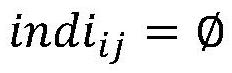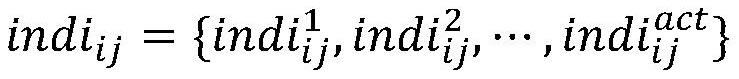Patents
Literature
46results about How to "Meticulously divided" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
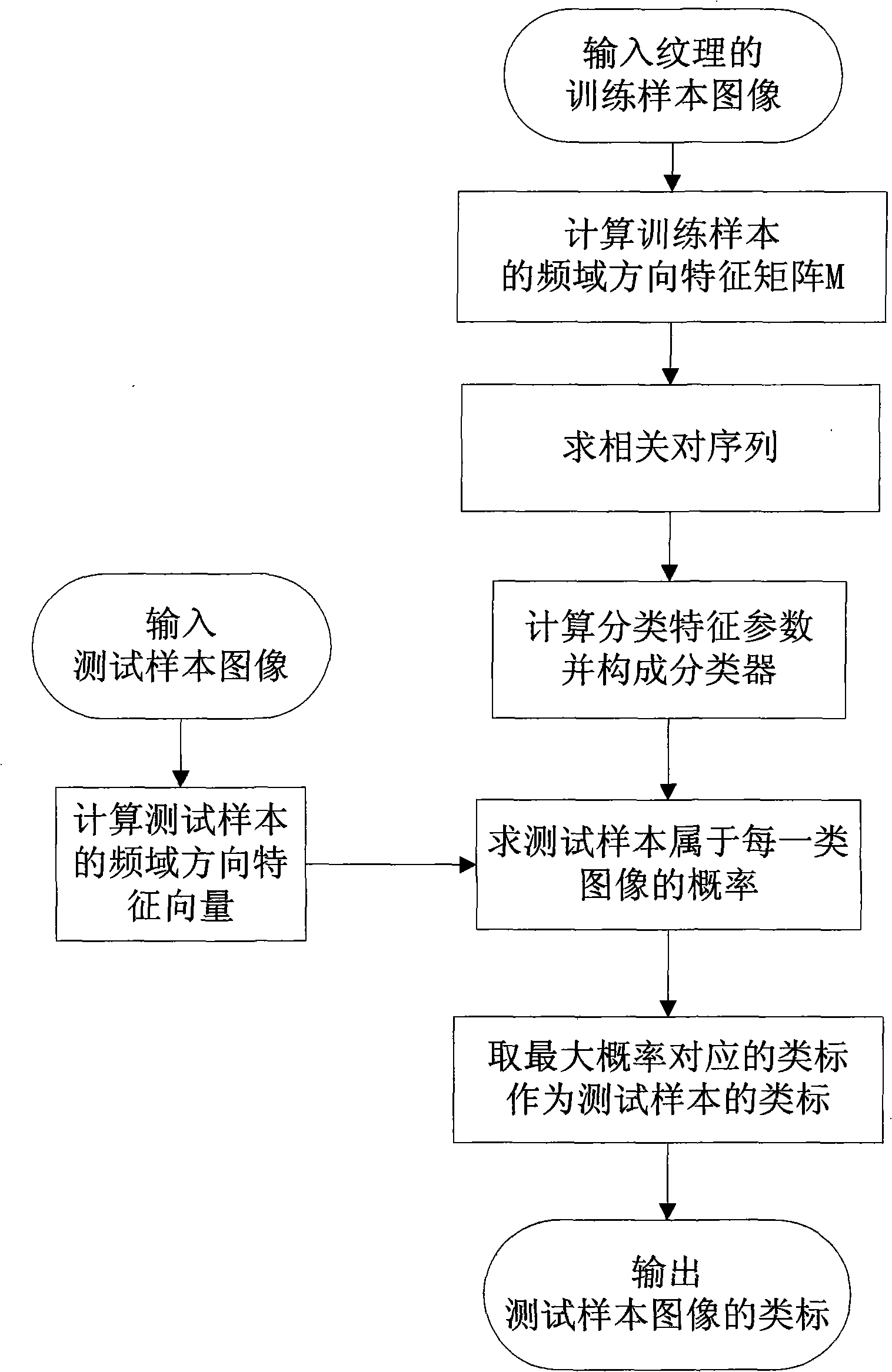
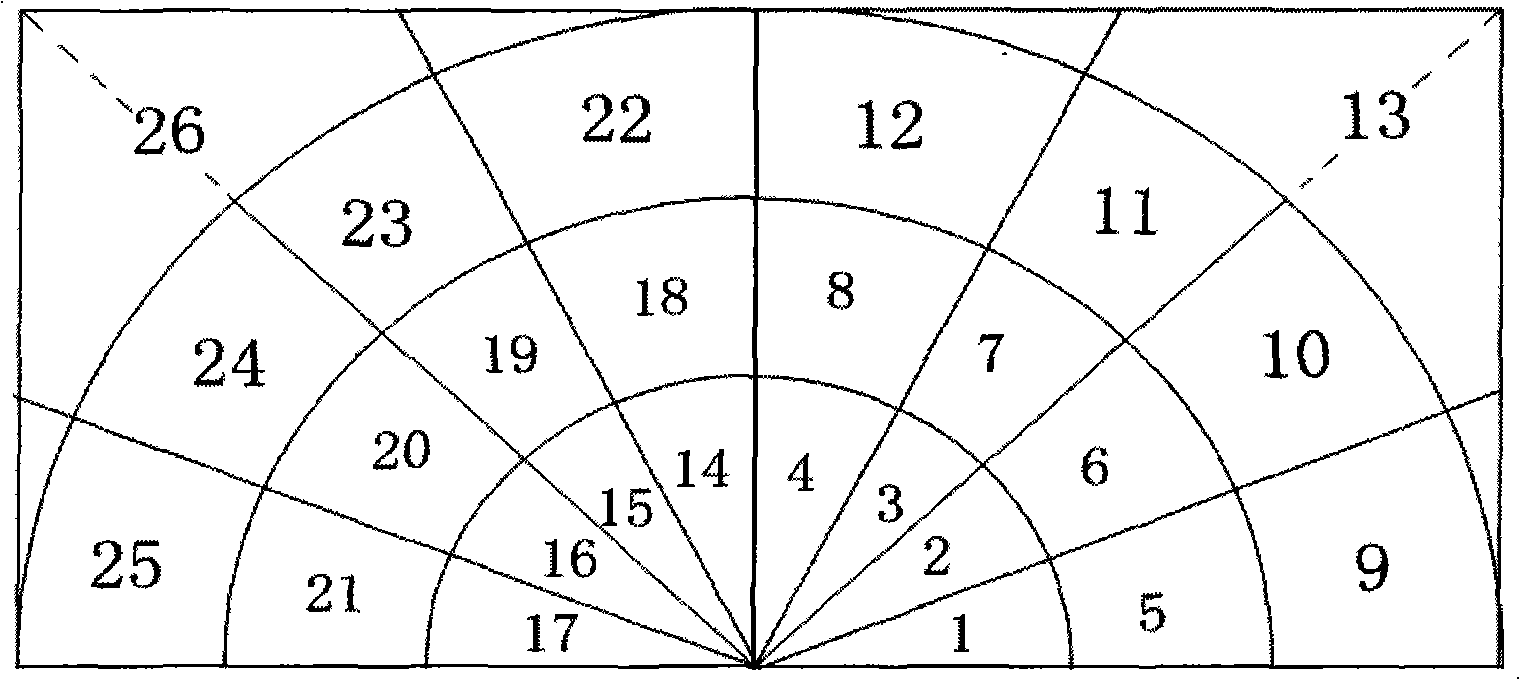
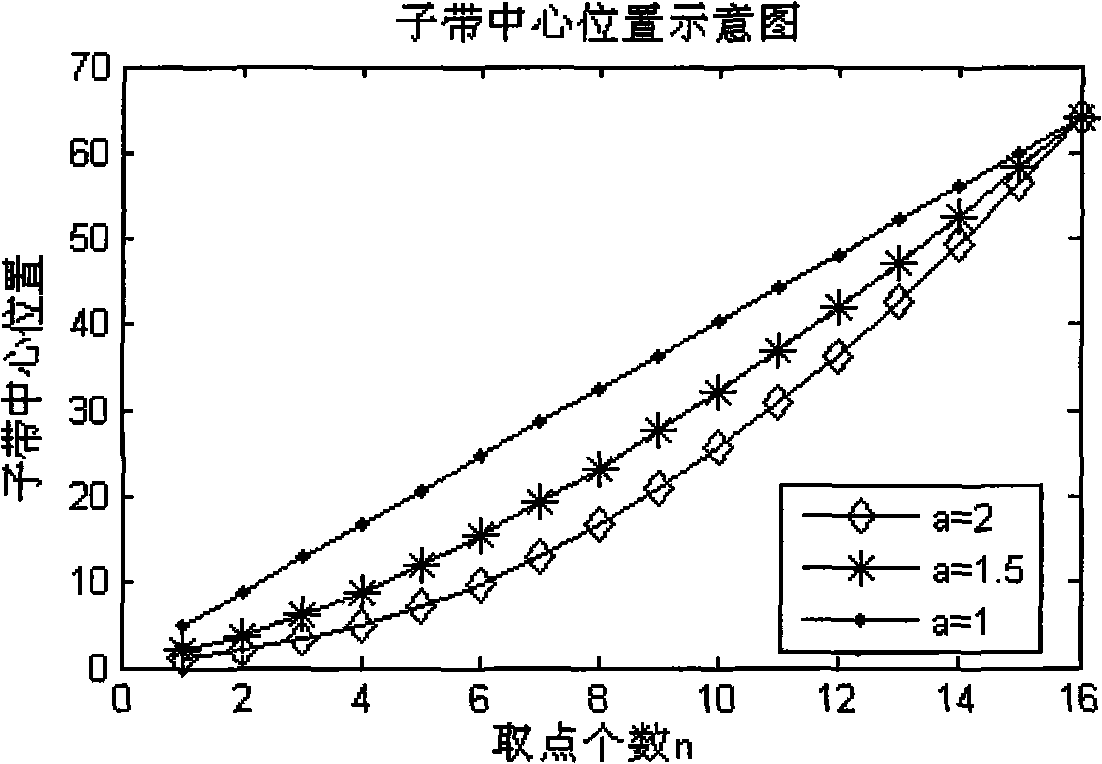
Image classification method based on feature correlation of frequency domain direction
InactiveCN101551864AMeticulously dividedImprove classification performanceCharacter and pattern recognitionData setTest sample
The invention discloses an image classification method based on the feature correlation of frequency domain direction, which mainly overcomes the shortages that the existing method has high calculation complexity, low classification precision and low robustness on image size variation. The method comprises the following steps of: (1) selecting a texture sample image and classifying the texture sample image into an image data set of training sample and an image data set of test sample; (2) implementing 2 dimensional fast Fourier transformation on the training sample image and dividing frequency domain direction subband according to the frequency and direction of the Fourier surface to obtain a frequency domain direction feature matrix; (3) calculating and obtaining a correlation pair sequence according to the correlation among subband features of the frequency domain direction feature matrix; (4) using unitary linear regression model for calculating the classification feature parameters of each correlation pair to form a classifier; (5) fitting the frequency domain direction features of the test sample image with the classifier parameters to obtain a classification label of the test sample; and (6) repeating step (5) to obtain the classification labels of all test samples. The i image classification method can be used for classifying the Brodatz texture images and the SAR images.
Owner:XIDIAN UNIV
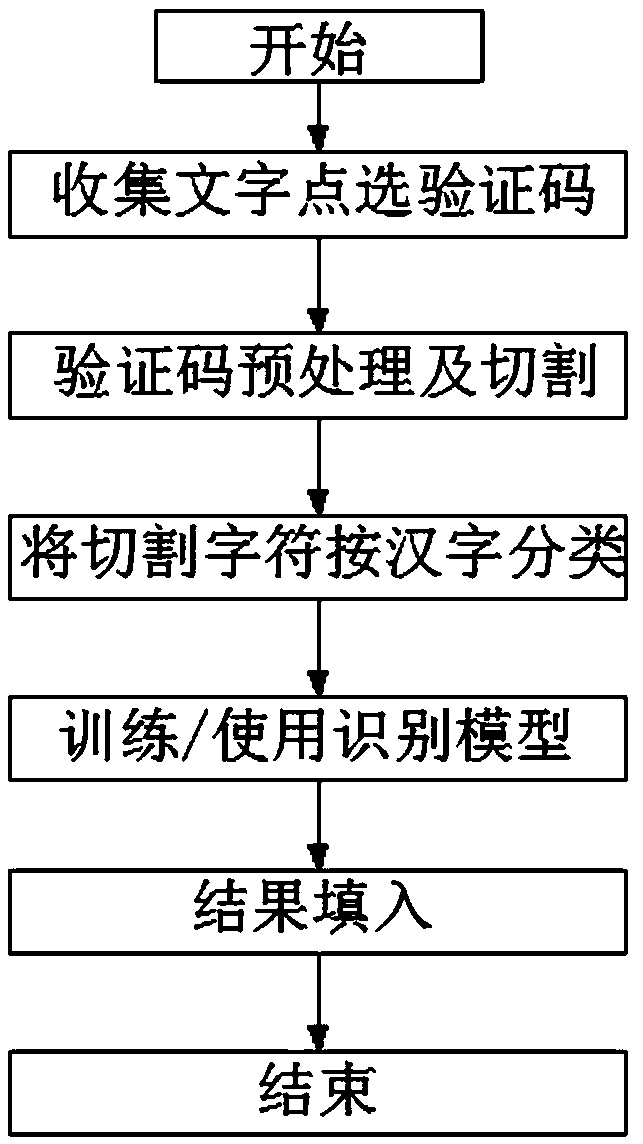
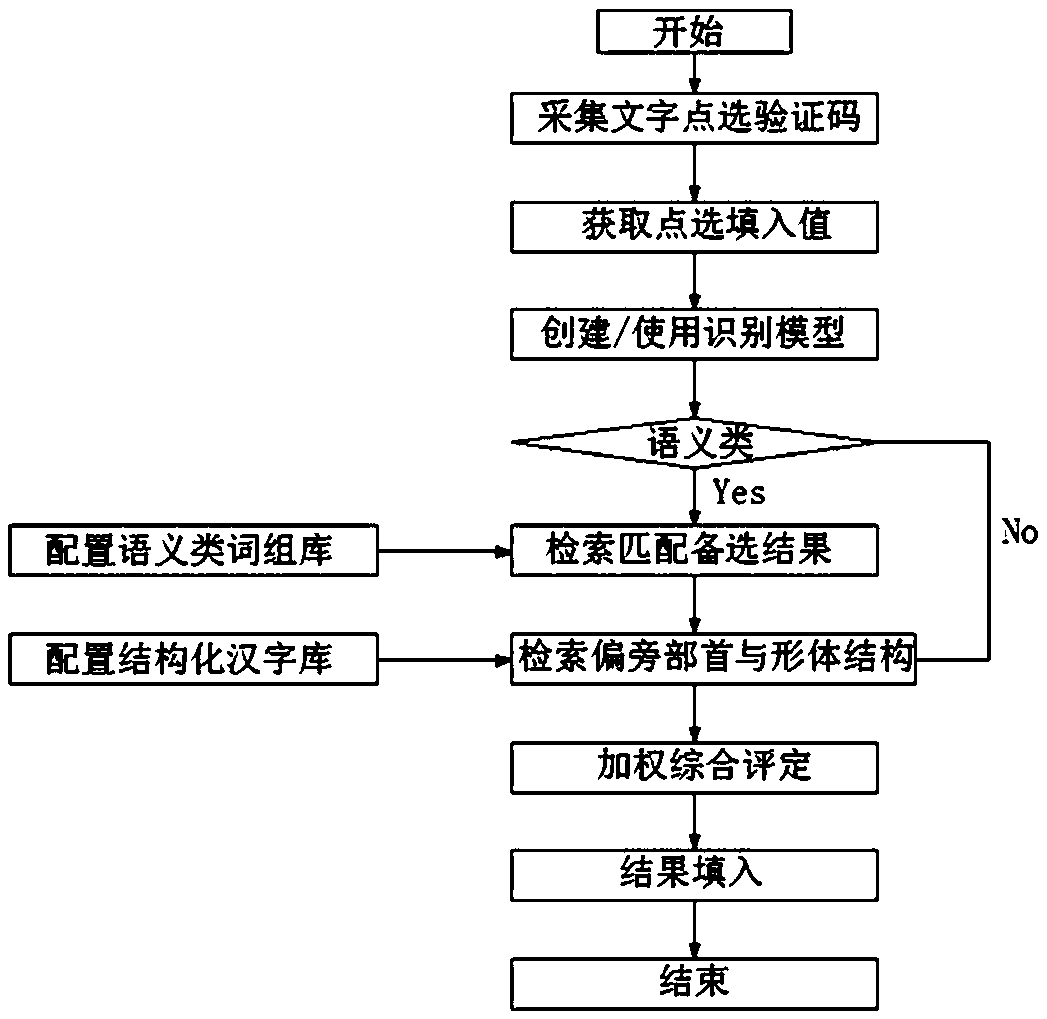
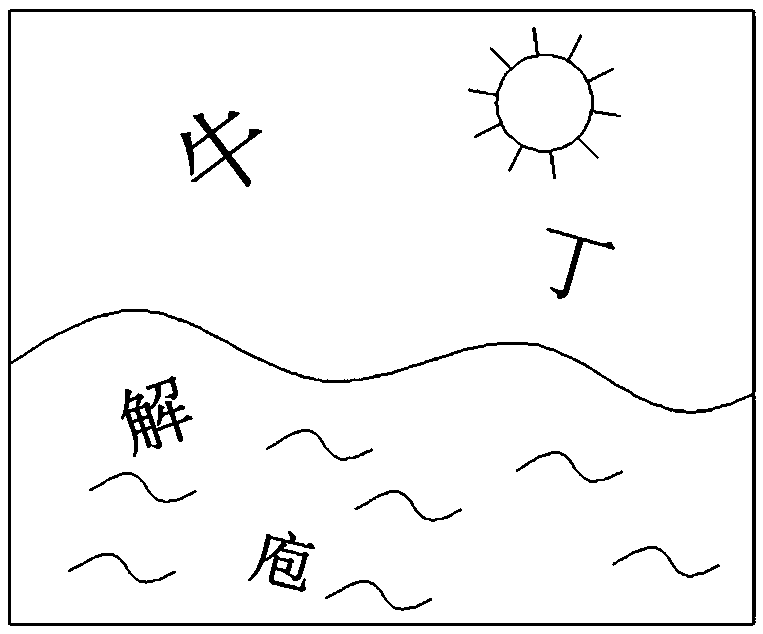
Character click verification code identification and filling method based on Chinese character structure
PendingCN110119441AFew samplesSave manpower and time costText database queryingSpecial data processing applicationsChinese charactersChinese word
The invention relates to a Chinese character structure-based character click verification code identification and filling method, which comprises the following steps of: pre-configuring a semantic word group library, collecting semantic Chinese word groups and adding the semantic Chinese word groups for retrieval; pre-configuring a structured Chinese character library, collecting Chinese characters and adding a structure label to a single Chinese character for retrieval; collecting character click verification code pictures, detecting areas with Chinese characters in the character click verification code pictures, cutting the areas into single Chinese character pictures, and recording area coordinates of the Chinese character pictures as filling values; pre-creating a recognition model forpredicting Chinese characters; according to the identification model, performing identification prediction on each Chinese character picture to obtain each predicted Chinese character; carrying out retrieval matching on each predicted Chinese character, an input semantic class phrase library and a structured Chinese character library, and carrying out weighted comprehensive evaluation to obtain atarget Chinese character filling sequence; and according to the obtained target Chinese character filling sequence and the regional coordinates of each Chinese character picture, clicking a verification code in a verification window of the verification code and submitting the verification code.
