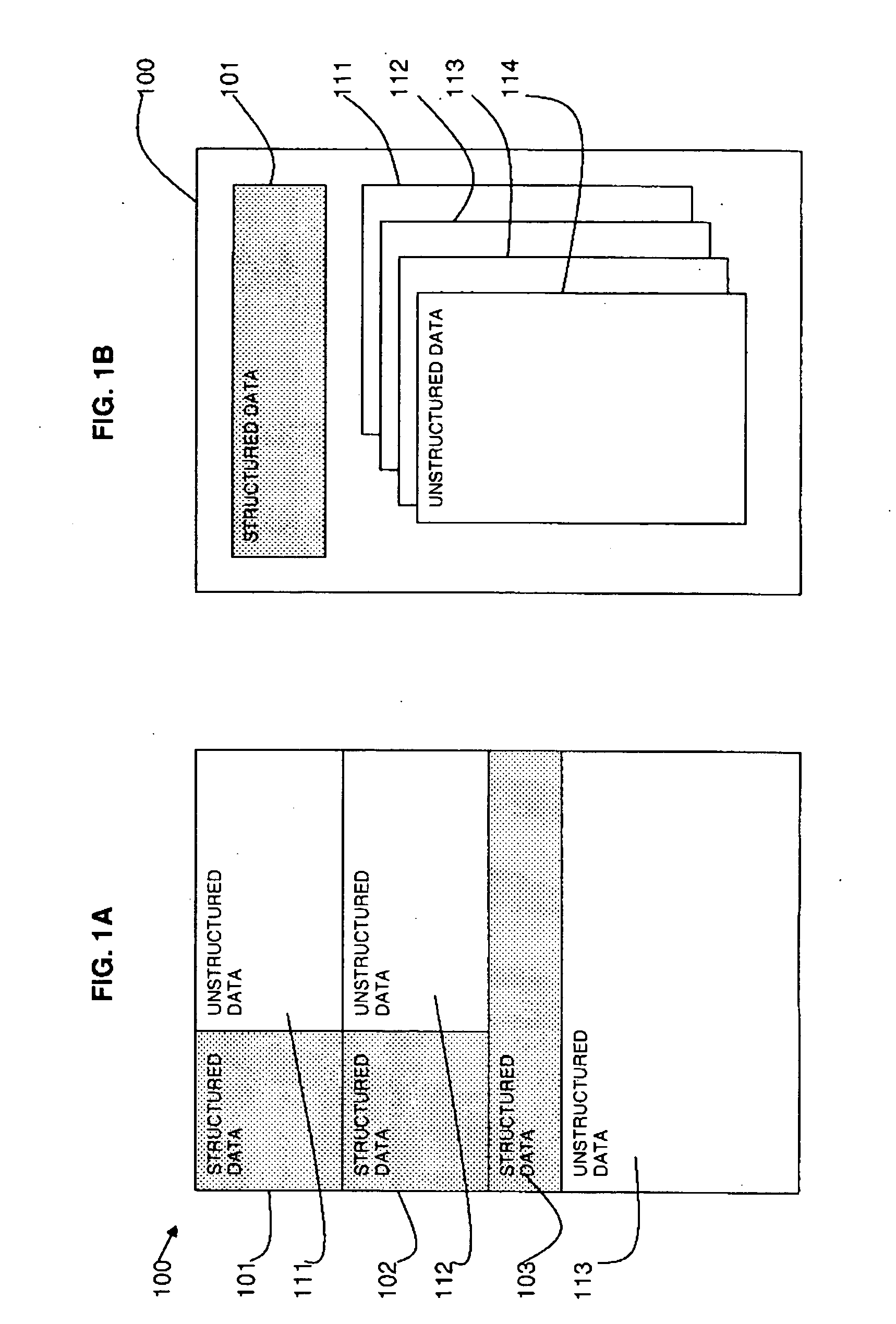
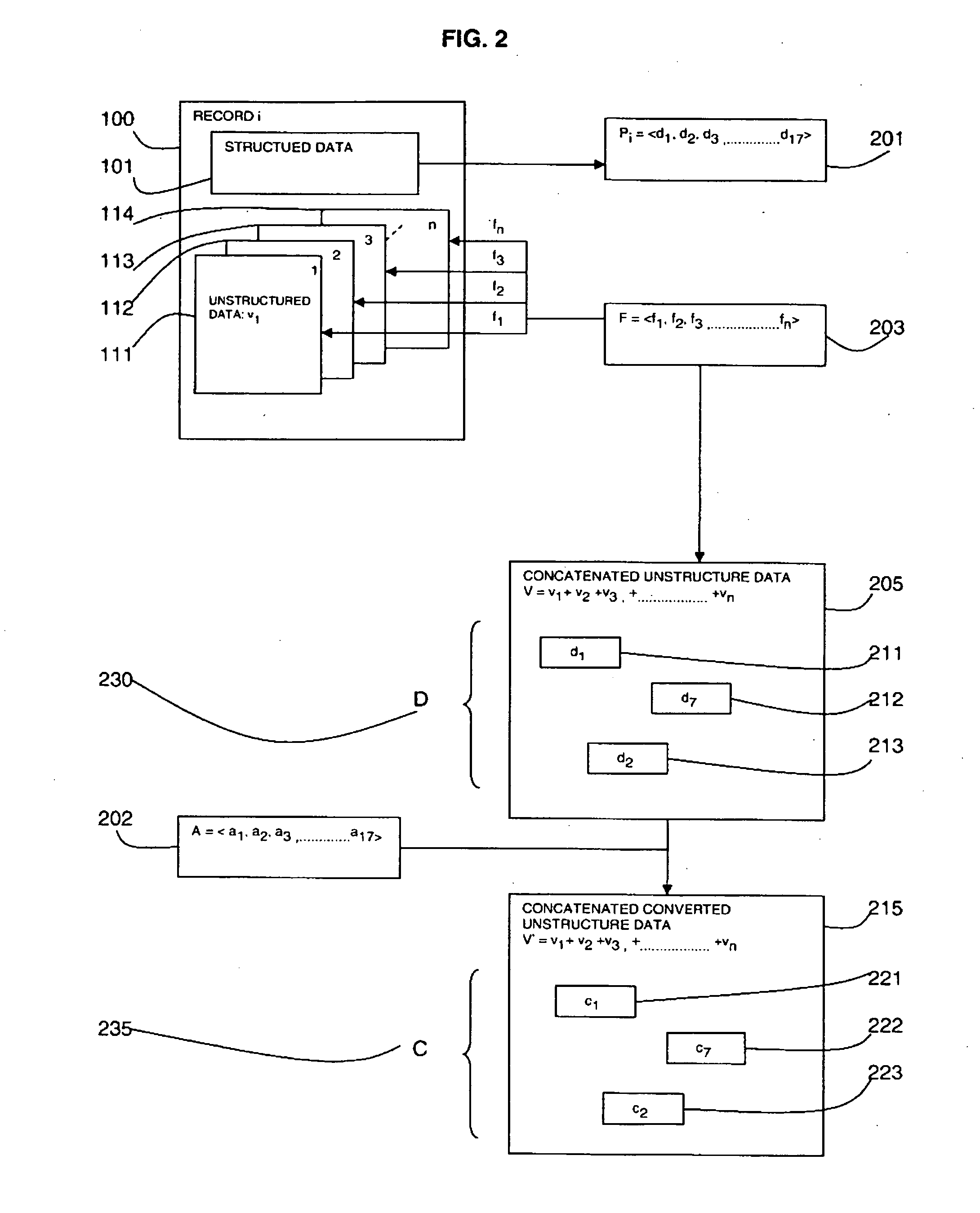
A method and system of de-identification of a record (100) are provided. The method includes creating a vector of identification field values (201) of a record (100), searching unstructured data (205) of the record (100) for each identification field value of the vector (201), and de-identifying the identification field values (230) of the record (100). The step of creating a vector of identification field values (201) extracts the values from one or more structured portions (101) of the record (100). An action (202) is defined for each identification field to de-identify the identification field. The method may include defining a mapping (203) of unstructured portions (111, 112, 113, 114) of the record (100), and extracting the unstructured portions (111, 112, 113, 114) of the record (100), wherein the steps of searching and de-identifying are carried out on the extracted unstructured portions (205).
Owner:IBM CORP
Data source privacy screening systems and methods
InactiveUS20040199781A1Digital data processing detailsRelational databasesReference databaseData set
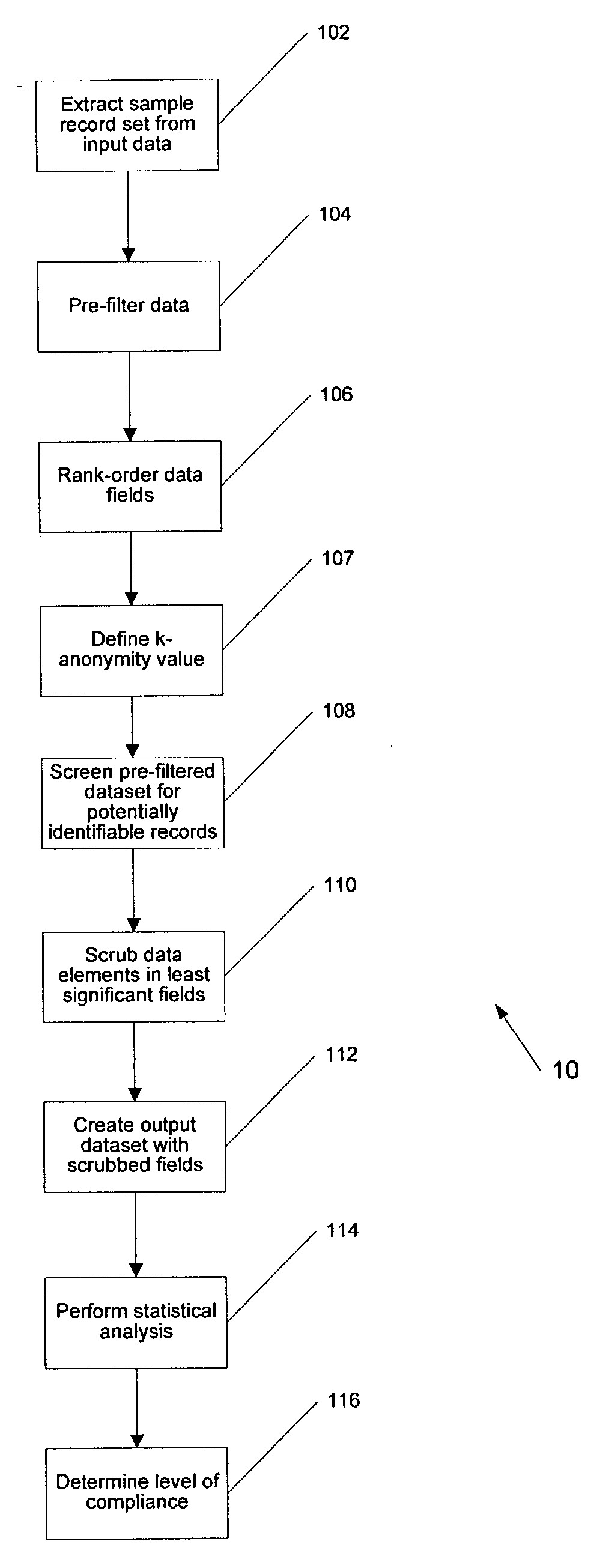
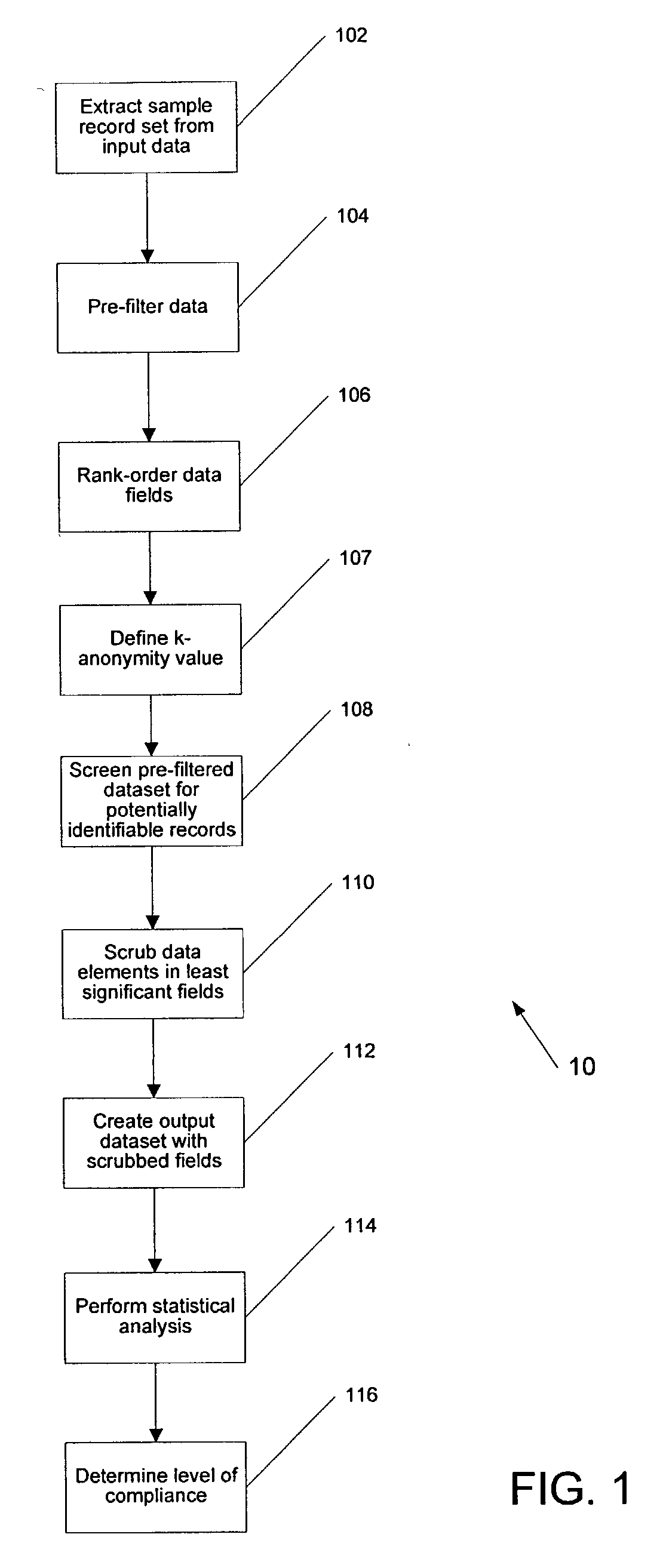
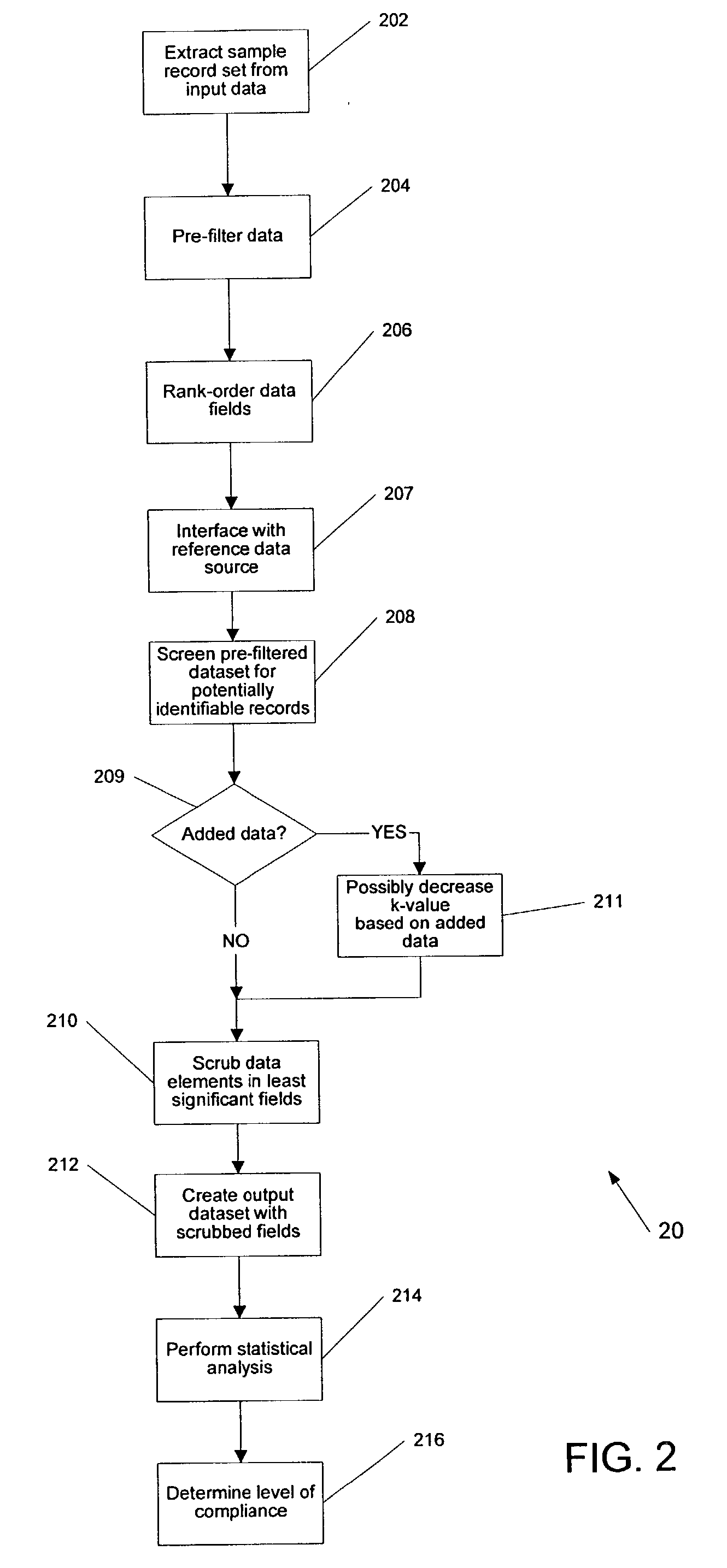
A de-identification method and an apparatus for performing same on electronic datasets are described. The method and system processes input datasets or databases that contain records relating to individual entities to produce a resulting output dataset that contains as much information as possible while minimizing the risk that any individual in the input dataset could be re-identified from that output dataset. Individual entities may include patients in a hospital or served by an insurance carrier, as well as voters, subscribers, customers, companies, or any other organization of discrete records. Criteria for preventing re-identification can be selected based on intended use of the output data and can be adjusted based on the content of reference databases. The method and system can also be associated with data acquisition equipment, such as a biologic data sampling device, to prevent de-identification of patient or other confidential data acquired by the equipment.
