Internet of Things privacy protection access control method based on block chain technology
An access control and privacy protection technology, applied in the field of Internet of Things, can solve the problems of untrustworthy nodes, easy failure of node authorization, low distributed management efficiency, etc., and achieve the effect of improving authorization efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0042] Specific implementation methods include:
[0043] The resource owner is device B, and the requester is device A;
[0044] work process:
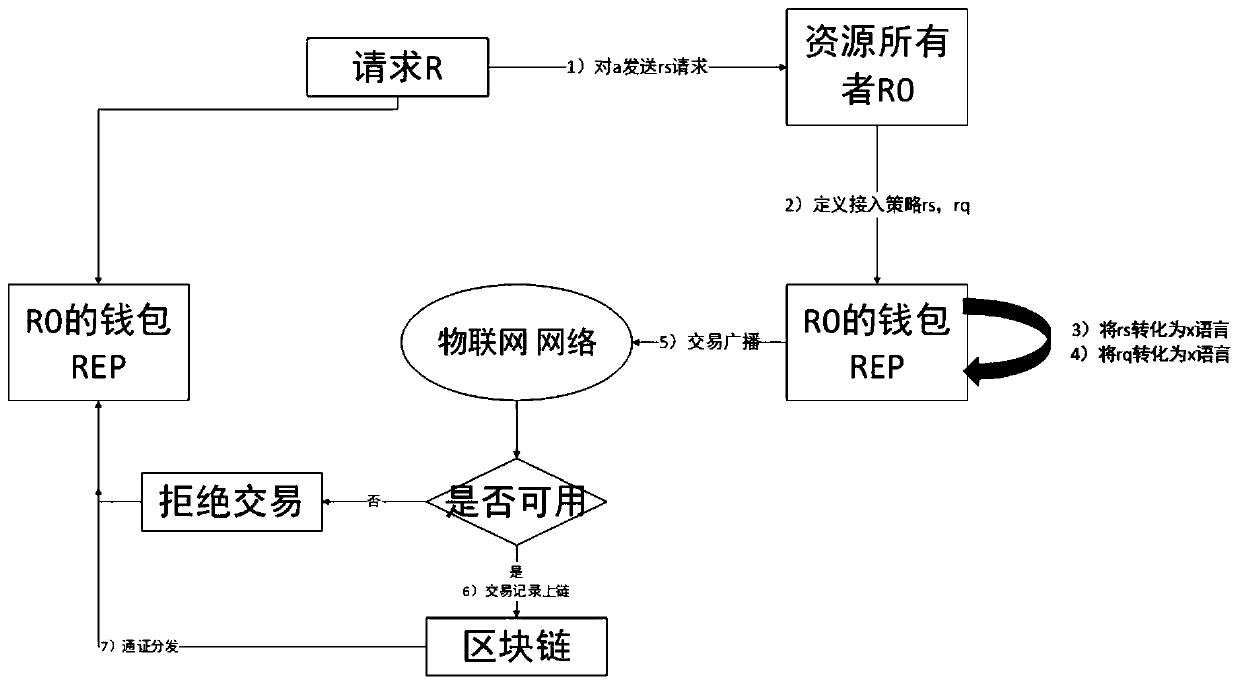
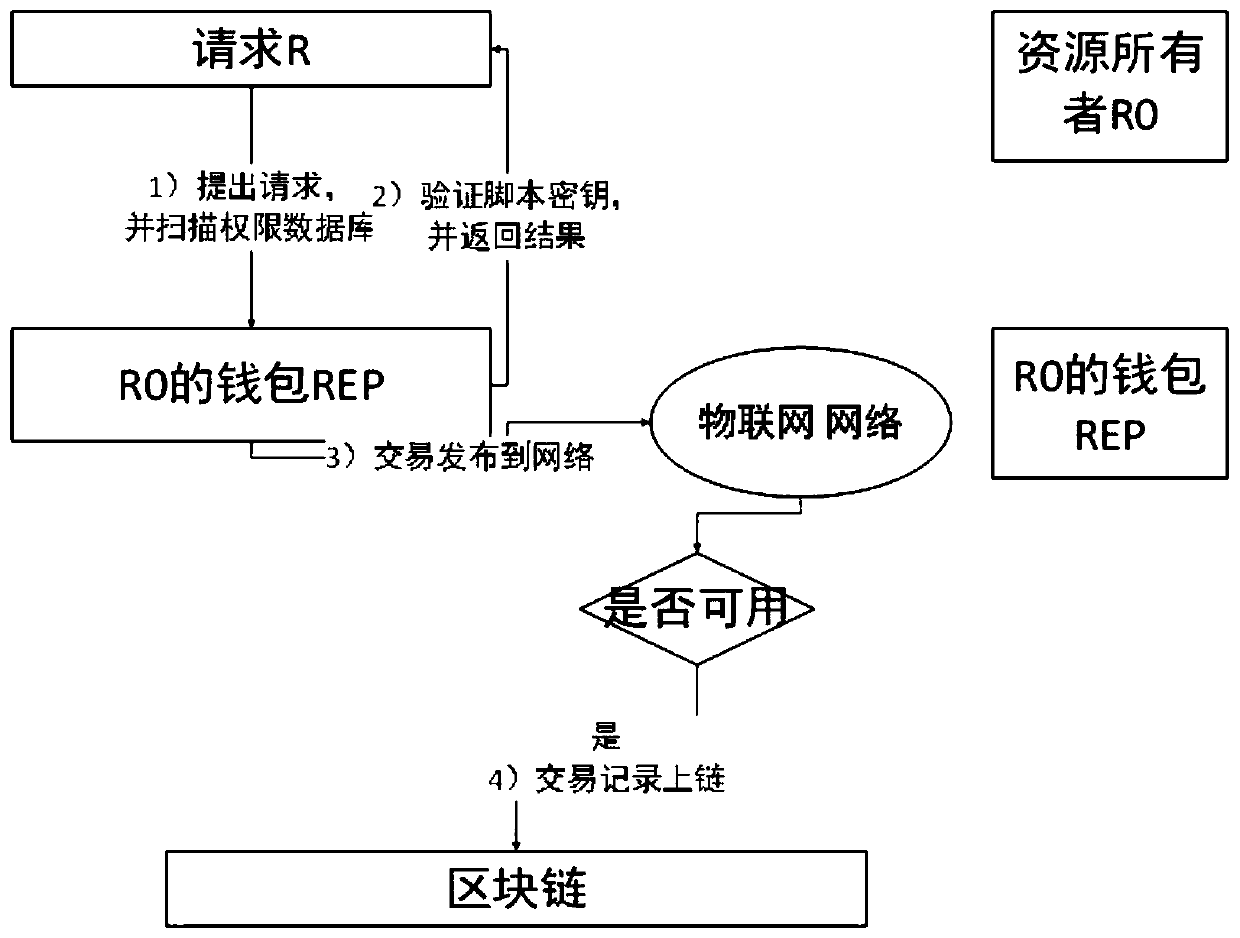
[0045] Define S100 to S300 as the authorized access transaction stage of the resource owner's resource request to the requester, (GATransacTion)
[0046] 1. If device A (represented by address rq) wants to perform an operation such as modifying the temperature of device B (represented by rs), device B defines an access permission policy and sends it to device A as an access transaction. This access transaction is called GATransaction;
[0047] 2. The policy management point of device B (called wallet in Bitcoin) converts the policy into a script language POLICY rs,rq→πx;
[0048] 3. Device B generates a Token marked as TKN rs,rq, which is encrypted with the requester's public key;
[0049] 4. Send the access transaction, and each node verifies the validity of the transaction, and if it is valid, packs the access transaction into t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com