Owner:厦门商集网络科技有限责任公司
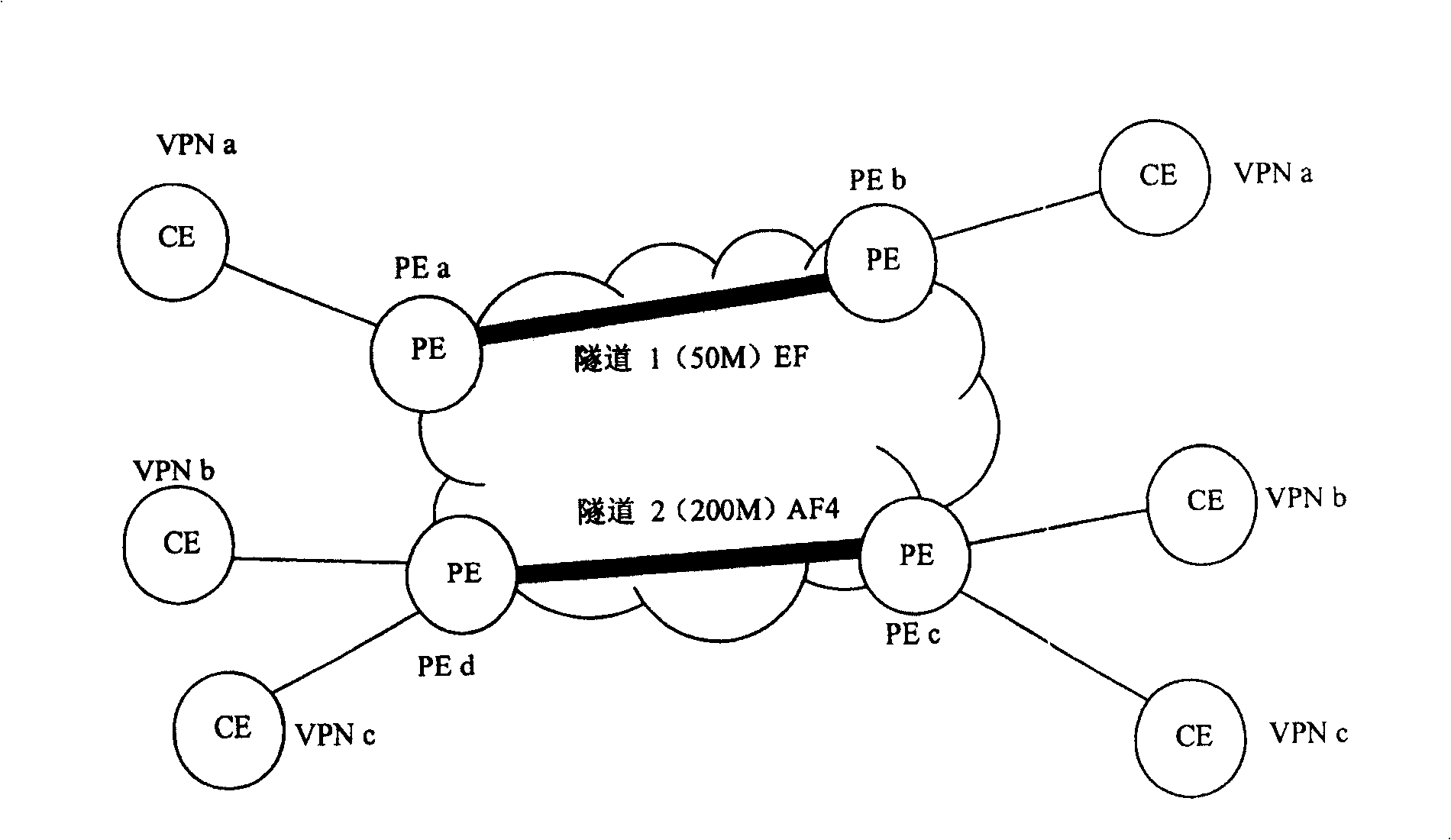
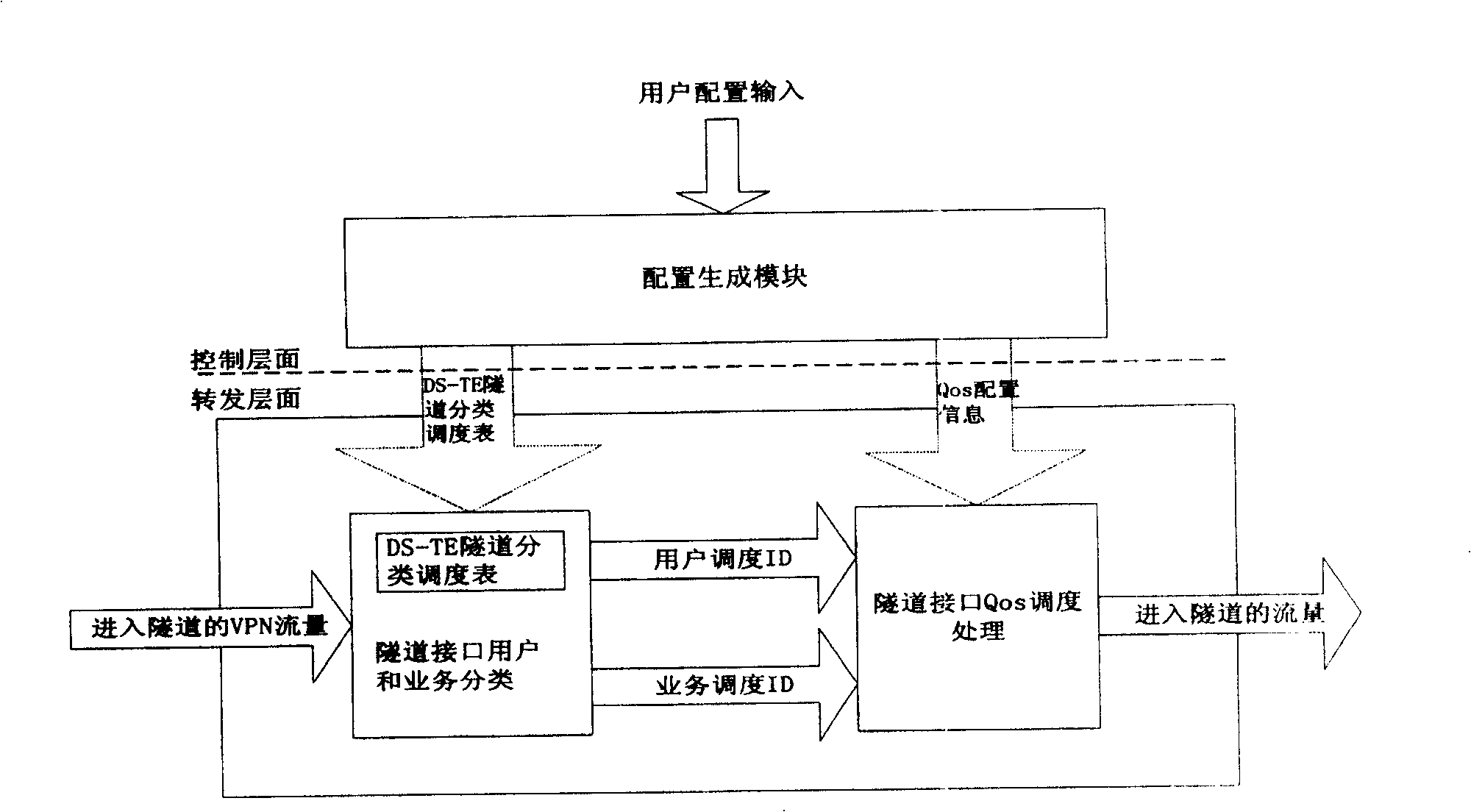
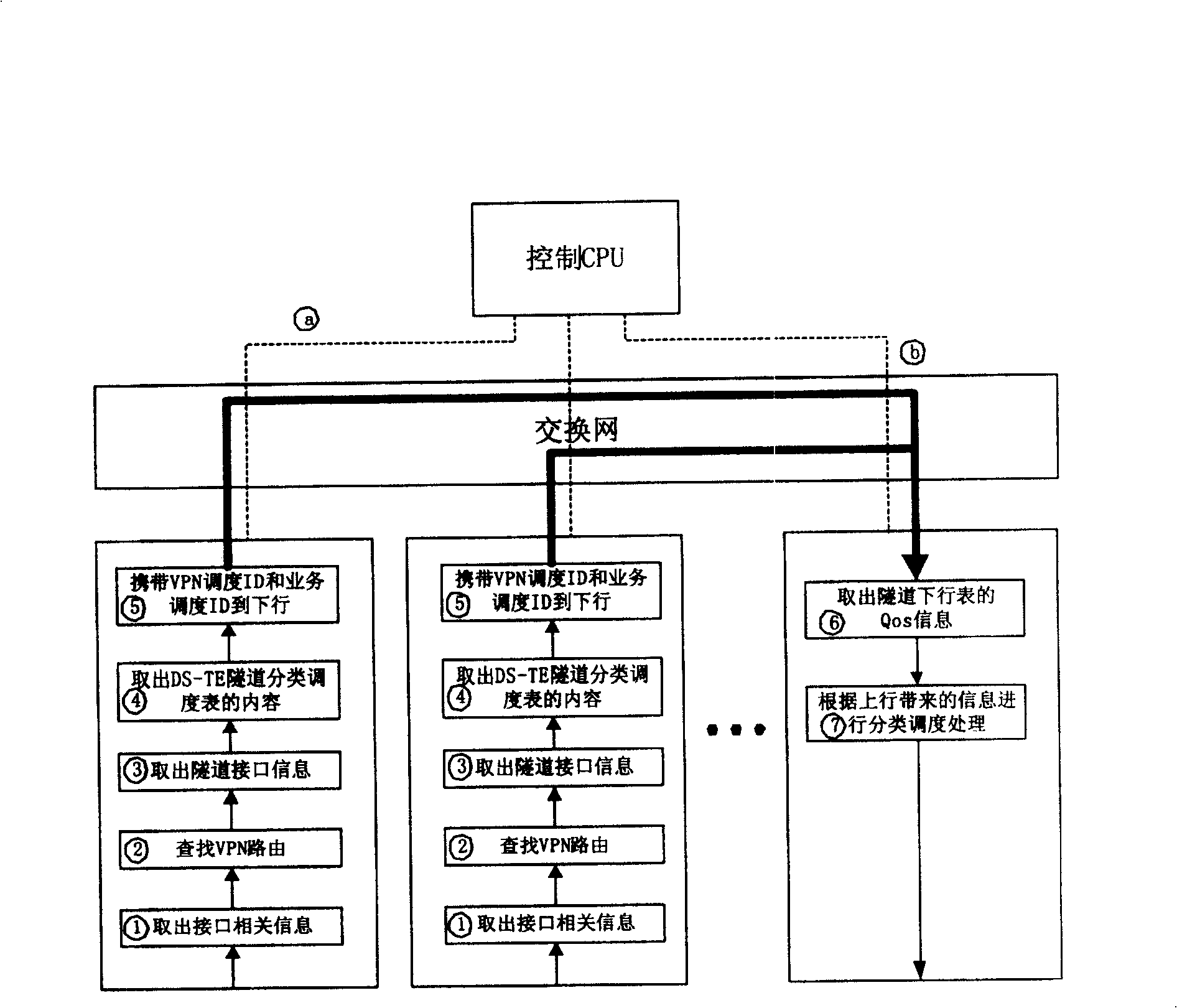
Method for providing QoS service for virtual special net user
InactiveCN100450093CMeticulously dividedNetworks interconnectionDistributed computingValue-added service
The present invention discloses a method providing QoS ministrant to virtual special network user, capable of providing multi-user multiple service difference service to virtual special network VPN. Said method includes based on user scheduling ID, DSCP or 8021. P value and service scheduling ID to construct DS-TE tunnel classified schedule table, querying DS-TE tunnel classified schedule table, if configured multi-user scheduling and / or multiple service scheduling, obtaining user scheduling ID and / or service scheduling ID; according to said user scheduling ID and / or service scheduling ID, tunnel interface QoS scheduling process, providing QoS service.