Owner:PRIVASOURCE
Audio signal de-identification
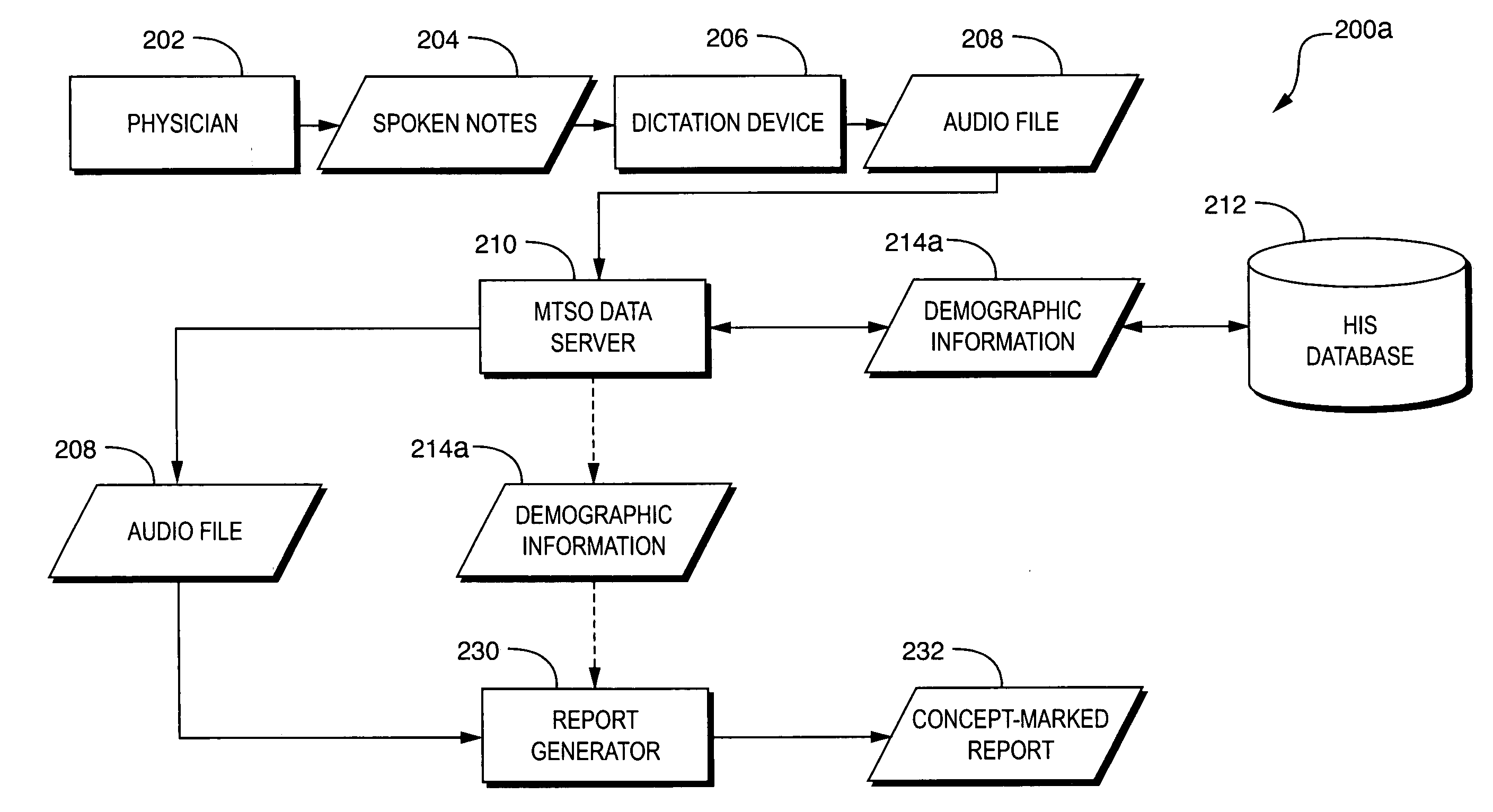
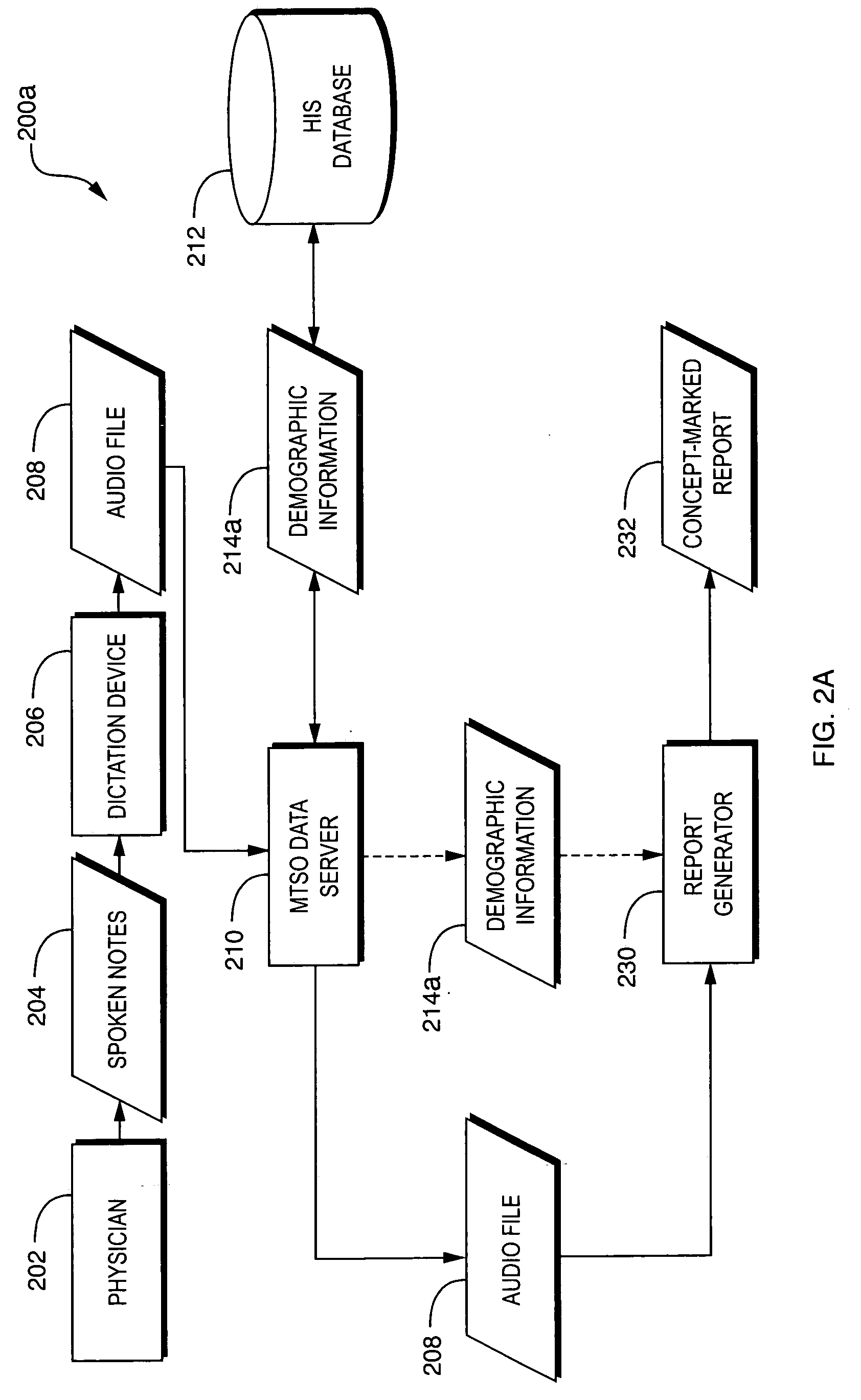
Techniques are disclosed for automatically de-identifying spoken audio signals. In particular, techniques are disclosed for automatically removing personally identifying information from spoken audio signals and replacing such information with non-personally identifying information. De-identification of a spoken audio signal may be performed by automatically generating a report based on the spoken audio signal. The report may include concept content (e.g., text) corresponding to one or more concepts represented by the spoken audio signal. The report may also include timestamps indicating temporal positions of speech in the spoken audio signal that corresponds to the concept content. Concept content that represents personally identifying information is identified. Audio corresponding to the personally identifying concept content is removed from the spoken audio signal. The removed audio may be replaced with non-personally identifying audio.
Owner:MULTIMODAL TECH INC
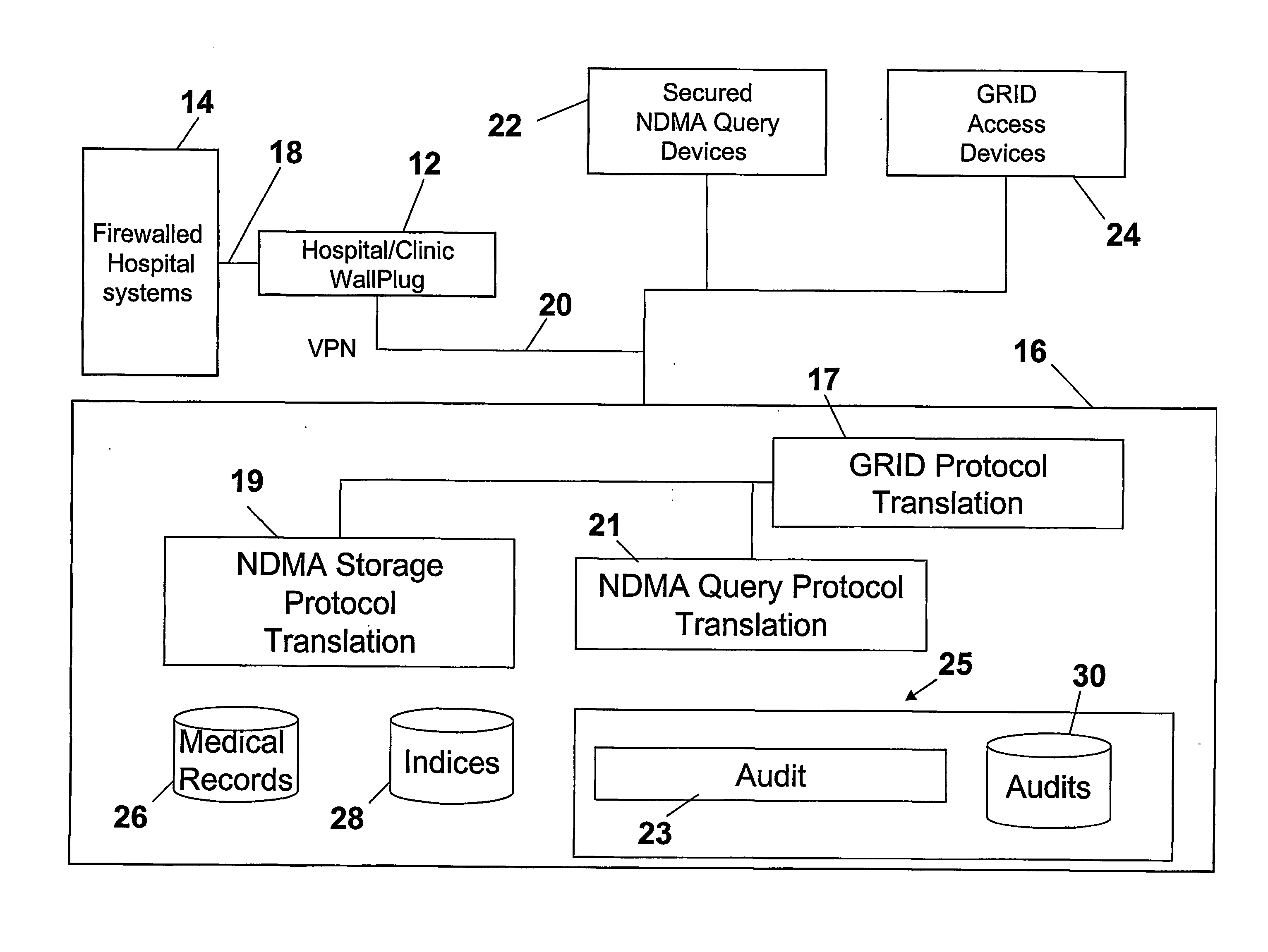
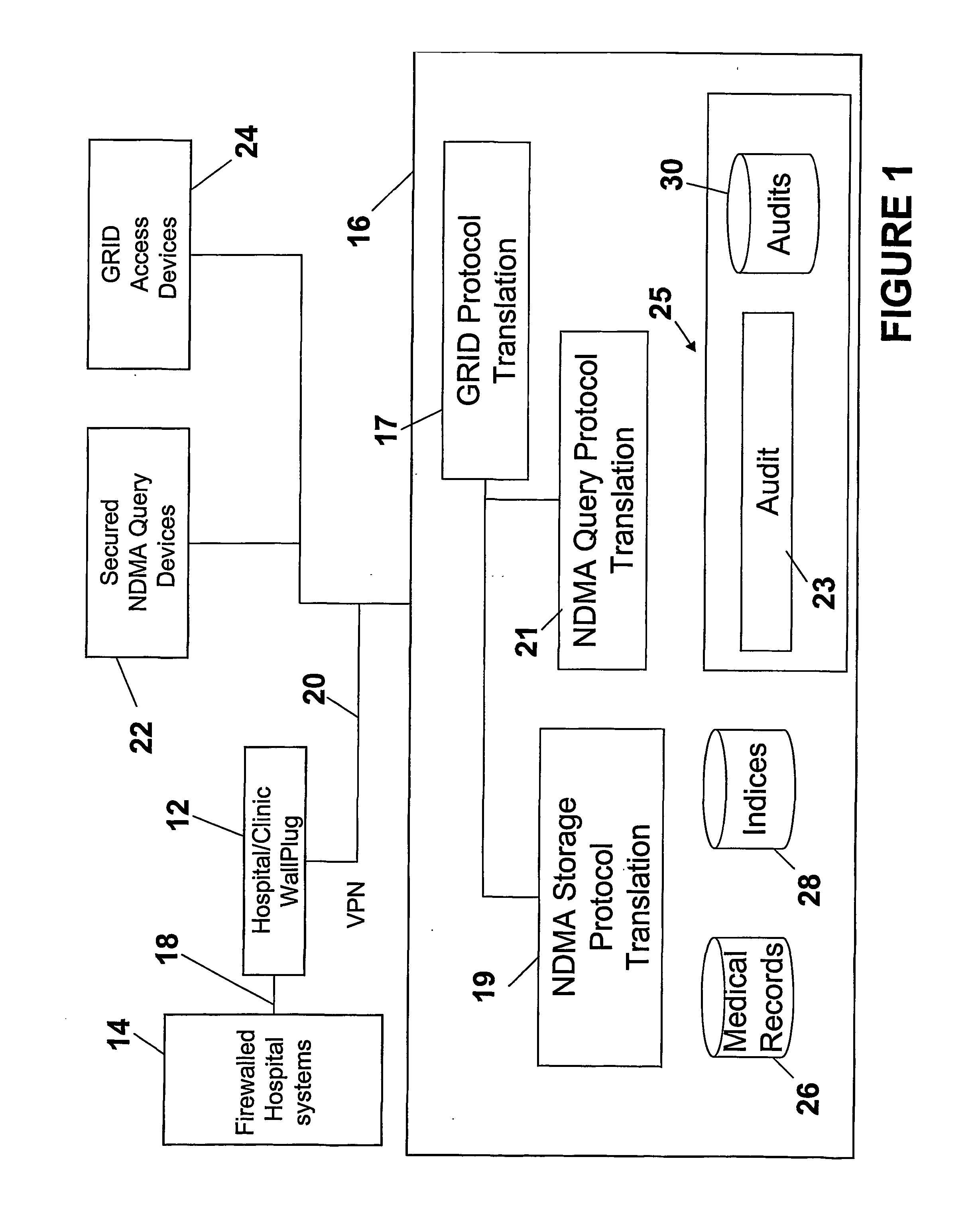
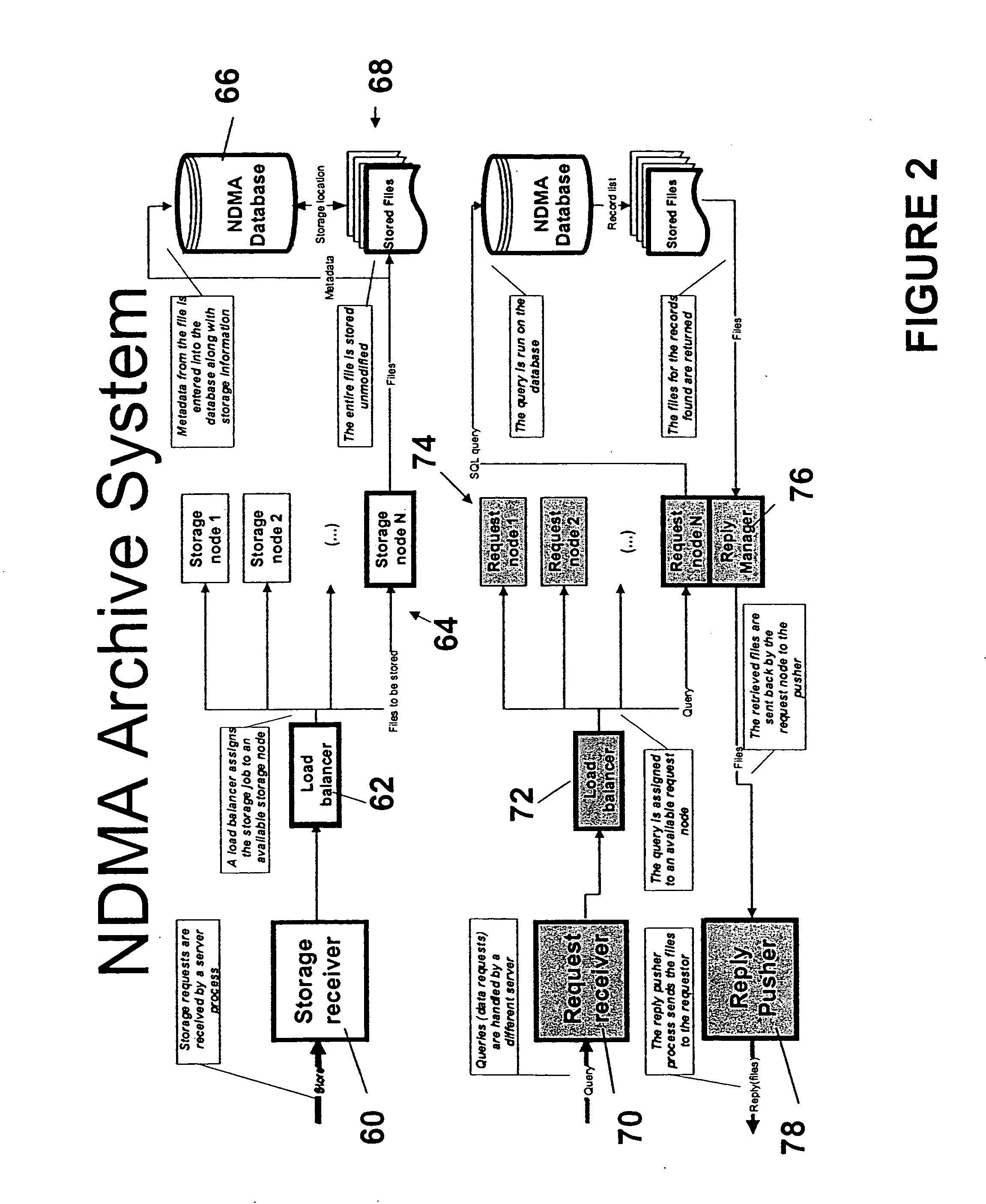
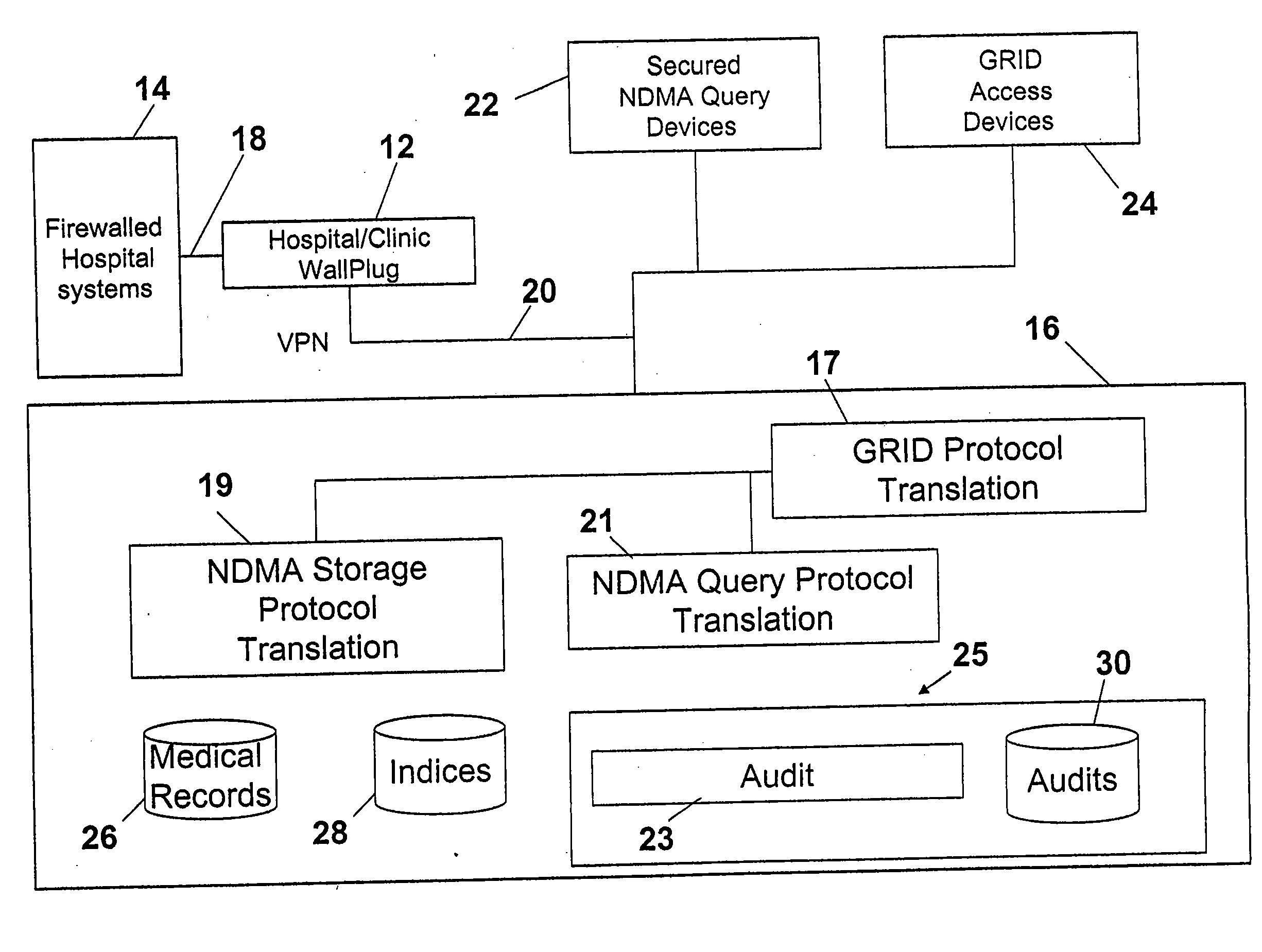
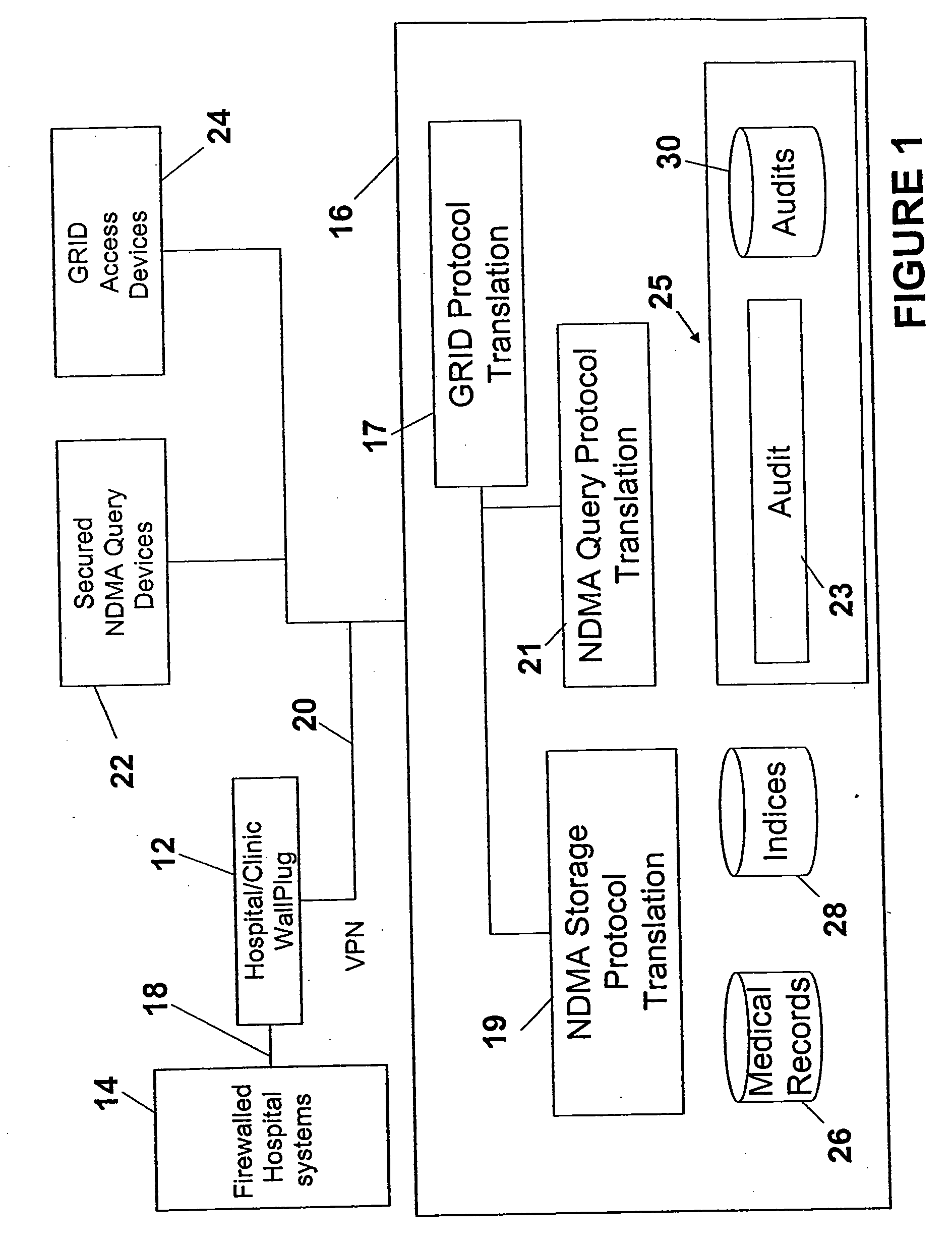
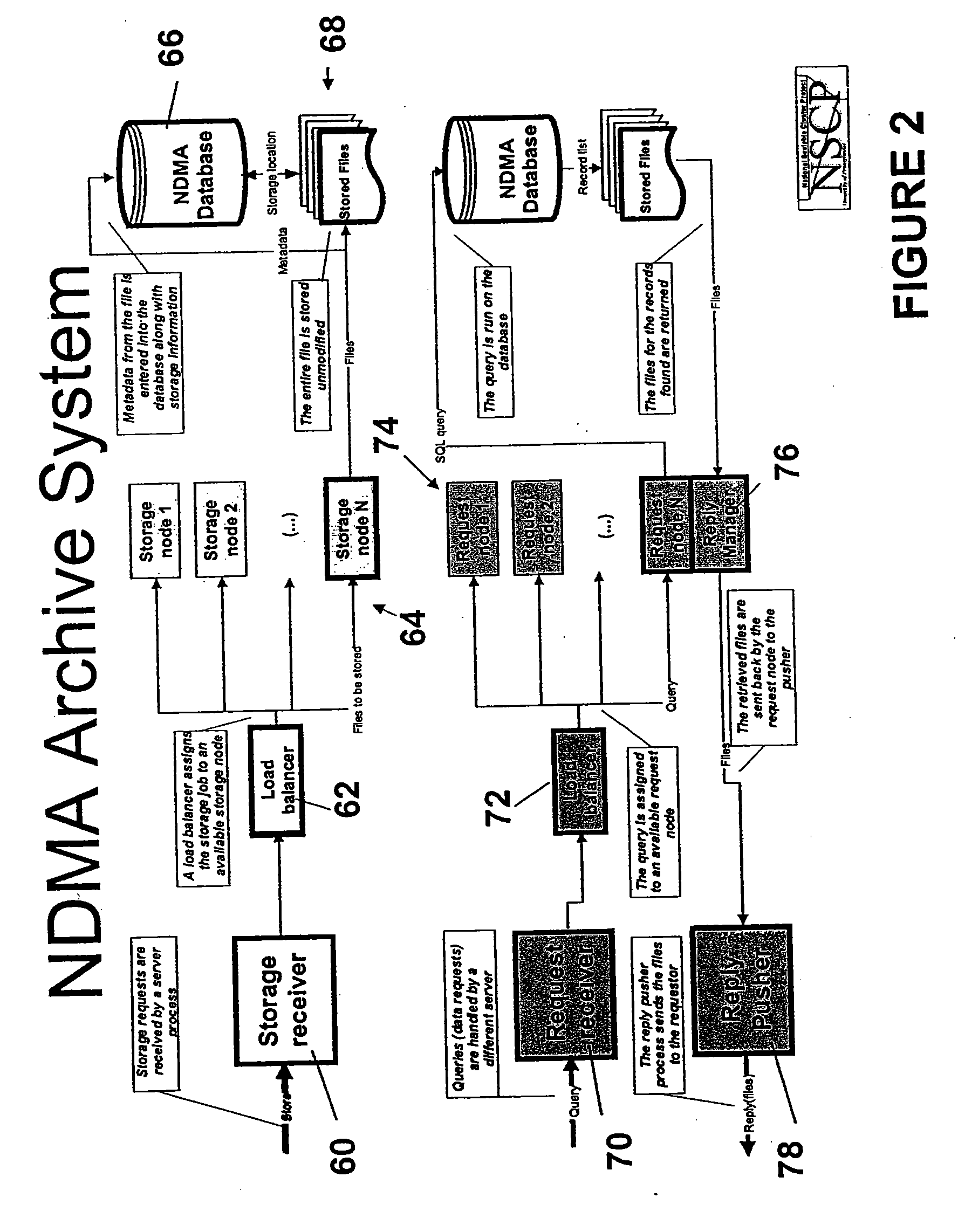
Ndma db schema, dicom to relational schema translation, and xml to sql query transformation
InactiveUS20060282447A1Efficiently handle transferMaintain privacyData processing applicationsDigital data information retrievalDICOMQuery transformation
A translation scheme translates DICOM content into a format compatible for storage in an NDMA relational database. The translation scheme employs a schema for indexing the DICOM content, and employs a mechanism for translating queries embedded in XML into SQL. The translation scheme translates DICOM compatible