A log-based method and system for proving control flow of embedded devices
An embedded device and control flow technology, applied in file systems, file system types, instruments, etc., can solve problems such as difficulty in verifying embedded devices, lack of key security storage, and inability to protect key security, etc. The effect of key leakage, improving security, and expanding the scope of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
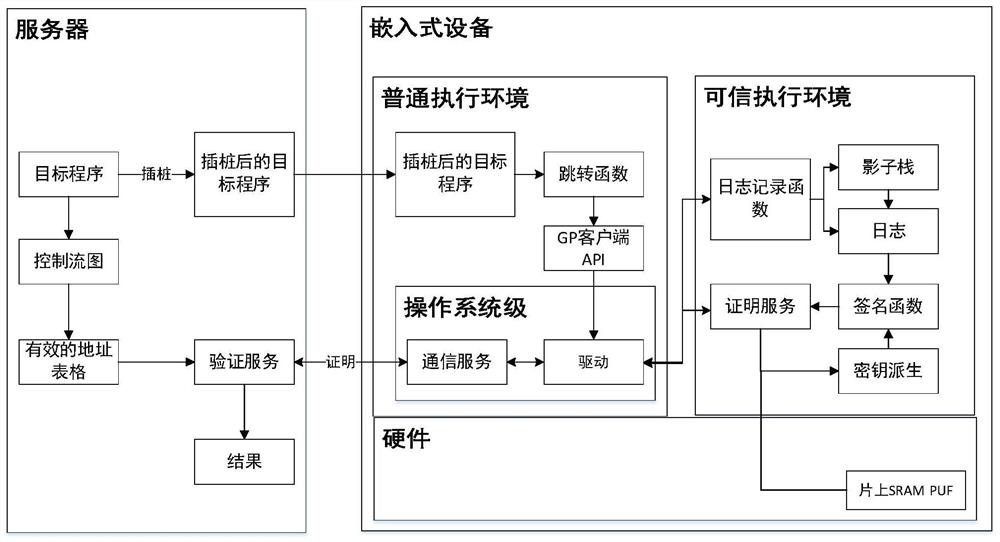
[0034] A log-based embedded device control flow proof method adopted in the present invention is based on figure 1 The system implementation shown, its principle steps are as follows:
[0035] 1. Preparation stage
[0036] a) Server and embedded device: First, use the initial code on the embedded device to collect the initial value of the on-chip SRAM on the embedded device and store it on the server, and deploy the logging function, key derivation function and signature function on the embedded device in the trusted execution environment. Among them, the log function is responsible for generating the actual log, the key derivation function is responsible for generating a key pair by using the SRAM PUF and the random number sent by the server, and the signa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com