Owner:HUAWEI TECH CO LTD
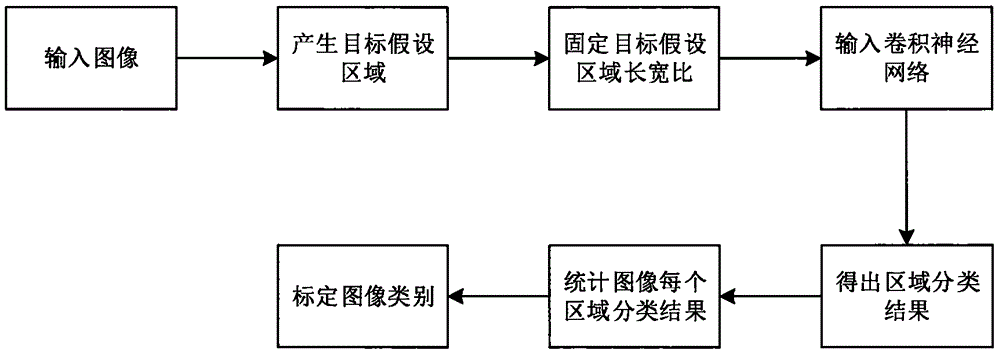
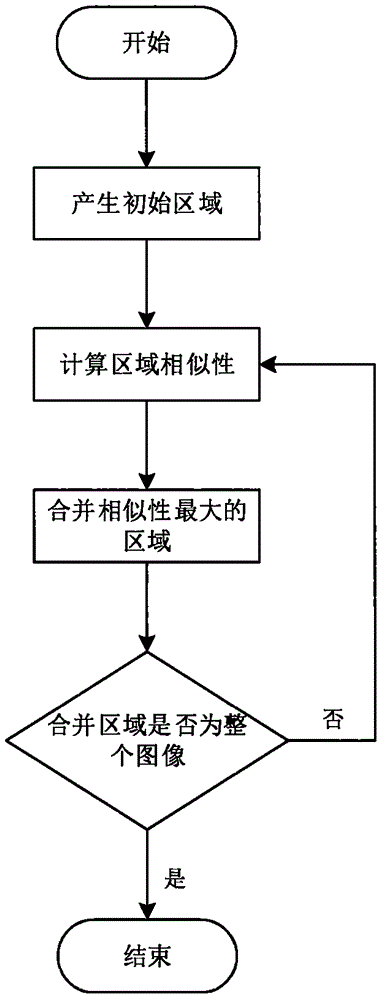
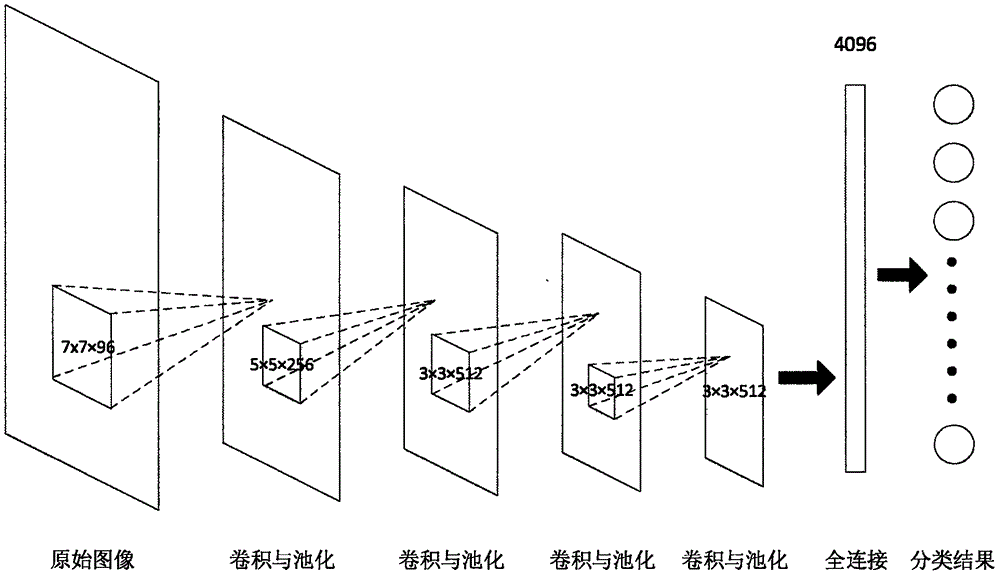
Precise image searching method based on region convolutional neural network
InactiveCN105868269AAutomatically learns wellOvercome limitationsSpecial data processing applicationsNeural network analysisImage database
The invention provides a precise image searching method based on a region convolutional neural network. By use of the convolutional neural network, contents of an image are analyzed, and regions and the number of objects included by the image are calibrated. By inputting searching conditions, the image including the objects can be precisely output by traversing the whole image database. The region convolutional neural network is capable of analyzing all objects in the image and the convolutional neural network is quite high in accuracy. Compared with the traditional method, the situation of omission or mistaken searching is avoided to the great extent and an objective of precise searching is achieved.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
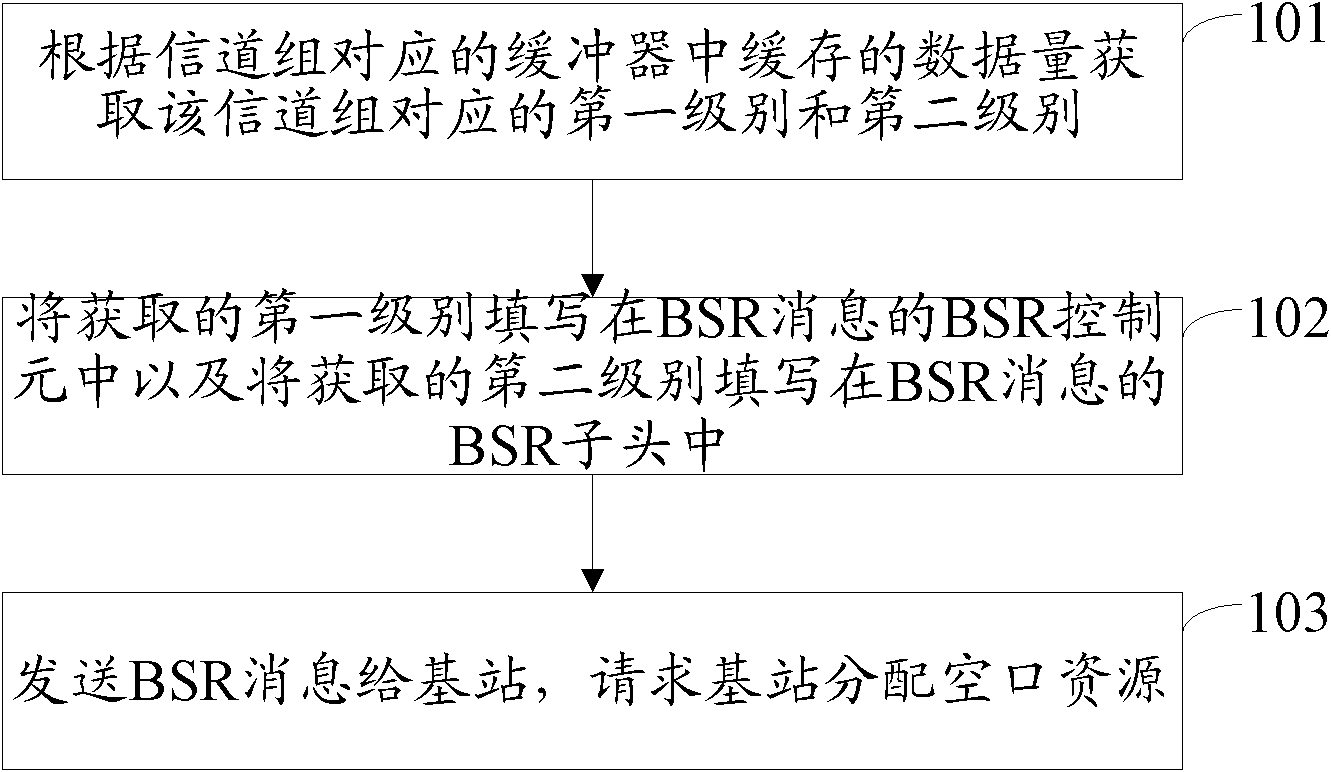
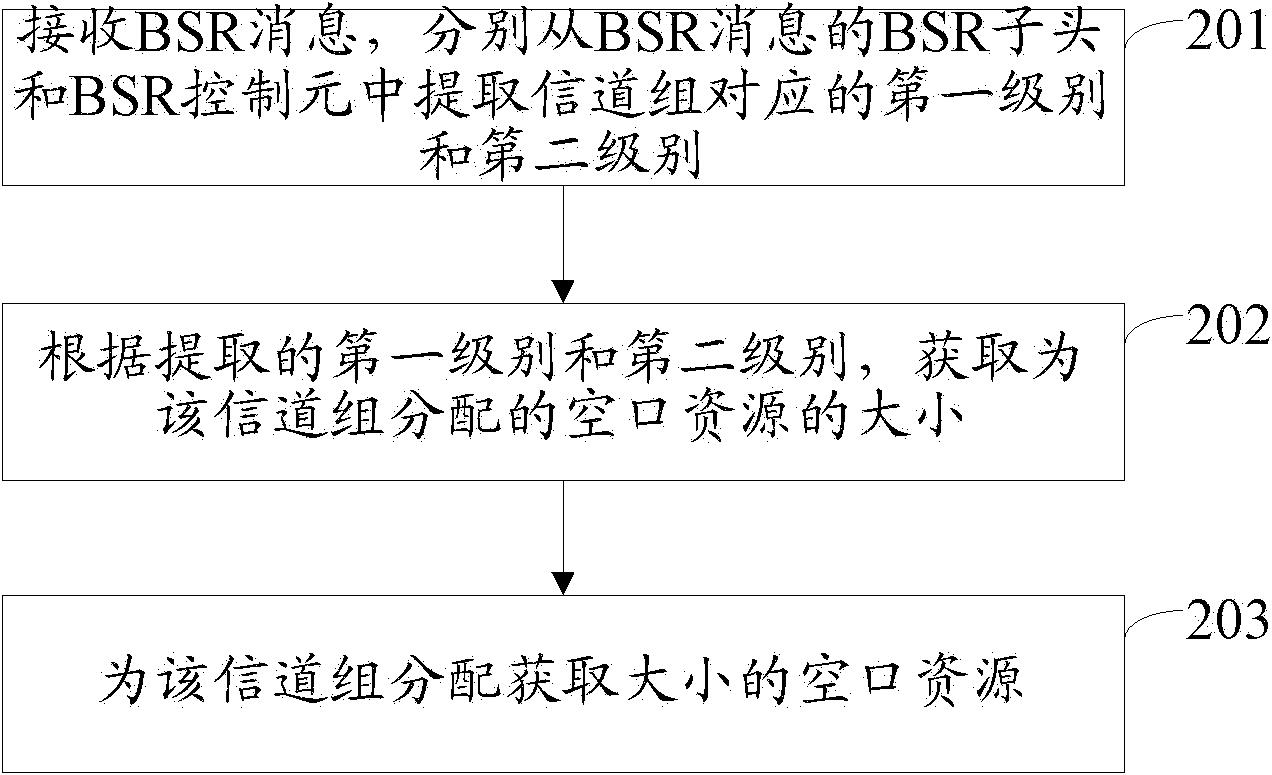
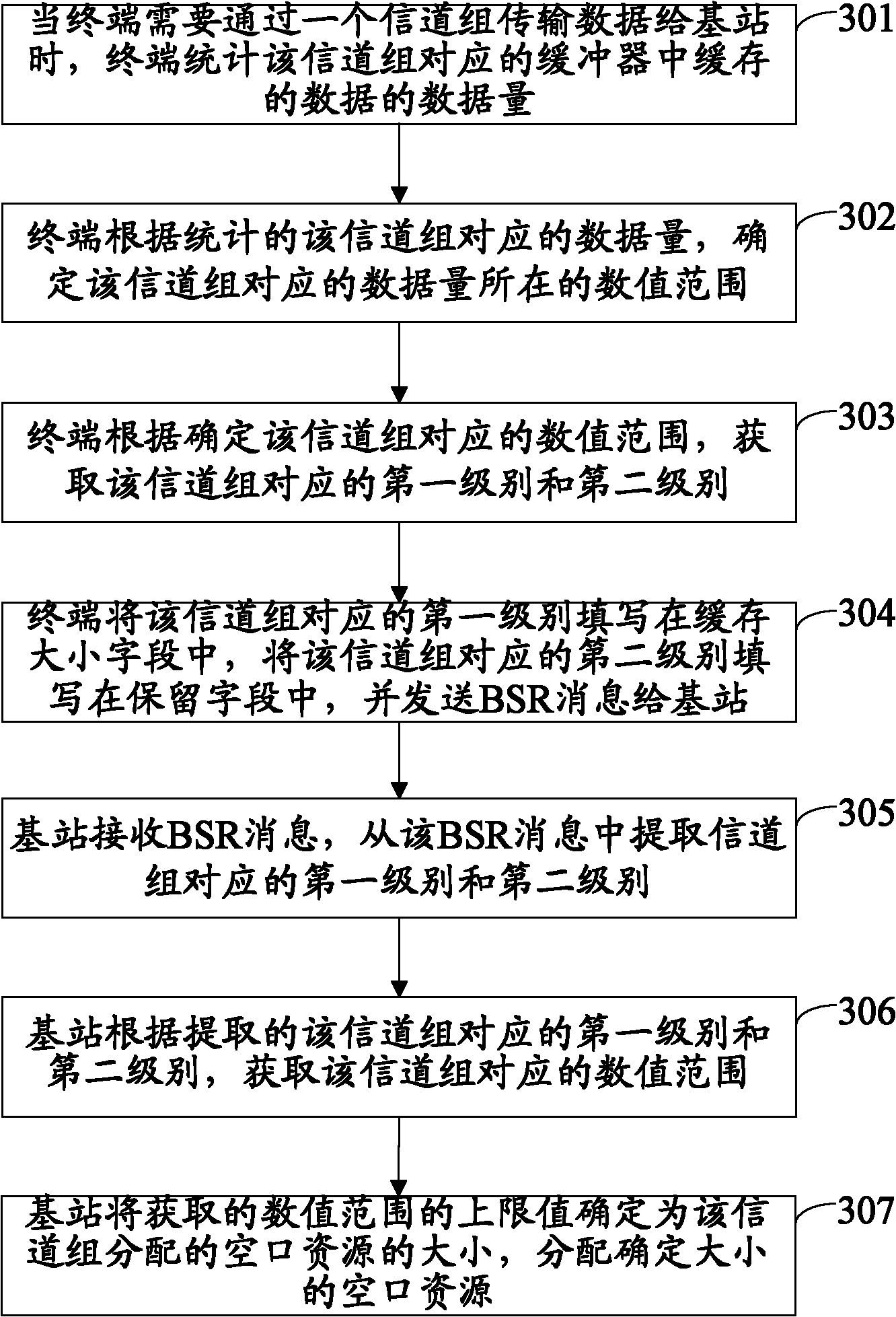
Method, device and system for allocating air interface resources
ActiveCN102083206AMeticulously dividedIncrease profitNetwork traffic/resource managementNetwork data managementAir interfaceEngineering
The invention discloses a method, device and system for allocating air interface resources, belonging to the communication field. The method comprises the steps of: obtaining a first level and a second level which correspond to a channel group according to data volume buffered in a buffer corresponding to the channel group, wherein the first level is used for indicating a section of number range,the second level is used for further indicating the number range where the data volume is in the section of number range; filling the first level in a BSR (Buffer State Report) control element of a BSR message and the second level in a BSR head of the BSR message; and sending the BSR message to a base station and requesting the base station for allocating the air interface resources. The system comprises a terminal and the base station. The terminal comprises a first acquisition module, a first filling module and a sending module. The base station comprises a first extraction module, a secondacquisition module and an allocation module. The invention can enhance the utilization rate of the air interface resources.
Owner:HONOR DEVICE CO LTD
Microseismic wave monitoring method and system based on steam-assisted gravity oil drainage
ActiveCN106873028AReduce noiseReduced shieldingSeismic signal receiversSeismic signal processingTime distributionContinuous monitoring
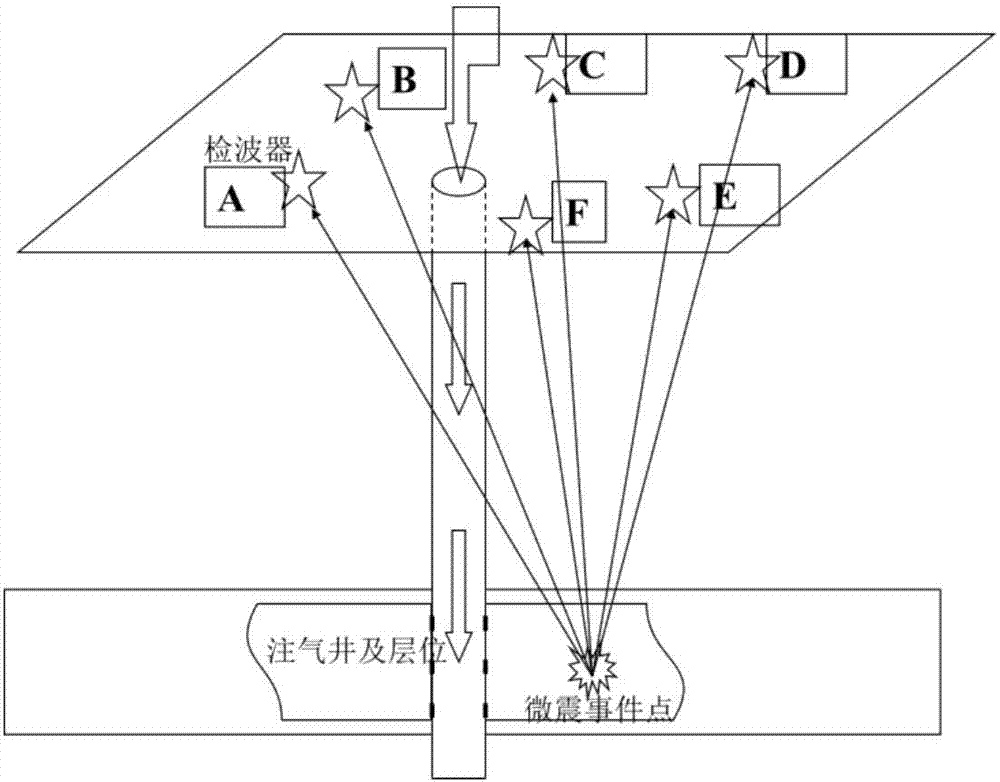
The invention relates to a microseismic wave monitoring method and system based on steam-assisted gravity oil drainage, and the method comprises the steps: arranging a detection device nearby a monitoring region, and starting the detection of a microseismic event; enabling a microseismic signal to be processed initially in an automatic manner after a monitoring substation receives the microseismic signal, and then transmitting the microseismic signal to a central processing station; enabling the central processing station to carry out the analysis and calculation of the data, and obtaining the spatial and time distribution data of the microseismic fracture energy; explaining the occurrence time, spatial distribution and size of the fracture, and determining the distribution range and occurrence time and time of a steam cavity. The invention also relates to a system, and the system comprises a ground monitoring module and an underground monitoring module. The ground monitoring module and the underground monitoring module are respectively used for receiving and processing the microseismic signal data received on the ground and in the observation well. According to the invention, the method effectively improves the event positioning precision under the complex stratum conditions. A microseismic monitoring positioning terminal is simple and reasonable in structural design, and can achieve the real-time and continuous monitoring of the microseismic signal.
