Agent user detection method based on communication behavior portrait
A detection method and user technology, applied in the field of network security, can solve problems such as low versatility, high detection false alarm rate, performance loss, etc., and achieve the effect of strengthening security defense, low detection false alarm rate, and high versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
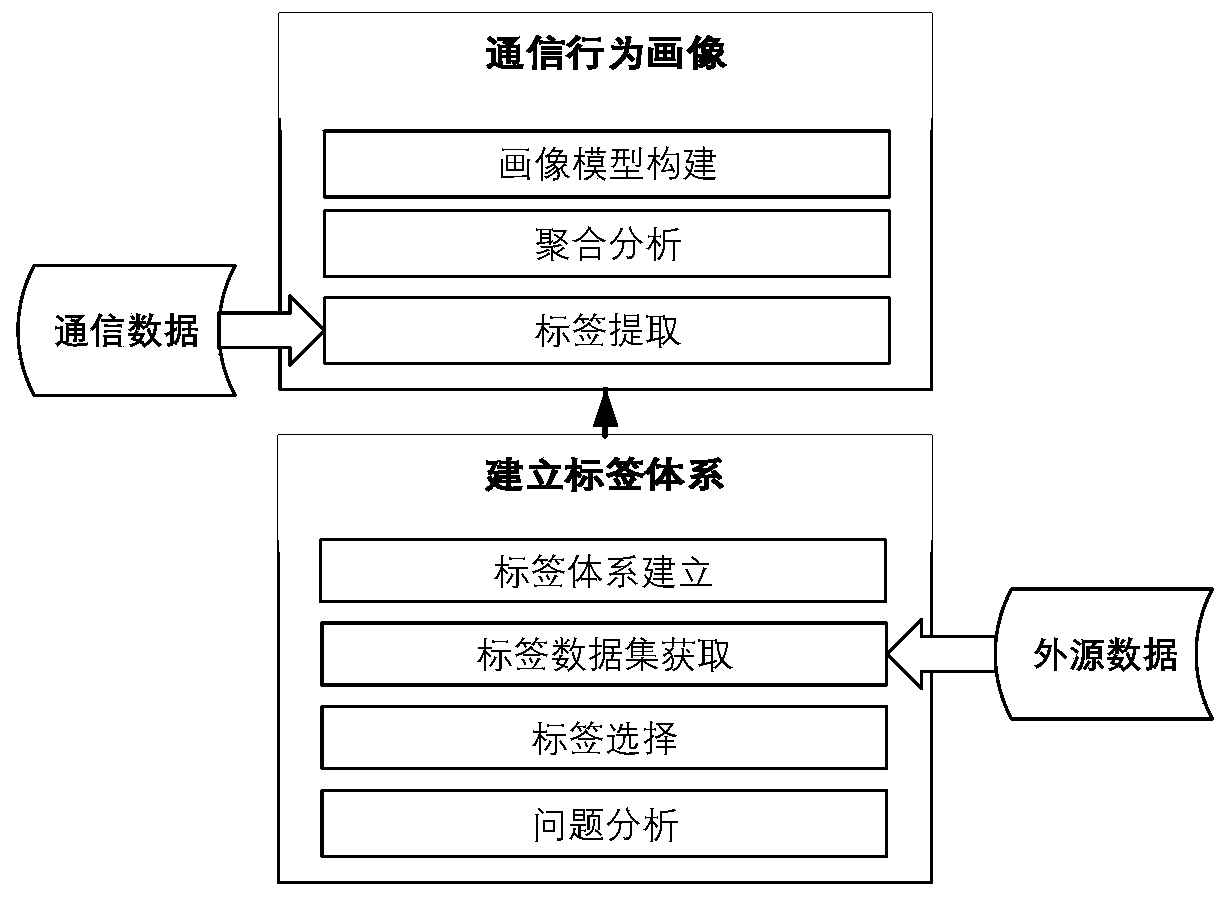
[0024] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. The method of the invention introduces the portrait technology into network behavior analysis, and conducts differentiation research and feature extraction between network objects from the perspective of portraits. Define the portrait target object as O, O={label 1 , label 2 ... label n},n≥1, where label={pf 1 , pf 2 ...pf m}, m≥1, pf represents the image feature. That is to say, any analysis object can be represented by a combination of a series of labels, and each type of label can extract several portrait features through aggregation and comparison analysis, so as to form the final portrait feature set that characterizes the analysis object.
