A new type of hardware wallet with dismantling and self-destruction
A hardware and wallet technology, applied in the field of digital currency, can solve problems such as theft of private keys, interference of hardware wallets, memory tampering, etc., to achieve a wide monitoring range, improve security, and meet the effects of security protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
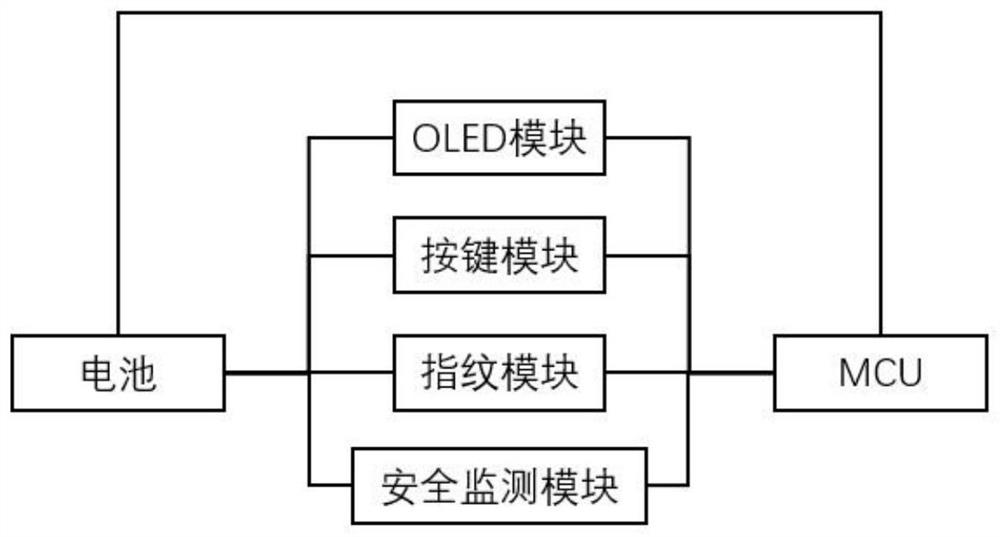
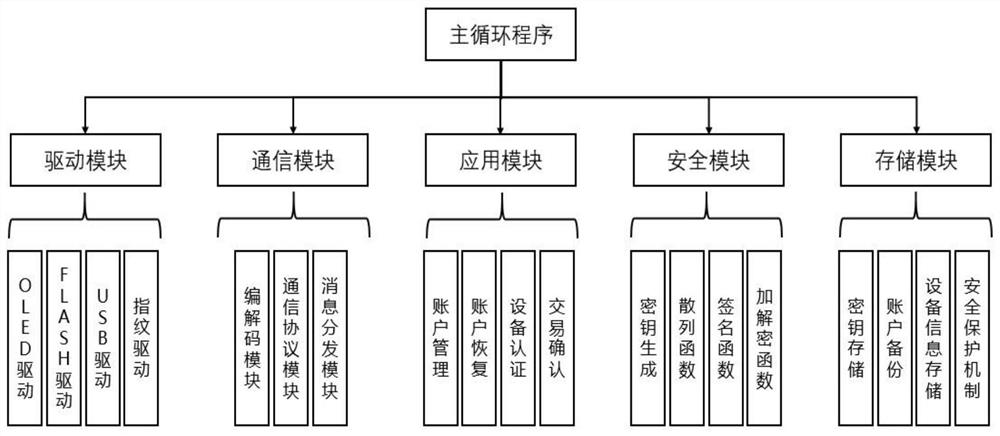
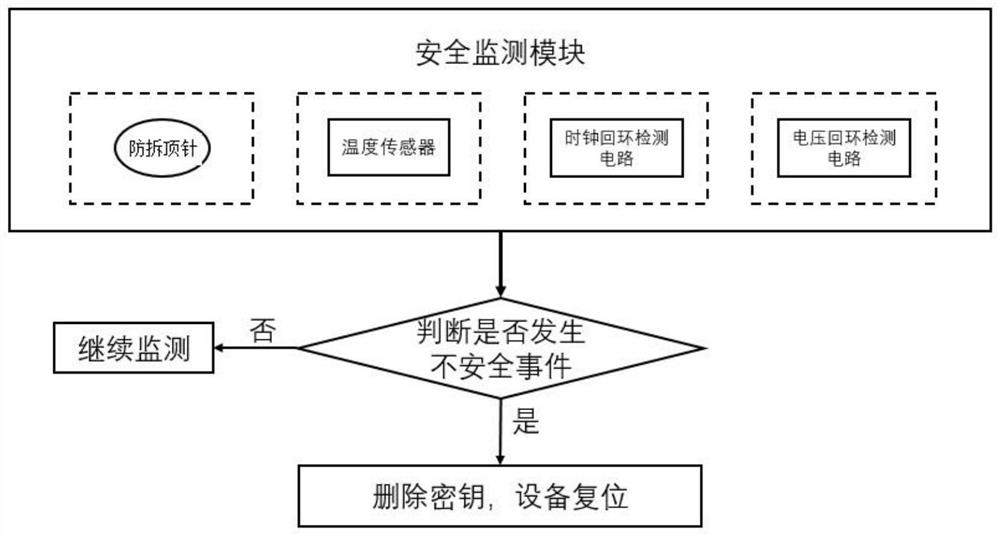
[0020] see Figure 1 to Figure 3 , this embodiment discloses a new hardware wallet with self-destruction after dismantling, including a battery module, a control module, a fingerprint module, a button module, an OLED module, a safety monitoring module, a memory safety protection module, a storage module, a safety module, an application modules, communication modules, the battery module is used to supply power to all modules of the hardware wallet, and the fingerprint module, button module, OLED module, storage module, security module, application module, and communication module are respectively connected with the control module to realize the function of the hardware wallet The safety monitoring module and the memory safety protection module are respectively connected to the control module, and the safety monitoring module is used to monitor various types of attacks such as external physics and the environment, and transmit the monitored signals to the control module, The con...
Embodiment 2
[0030] The novel hardware wallet with dismantling and self-destruction of the present invention also includes an alarm module, which is connected to a control module, and the control module is used to control the alarm module to give an abnormal alarm prompt. Other technical features of this embodiment are the same as those of Embodiment 1.
[0031] The patent of the present invention mainly protects the storage module. For example, after the hardware wallet is disassembled, the hardware wallet of the present invention avoids this problem by dismantling and self-destructing the technical solution, that is, erasing the encrypted content in the storage module.
[0032] The working principle of the present invention is: an anti-demolition thimble is installed between the circuit board and the shell of the hardware wallet, and the anti-demolition thimble connects the voltage, clock and other signals on the circuit board through the shell, and the MCU monitors the change of the volt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com