VPN tunnel mode optimization method and system
A technology of tunnel mode and optimization method, which is applied in the field of communication, can solve problems such as large proportion and increase of actual network load, and achieve the effect of reducing the amount of increase
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
[0021] A kind of VPN tunnel mode optimization method of the present invention comprises the following process:
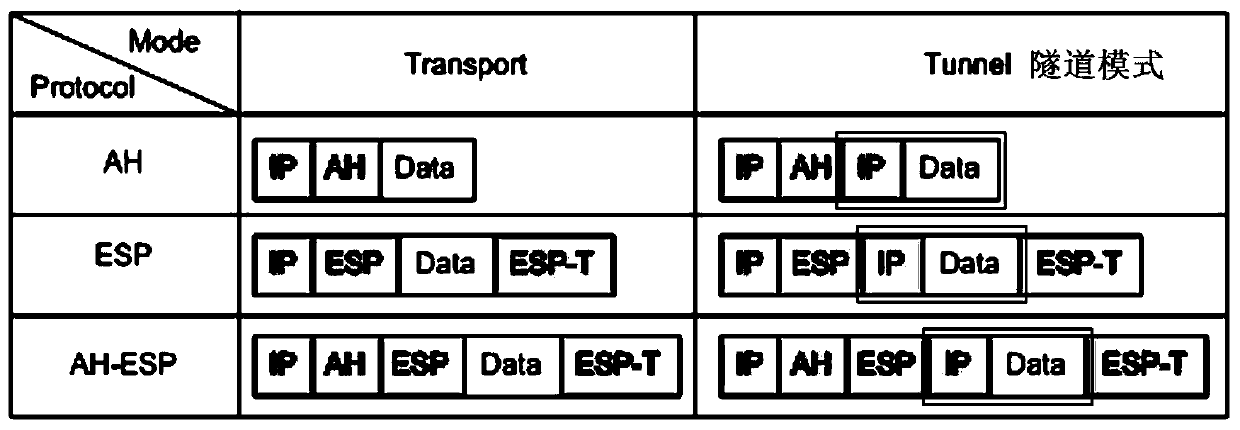
[0022] Step 1. The devices on both sides use the IPsec tunnel mode to encrypt data.
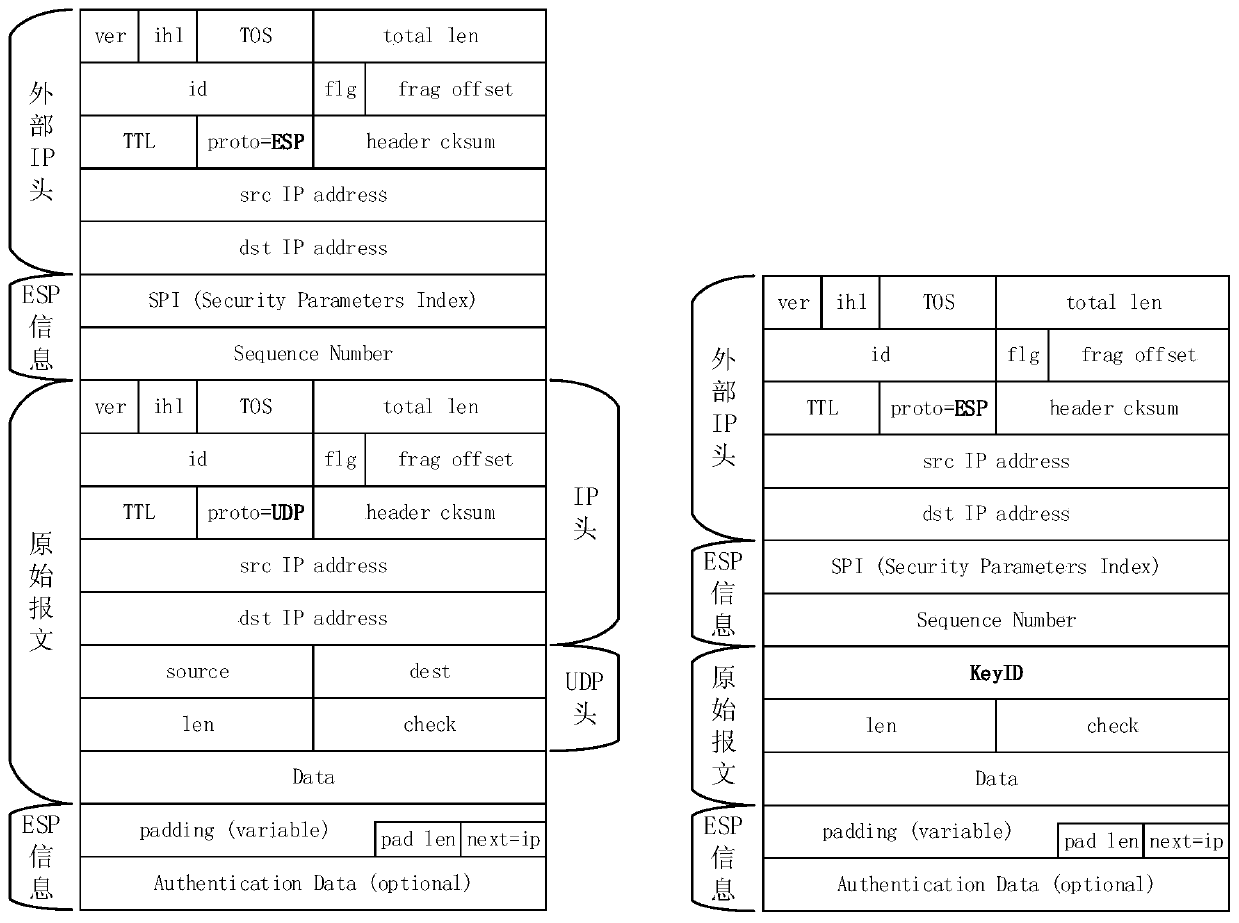
[0023] Step 2. Add a policy entry for the devices on both sides. The entry includes IP address, port number, and protocol number (such as TCP, UDP, ICMP, etc.), and configure a unique number KeyID to identify the current policy entry.
[0024] Data encryption and decryption exist in pairs. For a pair of encryption devices, policies are configured for each business. It can be understood that a business needs to configure a policy. Multiple policies can be configured on the device, and these policies...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap