Logical port authentication for virtual machines
一种逻辑端口、虚拟机的技术,应用在数字数据认证、软件仿真/解释/模拟、仪器等方向,能够解决未虚拟交换机优化等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
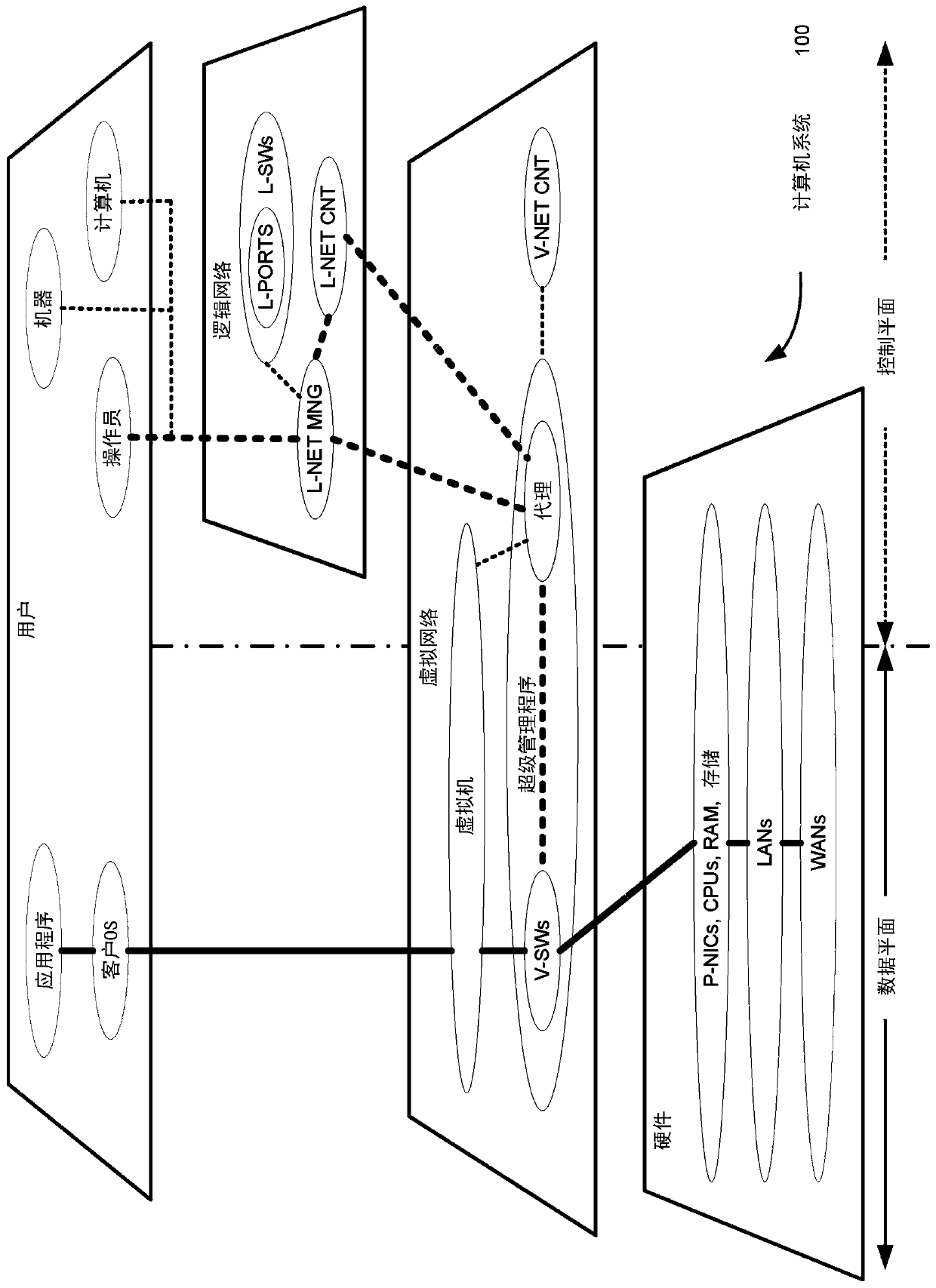
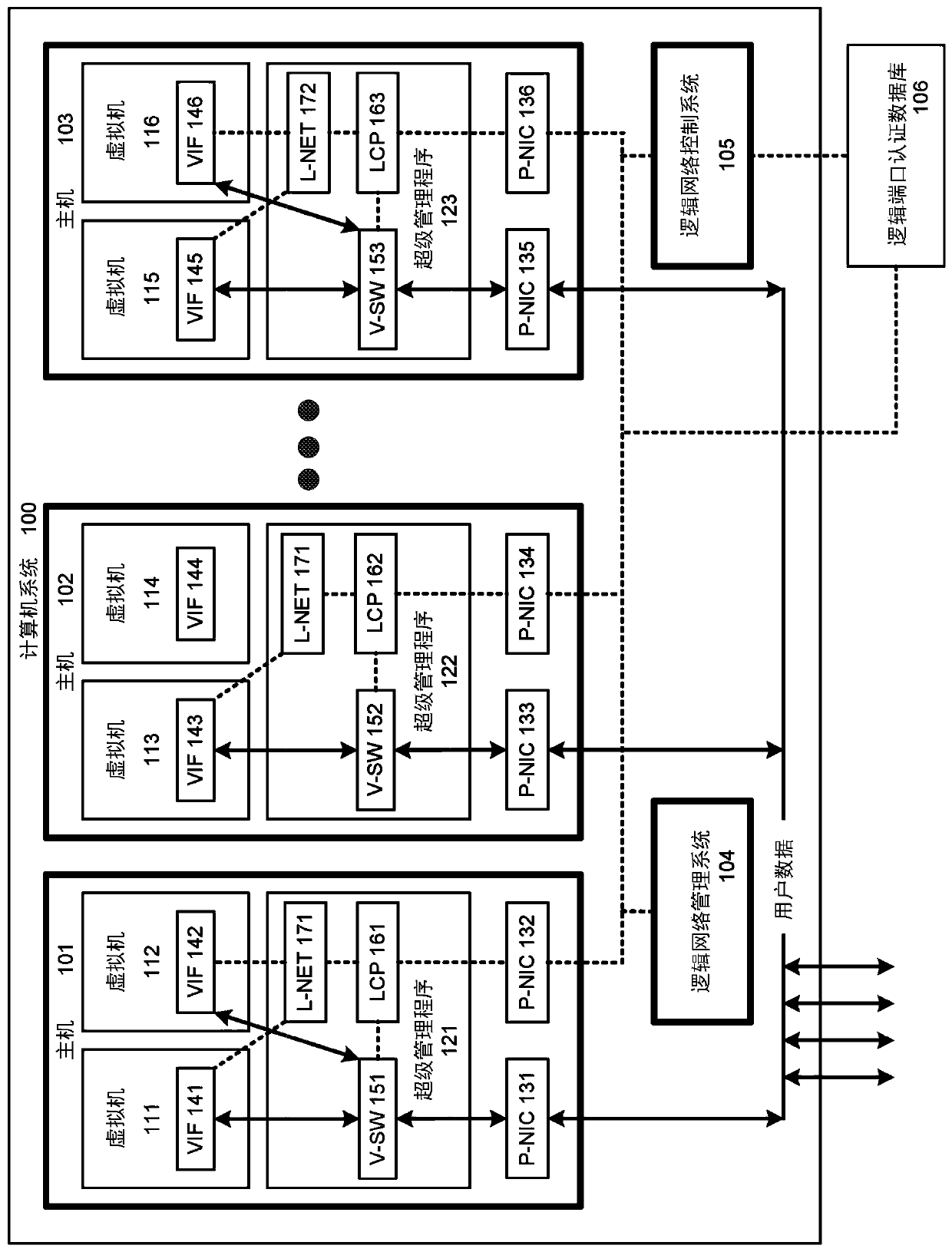
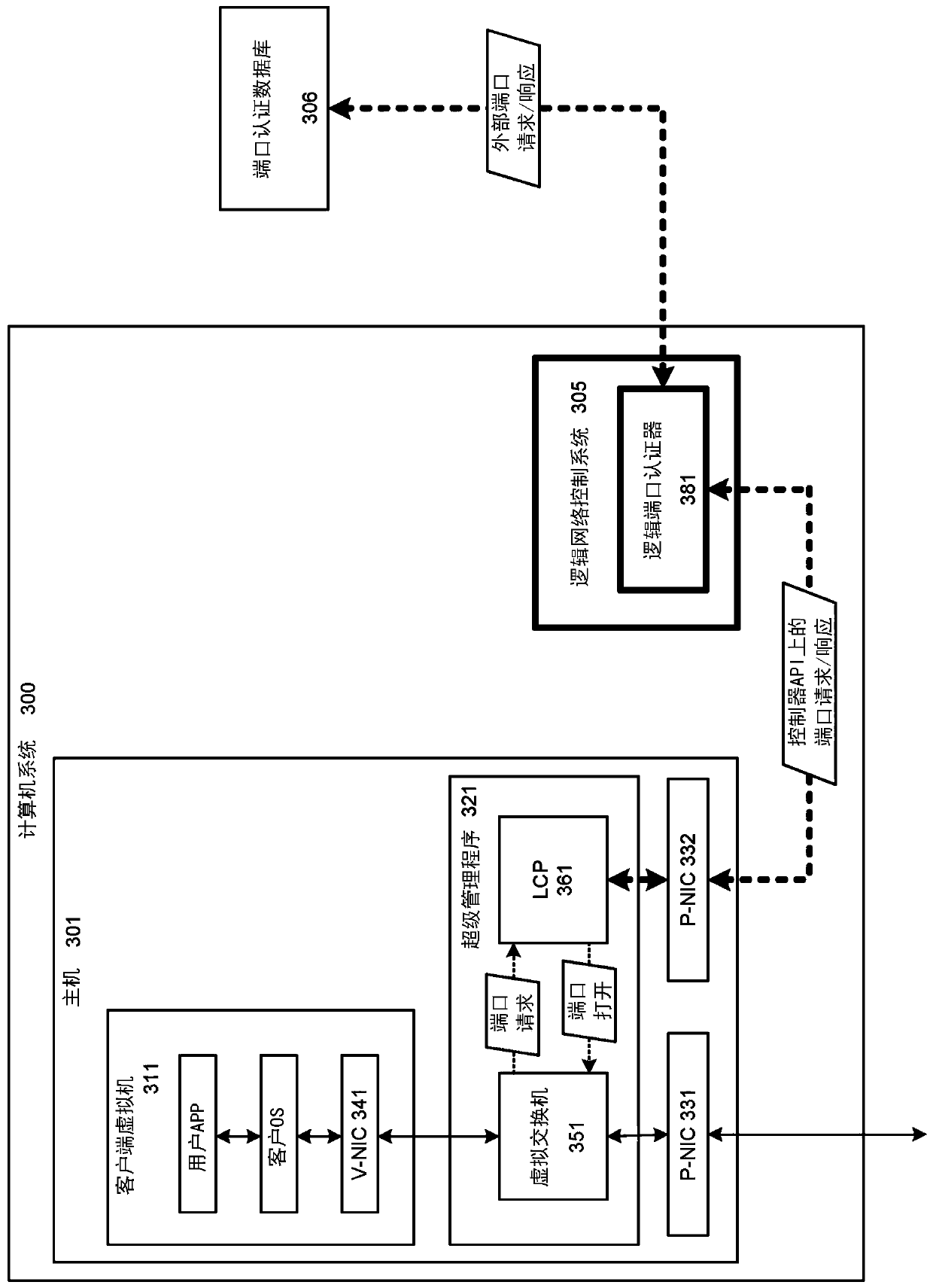
[0019] figure 1 A computer system 100 is shown for authenticating a logical port of a virtual machine. Computer system 100 includes a plurality of host computers configured with software and coupled by a data communications network. exist figure 1 In , the computer system 100 is vertically divided into four layers for users, logical network, virtual network and hardware. Computer system 100 is also divided horizontally into a data plane on the left and a control plane on the right.
[0020] In the data plane, hardware includes the physical network interface (P-NIC), central processing unit (CPU), random access memory (RAM), storage devices, local area network (LAN) and wide area network (WAN). In the data plane, a virtual network includes a hypervisor, a virtual switch (V-SW), and a virtual machine. The user layer in the data plane includes a guest operating system (OS) and user applications.
[0021] In the control plane, the hardware also includes the same or differen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com