Method for securing communication without management of states
A communication method and technology of communication entities, applied in the field of secure communication, can solve problems such as the limitation of extended sensor network security types and the inability to guarantee end-to-end security, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] definition
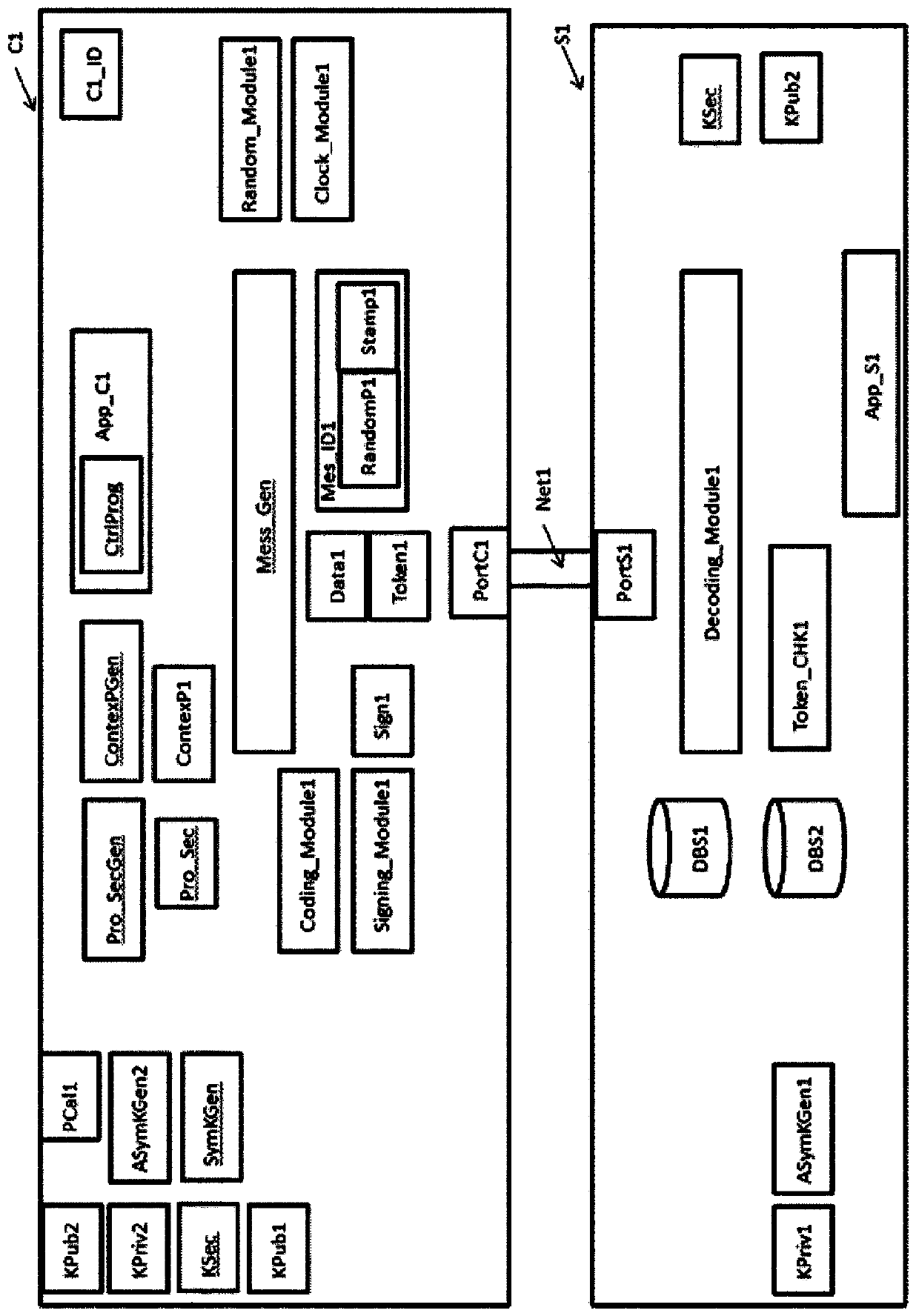
[0074] The present invention relates to communication security and authentication between two communicating entities.