data into a tab delimited flat representation of the DICOM content. The flat representation is then translated into data compatible with a relational database format, such as SQL, and then into database insert commands. The schema enables capture of the DICOM information into relational tables. Methods are also provided to service XML formatted research and clinical queries, to translate XML queries to optimized SQL and to return query results to XML specified destinations with record de-identification where required. Methods are also provided to interface to NDMA WallPlugs, secured query devices, or GRID devices.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA
System and method of de-identifying data
ActiveUS7158979B2Digital data processing detailsComputer security arrangementsFinancial transactionDe-identification
Owner:INGENIX INC
Systems and methods for de-identification of personal data
According to some embodiments, original data is retrieved from an original data source. The original data may be automatically searched for potential personal information, such as a person's name, address, or Social Security number. An obfuscation method may be selected from a plurality of potential obfuscation methods. The potential personal information in the original data may then be automatically replaced with fictional data in accordance with the selected obfuscation method.
Owner:HARTFORD FIRE INSURANCE
De-Identification of Data
ActiveUS20120151597A1Digital data processing detailsAnalogue secracy/subscription systemsProgramming languageDe-identification
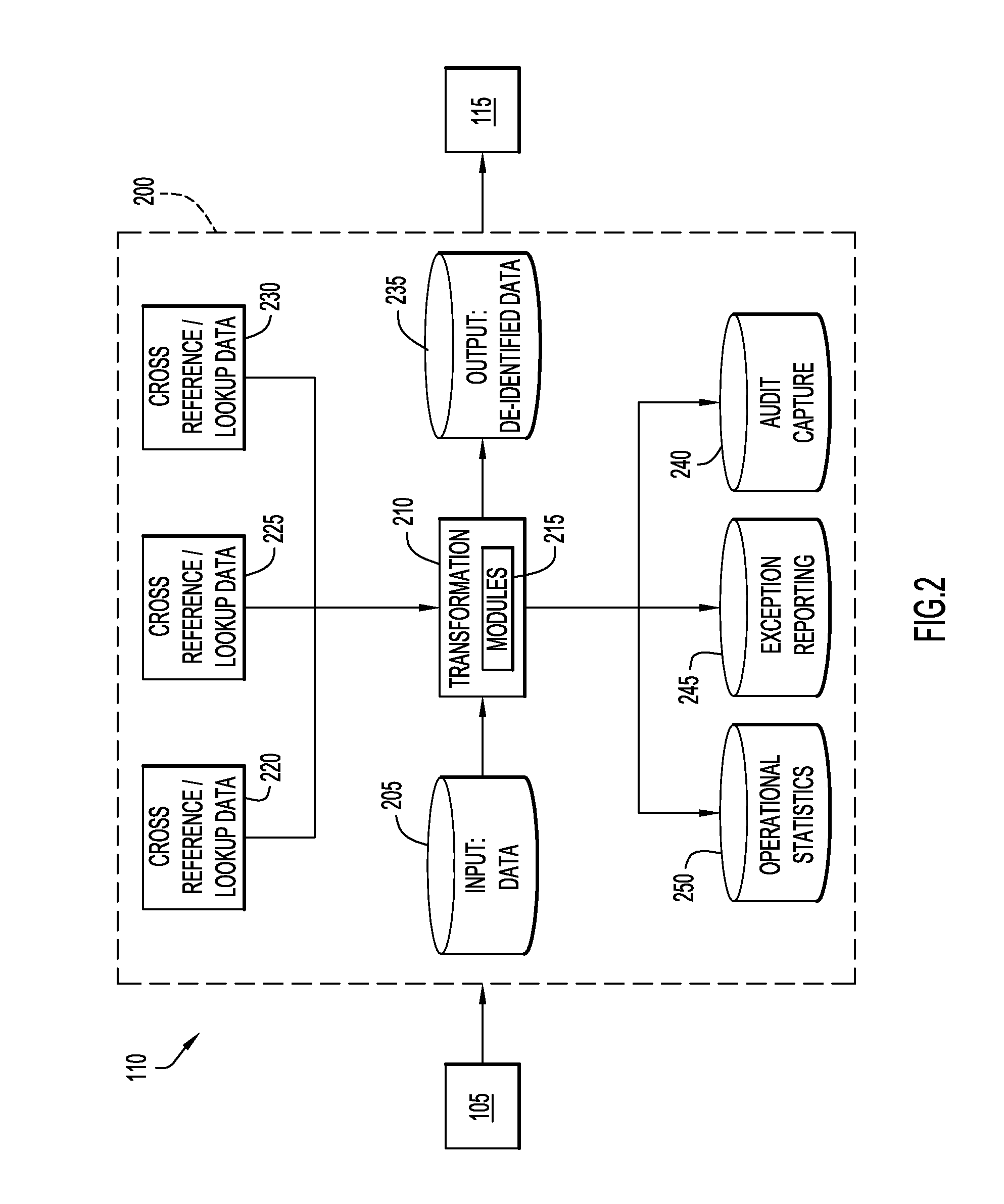
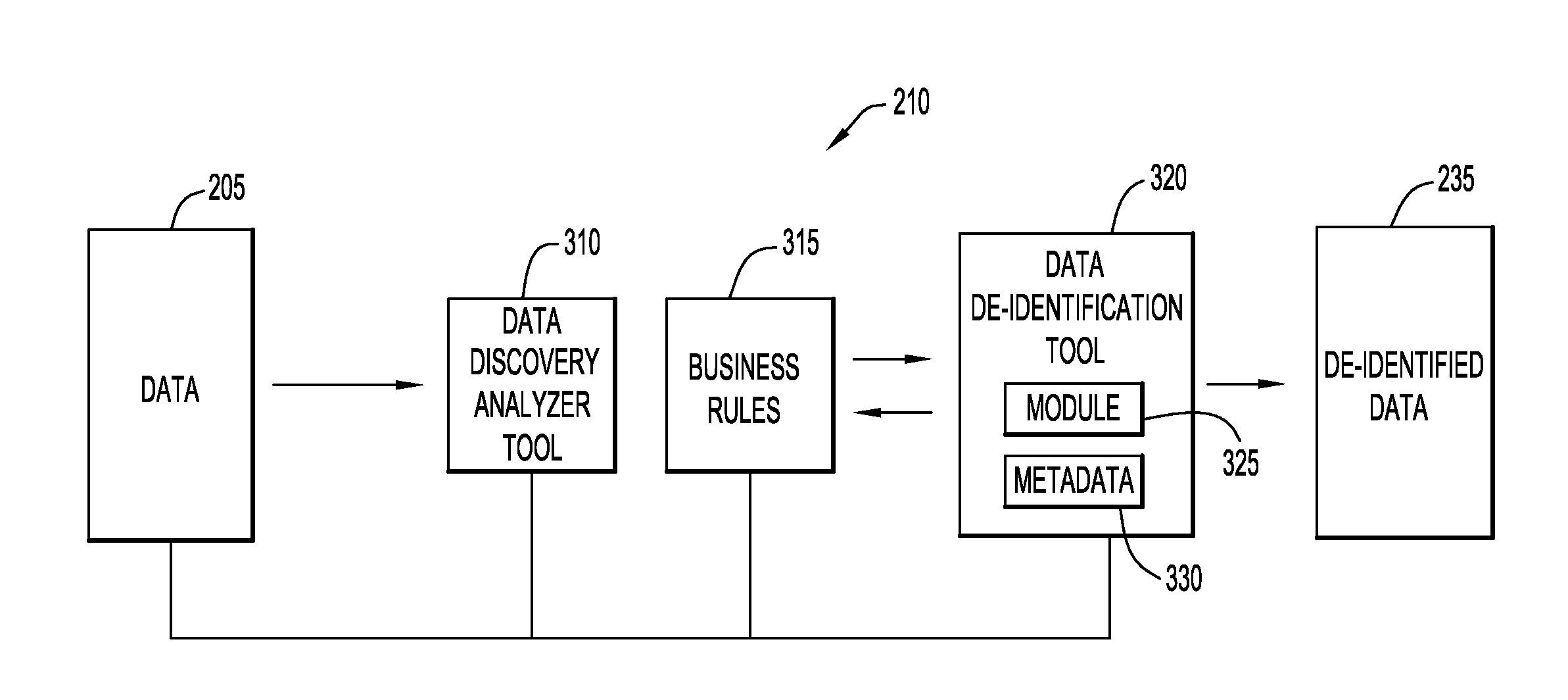
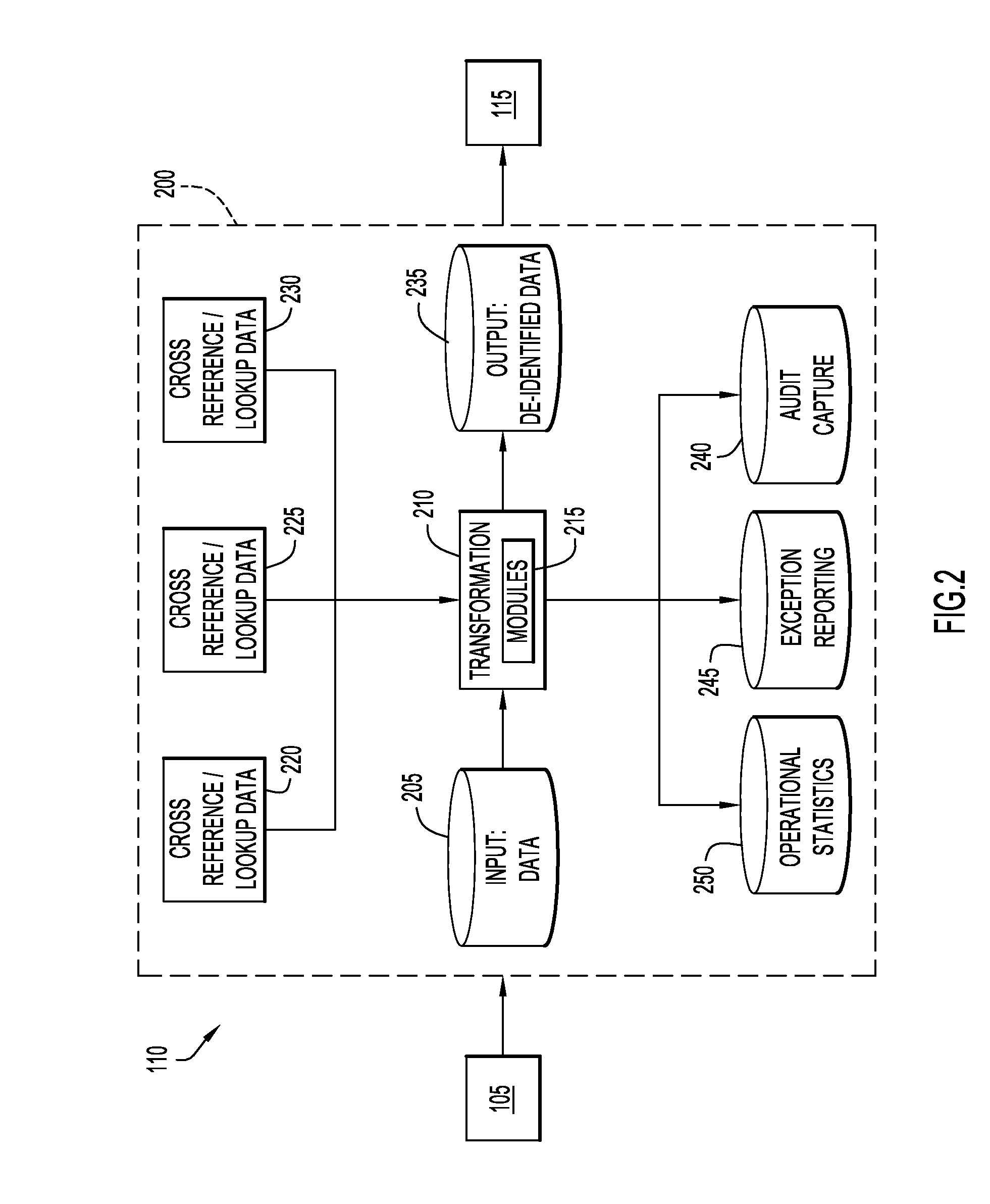
The present invention relates to a method, computer program product and system for de-identifying data, wherein a de-identification protocol is selectively mapped to a business rule at runtime via an ETL tool.
