A Speech Recognition Attack Defense Method Based on PSO Algorithm
A technology of speech recognition and speech recognition model, applied in speech recognition, speech analysis, countermeasures against encryption mechanisms, etc., to achieve the effects of avoiding distortion, high security and stability, and high privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be described in further detail below in conjunction with the accompanying drawings and examples in the specification. It should be noted that the following examples are intended to facilitate understanding of the present invention, and do not have any limiting effect on it.
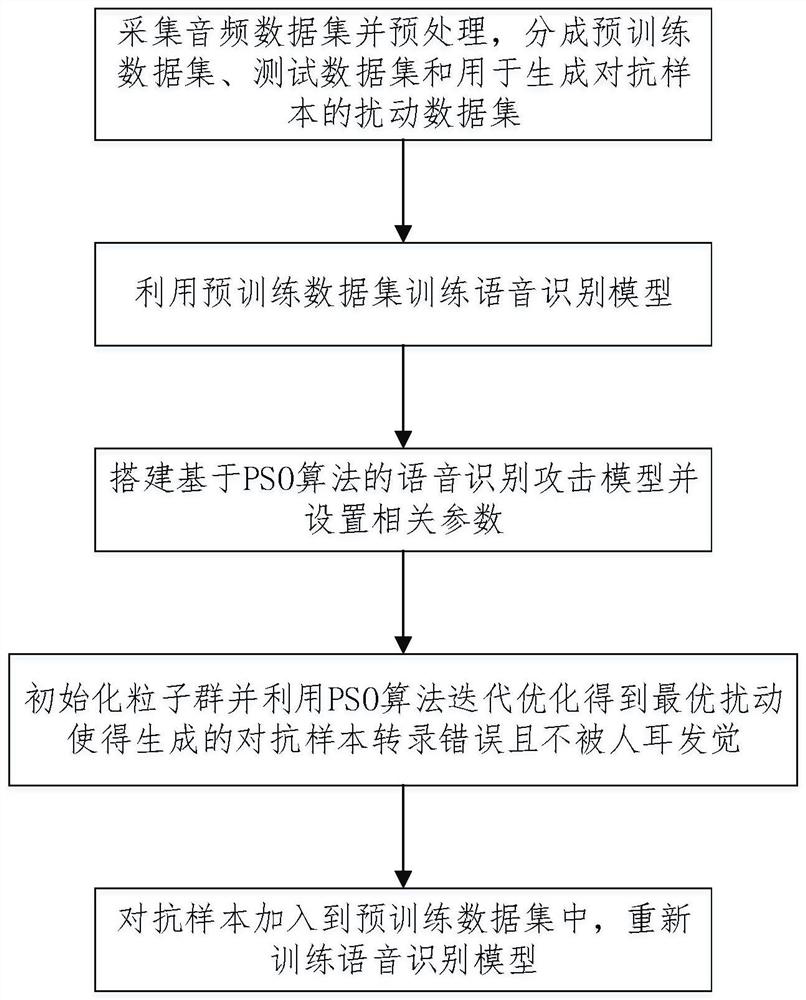
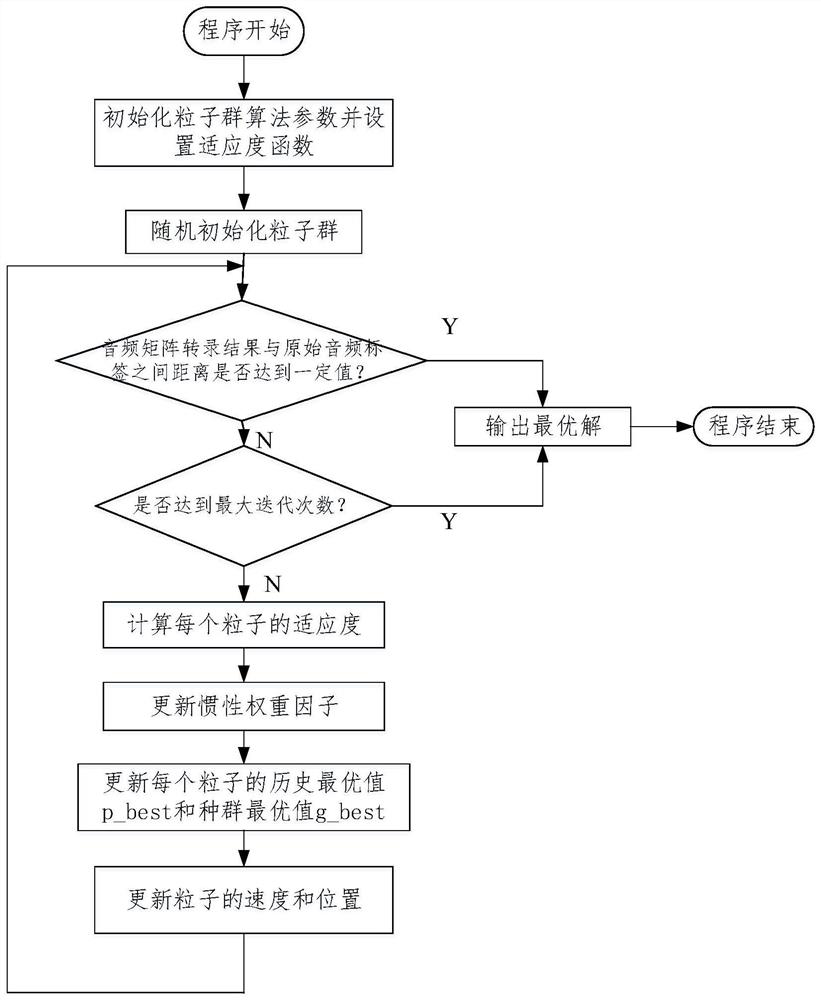
[0027] refer to Figure 1-Figure 3(2) , a kind of speech recognition attack defense method based on PSO algorithm comprises the following steps:
[0028] (1) Prepare the original audio data set: collect multiple types of audio in different scenarios and preprocess them, and divide them into pre-training data sets, test data sets and disturbance data sets for generating adversarial samples according to a certain ratio. The process is as follows:
[0029] Step11: Collect multiple types of audio in a variety of scenarios, including the voice of people speaking, the sound of music in real life scenes, where the content of people speaking includes fragments of articles read a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com