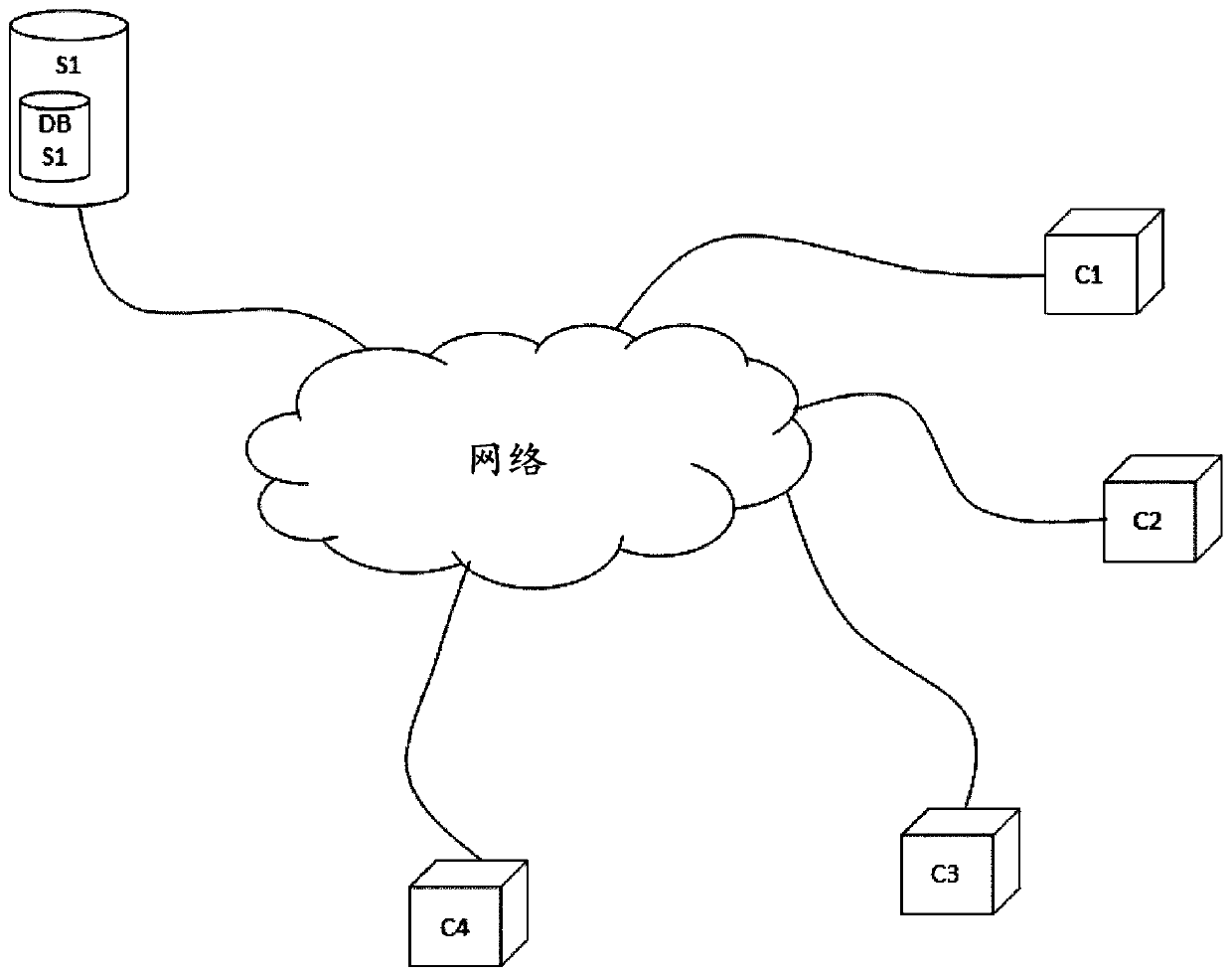
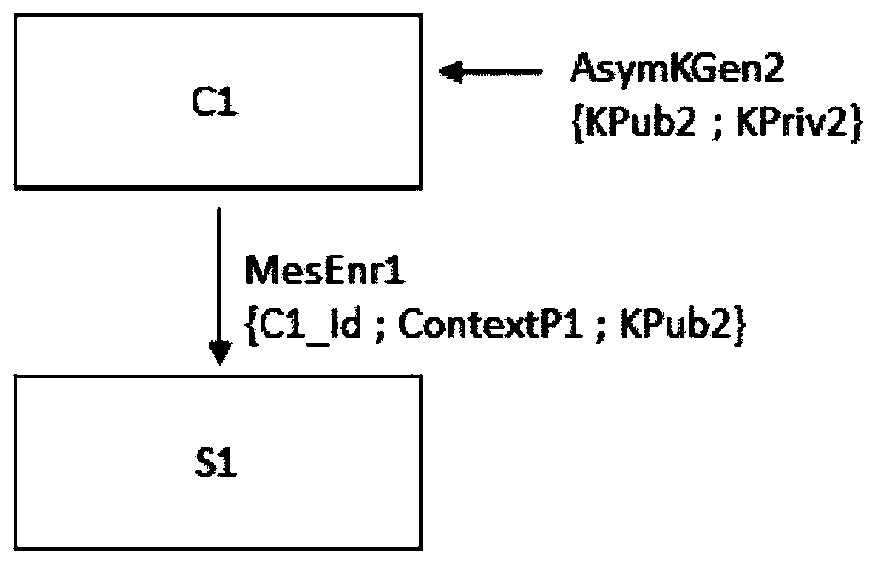
[0075] The description refers specifically to two entities, a client and a server. The client C1 is for example the connected object, and the server S1 is of the data server type, with which they receive the payload data Data1 collected by the connected object's sensors.
[0076] In this description, a first communicating entity C1 designates a communicating entity C1 that transmits, for example, payload data collected by one or more sensors. Sensors measure physical quantities such as temperature, pressure, vibration, force and acceleration. The first entity may include one or more actuators. The first entity may also comprise a set of sensors and actuators, the sensors providing eg information about the status or position of the actuators.
[0077] The second communicating entity S1 designates the communicating entity S1 receiving ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com