Traffic analysis method, public service traffic attribution method and corresponding computer system
A public service and traffic analysis technology, applied in the field of network traffic analysis, can solve problems such as service identification is more difficult, application identification accuracy decline, etc., to achieve efficient identification and improve accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] In order to facilitate the understanding of the technical solution proposed in this application, several elements that will be introduced in the description of this application are firstly introduced here. It should be understood that the following introduction is only for understanding these elements, so as to understand the content of the embodiments, and does not necessarily cover all possible situations.
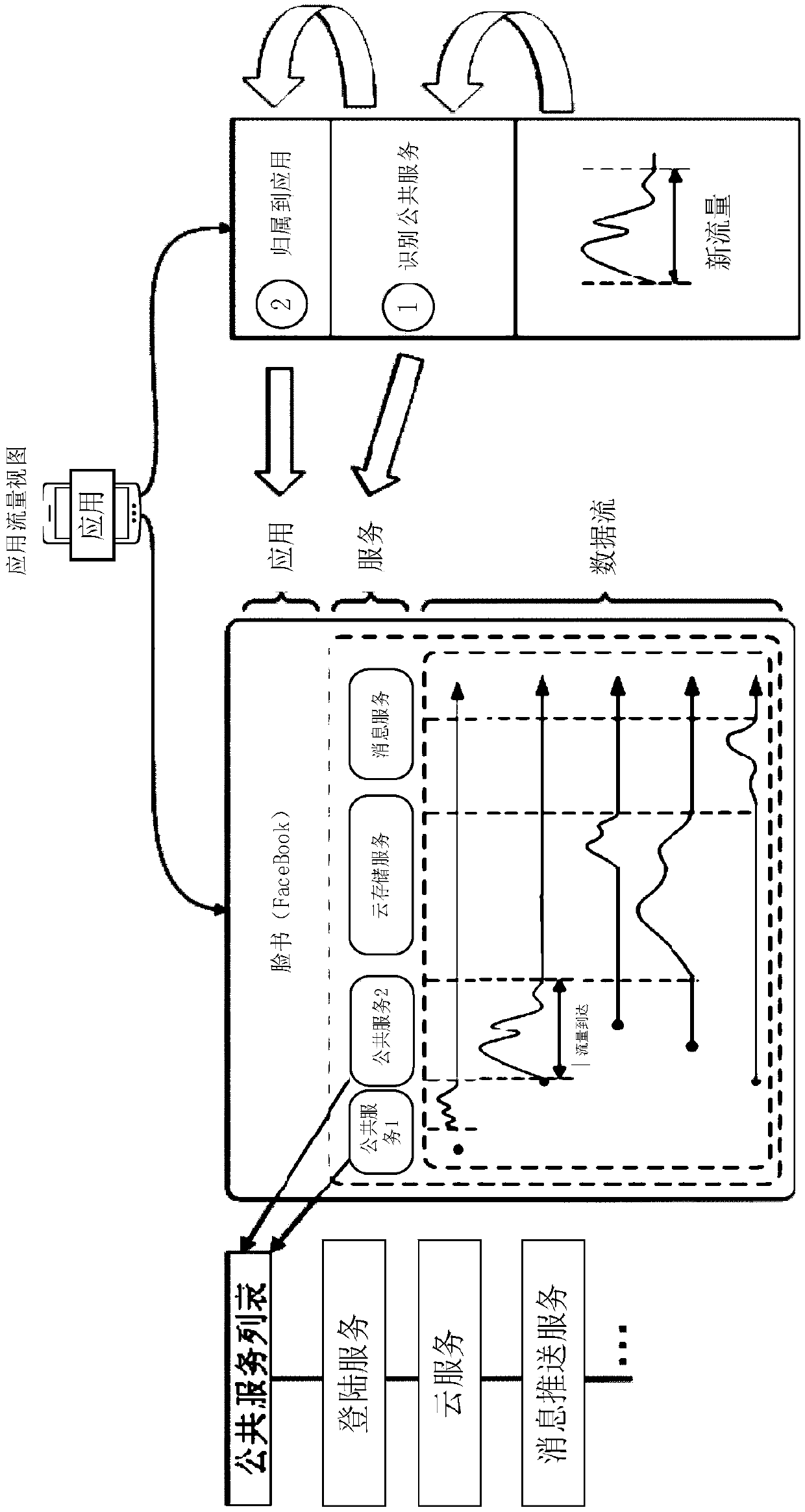
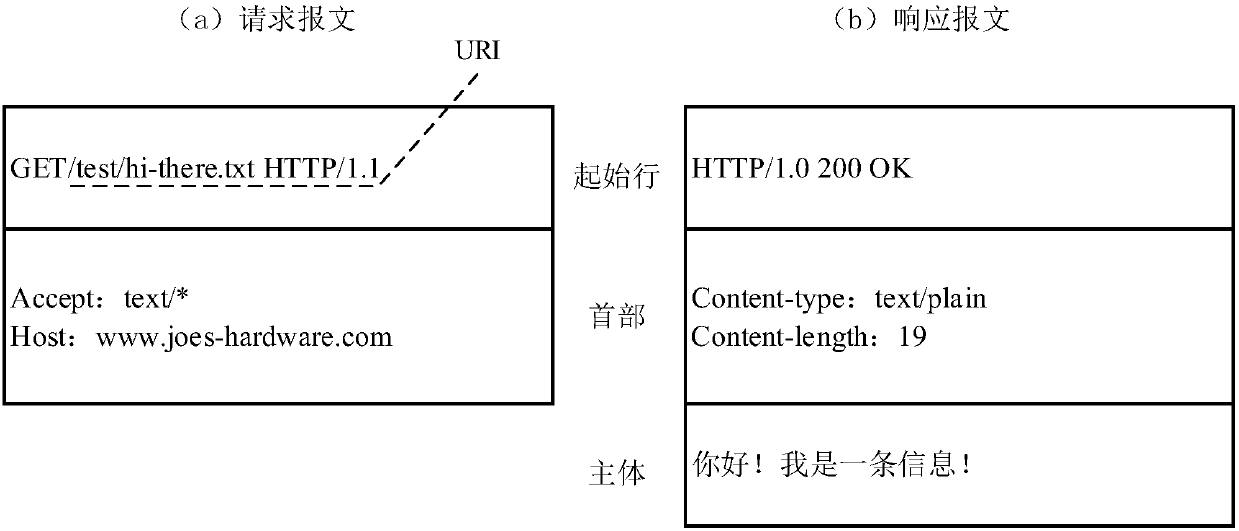
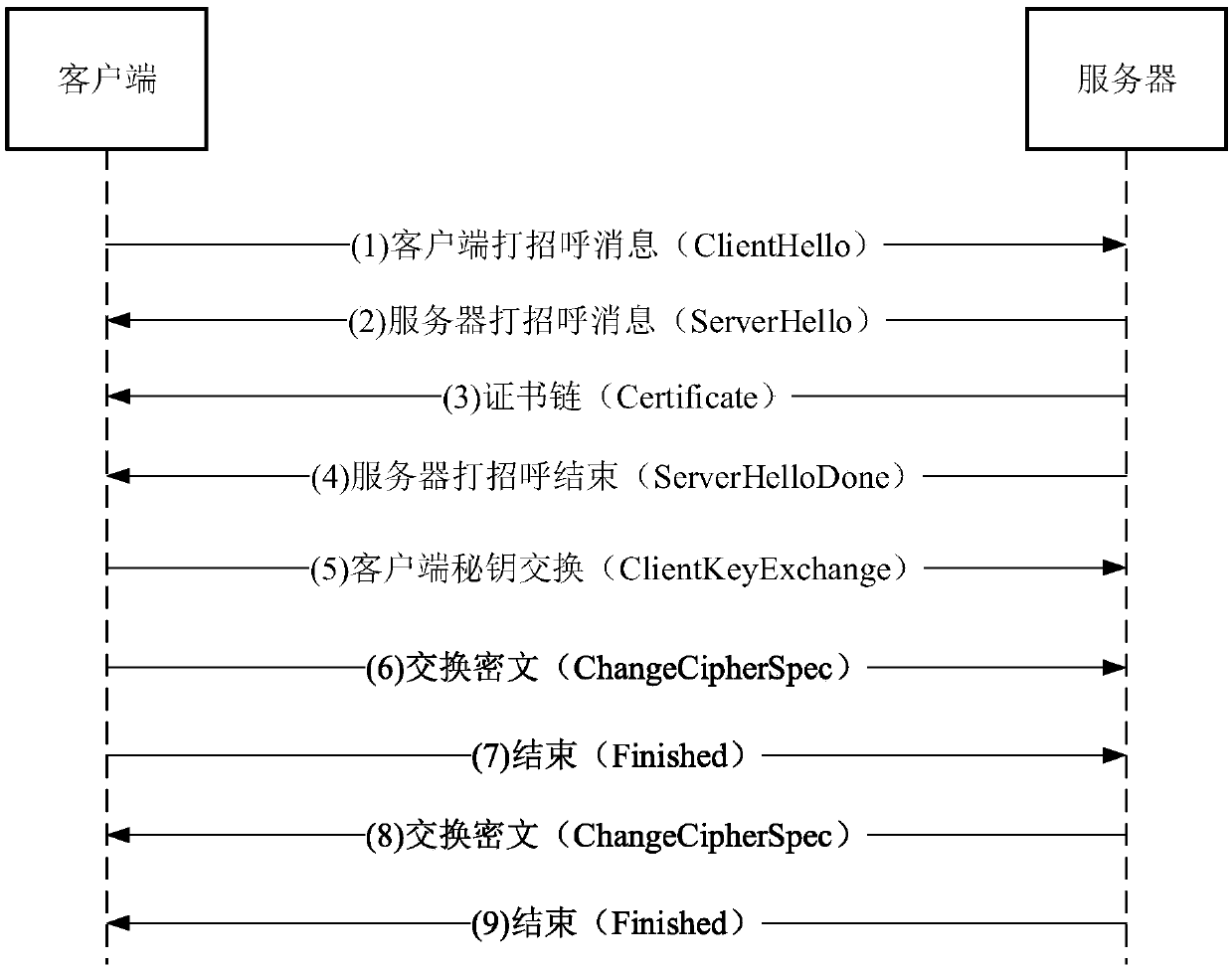
[0067] Traffic: Interaction between devices connected through the network will generate network communication packets, which are called traffic. Traffic is a general term.
[0068] Data flow: The data packets generated during a complete communication process between the server and the client (from connection establishment to connection end), are called the data flow of the connection. During the application process, multiple interactions are usually performed, so multiple interactions will be generated. Data streams form application traffic.
[0069]For example,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com