Owner:IBM CORP
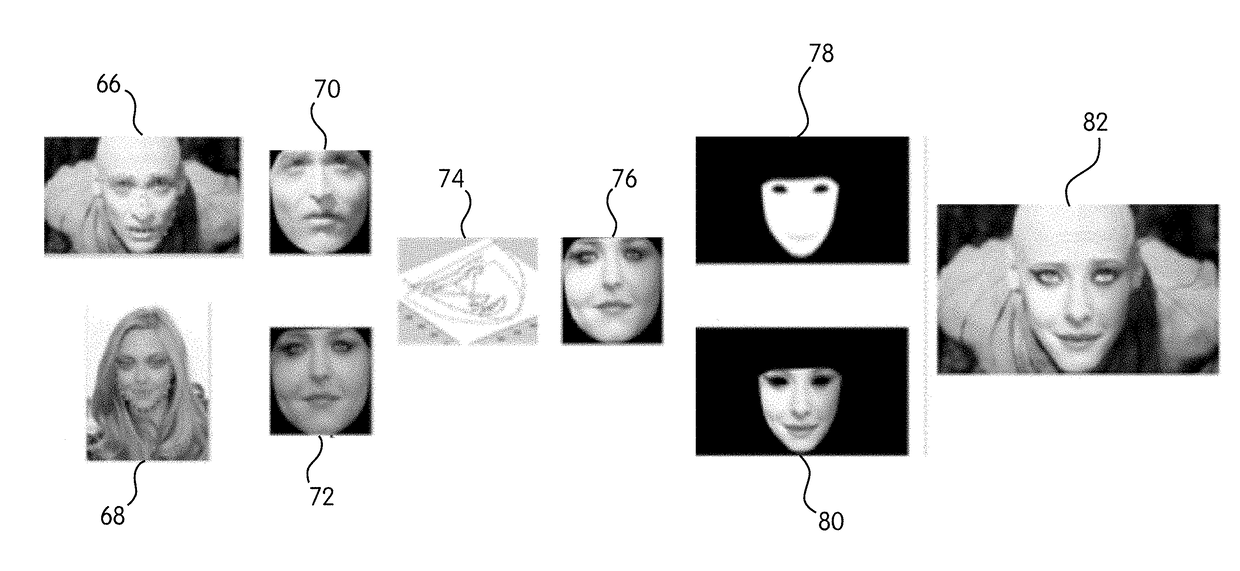
System and method for processing video to provide facial de-identification
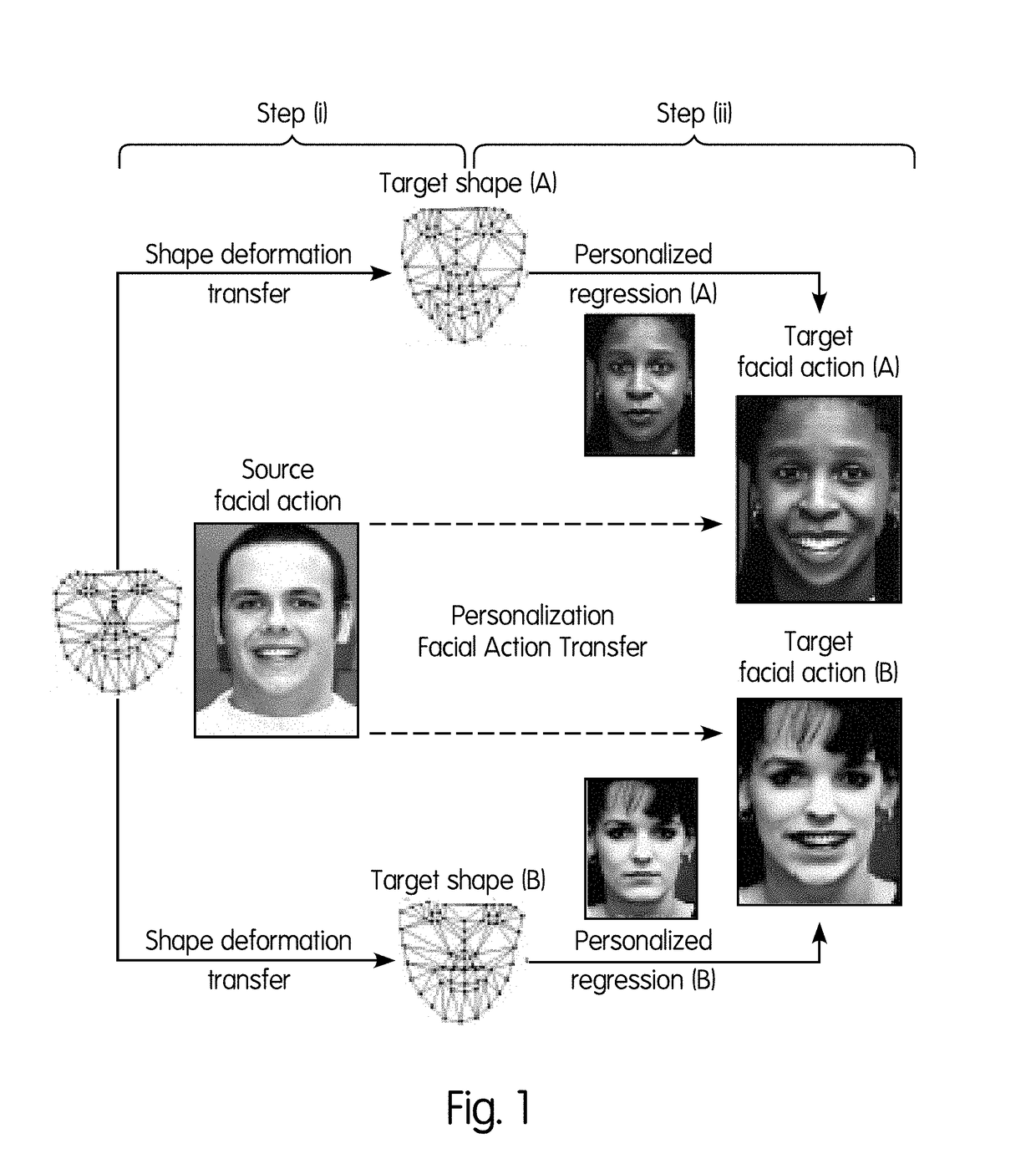
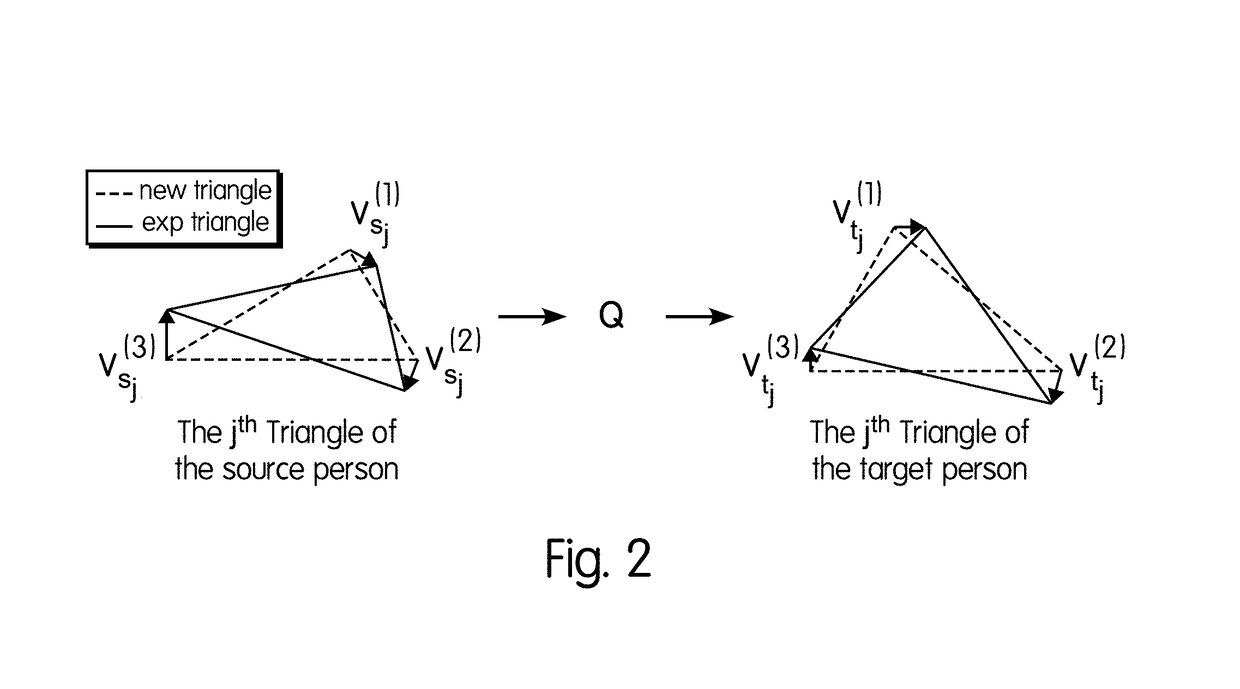
A system and method for real-time image and video face de-identification that removes the identity of the subject while preserving the facial behavior is described The facial features of the source face are replaced with that of the target face while preserving the facial actions of the source face on the target face. The facial actions of the source face are transferred to the target face using personalized Facial Action Transfer (FAT), and the color and illumination is adapted. Finally, the source image or video containing the target facial features is outputted for display. Alternatively, the system can run in real-time.
Owner:UNIVERSITY OF PITTSBURGH
Dicom de-identification system and method
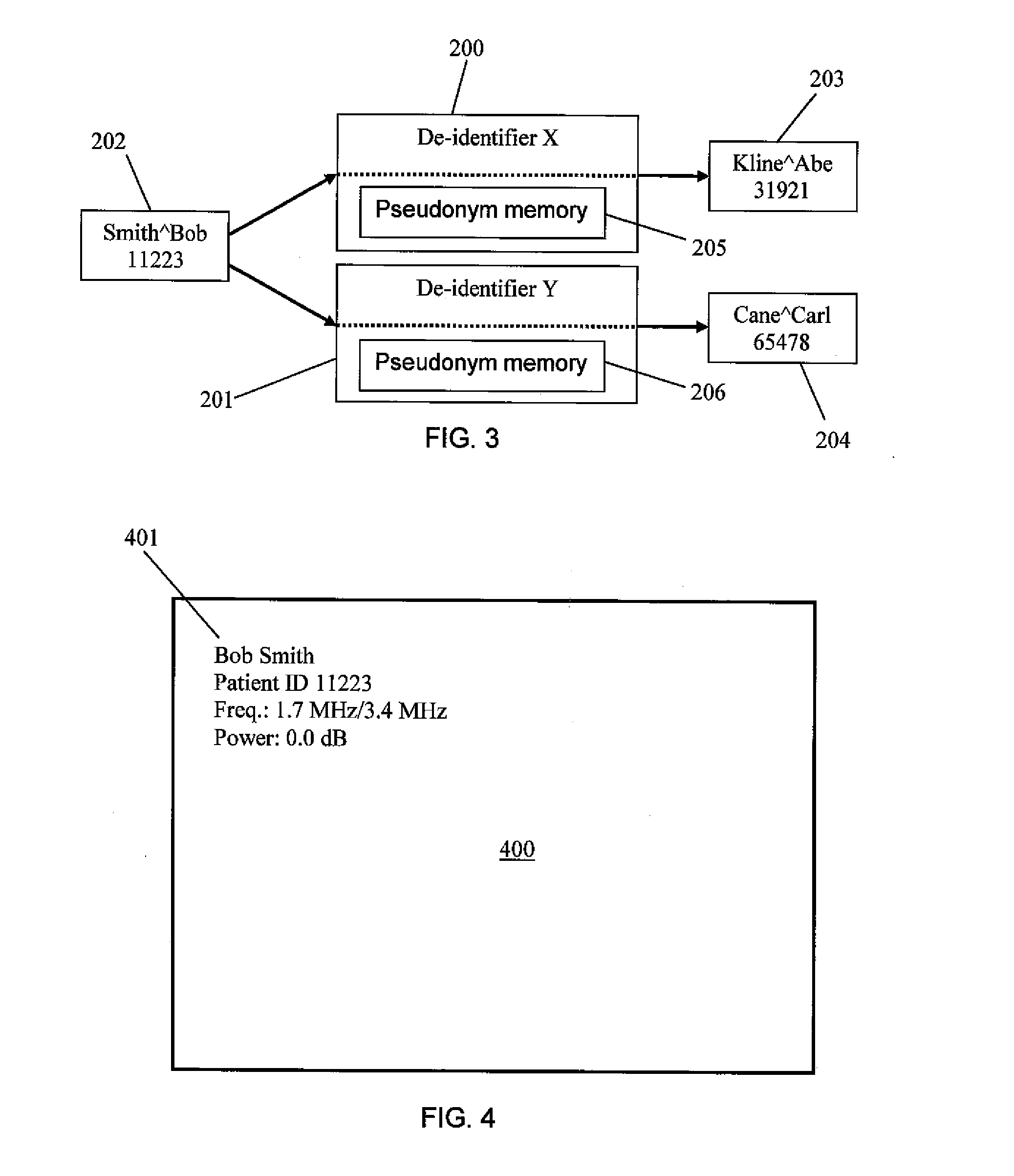
A system for creating de-identification programs for de-identifying DICOM image files containing DICOM images and metadata. The system provides a user interface that allows users to create de-identification programs. Each program has redaction rules specifying redaction regions in normalized coordinates defining a region of a DICOM image to be redacted to obfuscate content in the redaction region, and metadata substitution rules specifying metadata elements to be substituted with pseudonyms. The user may modify the redaction rules and metadata substitution rules, and preview the effect of the de-identification program by applying the de-identification program to DICOM images and associated metadata and displaying the resulting modified DICOM image and associated metadata. The system maintains a pseudonym memory to determine if a pseudonym has been stored for each metadata element specified by the substitution rule so that the same pseudonym is consistently used for the same element values.
Owner:SYNAPTIVE MEDICAL INC
System and method to reduce a risk of re-identification of text de-identification tools
ActiveUS20170177907A1Improve de-identificationNot at risk of errorDigital data protectionProbabilistic networksMedical recordData set
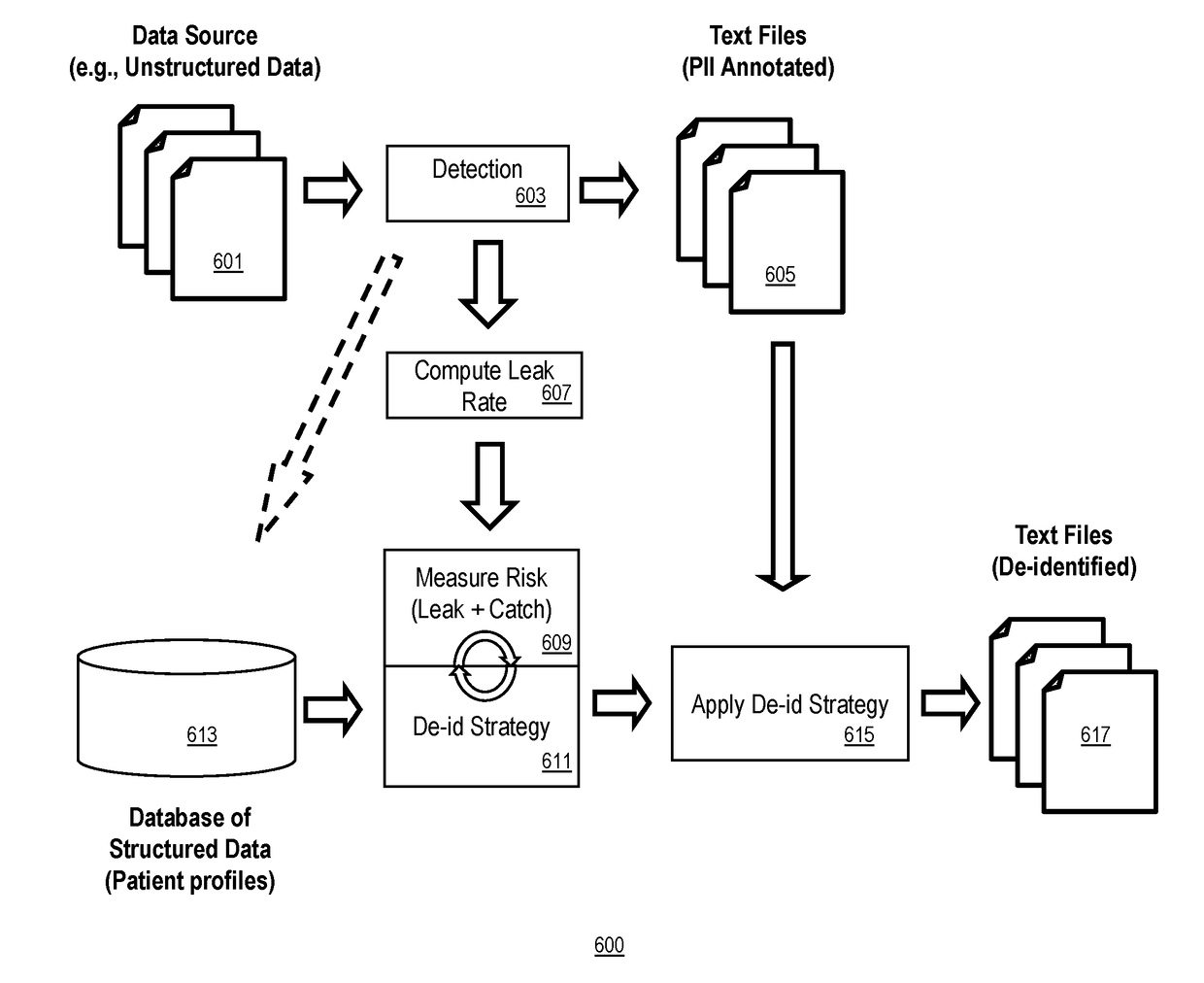
A computer-implemented system and method to reduce re-identification risk of a data set. The method includes the steps of retrieving, via a database-facing communication channel, a data set from a database communicatively coupled to the processor, the data set selected to include patient medical records that meet a predetermined criteria; identifying, by a processor coupled to a memory, direct identifiers in the data set; identifying, by the processor, quasi-identifiers in the data set; calculating, by the processor, a first probability of re-identification from the direct identifiers; calculating, by the processor, a second probability of re-identification from the quasi-direct identifiers; perturbing, by the processor, the data set if one of the first probability or second probability exceeds a respective predetermined threshold, to produce a perturbed data set; and providing, via a user-facing communication channel, the perturbed data set to the requestor.
Owner:PRIVACY ANALYTICS
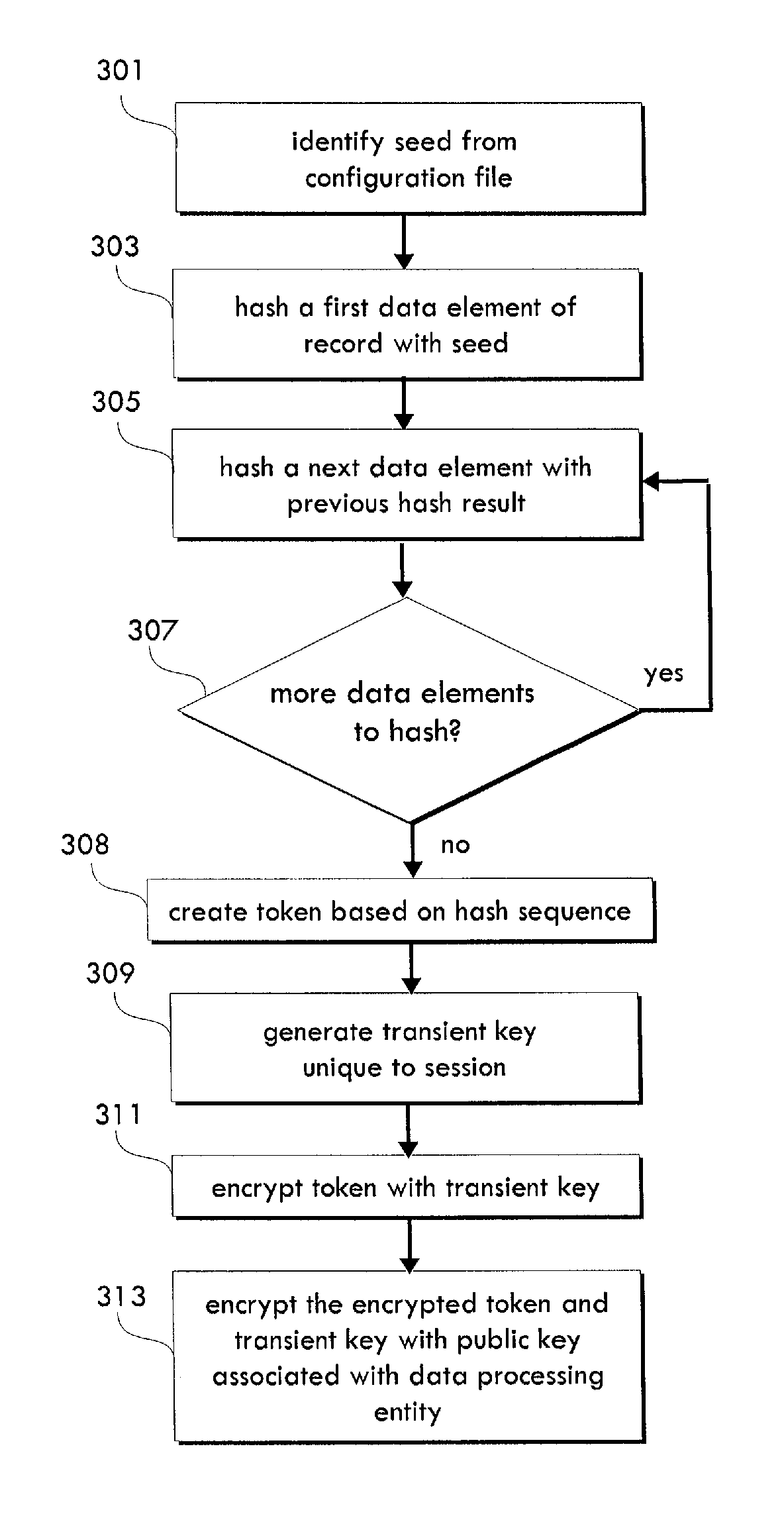
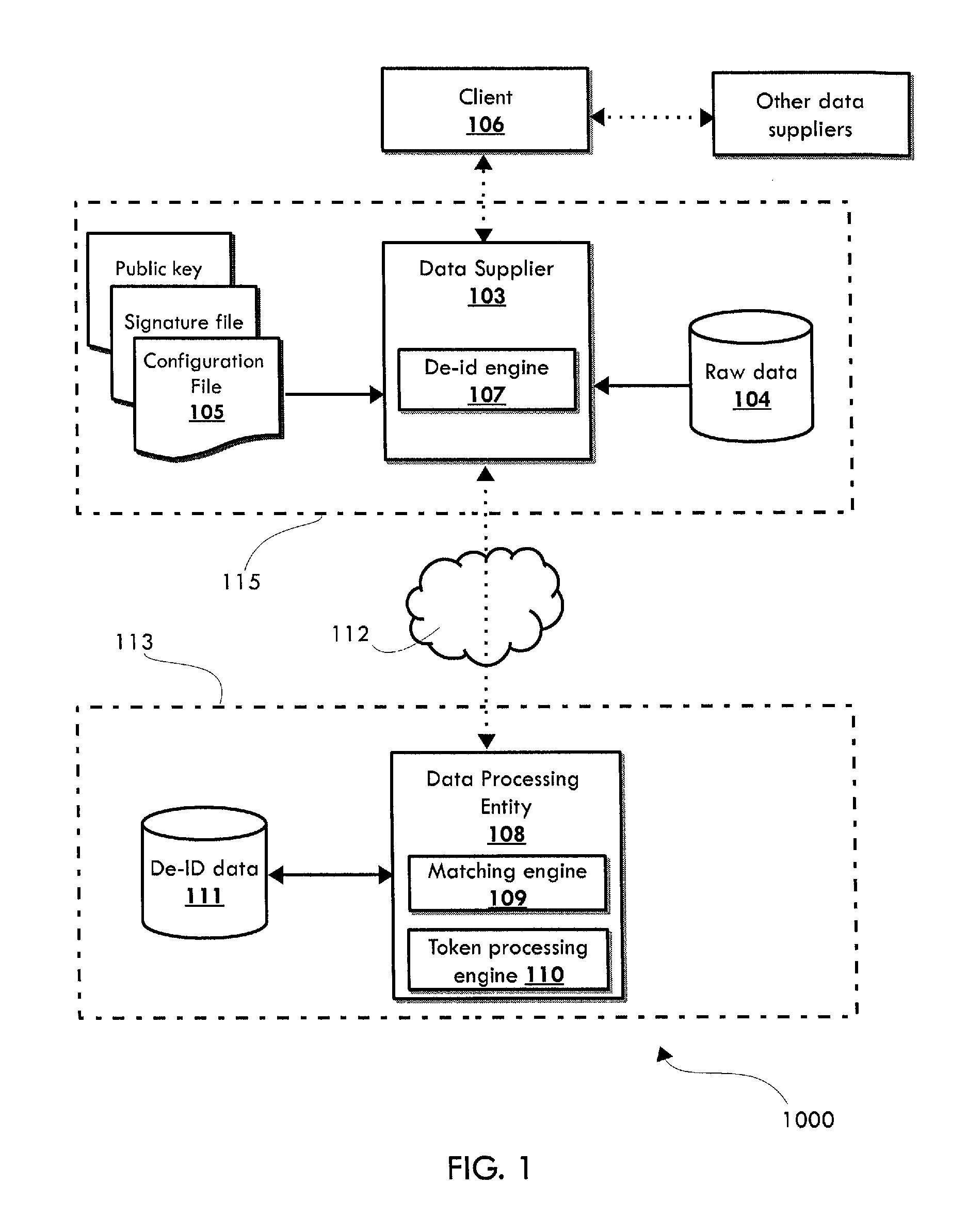
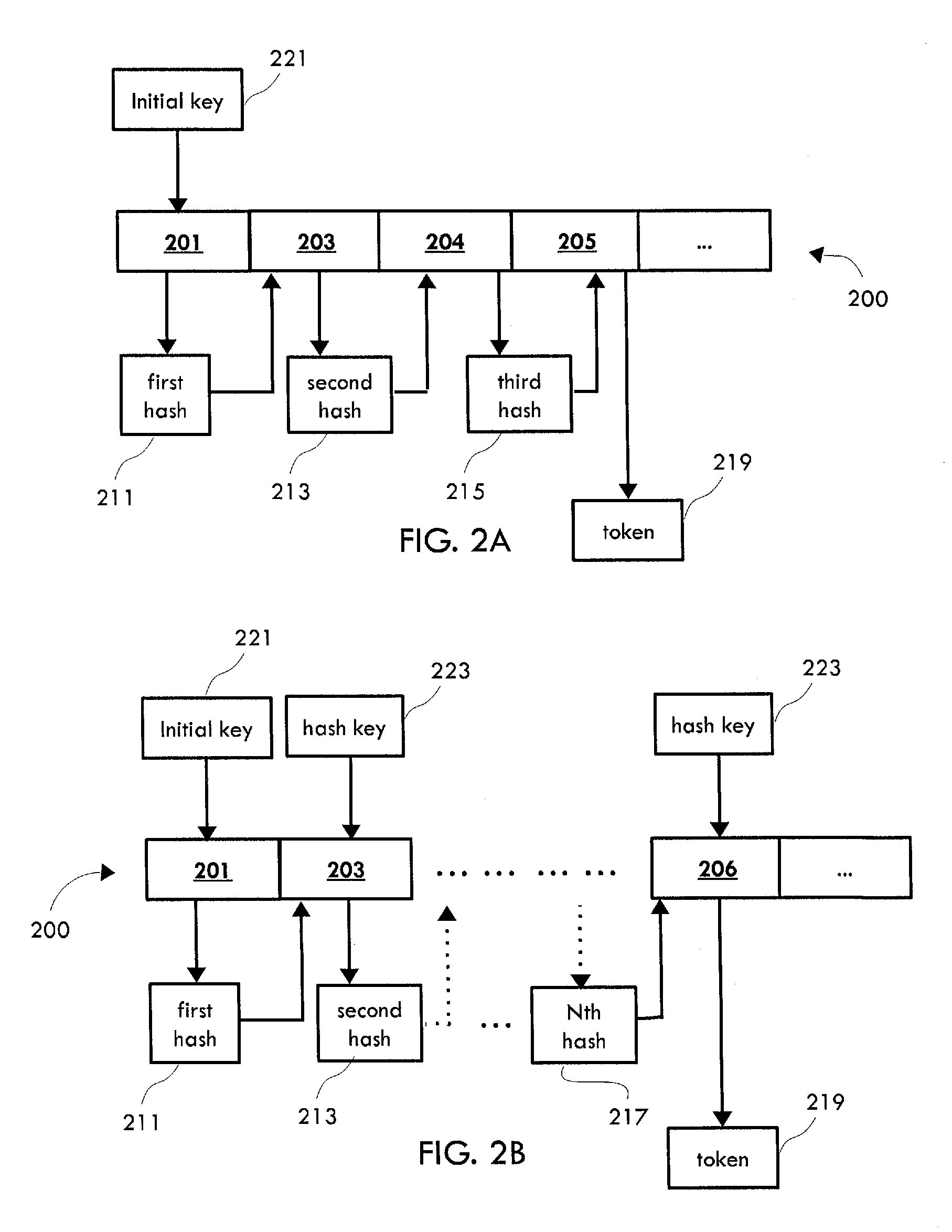
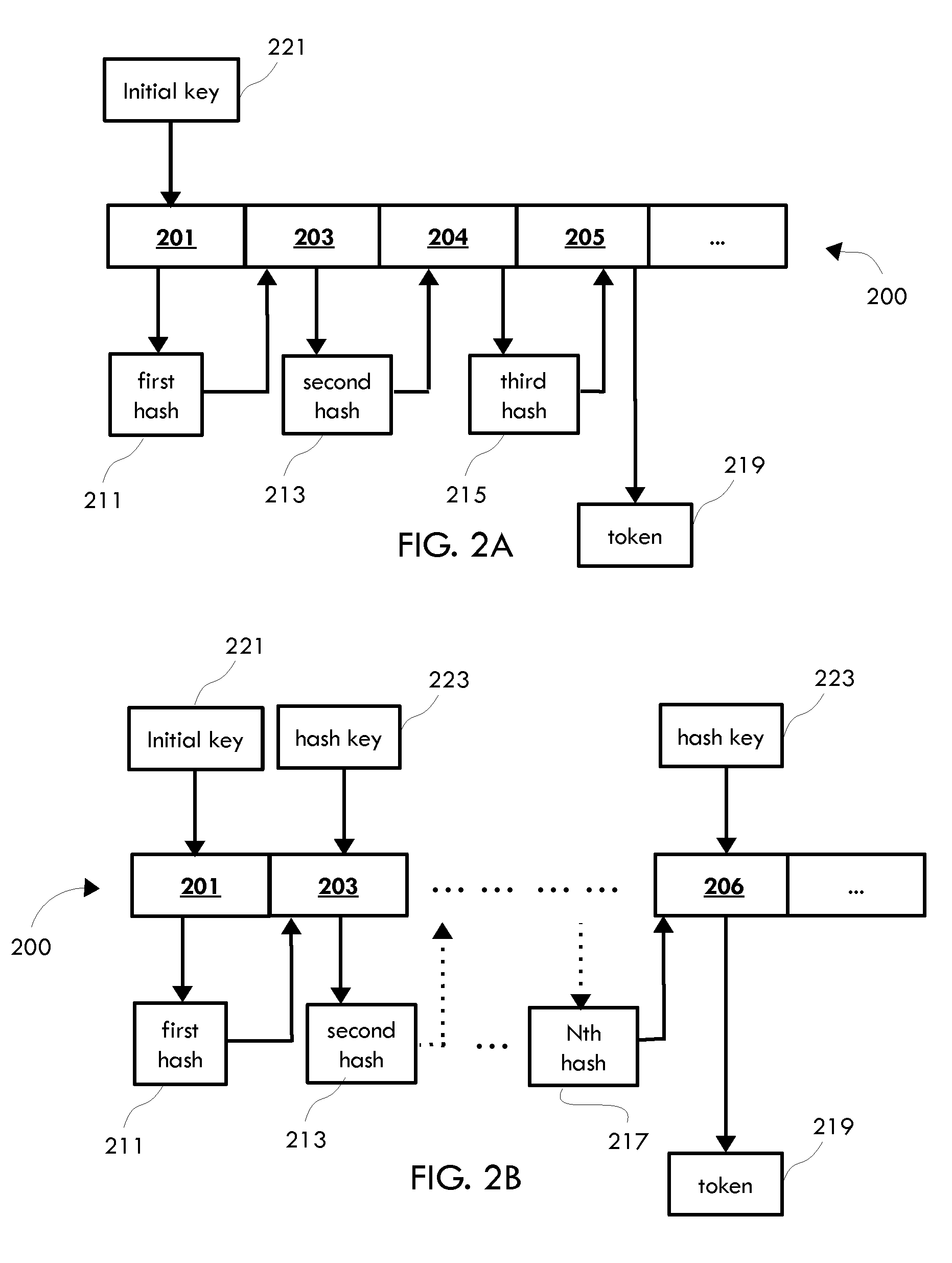
System and method for cascading token generation and data de-identification
ActiveUS9292707B1Multiple keys/algorithms usageEncryption apparatus with shift registers/memoriesTheoretical computer scienceData element
A computer-implemented method for de-identifying data by creating tokens through a cascading algorithm includes the steps of processing at least one record comprising a plurality of data elements to identify a subset of data elements comprising data identifying at least one individual; generating, with at least one processor, a first hash by hashing at least one first data element with at least one second data element of the subset of data elements; generating, with at least one processor, a second hash by hashing the first hash with at least one third data element of the subset of data elements; creating at least one token based at least partially on the second hash or a subsequent hash derived from the second hash, wherein the token identifies the at least one individual; and associating at least a portion of a remainder of the data elements with the at least one token.
Owner:MANAGEMENT SCI ASSOC
Ndma db schema, dicom to relational schema translation, and XML to SQL query translation
InactiveUS20090177637A1Efficiently handle transferData processing applicationsMedical imagesDICOMRelational table
A translation scheme translates DICOM content into a format compatible for storage in an NDMA relational database. The translation scheme employs a schema for indexing the DICOM content, and employs a mechanism for translating queries embedded in XML into SQL. The translation scheme translates DICOM compatible data into a tab delimited flat representation of the DICOM content. The flat representation is then translated into data compatible with a relational database format, such as SQL, and then into database insert commands. The schema enables capture of the DICOM information into relational tables. Methods are also provided to service XML formatted research and clinical queries, to translate XML queries to optimized SQL and to return query results to XML specified destinations with record de-identification where required. Methods are also provided to interface to NDMA WallPlugs, secured query devices, or GRID devices.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA
Dynamic De-Identification of Data
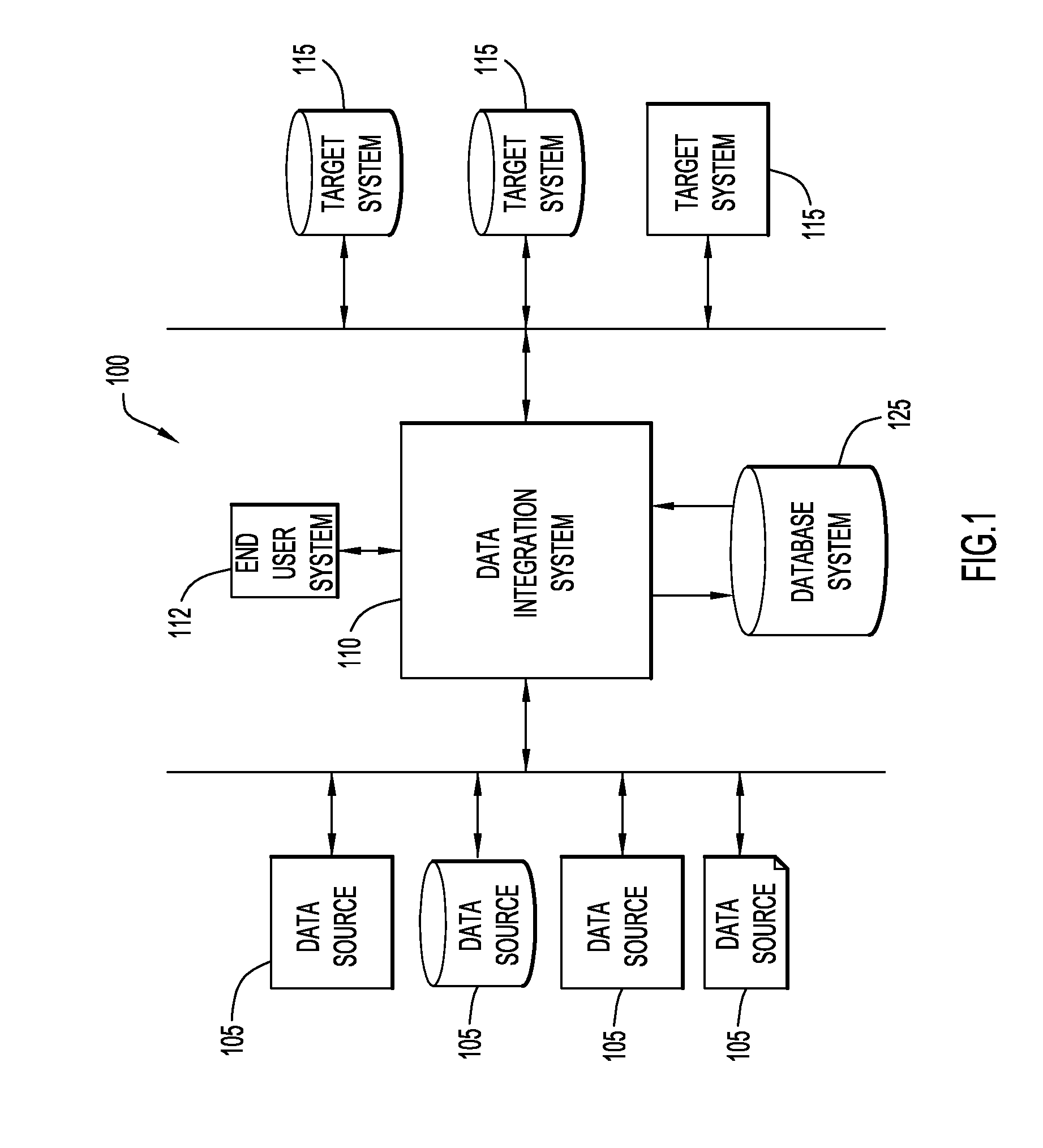
InactiveUS20120131481A1Digital data information retrievalOffice automationInternet privacyData source
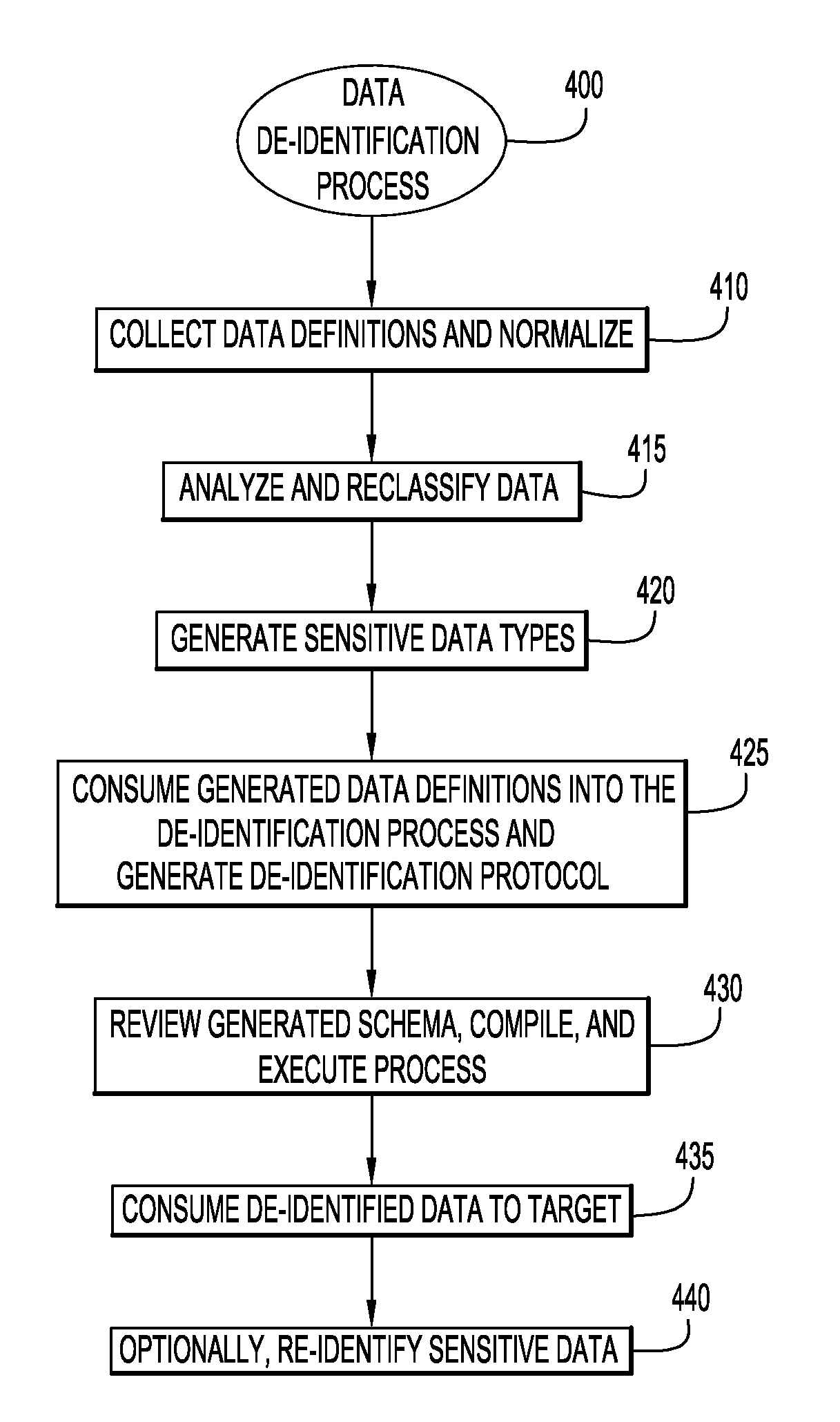
The present invention relates to a method, computer program product and system for masking sensitive data and, more particularly, to dynamically de-identifying sensitive data from a data source for a target application, including enabling a user to selectively alter an initial de-identification protocol for the sensitive data elements via an interface.
Owner:IBM CORP
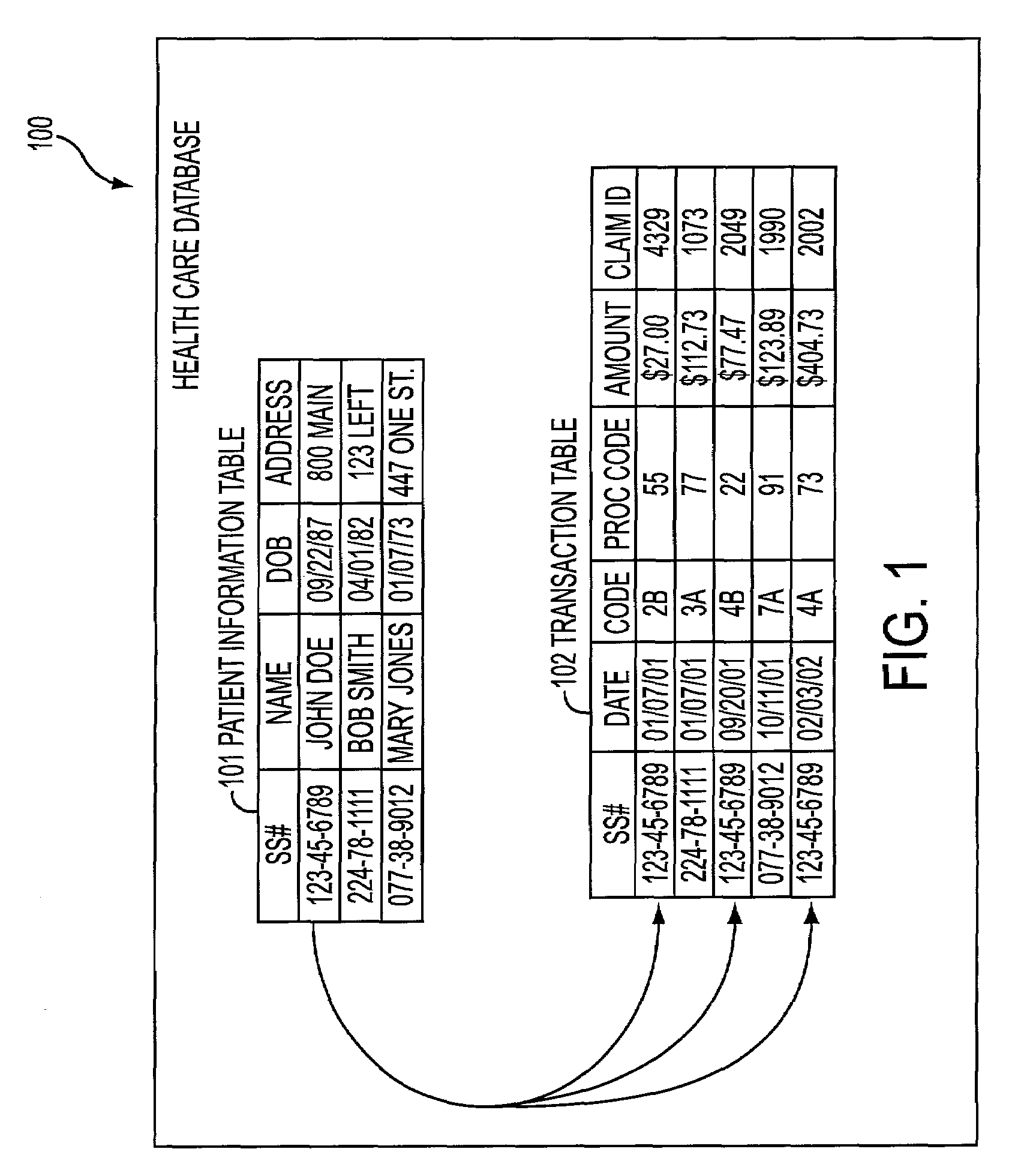
Managing data in compliance with regulated privacy, security, and electronic transaction standards
InactiveUS7191463B2Preserving professional confidenceAvoid identificationMedical communicationData processing applicationsElectronic tradingConsent Type
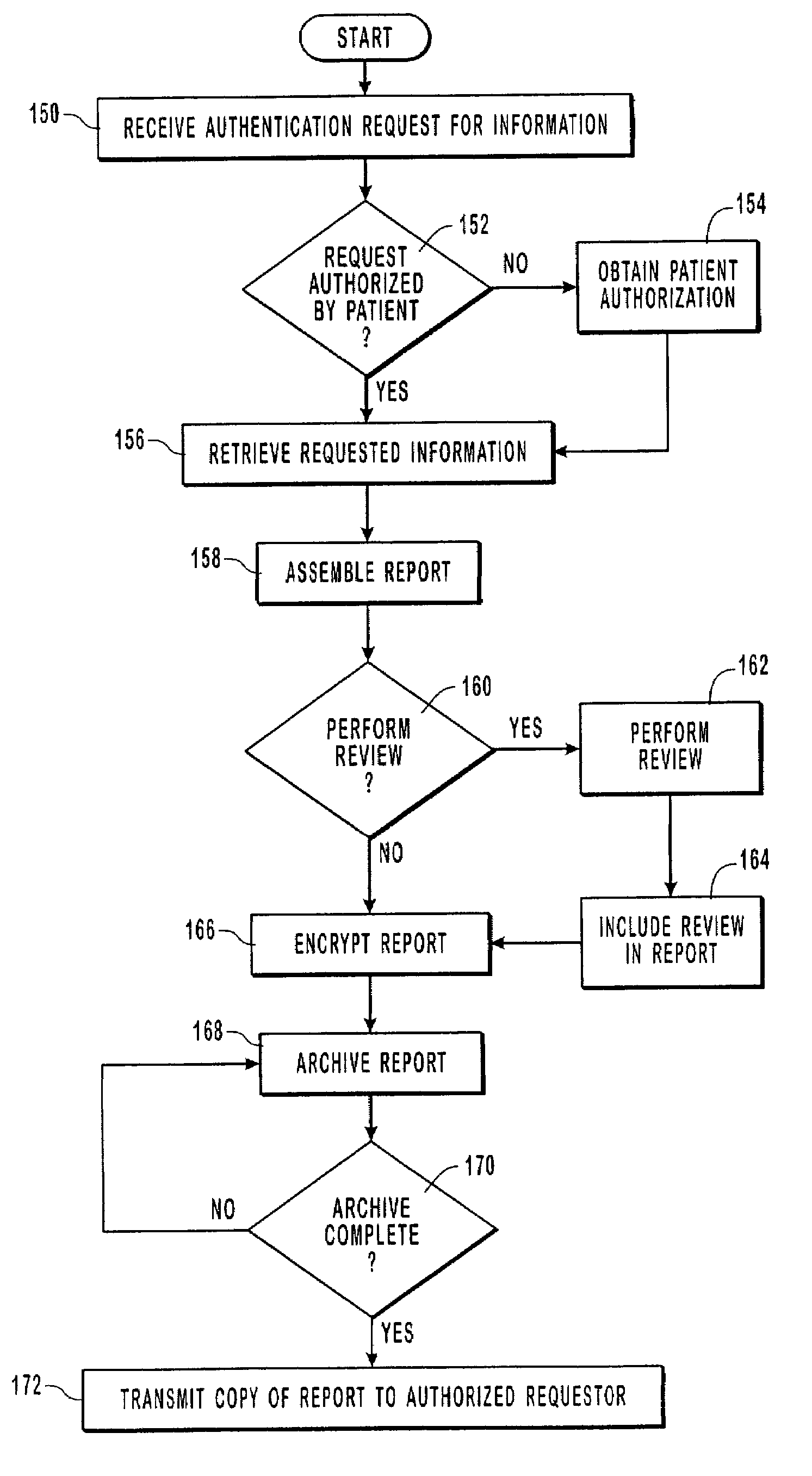
Systems and methods for managing data in compliance with regulated privacy, security, and electronic transaction standards. One or more computer devices are used in a system to manage data in compliance with regulated privacy, security, and electronic transaction standards. In one implementation, a fax machine is used to provide a transmission set to a computer system, which acknowledges receipt of the set and preserves the transmission set for a period of time to satisfy a regulation. The system includes a single point of entry for external and / or internal requests, and / or a single point of exit for transmissions of information, wherein the transmissions include individually identifiable patient information to legitimate patient-approved requests. Information is de-identified so as to be selectively used and / or sold. The de-identification prevents the identification of patients corresponding to the medical information, thus allowing the information to be useful while still preserving professional confidences. Moreover, digital authorizations and consents for retrieval from external data sources may be utilized.
Owner:VERISMA SYST
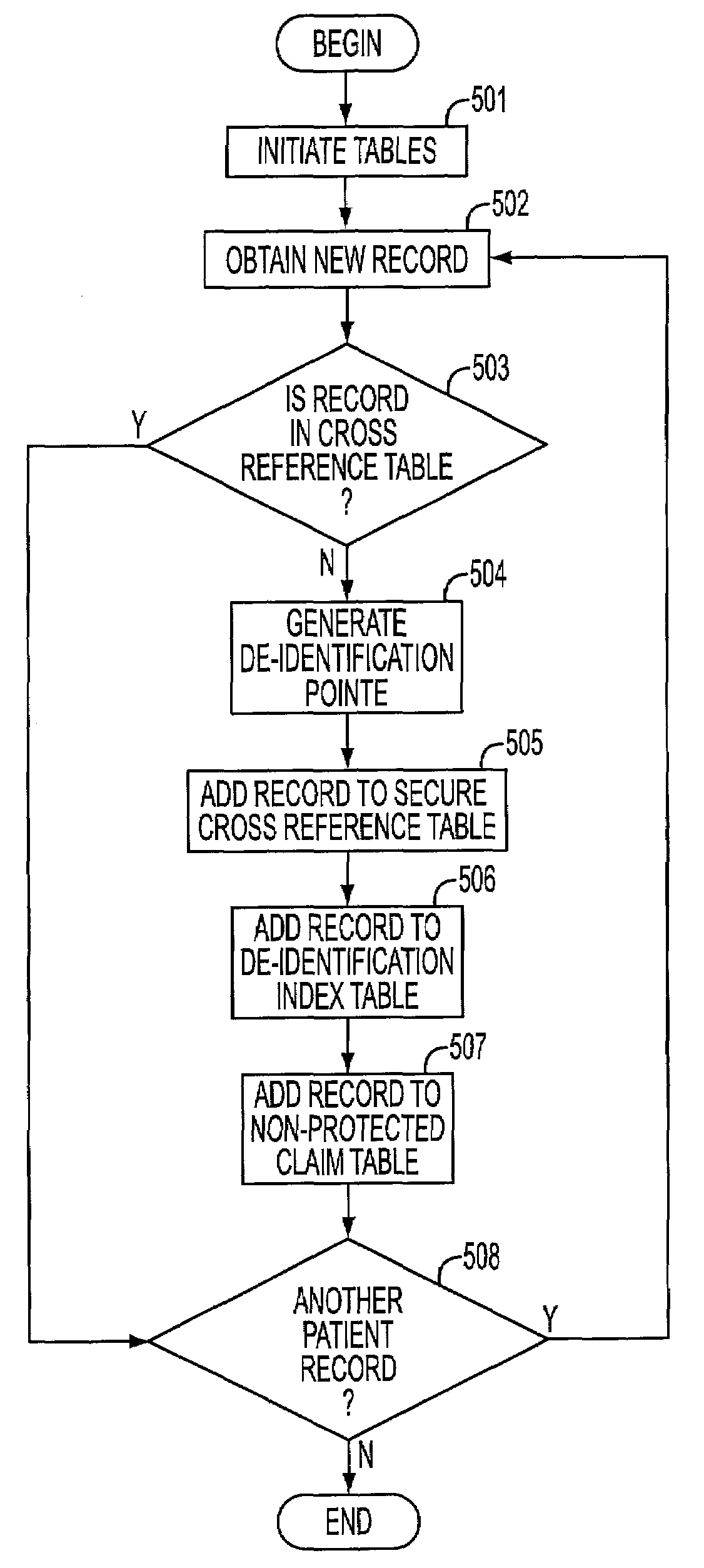
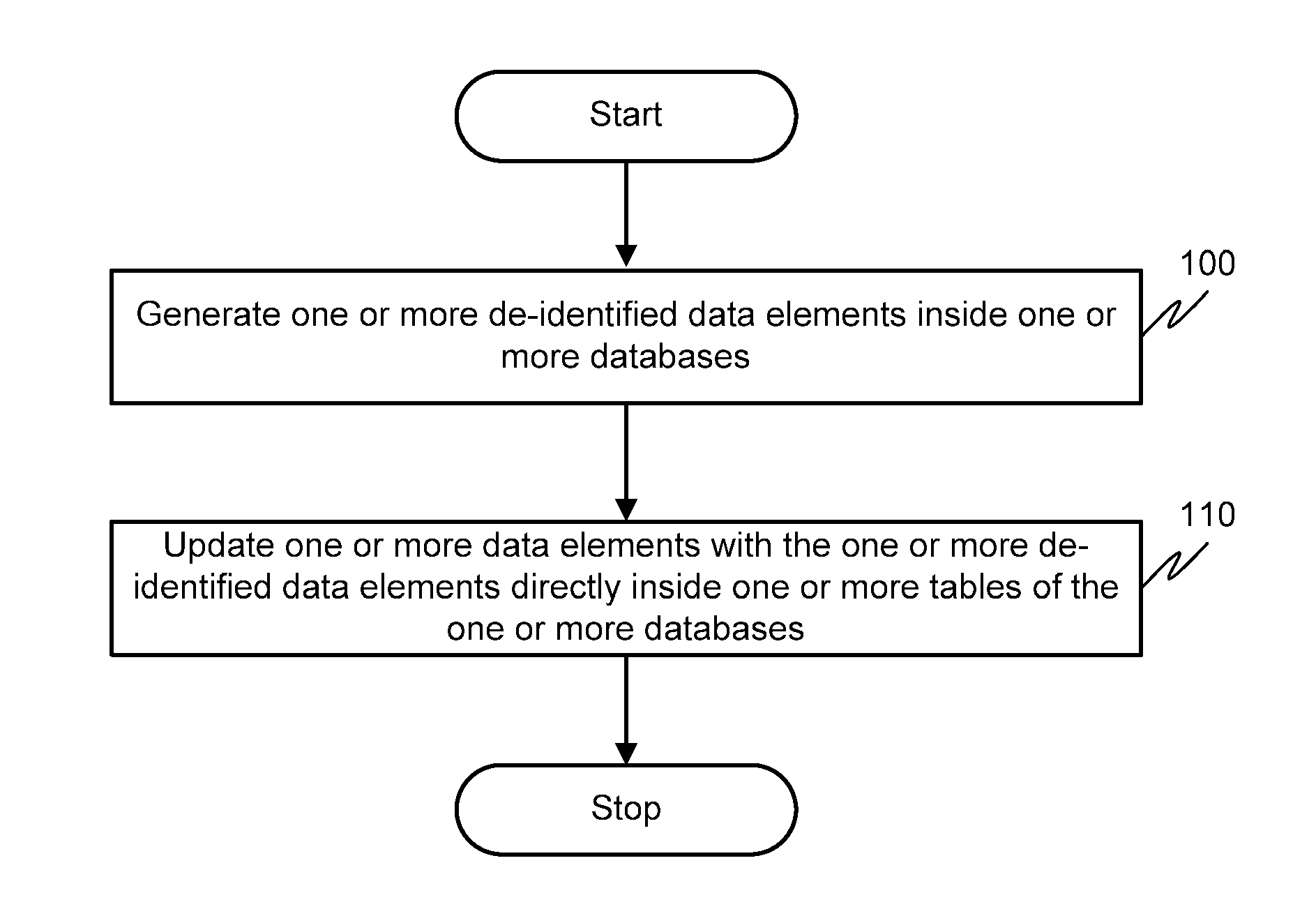
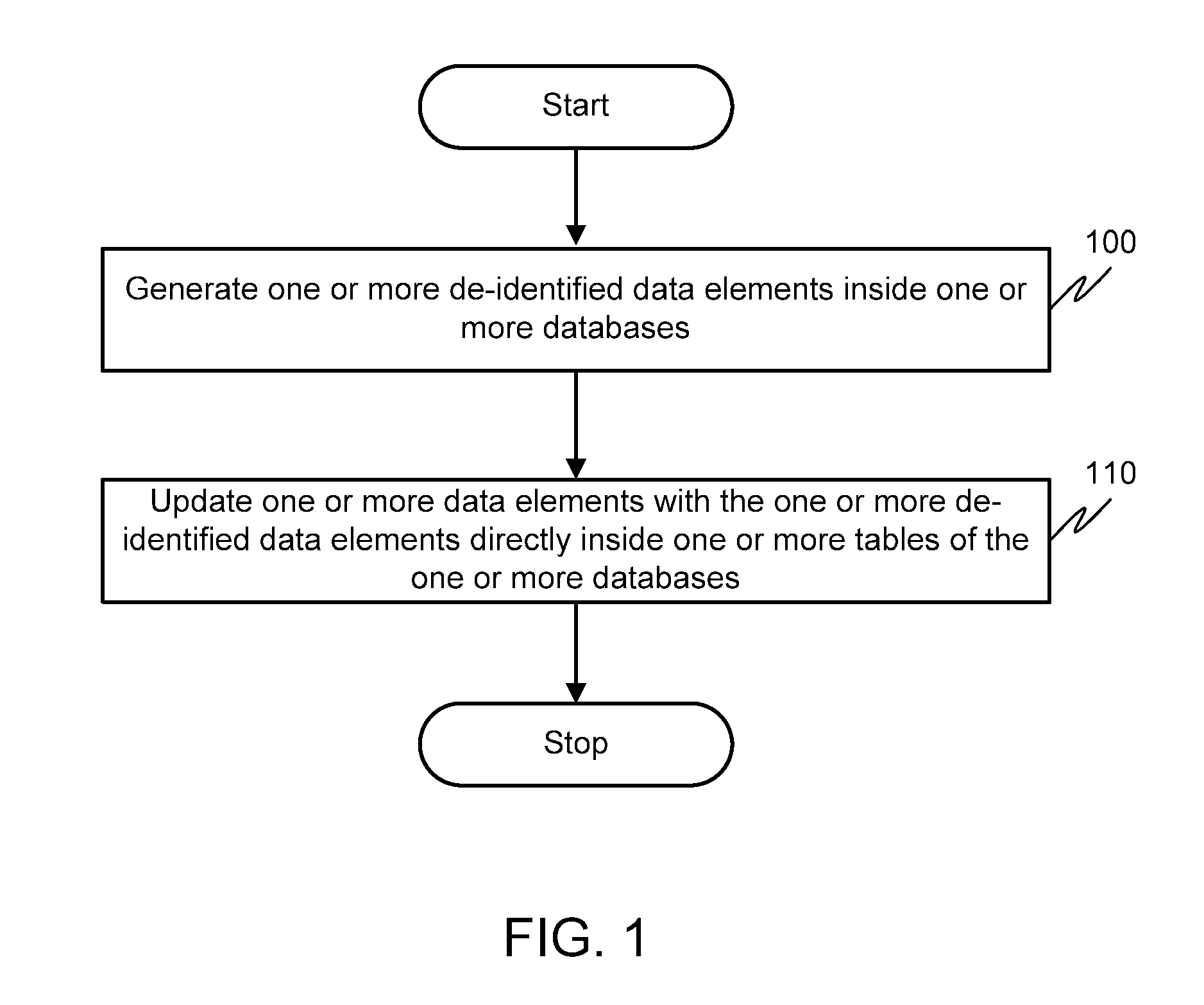
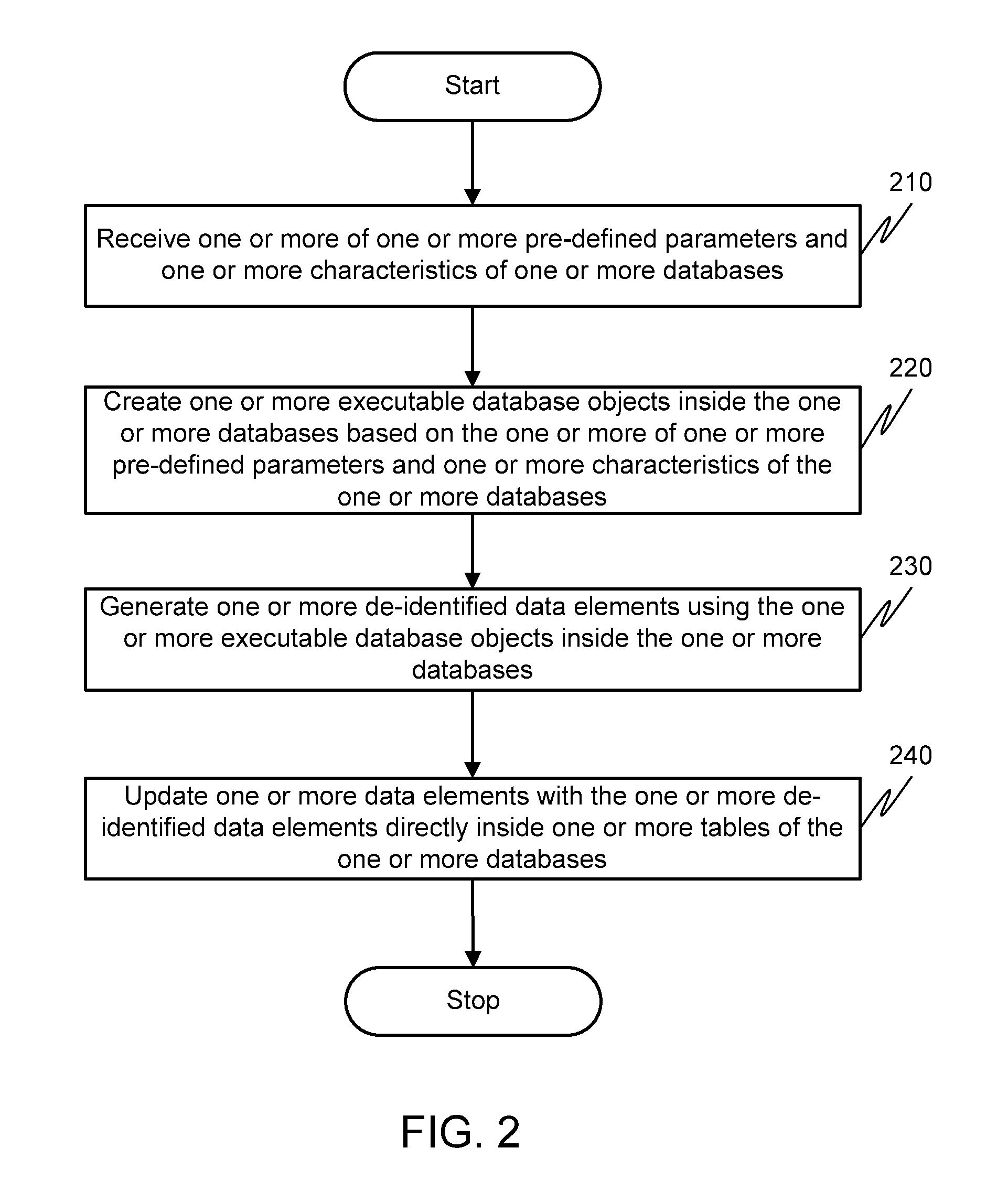
Method and system for de-identification of data within a database
InactiveUS20130080398A1Digital data processing detailsComputer security arrangementsData elementComputer science
