Intelligent unlocking method and corresponding device
An unlocking and intelligent technology, applied in the field of security identification, can solve problems such as easy to be stolen, and achieve the effects of high security, high verification accuracy and simple operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
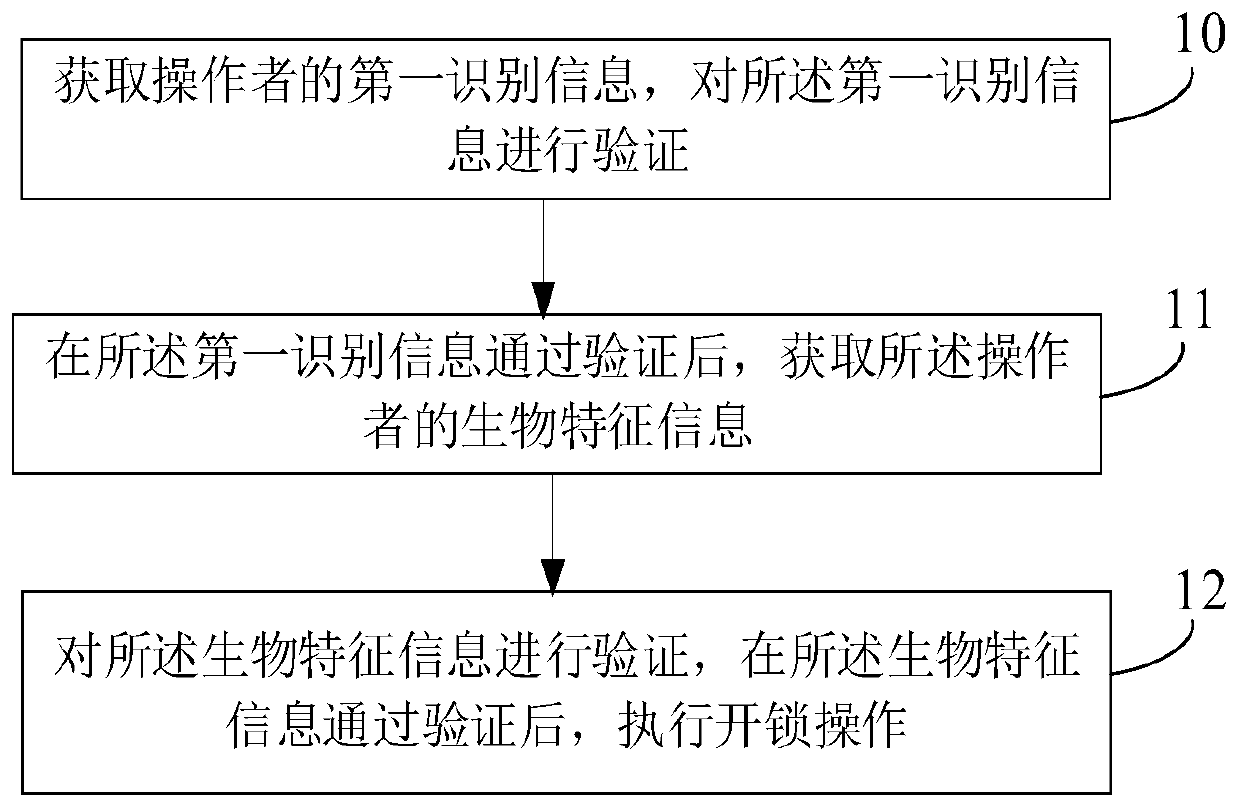
[0062] refer to figure 1 , the present embodiment provides an intelligent unlocking method, the intelligent unlocking method comprising the following steps:
[0063] Step 10: Obtain the first identification information of the operator, and verify the first identification information.
[0064] In an optional embodiment, the first identification information may be the certificate of the operator, where the certificates applicable to this embodiment include but are not limited to ID cards, passports, Hong Kong and Macao travel permits, Taiwan compatriots certificates, Hong Kong and Macao Taiwan resident residence permit and driver's license and other documents.
