Verification method for software upgrading of a security-critical system
A technology of system software and verification method, which is applied in the field of verification of safety-critical system software upgrades, to alleviate the contradiction of limited on-site test time and ensure quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described below in conjunction with accompanying drawing.
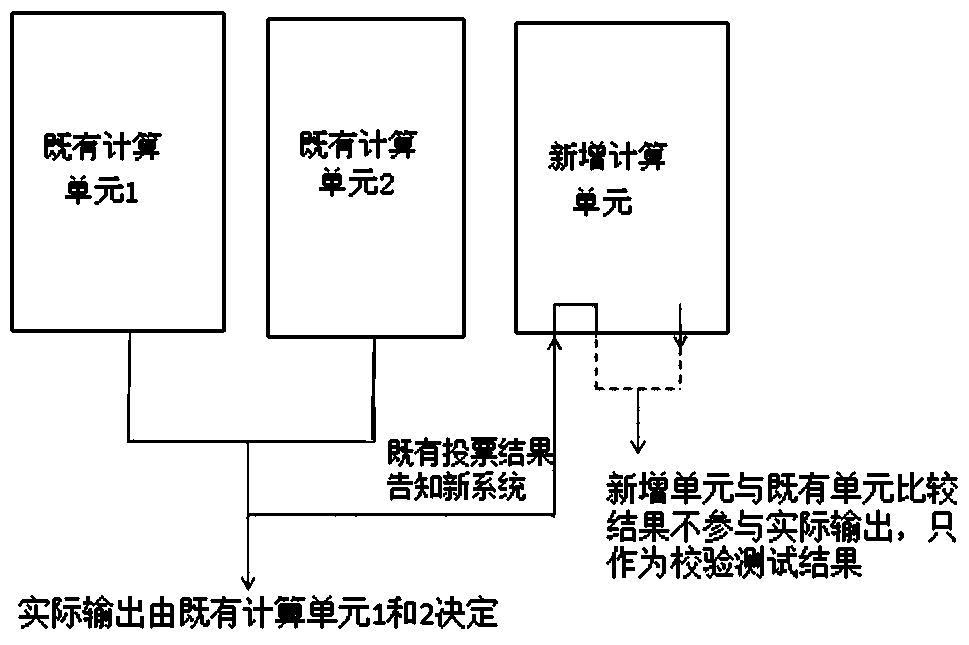
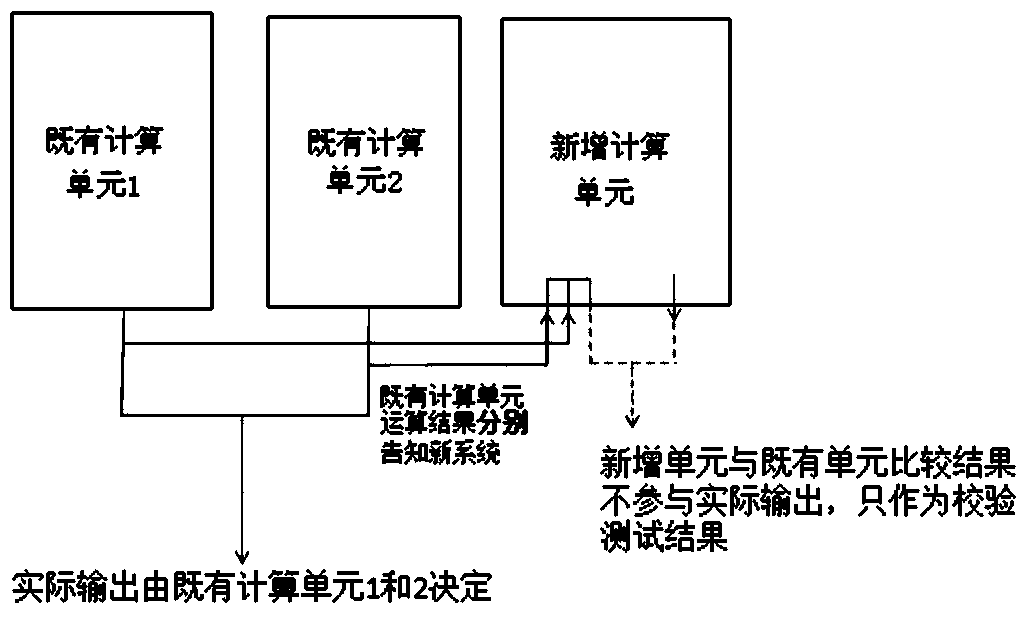
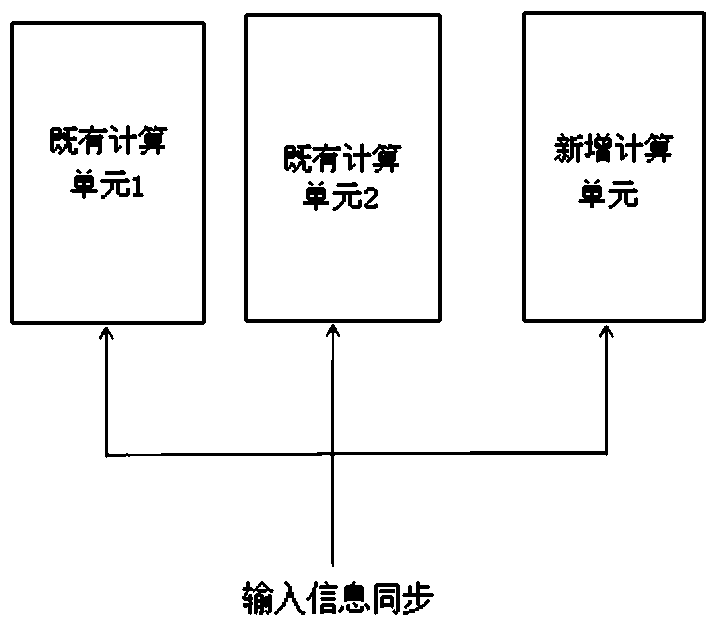
[0033] Redundancy provides system availability, that is, both systems A and B can perform the same task and achieve the same function. Under normal circumstances, system A works, and system B is always ready to take over from system A, but does not participate in the execution of the task. Once system A fails, system B immediately receives tasks to ensure that the system continues to operate normally.
[0034] The purpose of verification is to alleviate the security hazards caused by random failures. For the same task, arrange unit A1 and unit A2 with the same function to do it independently at the same time. After finishing, use the results calculated by units A1 and A2 to vote, and adopt the principle of minority obeying the majority. The measure of randomness is probability. From the perspective of probability, the probability of random failure of multiple units at th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com