A method and system for de-identification of one or more data elements inside one or more tables of one or more databases is disclosed. The method includes generating one or more de-identified data elements inside the one or more databases. Upon generating the one or more de-identified data elements, the one or more data elements are updated with the one or more de-identified data elements. The updating of the one or more data elements is directly performed inside the one or more tables of the one or more databases.
Owner:DATAGUISE
System and method for the protection and de-identification of health care data
ActiveUS9355273B2Digital data protectionPatient personal data managementHash functionInternet privacy
A system for protecting and de-identifying healthcare data includes a storage device for storing the healthcare data and personally identifiable information for a person and a processor in communication with the database. The processor generates an anonymous linking code using a keyed hash function and a second hash function. The anonymous linking code is based at least in part on a portion of the personally identifiable information. The processor further appends the anonymous linking code to the healthcare data for the person.
Owner:IQVIA INC
Implementation method of multifunctional intelligent electronic label management system based on cloud computation
The invention provides an implementation method of a multifunctional intelligent electronic label management system based on cloud computation. A plurality of card swiping terminals, a plurality of labels, a physical intelligent management system and a third-party payment system are used. The method is implemented by virtue of an identify identification device, an identity verifier, a collection device, a web portal and a cloud computation device. The identity identification device is portable equipment with the functions of a noncontact intelligent card. The functions of the noncontact intelligent card are integrated into the portable equipment, thus, a card can be automatically and quickly swiped through the portable equipment; under the processing capability of the portable equipment, a plurality of intelligent cards are integrated, so that 'one-card-multiple-services' can be really achieved. With the web portal, the scope of the services of the identity identification device can be set, changed and canceled, therefore, the payment and verification of various identities can be achieved, such as small amount payment, electronic ticket, sign-in, and entrance guard, and the one-card-multiple-services can be achieved; the method is conveniently popularized, and the problem that one current card is inconvenient to operate due to the fact that only one function is fixed for one card; and the method saves a large quantity of resources, labor and cost.
Owner:张默
System and Method for Cascading Token Generation and Data De-Identification
ActiveUS20160182231A1Multiple keys/algorithms usagePublic key for secure communicationTheoretical computer scienceData element
Owner:MANAGEMENT SCI ASSOC
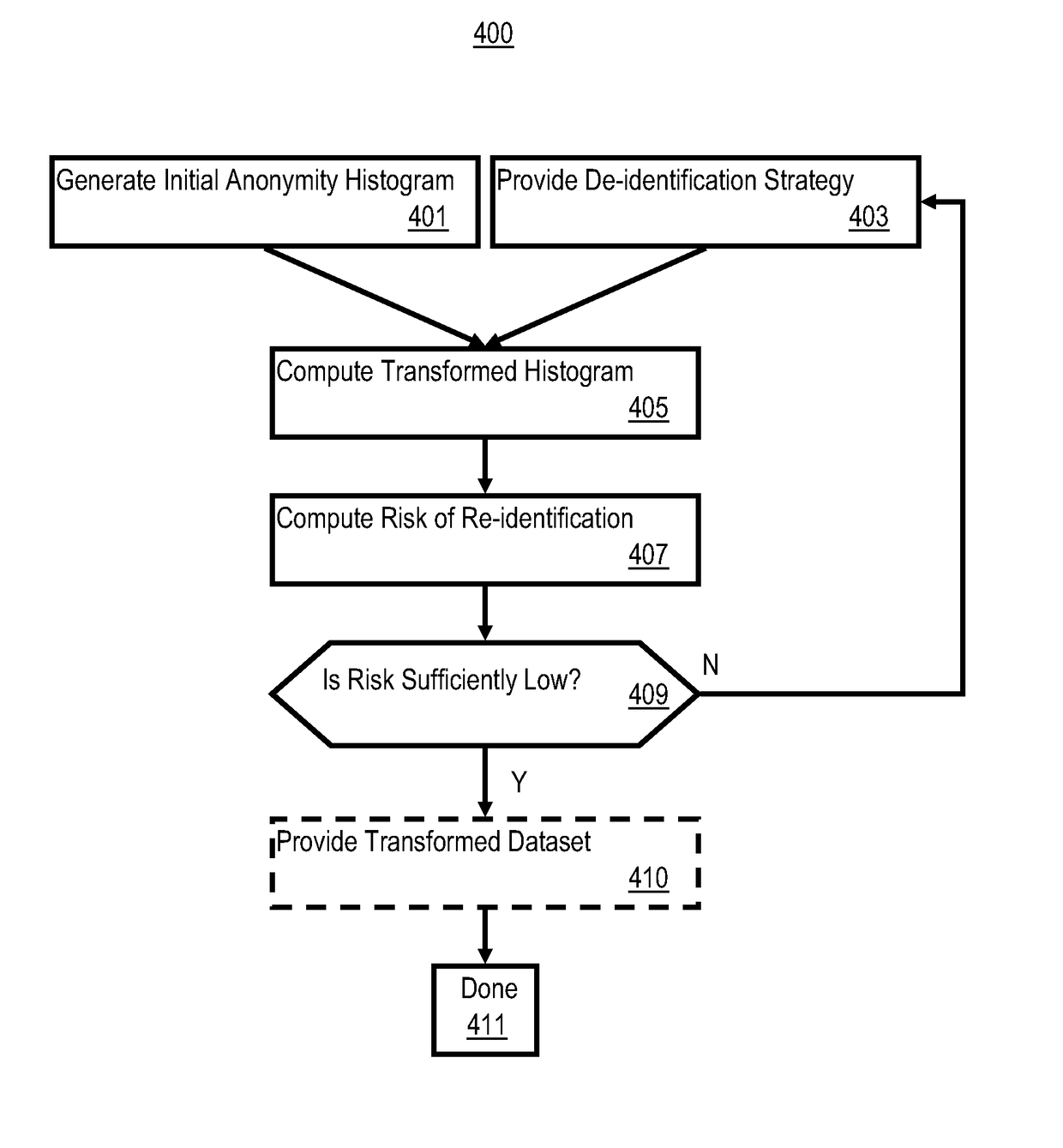
Re-identification risk prediction
ActiveUS20170124351A1Reducing re-identification riskEfficient reductionDigital data protectionTransmissionData setRe identification
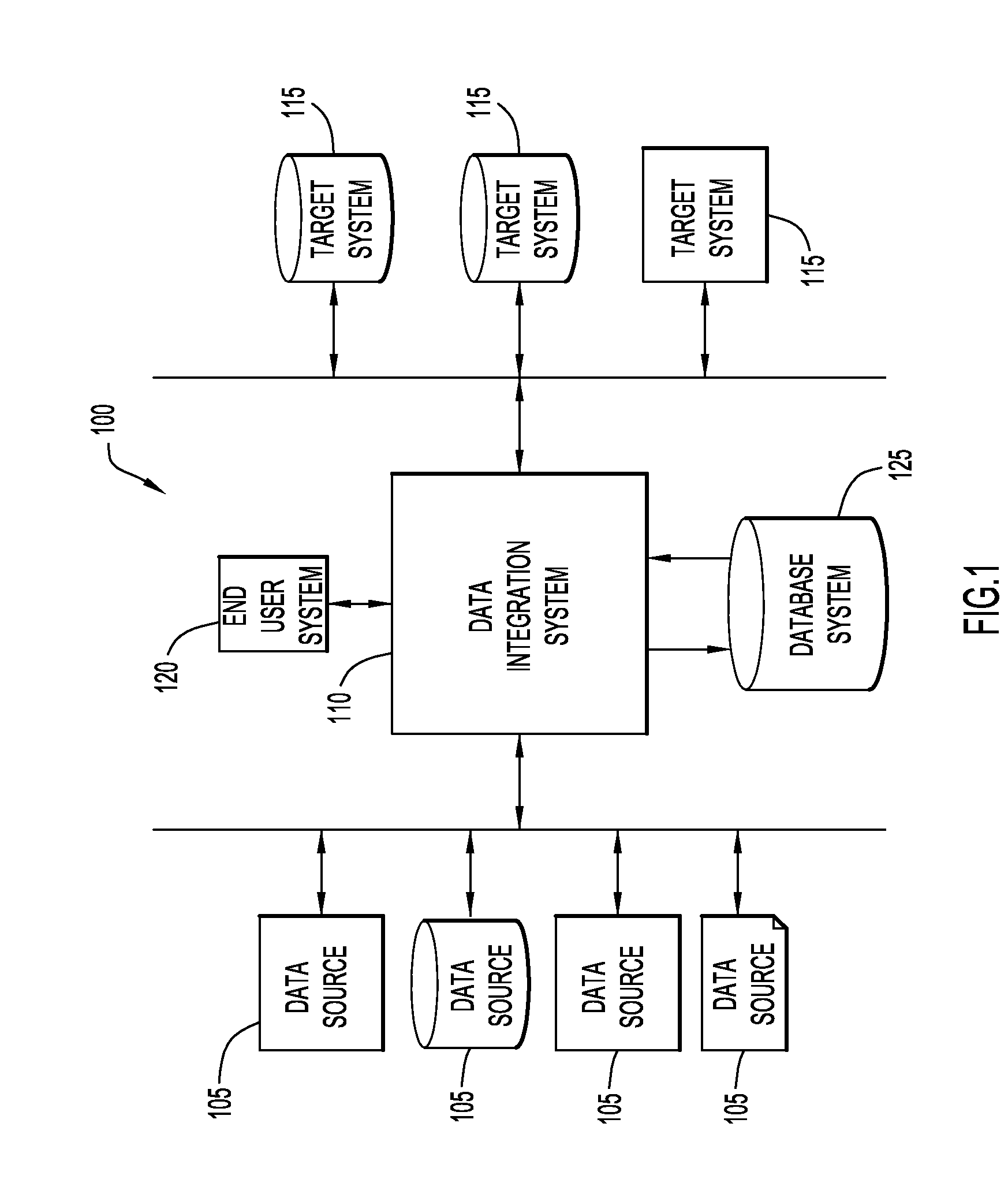
System and method to predict risk of re-identification of a cohort if the cohort is anonymized using a de-identification strategy. An input anonymity histogram and de-identification strategy is used to predict the anonymity histogram that would result from applying the de-identification strategy to the dataset. System embodiments compute a risk of re-identification from the predicted anonymity histogram.