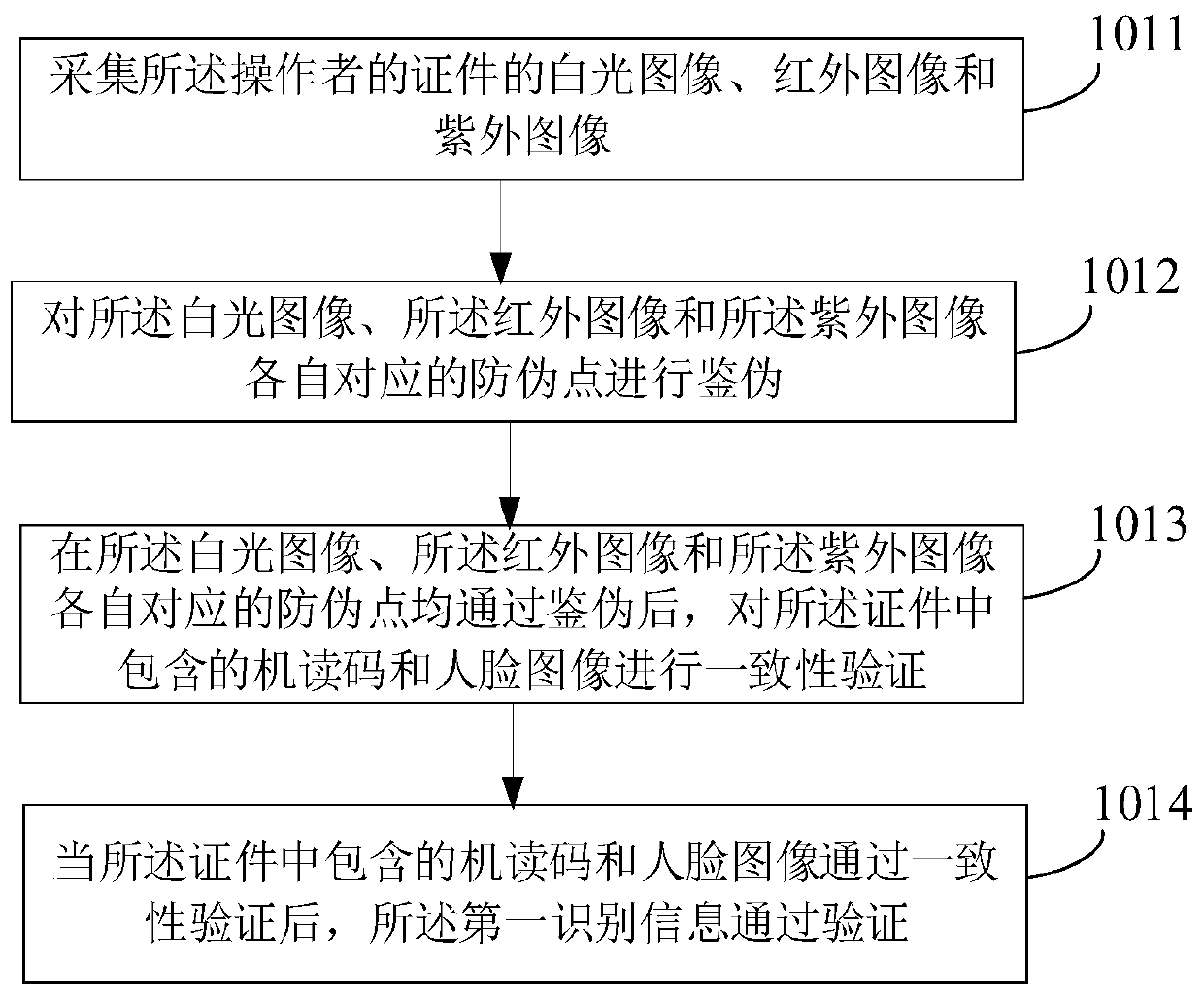
[0065] When the first identification information is a certificate, the process of verifying the first identification information is the verification process of the certificate. When the certificate passes the authenticity verification, the first identification information passes the verification.
[0066] In practical ...
Embodiment 2
[0127] Combine below Figure 5 ~ Figure 7 , specifically illustrating an implementation manner in which the first identification information is a verification code.
[0128] In one example, see Figure 5 and Figure 7 , step 10 includes the following steps:
[0129] Step 1021: Receive a trigger request from the operator, and obtain the contact information of the user corresponding to the electronic lock according to the trigger request.
[0130] Wherein, the trigger request may be the unique identification information of the electronic lock input by the operator, or the face image corresponding to the electronic lock selected by the operator.
[0131] Wherein, the contact method can be telephone, WeChat, qq or other types of social methods.
[0132] Step 1022: Send a verification code to the user corresponding to the electronic lock through the contact information.
[0133] Step 1023: Determine whether the verification code input by the operator within the preset time is ...
Embodiment 3
[0148] The foregoing embodiments mainly illustrate the process of verifying and unlocking, below in conjunction with Figure 8 , briefly explain the process of a user's initial registration and use of electronic locks.
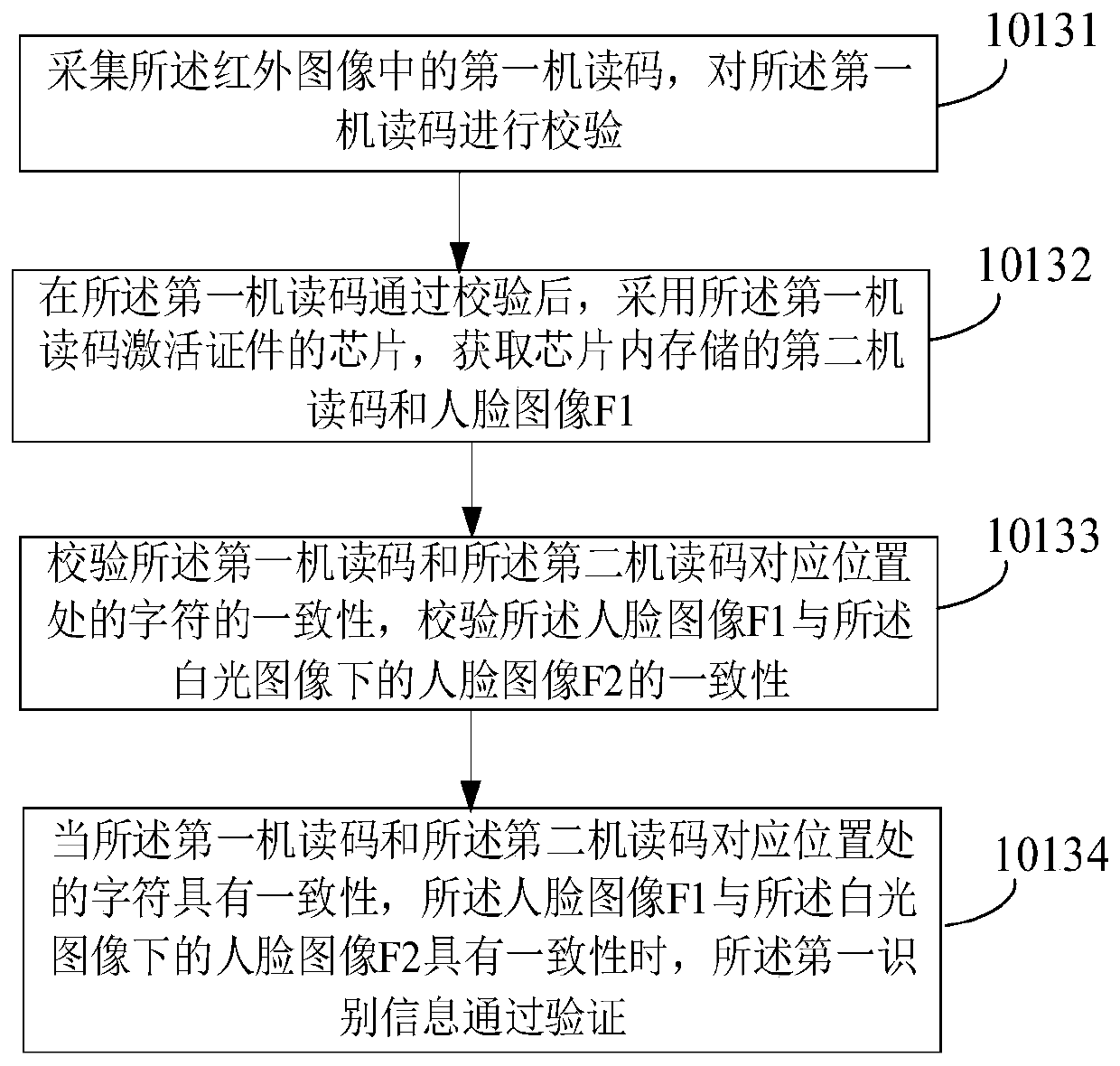
[0149] Such as Figure 8 As shown, firstly, according to the certificate verification method in Example 1, the certificate is authenticated and verified for consistency. The face image is processed to obtain the face image F3, wherein, the manner of the face image F3 can refer to Embodiment 1, and will not be repeated here.
[0150] Verify the consistency between the face image F3 and the face images (F1 and F2) in the certificate. When the face image F3 is consistent with the face images (F1 and F2) in the certificate, the receiving operator (user) Enter the biometric information and contact information, and set the authorization period of the operator (user), after the authorization period is exceeded, the operator (user) information will be deleted from t...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap