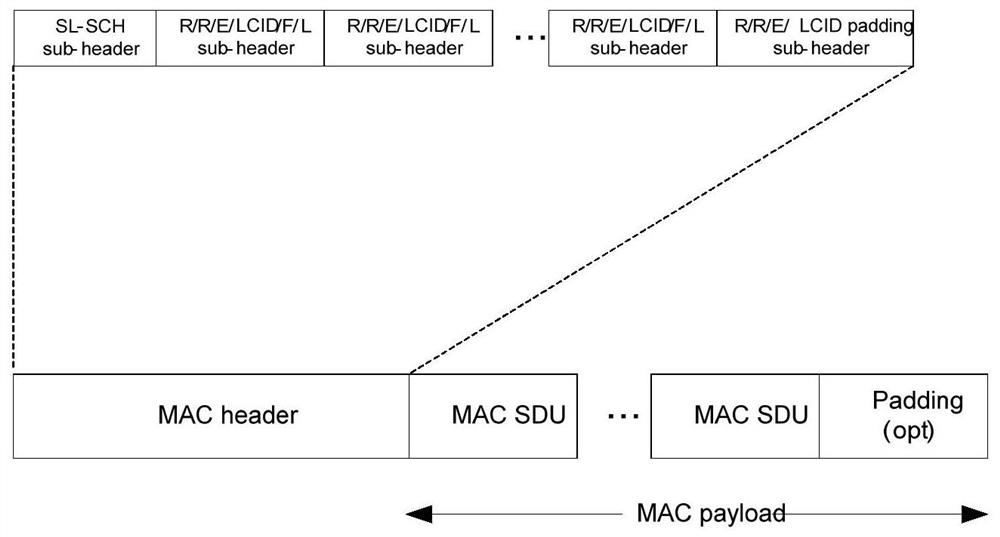
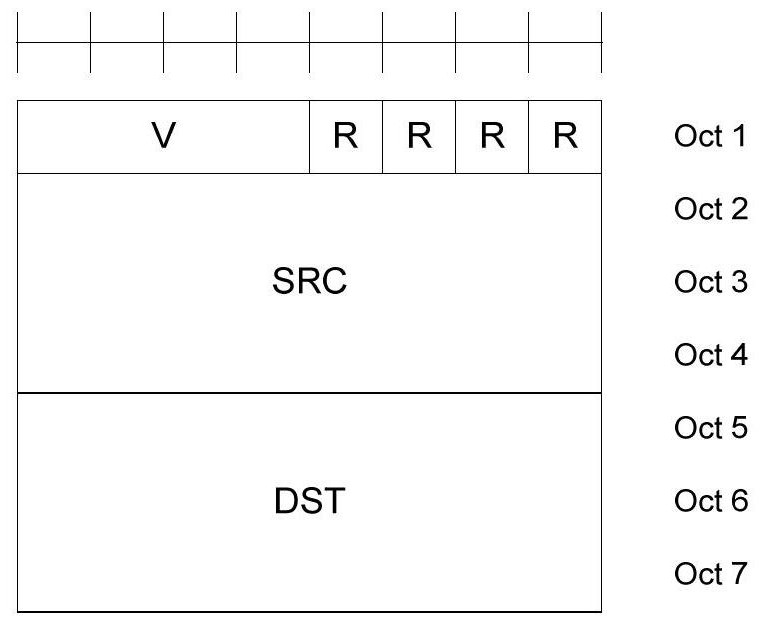
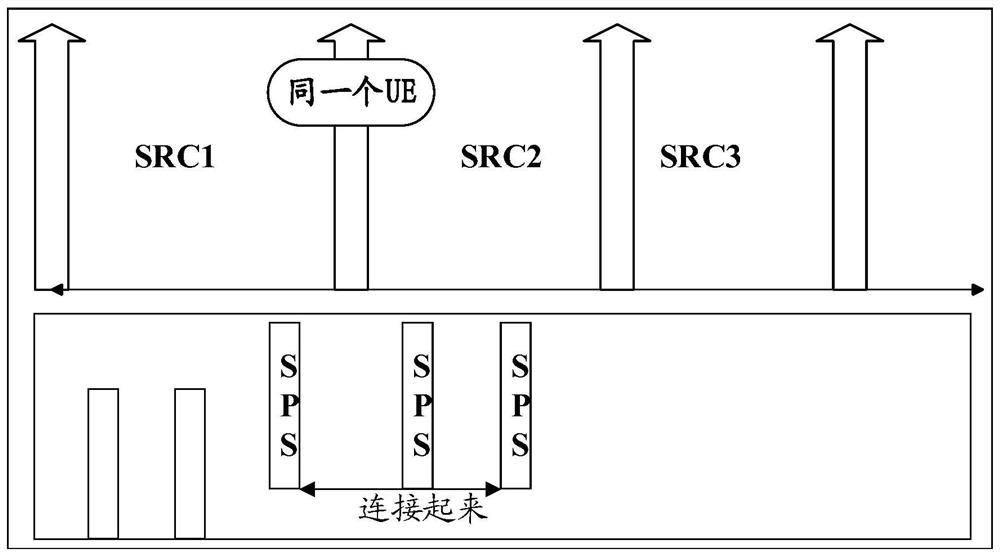
A resource selection method, base station and terminal
A resource selection and resource technology, applied in transmission path sub-channel allocation, digital transmission system, connection management, etc., can solve problems such as target terminal privacy leakage, and achieve the effect of reducing the probability of continuous tracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0089] In order to make the technical problems, technical solutions and advantages to be solved by the present invention clearer, the following will describe in detail with reference to specific embodiments and accompanying drawings.
[0090] In order to enable those skilled in the art to better understand the embodiments of the present invention, the following explanations are first made.
[0091] PC5 mode mode3 has two types of scheduling: Dynamical Scheduling (DS for short) and Semi-Persistent Scheduling (SPS for short). Mode 4V2V has two types of scheduling based on monitoring sensing SPS and sending one shot at a time. For DS / one shot scheduling, it is impossible for a malicious terminal to track the geographical location of the target vehicle through continuous monitoring and high-level data processing on certain physical resources. In the embodiment of the present invention, only mode 4 sensing SPS and mode 3 SPS scheduling are considered.
[0092] For mode 4sensing SP...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com