Owner:克拉玛依市海晟达石油科技有限公司
Ultra-low power consumption digital baseband system based on ultrahigh frequency RFID tag chip
ActiveCN112232098AMeticulously dividedReduce power consumptionForward error control useSensing by electromagnetic radiationMemory interfaceRadio frequency
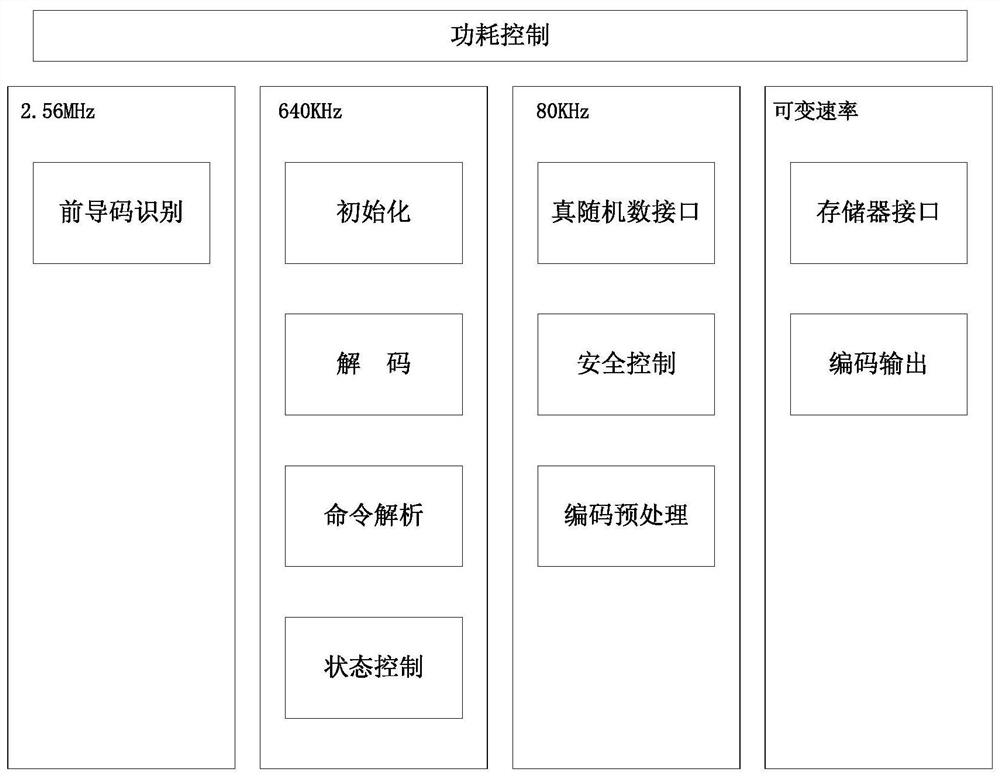
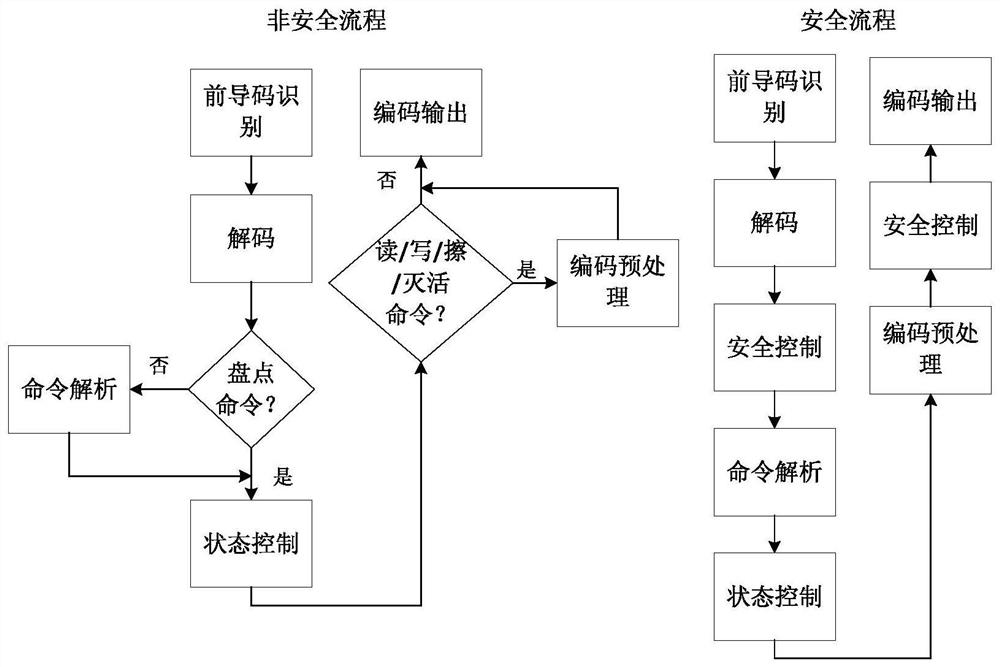
The invention discloses an ultra-low power consumption digital baseband system based on an ultrahigh frequency RFID tag chip, and belongs to the technical field of radio frequency identification. Thesystem comprises a power consumption control module, an initialization module, a lead code recognition module, a decoding module, a command analysis module, a state control module, a code preprocessing module, a code output module, a safety control module, a true random number interface and a memory interface. According to the invention, a reader signal demodulated by the RFID chip radio frequencyanalog front end can be received, decoding and command analysis are carried out, responsive label state conversion is carried out, and then a correct response signal is output and returned to the radio frequency analog front end. The system meets the GJB7377.1 protocol requirement, supports safety identification and safety communication, and is an important improvement on the prior art.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
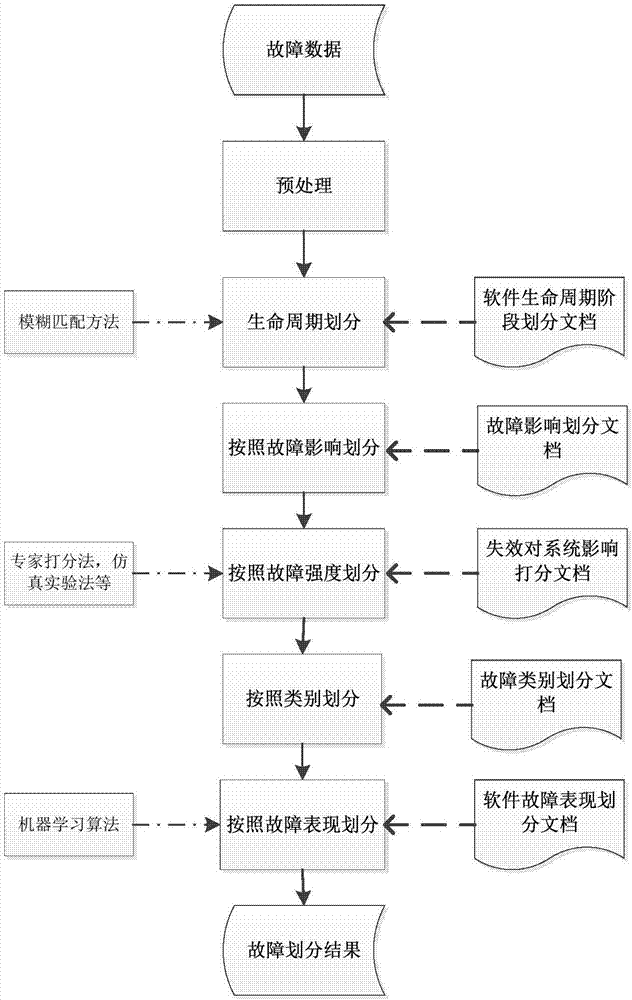
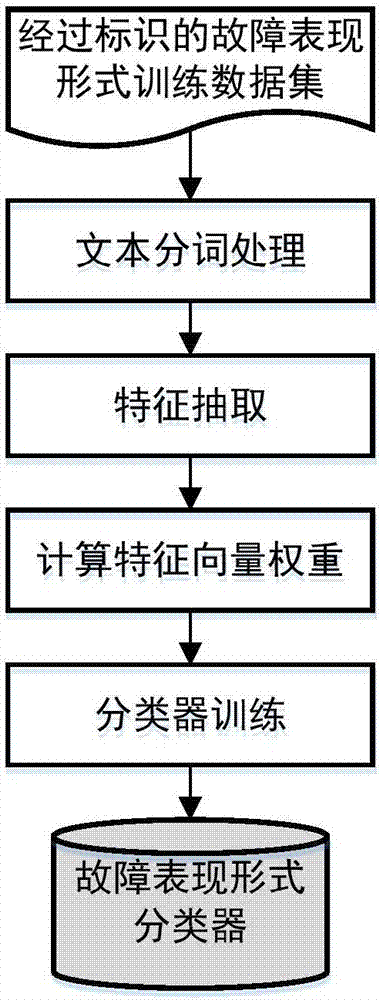
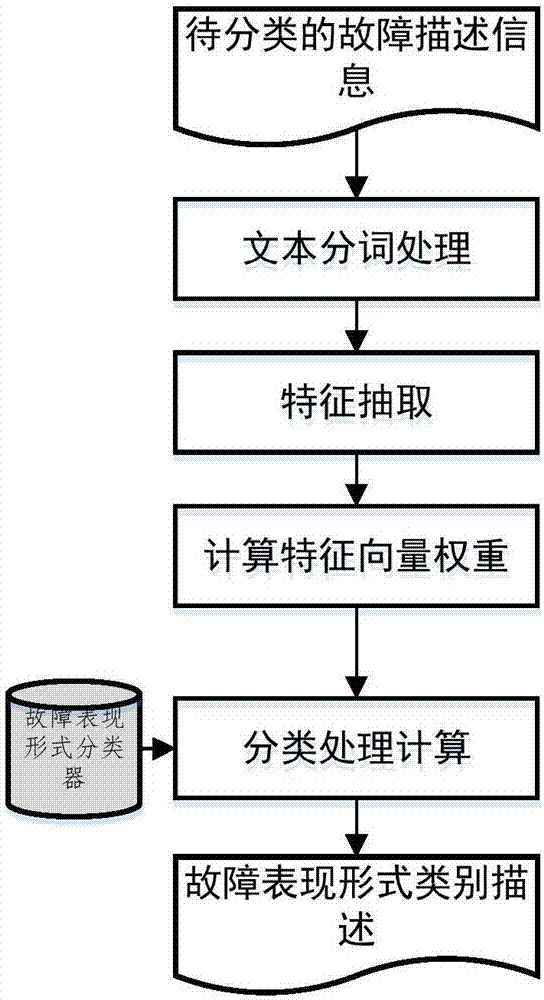
Complex software intensive system oriented fault classification method
InactiveCN107102909AMeticulously dividedHigh precisionFault responseLogic complexityClassification methods
For the problem that the conventional software fault classification methods do not consider new characteristics of a complex software intensive system, the invention provides a complex software intensive system oriented fault classification method which fully considers the new characters such as logic complexity and boundary corrosion of the complex software intensive system, can classify faults according to the life periods and fault classes, and can determine each classification attribute value of fault classification through artificial determination and machine automatic identification. The complex software intensive system oriented fault classification method can improve the accuracy and the precision of fault class division and recognition of the software intensive system, and provides a basis for fault injection research and failure mechanism research of the complex software intensive system.
Owner:BEIHANG UNIV
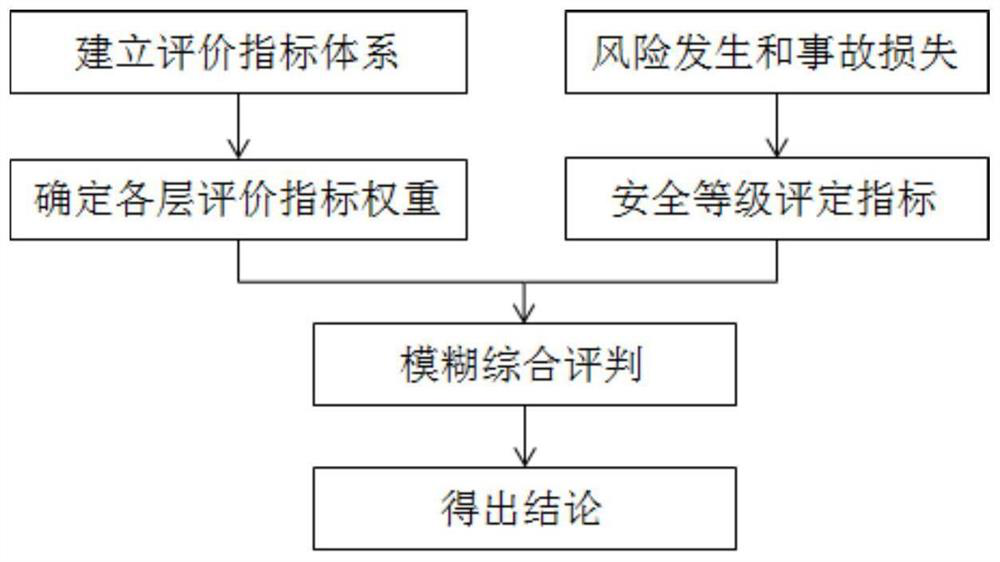
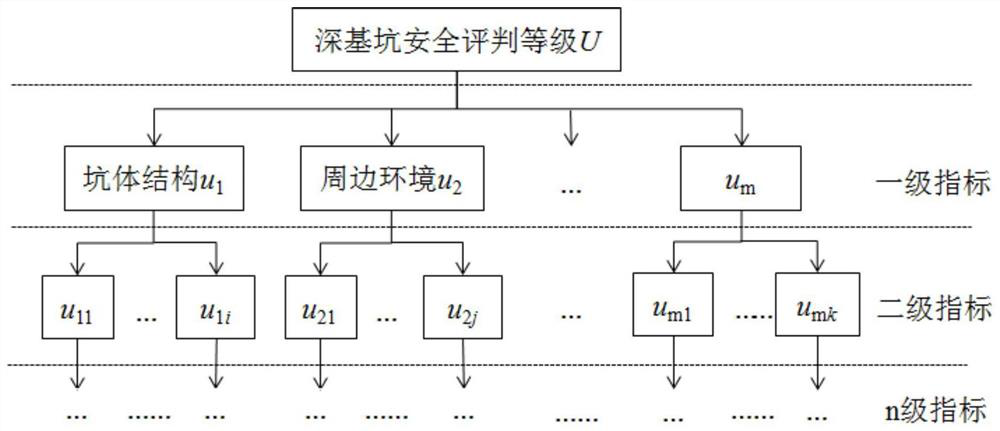
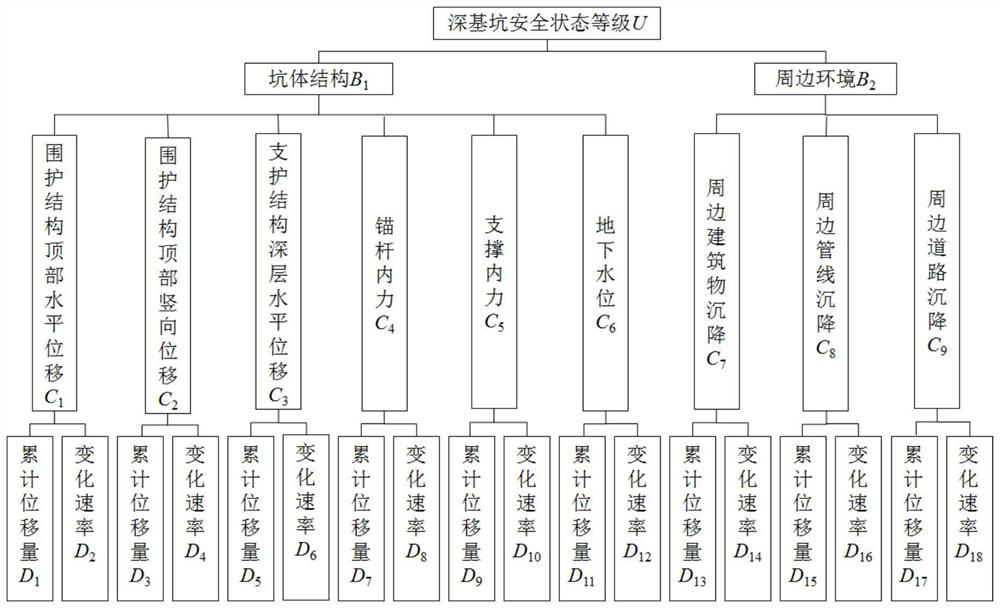
Deep foundation pit stability evaluation method based on entropy weight-analytic hierarchy process fuzzy comprehensive evaluation method
PendingCN114548725AImprove objectivityAccurate empowermentDigital data information retrievalCharacter and pattern recognitionAlgorithmEntropy weight method
The invention discloses a deep foundation pit stability evaluation method based on an entropy weight-analytic hierarchy process fuzzy comprehensive evaluation method, and belongs to the field of geotechnical mechanics and engineering. The method not only considers objectivity of index weight empowerment, but also considers risk occurrence probability and accident damage loss degree, and mainly comprises the following steps: constructing an evaluation index system; determining an evaluation index weight based on an analytic hierarchy process; based on an entropy weight method, correcting the weight of the evaluation index; determining an index comprehensive weight; dividing security levels; determining a security level; and performing fuzzy comprehensive evaluation to obtain an evaluation score. According to the method, the difference coefficient is provided, linear weighted combination is carried out on each index weight calculated by the analytic hierarchy process and the entropy weight method based on the coefficient, and the stable state of the deep foundation pit is comprehensively and quantitatively evaluated by combining the refined deep foundation pit construction safety state grade evaluation table. According to the method, the problem that judgment of the matrix A is influenced by the expert experience level in an existing analysis method is solved, the evaluation indexes can be objectively and accurately weighted, and the credibility of weight calculation is improved.