Owner:PRIVACY ANALYTICS
Method and apparatus for de-identification of personal information
ActiveUS20190228183A1Reducing re-identification riskAddressing slow performanceDatabase updatingDigital data protectionData miningDe-identification
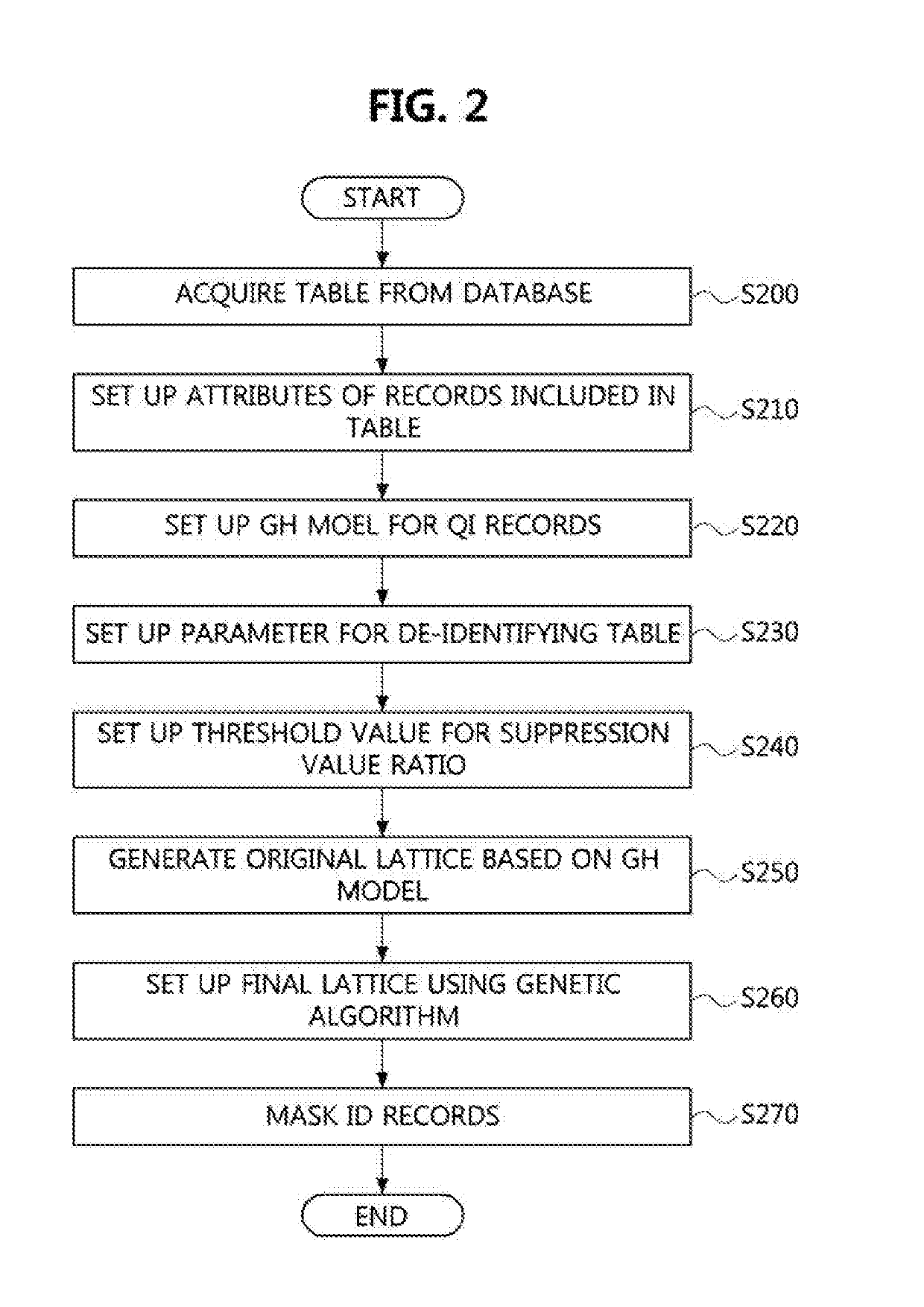
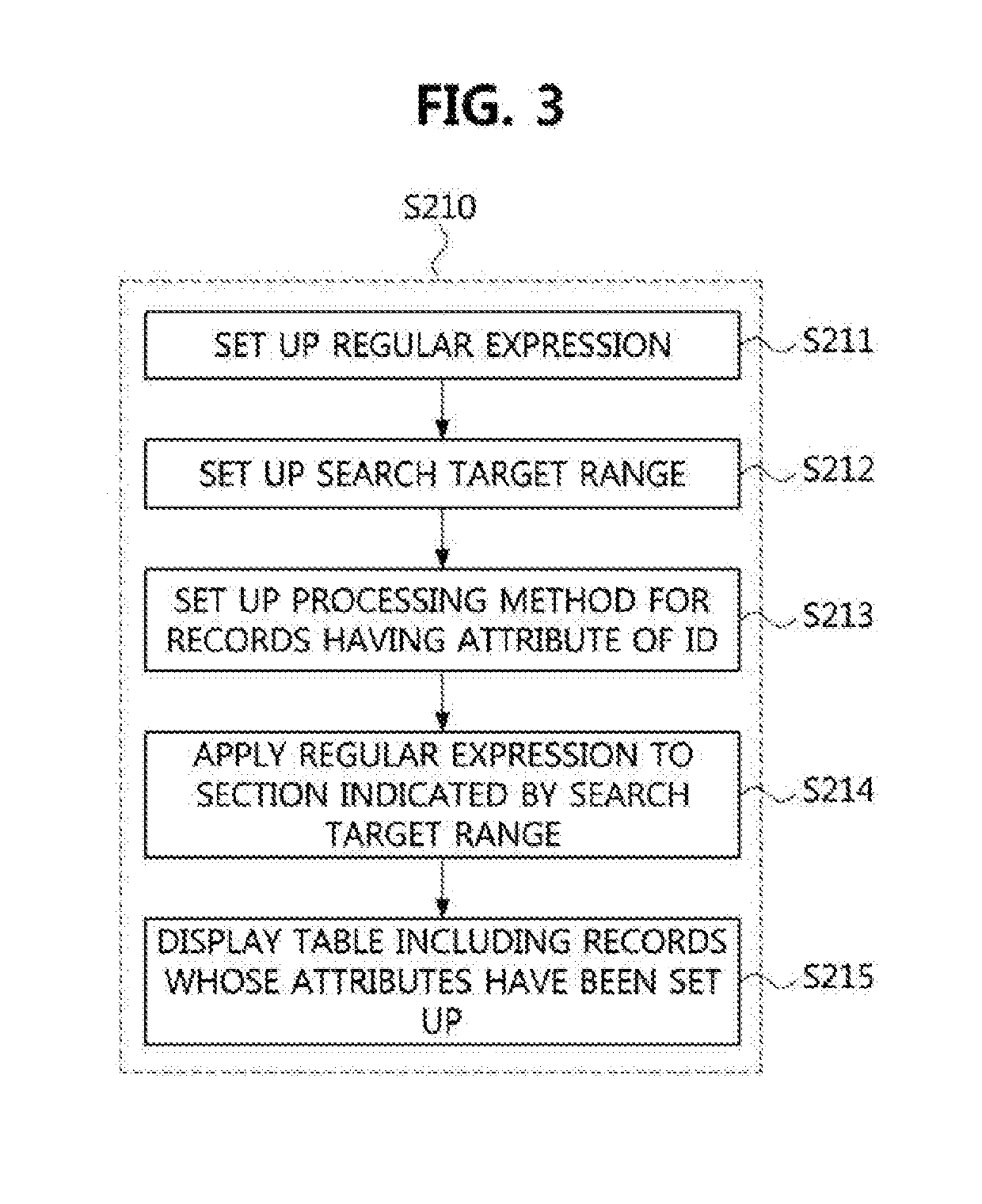
Disclosed are a method and an apparatus for de-identification of personal information. The method for de-identification of personal information comprises the steps of: obtaining, from a database, a raw table including records in which raw data indicating the personal information is recorded; generating generalized data by generalizing the raw data recorded in each of the records included in the raw table; setting a generalized hierarchical model consisting of the raw data and the generalized data; generating a raw lattice including a plurality of candidate nodes on the basis of the generalized hierarchical model; and setting, from among the plurality of candidate nodes included in the raw lattice, a final lattice including at least one candidate node satisfying a predetermined criterion. Thus, it is possible for the personal information to be efficiently de-identified.
Owner:FASOO COM
Dynamic De-Identification of Data
InactiveUS20120266255A1Digital data information retrievalDigital data processing detailsInternet privacyData source
The present invention relates to a method, computer program product and system for masking sensitive data and, more particularly, to dynamically de-identifying sensitive data from a data source for a target application, including enabling a user to selectively alter an initial de-identification protocol for the sensitive data elements via an interface.
Owner:INT BUSINESS MASCH CORP
De-Identification of Data
ActiveUS20120266254A1Digital data processing detailsAnalogue secracy/subscription systemsDe-identificationComputer program
The present invention relates to a method, computer program product and system for de-identifying data, wherein a de-identification protocol is selectively mapped to a business rule at runtime via an ETL tool.
Owner:INT BUSINESS MASCH CORP
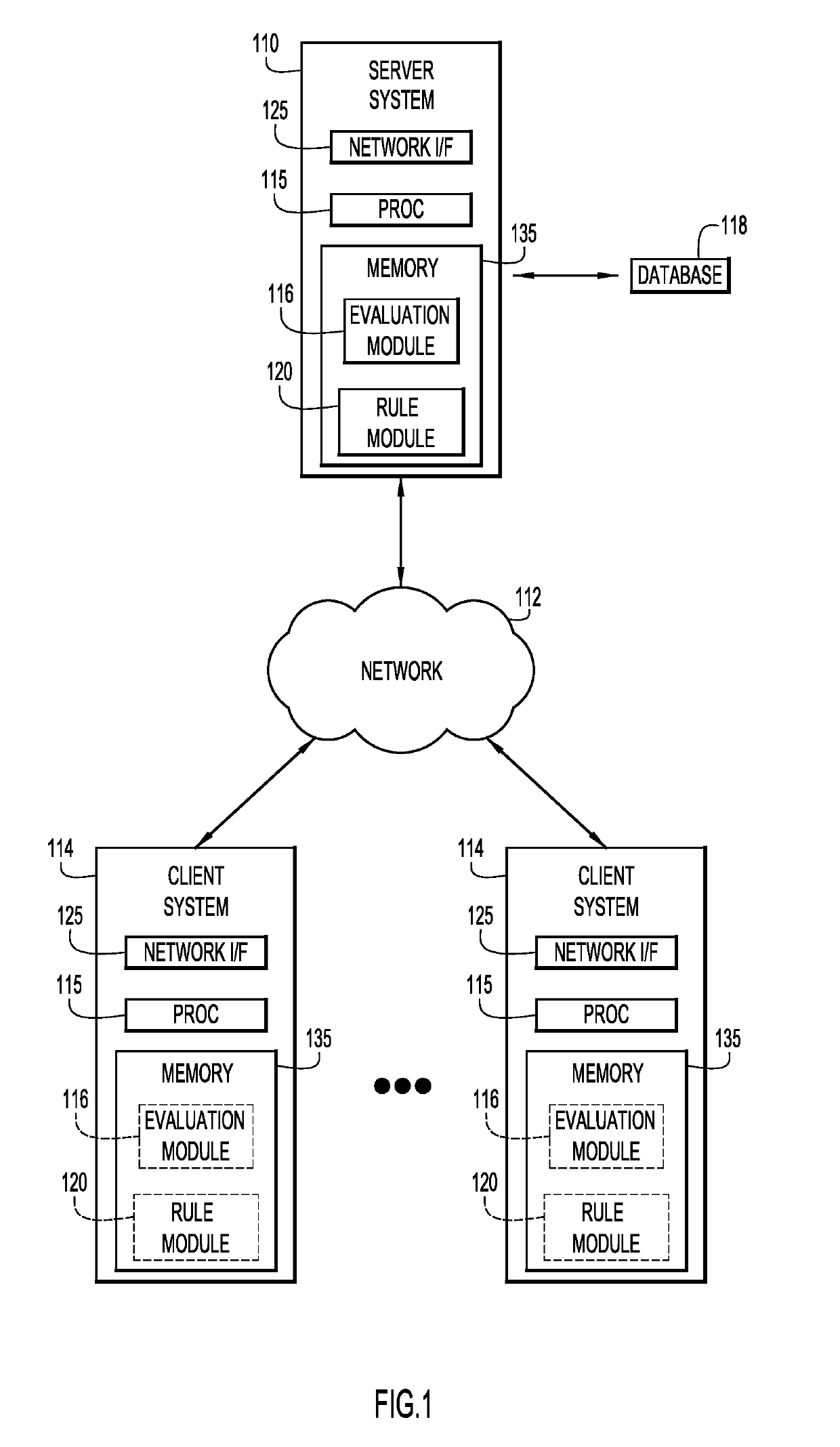
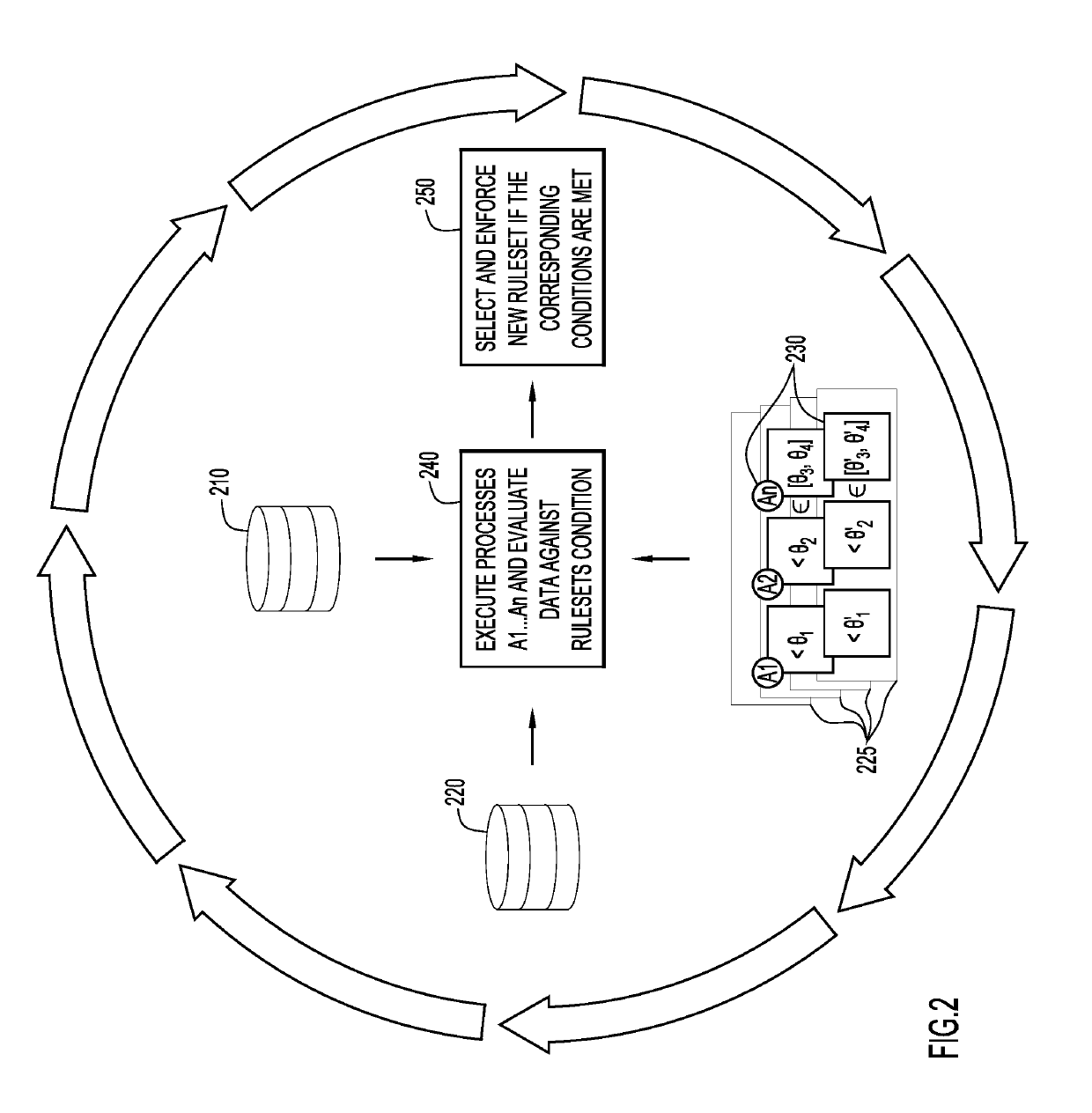
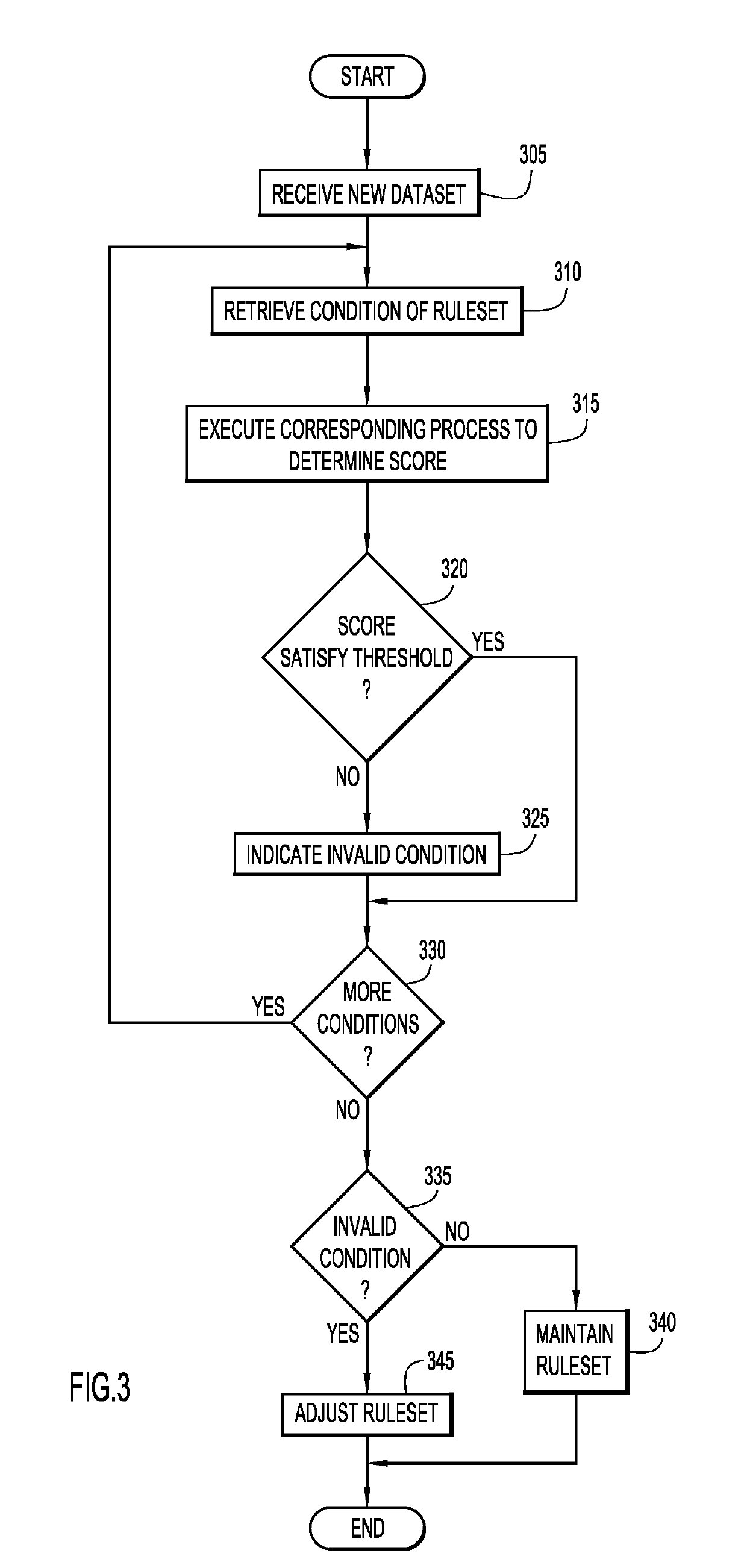
Adaptive statistical data de-identification based on evolving data streams
ActiveUS20190188292A1Sufficient privacy protectionPrivacy protectionDatabase updatingDigital computer detailsDe-identificationData export
A system dynamically changes a data de-identification ruleset applied to a dataset for de-identifying data and comprises at least one processor. The system periodically monitors a dataset derived from data that is de-identified according to a data de-identification ruleset under a set of conditions. The set of conditions for the data de-identification ruleset is evaluated with respect to the monitored data to determine applicability of the data de-identification. One or more rules of the data de-identification ruleset are dynamically changed in response to the evaluation indicating one or more conditions of the set of conditions for the data de-identification ruleset are no longer satisfied. Embodiments of the present invention may further include a method and computer program product for dynamically changing a data de-identification ruleset applied to a dataset for de-identifying data in substantially the same manner described above.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com