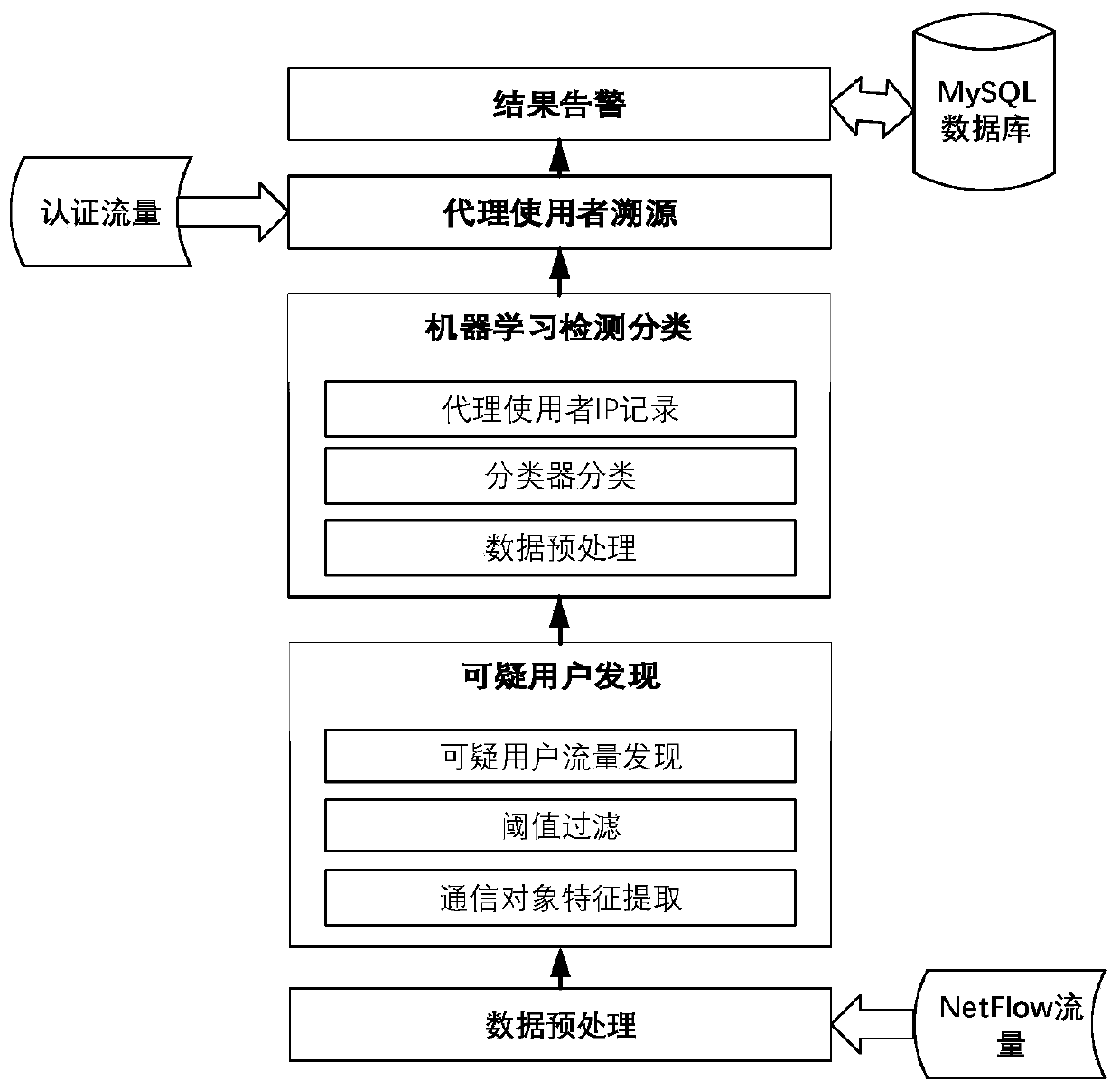
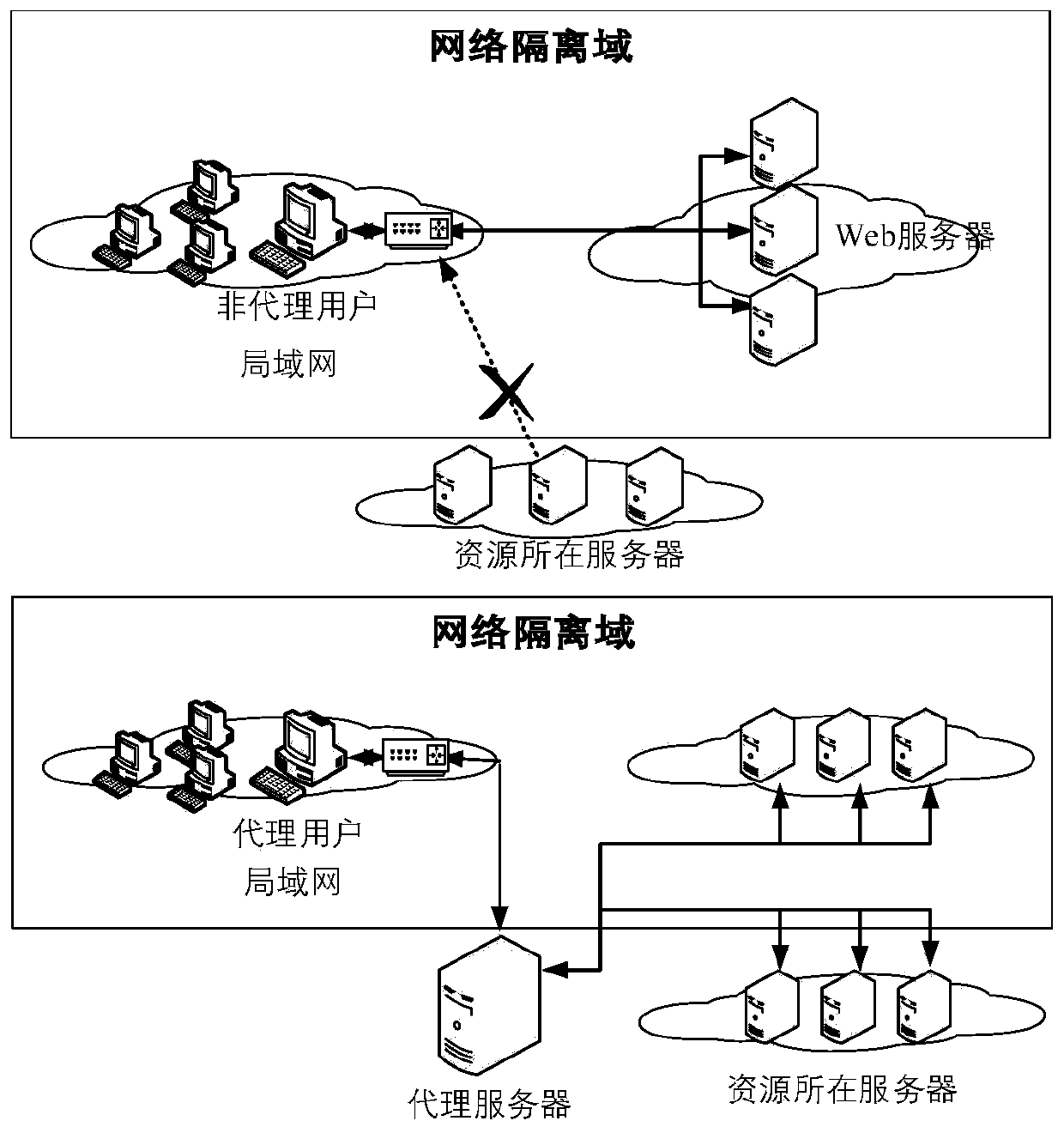
[0025] figure 1 It is a framework diagram of proxy user detection based on communication behavior portrait in the present invention. The framework can realize accurate detection and pos...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com