Owner:DALIAN UNIV OF TECH +1
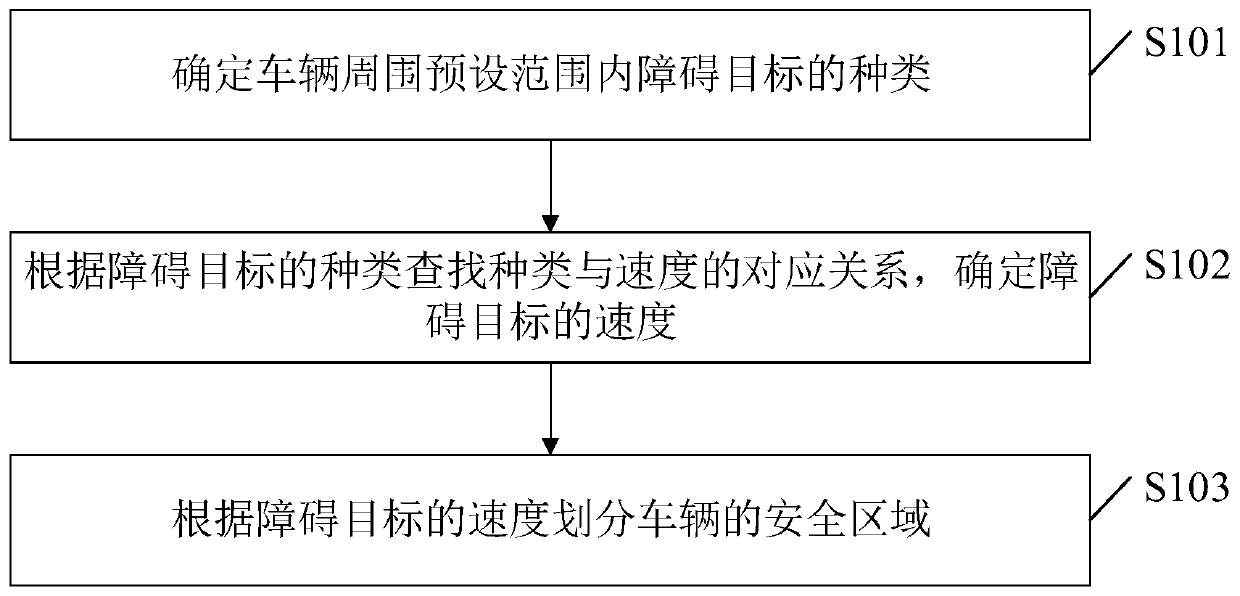
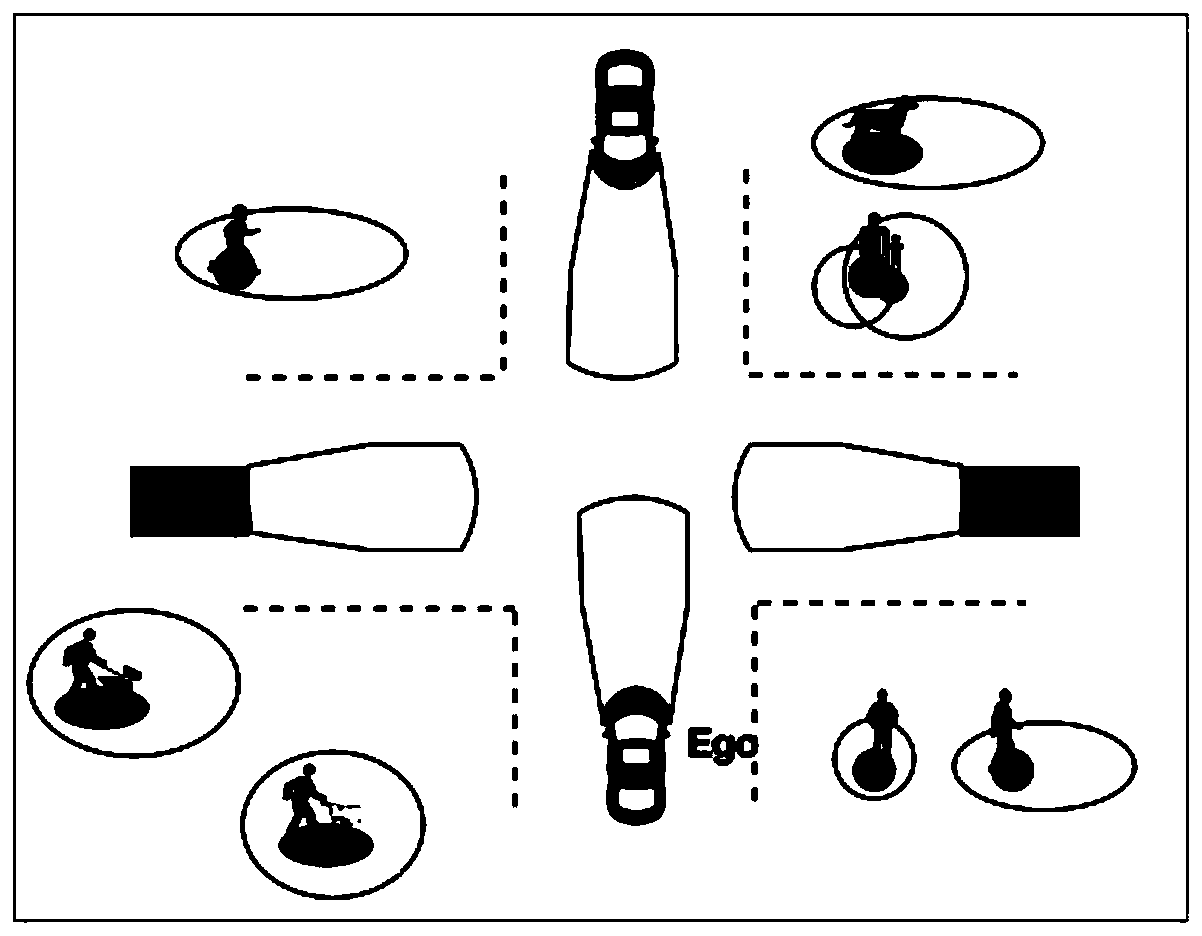
Method and device for determining vehicle safe area, electronic equipment and storage media
ActiveCN110502018AHigh precisionMeticulously dividedPosition/course control in two dimensionsComputer scienceAutopilot
The invention discloses a method and device for determining a vehicle safe area, electronic equipment and a storage media and relates to the field of intelligent traffic. The method comprises the following specific realization steps: determining the type of an obstacle target within a preset range around a vehicle; searching correspondence relation between type and speed according to the type of the obstacle target, and determining the speed of the obstacle target; and dividing a safe area of the vehicle according to the speed of the obstacle target. The method can improve accuracy of divisionof the vehicle safe area. The scheme can be used in the field of autonomous driving, especially autonomous parking.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
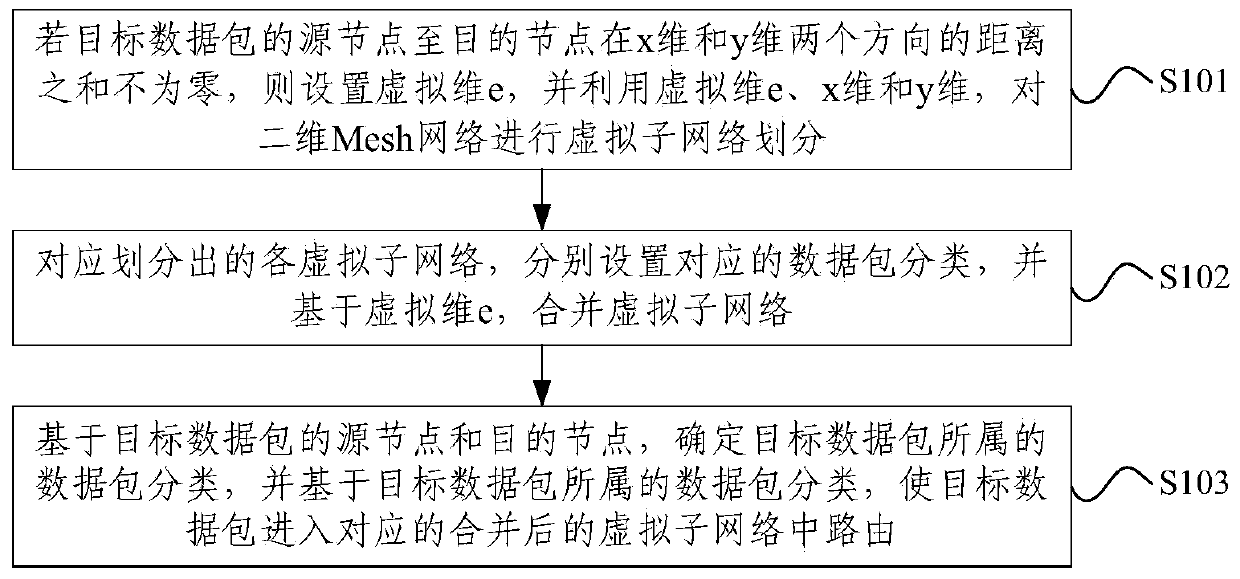
Self-adaptive routing method for data packets in two-dimensional Mesh network and electronic equipment
ActiveCN110048947AMeticulously dividedImprove channel utilizationData switching networksSelf adaptiveData transmission
The embodiment of the invention provides a self-adaptive routing method for data packets in a two-dimensional Mesh network and electronic equipment. The method comprises the steps of setting a virtualdimension e if the sum of distances from a source node of a target data packet to a target node in an x-dimensional direction and a y-dimensional direction is not zero, and performing virtual sub-network division on the two-dimensional Mesh network by utilizing the virtual dimension e, the x-dimension and the y-dimension; correspondingly dividing the virtual sub-networks, respectively setting corresponding data packet classifications, and combining the virtual sub-networks based on the virtual dimension e; and based on the source node and the destination node of the target data packet, determining the data packet classification to which the target data packet belongs, and based on the data packet classification to which the target data packet belongs, enabling the target data packet to enter a corresponding merged virtual sub-network for routing. According to the embodiment of the invention, the channel utilization rate of the two-dimensional Mesh network can be effectively improved,and the channel usage amount is reduced, so that the data transmission efficiency is effectively improved.
Owner:TSINGHUA UNIV
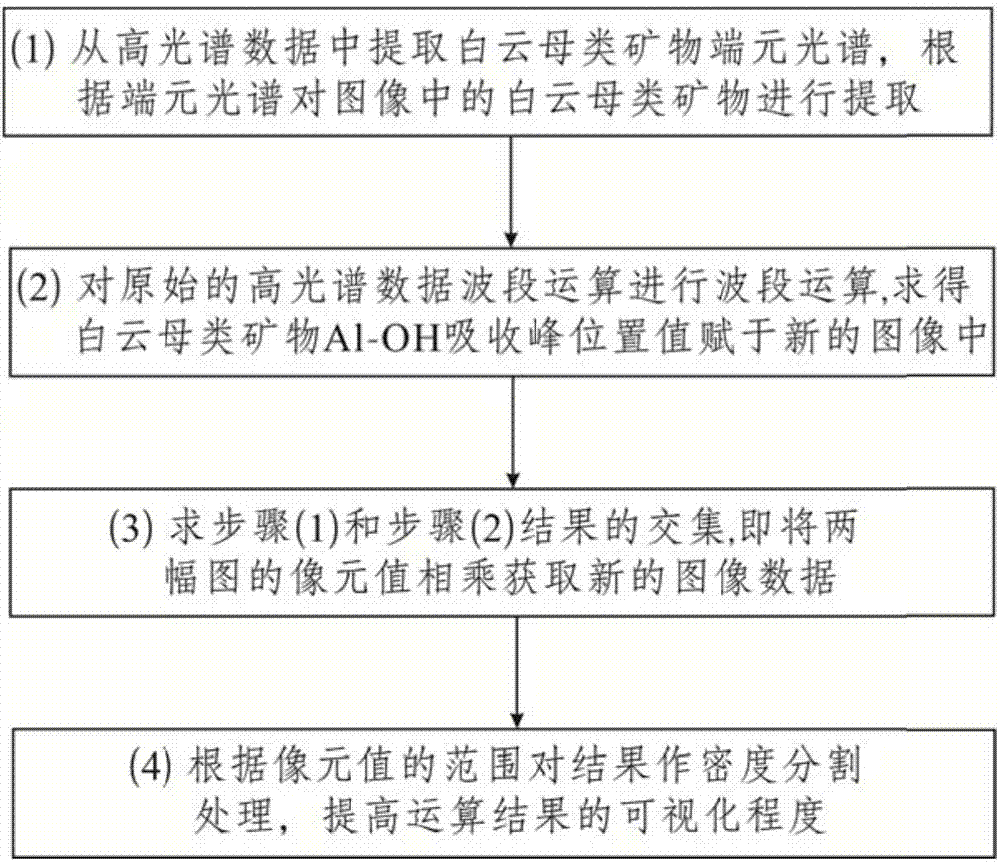
Method for calculating Al-OH absorption position of muscovite by using hyperspectral data
ActiveCN108007902AMeticulously dividedInvestigating crystalsScattering properties measurementsAviationTreatment results
The invention belongs to the technical field of hyperspectral remote sensing analysis, and particularly relates to a method for calculating the Al-OH absorption position of muscovite by using hyperspectral data. The method comprises: 1, extracting muscovite type minerals, and recording the result as result (Muscovite); 2, carrying out wave band calculation on aviation hyperspectral data, and recording the calculation result as result (Al-OH); 3, calculating the intersection set of the treatment result of the step 1 and the treatment result of the step 2, and recording as result (mus-wavelength); and 4, carrying out density division on the result obtained in the step 3. According to the present invention, based on the aviation hyperspectral data in the existing spectral resolution, the muscovite type mineral unit is extracted, the Al-OH absorption peak position of the muscovite type mineral is calculated through the wave band calculation, and further the muscovite type mineral is subdivided according to the absorption peak position so as to be well used for mineral exploration.
Owner:BEIJING RES INST OF URANIUM GEOLOGY
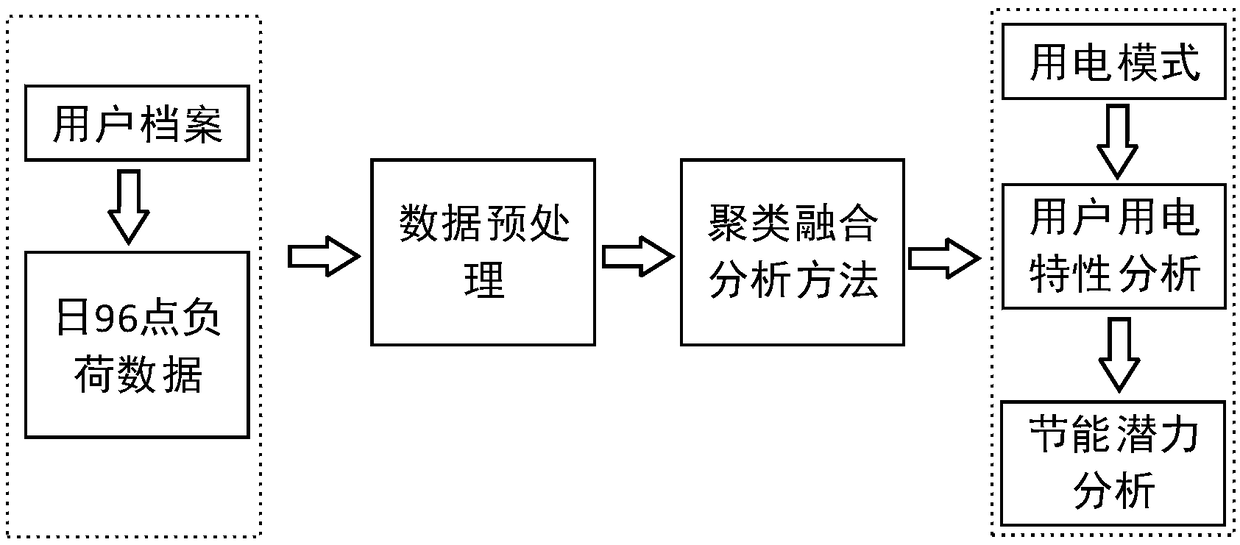
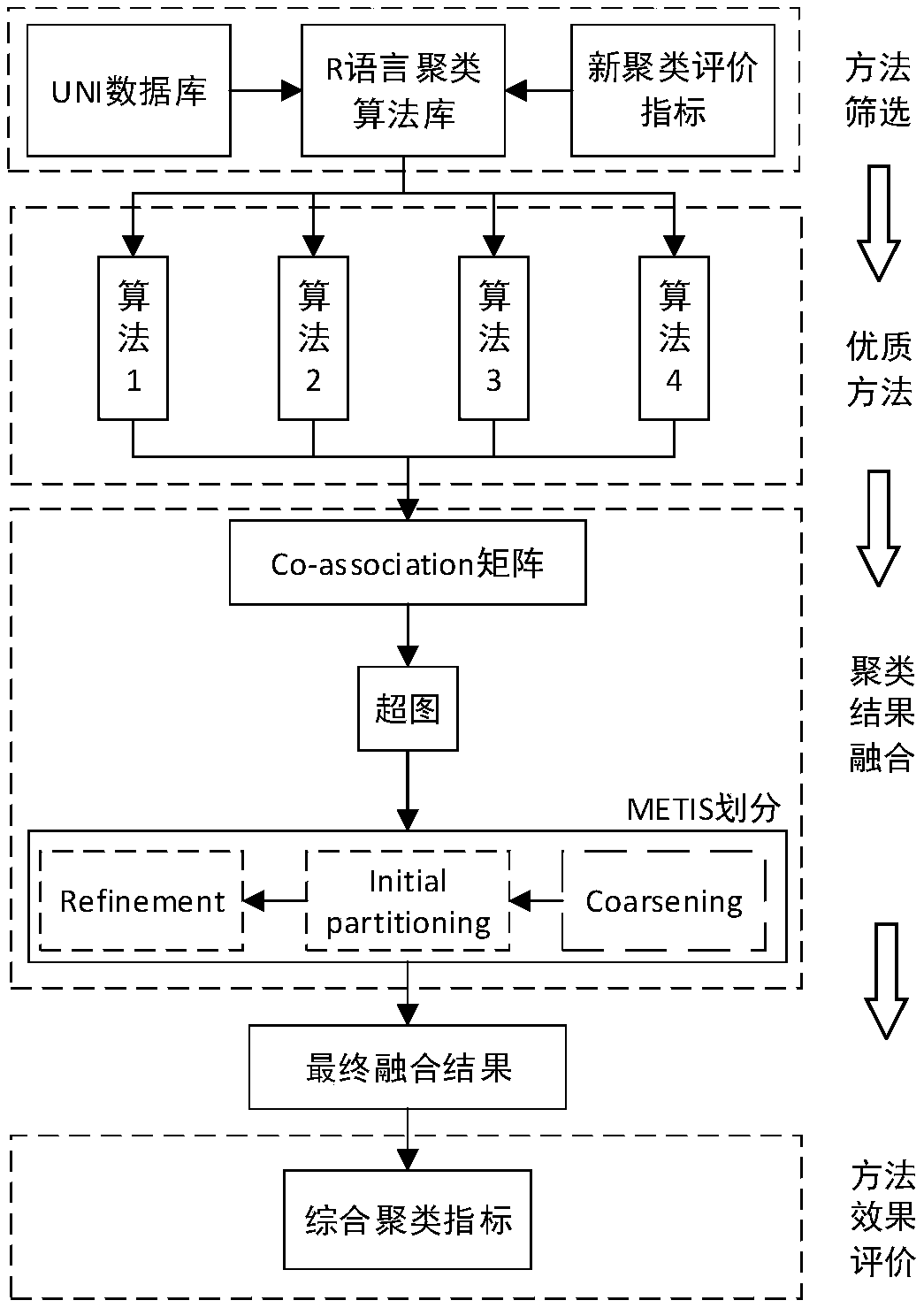
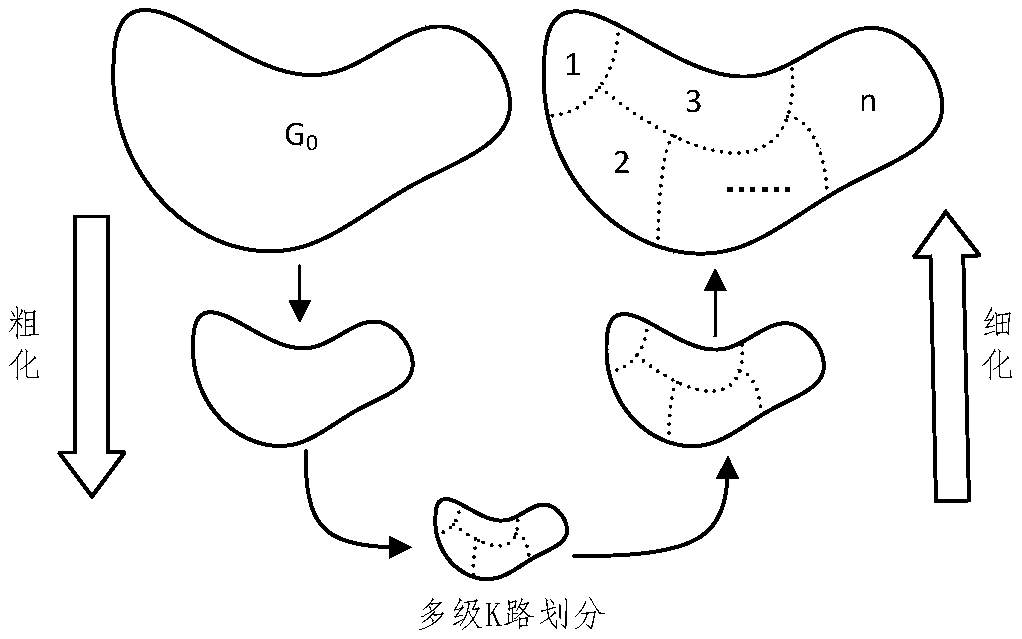
User behavior analysis method for large-scale buildings based on improved clustering fusion
ActiveCN109064353AImprove effectivenessImprove accuracyCharacter and pattern recognitionResourcesCluster algorithmState of art
The invention relates to a large-scale building user behavior analysis method based on improved clustering fusion. The method is used for determining the power consumption mode of the large-scale building user. The method comprises the following steps: (1) obtaining the total load data of the large-scale building user to be analyzed and the sub-item measurement data; (2) constructing the comprehensive evaluation index of clustering effect, and selecting various high-quality clustering methods; (3) Clustering the total load data of large-scale building users to obtain different clustering results by using the selected high-quality clustering method; (4) fusing the clustering results obtained by the high-quality clustering method to obtain the final power consumption mode. Compared with theprior art, the invention can absorb the advantages of different single clustering algorithms, the effectiveness and the accuracy of the clustering algorithm are higher than those of the single clustering method, and the expansibility is improved.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +1
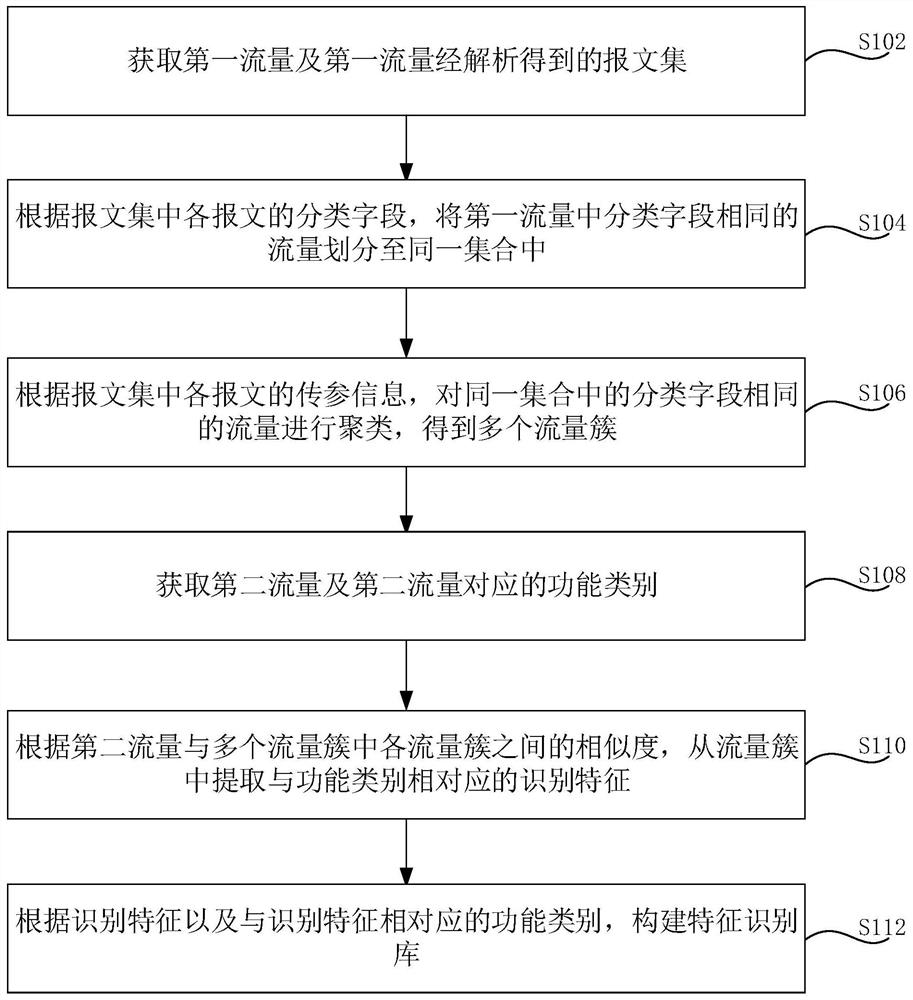
Method and device for constructing feature recognition library and flow recognition method
PendingCN113890902ADetailed traffic divisionImprove accuracyCharacter and pattern recognitionTransmissionMachine learningComputer device
The invention relates to a feature recognition library construction method and device, a traffic recognition method, computer equipment and a storage medium. The feature recognition library construction method comprises the steps of obtaining first traffic and a message set obtained by analyzing the first traffic; according to the classification field of each message in the message set, dividing the traffic with the same classification field in the first traffic into the same set; according to the transmission parameter information of each message in the message set, clustering the traffic with the same classification field in the same set to obtain a plurality of traffic clusters; obtaining a second flow and a function category corresponding to the second flow; according to the similarity between the second traffic and each traffic cluster in the plurality of traffic clusters, extracting identification features corresponding to the function categories from the traffic clusters; and constructing a feature recognition library according to the recognition features and the function categories corresponding to the recognition features. By adopting the method, the accuracy of feature recognition in the feature recognition library can be improved, so that the accuracy is higher when the feature recognition library is adopted for traffic recognition.
Owner:BEIJING QIANXIN TECH +1
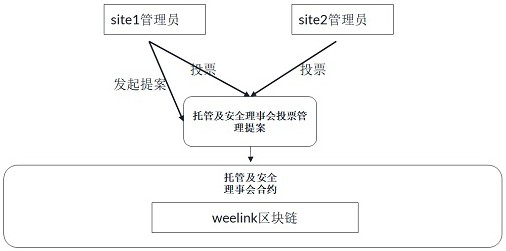
Network security communication system based on block chain smart contract
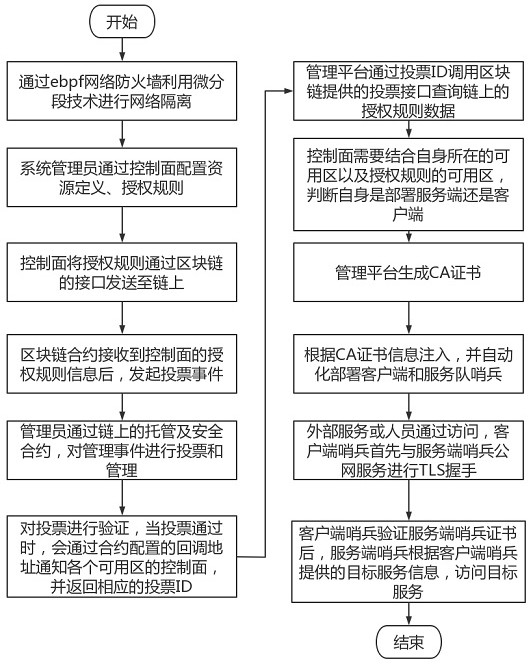
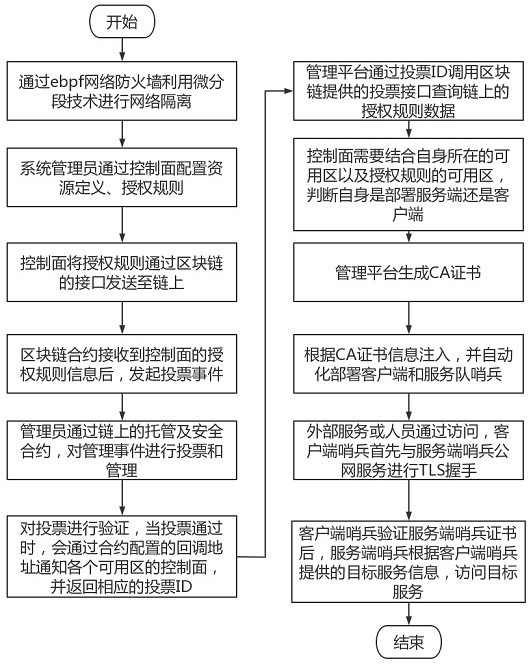
ActiveCN114430350AImprove securityGuaranteed traceabilityUser identity/authority verificationNeural architecturesSystem administratorAuthorization
The invention discloses a network security communication system based on a block chain smart contract, and belongs to the technical field of digital information transmission. The system comprises a network isolation module, a user-defined configuration module, an authorized access module, an intelligent contract module, a certificate management module, an automatic deployment module and a sentry verification module. Network isolation is carried out through a network isolation module by adopting an ebpf network firewall and utilizing a micro-segmentation technology; through the custom configuration module, a system administrator configures custom resources and authorization rules on the platform and initiates voting; the administrator votes and manages the management event through the trusteeship and security contract on the block chain by using the authorization access module; querying a contract through an intelligent contract module to obtain a corresponding state change; generating a CA certificate by using a certificate management module; automatically deploying a client and a service team sentinel by using an automatic deployment module according to CA certificate information injection; and the guard verification module is used for accessing a specified interface.
Owner:南京智人云信息技术有限公司
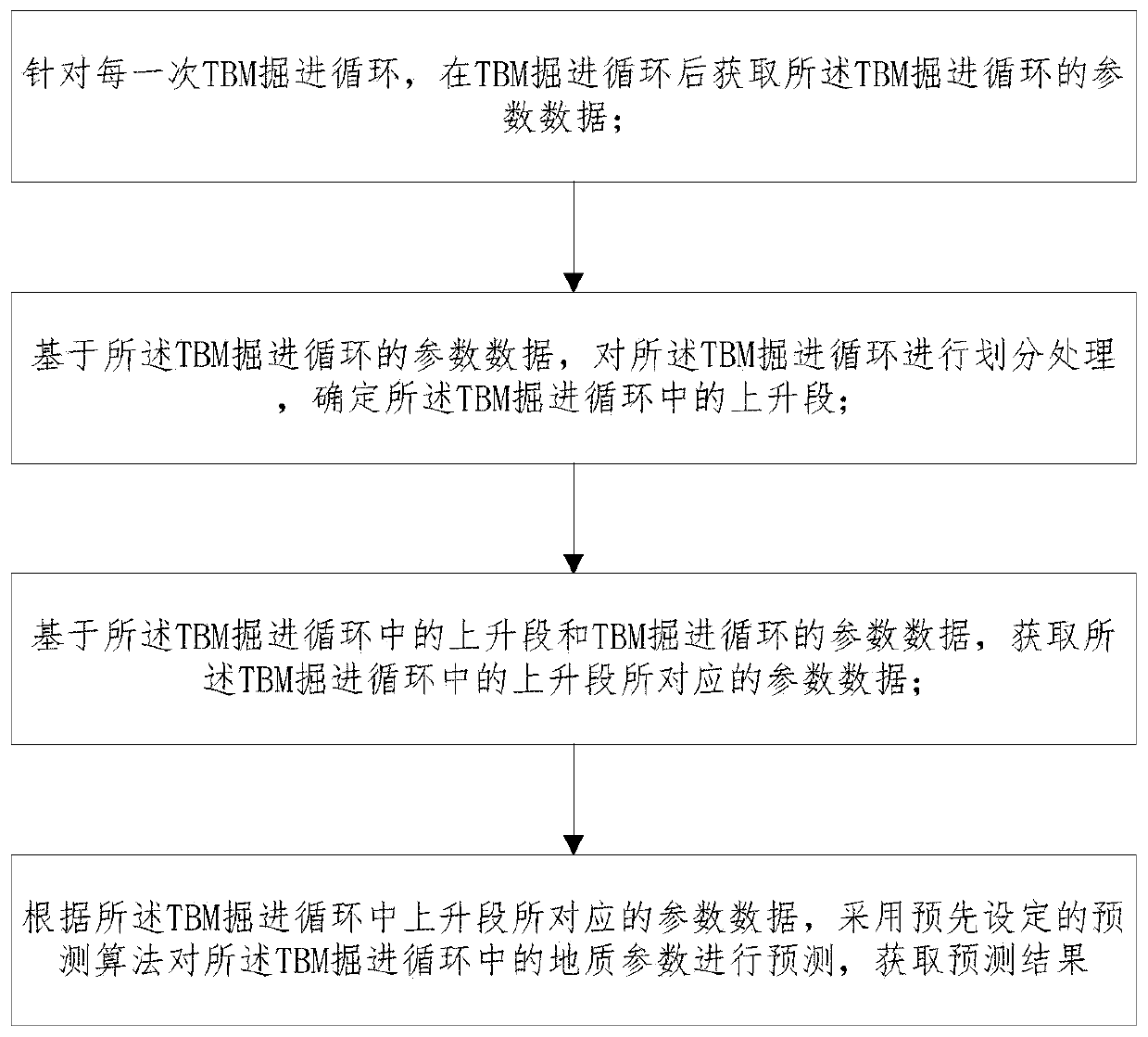
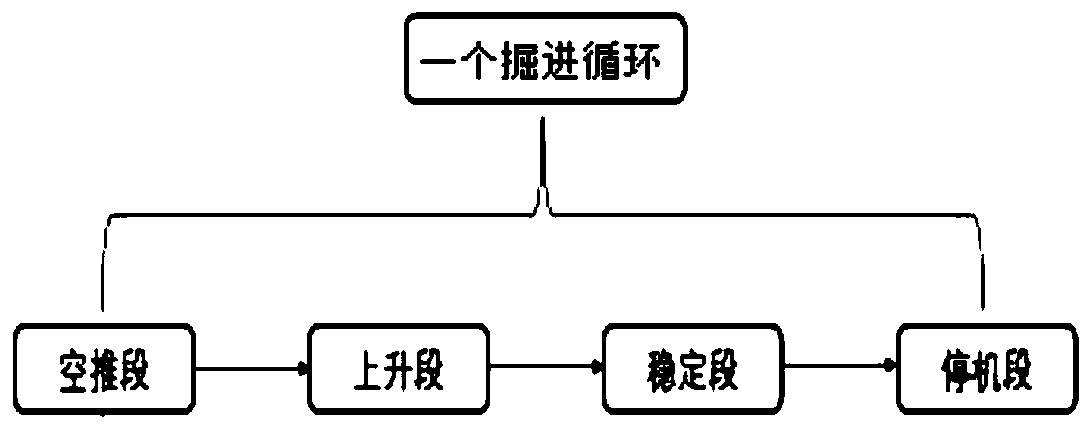
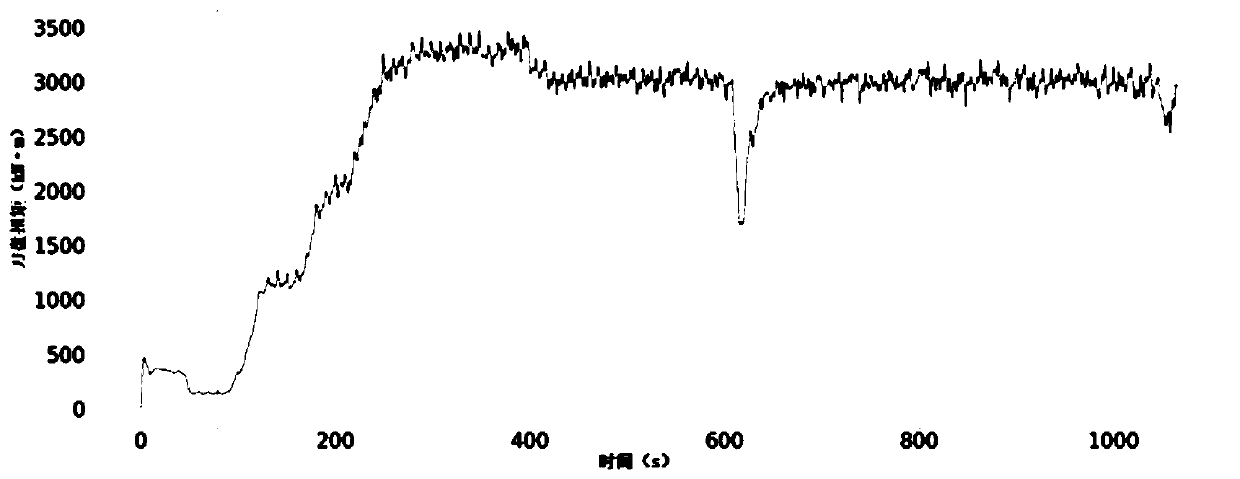
Method for dividing open type TBM construction data tunneling cycle
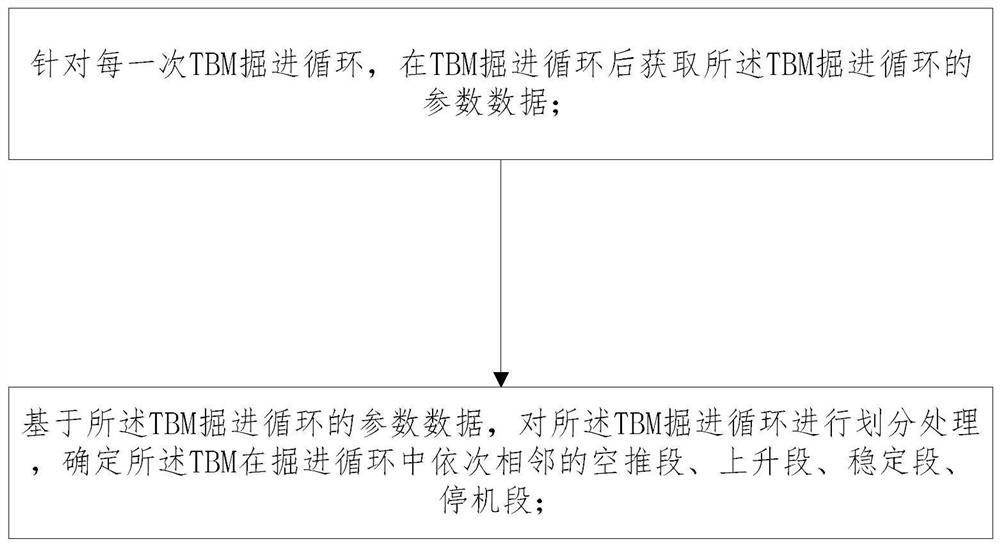
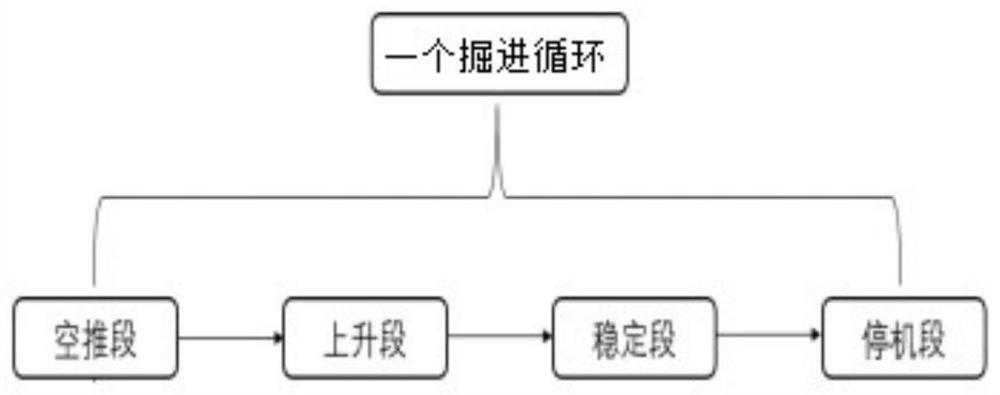
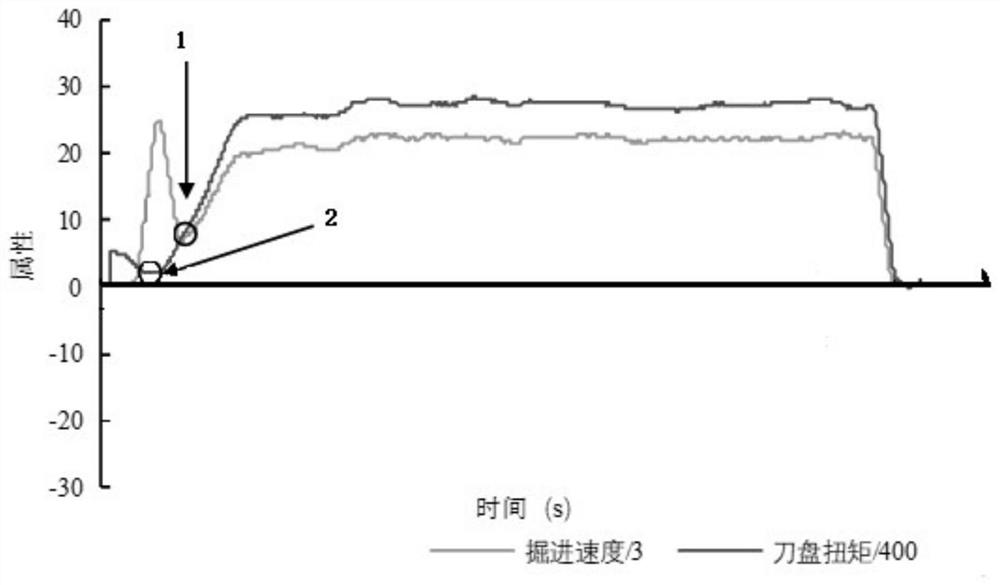
ActiveCN111594198AAccurate divisionMeticulously dividedMining devicesTunnelsPrediction algorithmsComputational physics
The invention relates to a method for dividing an open type TBM construction data tunneling cycle. The method comprises the following steps that A1, for each TBM tunneling cycle, parameter data of theTBM tunneling cycle are acquired after the TBM tunneling cycle; A2, based on the parameter data of the TBM tunneling cycle, division processing is performed on the TBM tunneling cycle, and a rising segment in the TBM tunneling cycle is determined; A3, the parameter data corresponding to the rising segment in the TBM tunneling cycle are acquired based on the rising segment in the TBM tunneling cycle and the parameter data of the TBM tunneling cycle; and A4, geological parameters in the TBM tunneling cycle are predicted by adopting a preset prediction algorithm according to the parameter data corresponding to the rising segment in the TBM tunneling cycle, and a prediction result is obtained. According to the method, the performance parameters of cutter disc torque equipment and two equipment control parameters such as the tunneling speed and the cutting disc rotating speed are utilized, the empty push segment, the rising segment, the stable segment and the stop segment of the open typeTBM tunneling cycle can be effectively divided, and the tunneling cycle division is more accurate and detailed.
Owner:NORTHEASTERN UNIV
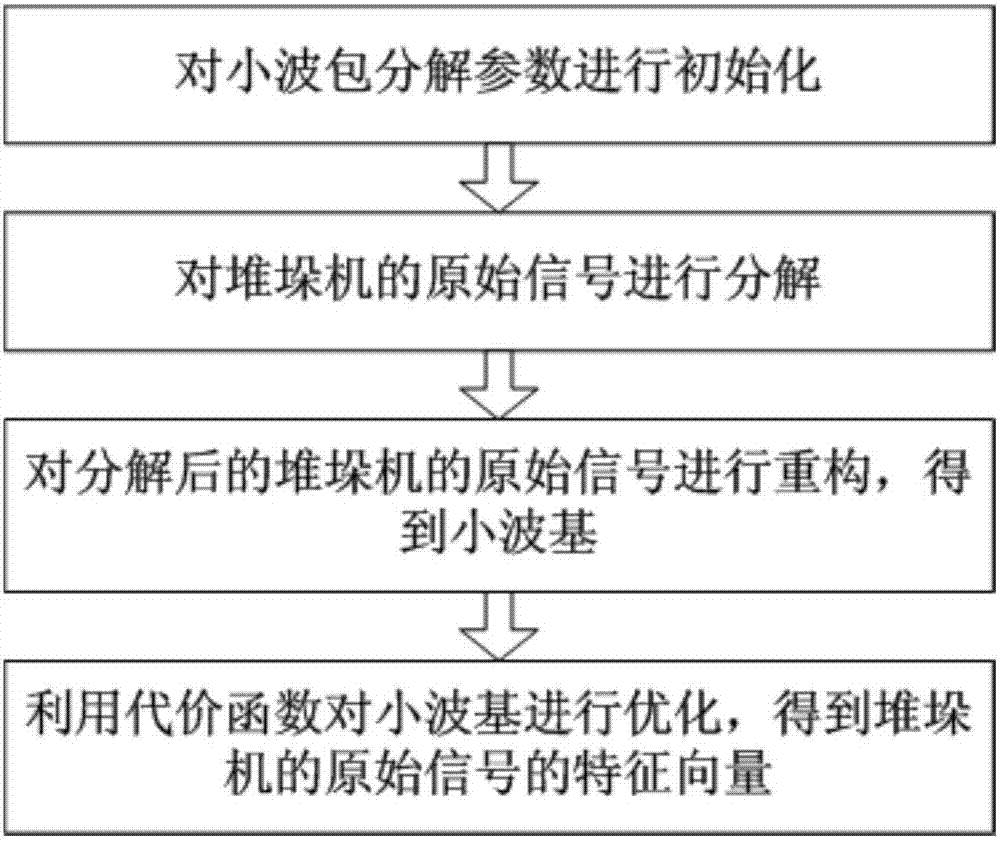
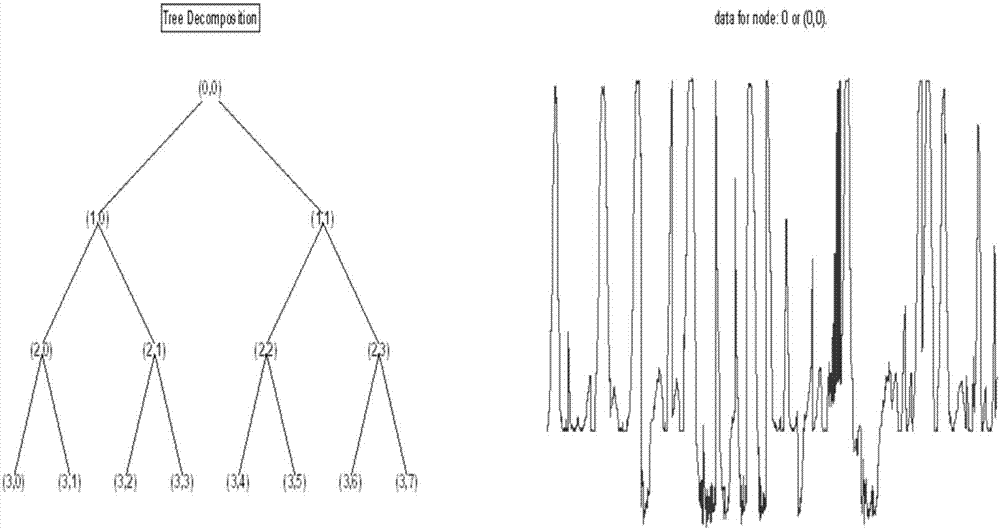
Method for extracting characteristic data of stacker based on wavelet packet analysis
InactiveCN107368801AAchieve the purpose of compressionReasonable decompositionCharacter and pattern recognitionComplex mathematical operationsData ingestionFeature vector
The present invention discloses a method for extracting characteristic data of a stacker based on wavelet packet analysis. According to the method disclosed by the present invention, a wavelet packet decomposition parameter is initialized, an appropriate scaling function is selected, and a wavelet library is generated through the scaling function, so that the optimal decomposition effect is achieved, and the signal is decomposed reasonably; an appropriate cost function is selected so as to seek the optimal wavelet base, and the cost function satisfies the monotonicity and additivity; through the functions, the purpose that the original signal is compressed is achieved, and the size of the data is reduced; eigenvectors containing complete information of the original signal is obtained, and the working state signal for the stacker is processed and expanded; and the eigenvectors of the original signal of the stacker are extracted in the process, so that the purpose of data compression is achieved and good application prospect is ensured.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO ELECTRIC POWER RES INST +2
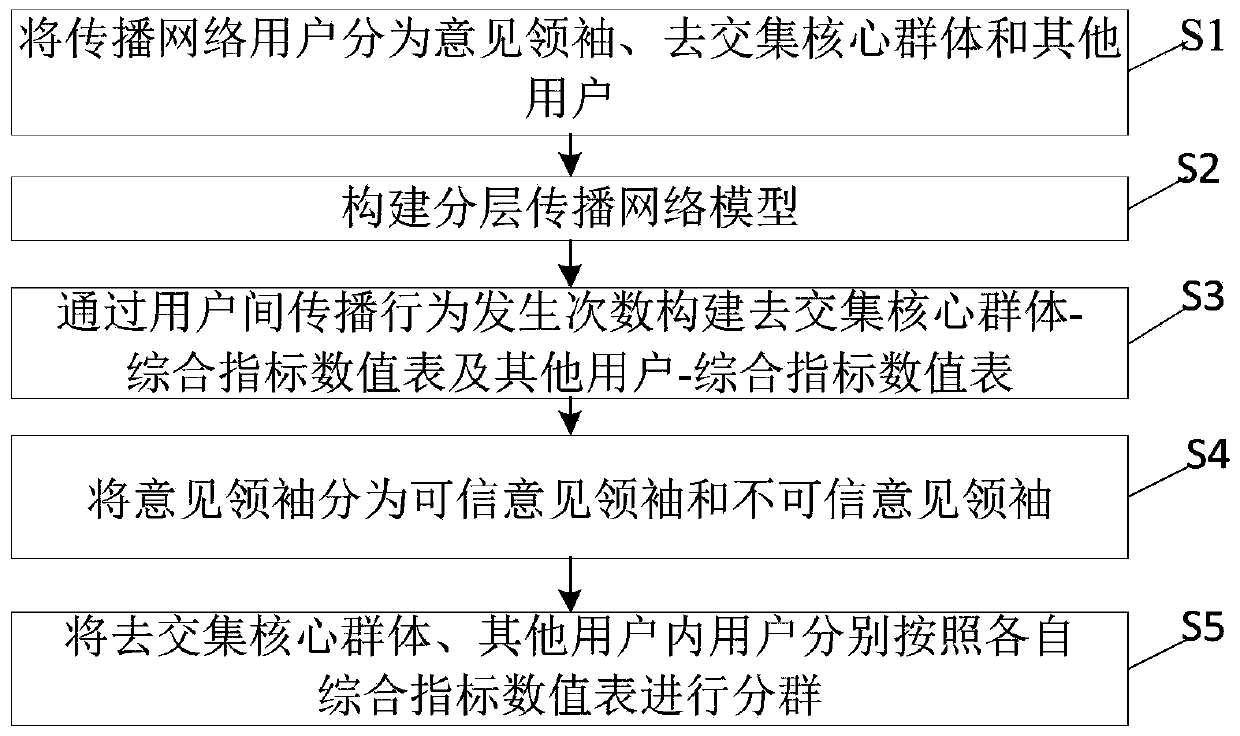
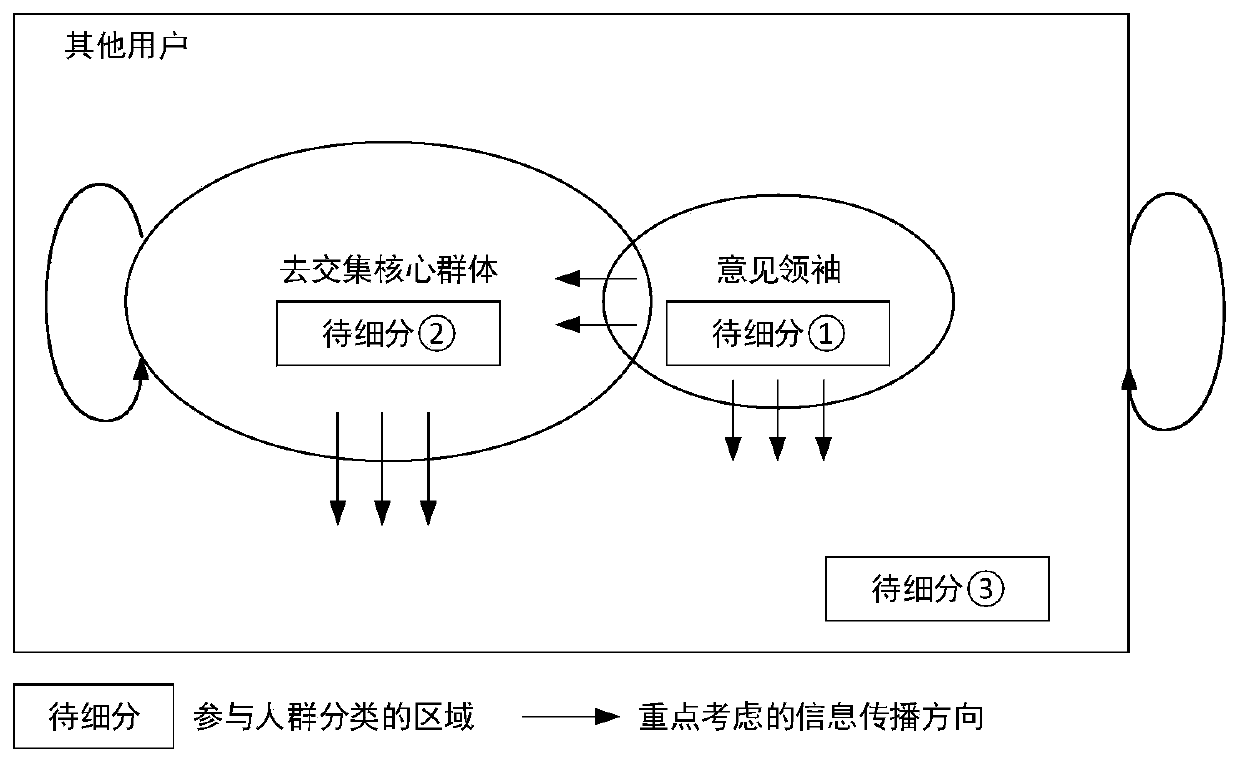
Clustering method and system based on core group mining and opinion leader identification results
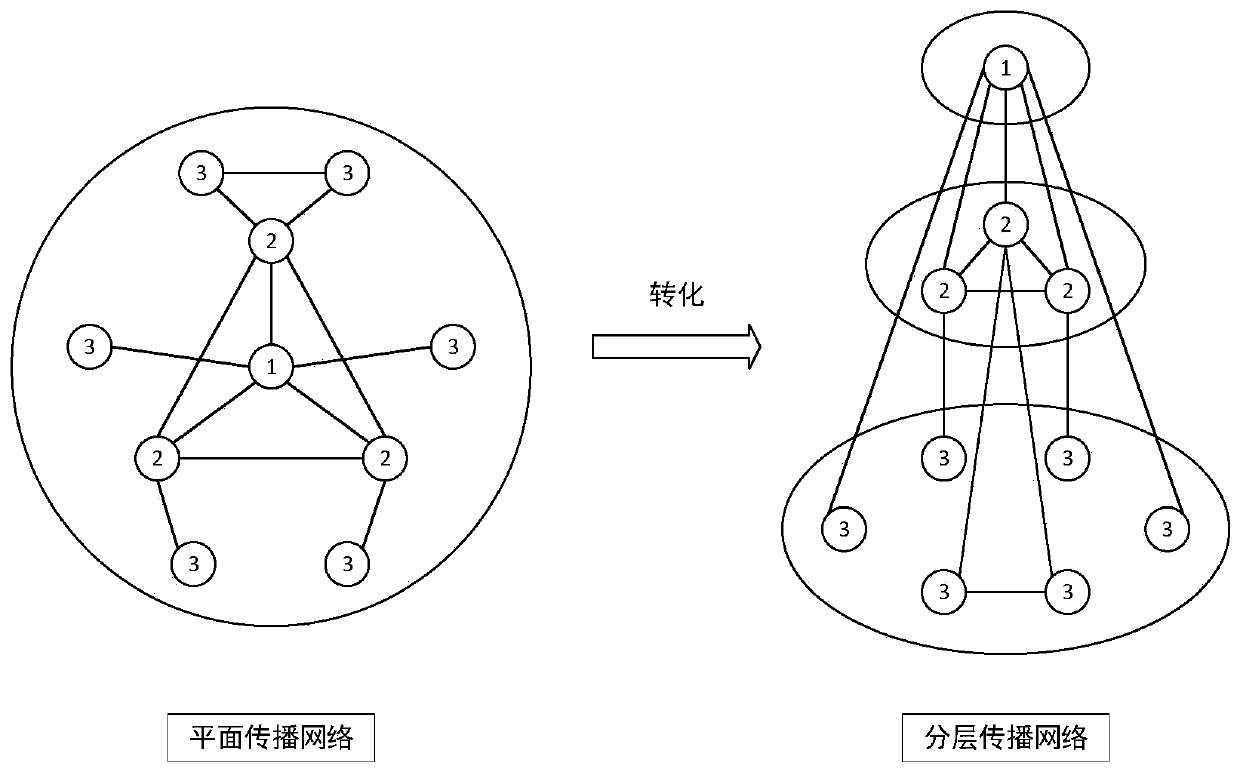
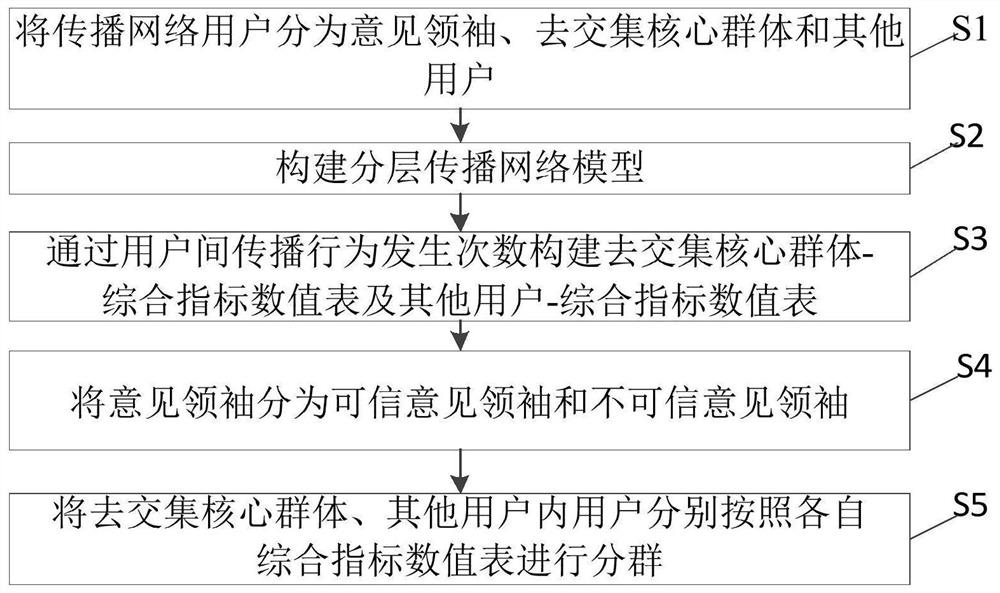
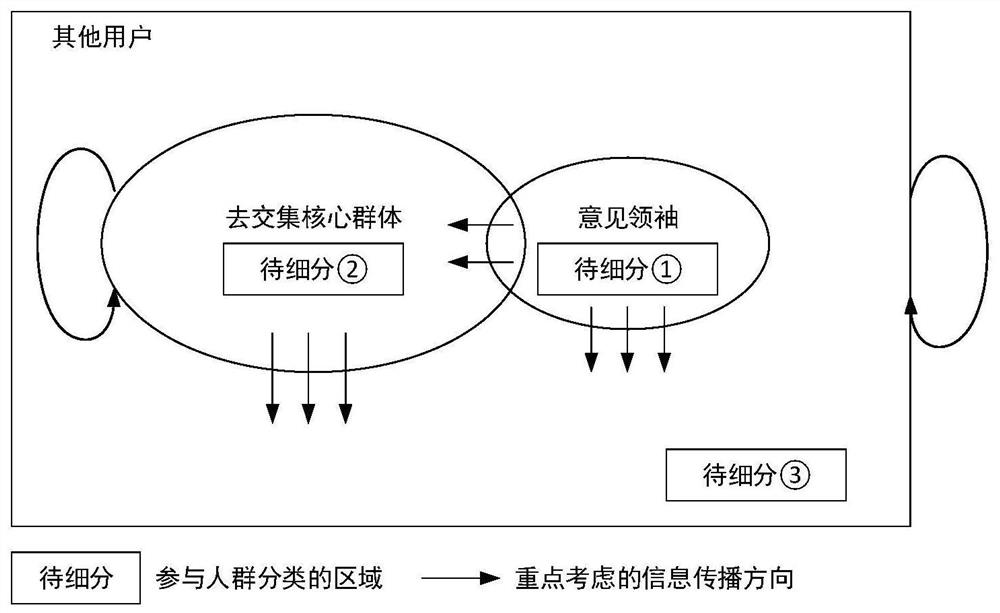
ActiveCN109828998APioneering taxonomyMeticulously dividedData processing applicationsSpecial data processing applicationsNODALNetwork model
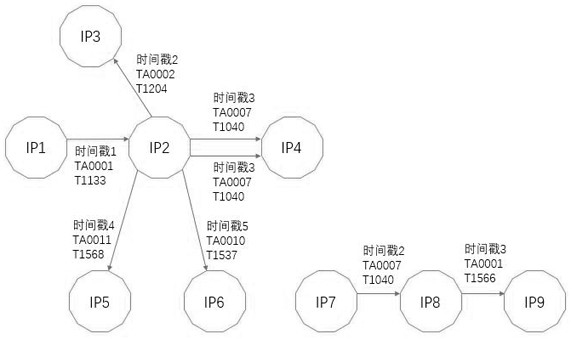
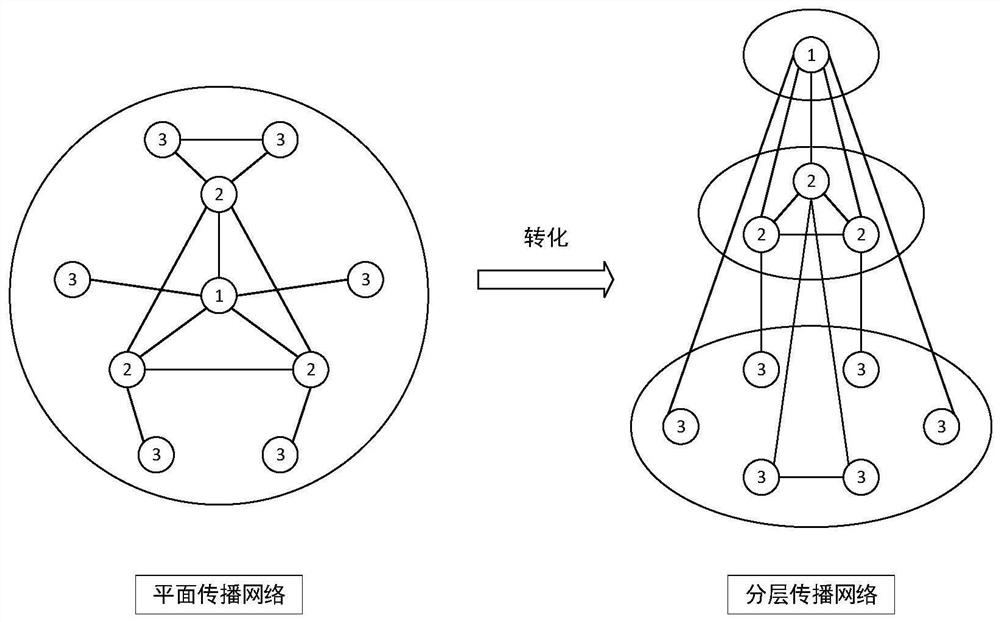
The invention provides a clustering method and system based on core group mining and opinion leader identification results. The clustering method comprises the following steps: dividing a propagationnetwork user into an opinion leader, a de-intersection core group and other users; constructing a hierarchical propagation network model wherein nodes are users in the three classes, and propagation behaviors among the users serve as paths among the corresponding nodes; by obtaining the number of times the propagation behavior occurs, acquiring different comprehensive index values of different propagation directions of the middle layer and the bottom user, and a de-intersection core group-integrated indicator value table and other user-integrated indicator value tables are constructed; dividing the opinion leader into credible opinions. Leaders and untrustworthy opinion leaders; grouping users who go to the core group and other users according to the core group-combined indicator value table and other user-integrated indicator value tables. According to the method and the system, the core group mining result and the opinion leader identification result are fully utilized to realize user grading based on the event participation degree.
Owner:COMMUNICATION UNIVERSITY OF CHINA
User right control method and apparatus
InactiveCN105608373AIncrease flexibilityMeticulously dividedPlatform integrity maintainanceEmbedded systemUser Privilege
Owner:DAWNING INFORMATION IND BEIJING
Office software operation and maintenance monitoring system
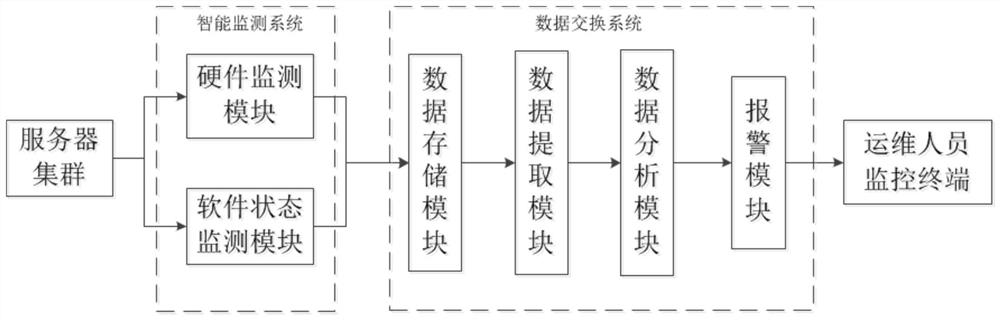
InactiveCN112631404AEasy maintenanceRapid positioningDigital data processing detailsHardware monitoringData ingestionMonitoring system
The invention discloses an office software operation and maintenance monitoring system, which belongs to the technical field of operation and maintenance monitoring, and comprises a server cluster, a data exchange system and an intelligent monitoring system, and is characterized in that the server cluster comprises a plurality of servers, and the intelligent monitoring system comprises a hardware monitoring module; wherein monitoring objects of the hardware monitoring module comprise a CPU average workload, a memory usage rate, a network transmission rate value and a network bandwidth occupancy rate of the server; the data exchange system comprises a data extraction module, a data analysis module, a data storage module and an alarm module; and the server, the hardware monitoring module, the data storage module, the data extraction module, the data analysis module and the alarm module are connected in sequence. The problem that an existing office software operation and maintenance monitoring system lacks a mechanism for discovering faults in advance is solved.
Owner:上海丰乐信息科技有限公司
Projector convenient for calibrating projection position and good in stability
InactiveCN111193914AHigh precisionMeticulously dividedPicture reproducers using projection devicesElectric machineryAir pump
The invention discloses a projector convenient to calibrate a projection position and good in stability. The projector comprises a projector body, lifting mechanisms, a fixing mechanism and an air passage. A bottom plate is fixed with the lower surface of the projector body through bolts. A rotating rod is mounted below the middle position of the bottom plate. A supporting plate is arranged on theouter side of the rotating rod. A rotating mechanism is mounted below the rotating rod. The lifting mechanisms are installed at the four corners of the outer edge of the supporting plate correspondingly. A mounting box is connected below the lifting mechanisms. The fixing mechanism is connected with the lower portion of the mounting box. A lifting motor is mounted in the mounting box. A transverse plate is fixed on the outer surface of the inner side of the mounting box. An air pipe is mounted on the lower surface of the transverse plate. A micro air pump is fixed on the middle of the upper surface of the transverse plate, and a connecting pipe is mounted at the joint of the micro air pump and the air pipe. According to the invention, the accuracy of adjusting the calibration projection position of the projector is improved, and the projector is adsorbed on a desktop through negative pressure, thereby facilitating the improvement of the fixing stability of the projector.
Owner:厦门卓旭智能科技有限公司
Open type TBM tunneling cycle division method, surrounding rock grade prediction method and lithology prediction method
The invention relates to an open type TBM tunneling cycle division method, a surrounding rock grade prediction method and a lithology prediction method. The open type TBM tunneling cycle division method comprises the steps that for each TBM tunneling cycle, parameter data of the TBM tunneling cycle are obtained after the TBM tunneling cycle, wherein TBM tunneling cycle parameter data comprises cutterhead torque data, tunneling speed data and cutterhead rotating speed data in the TBM tunneling cycle; and on the basis of the parameter data of the TBM tunneling cycle, the TBM tunneling cycle is divided, and an empty pushing section, an ascending section, a stable section and a shutdown section, sequentially adjacent to each other, of the TBM in the tunneling cycle are determined. The invention also relates to a surrounding rock grade prediction method. The surrounding rock grade prediction method comprises the following steps: acquiring second data in each tunneling cycle to be predicted; and inputting the second data into the trained classification model to obtain a classification result.
Owner:NORTHEASTERN UNIV
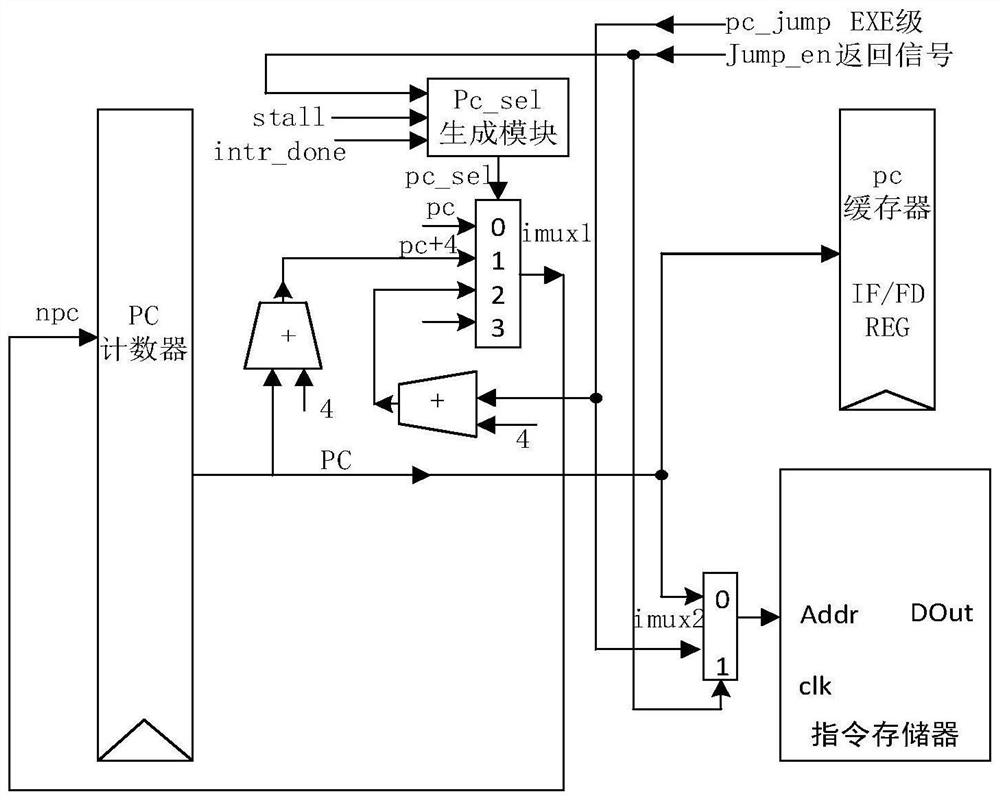
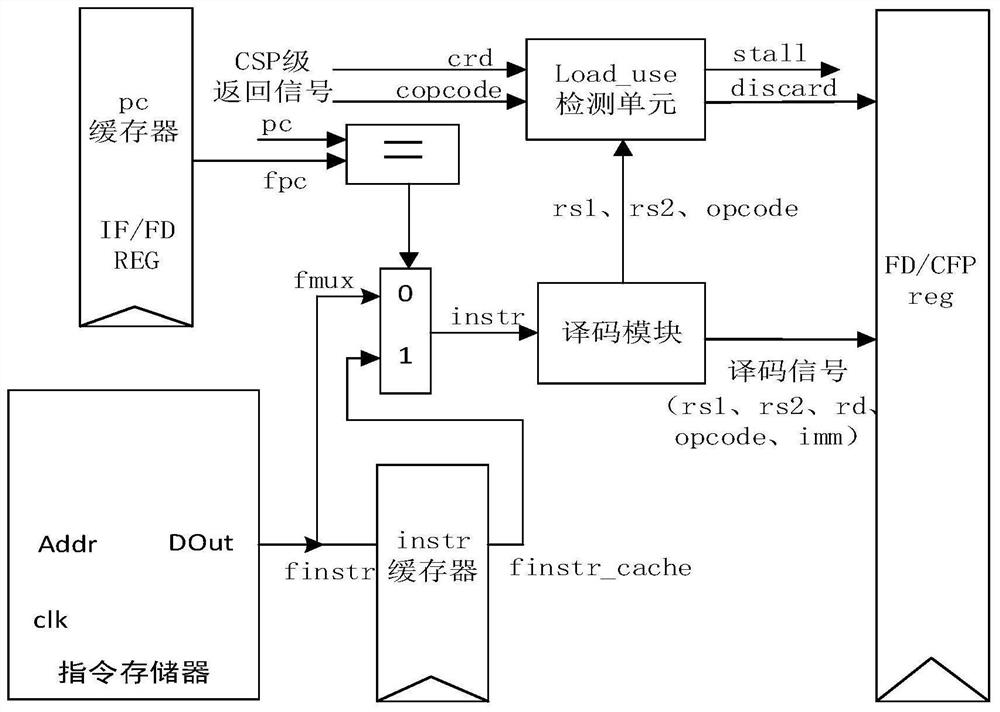
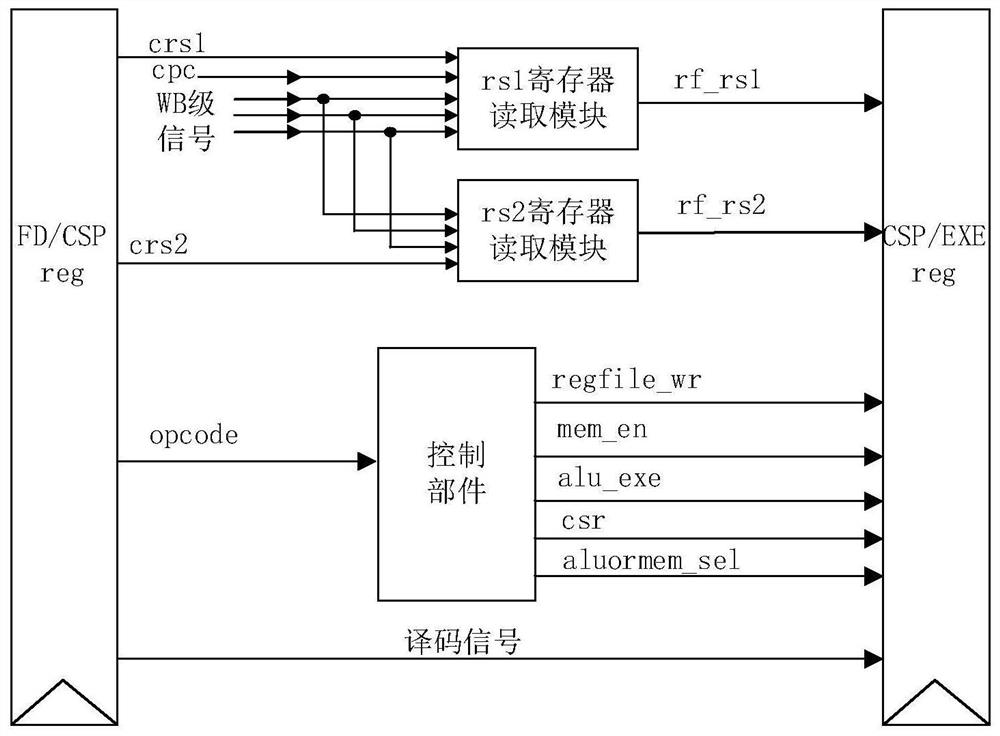
Six-level assembly line CPU based on RISC-V instruction set
PendingCN113986354AMeticulously dividedReduced execution timeDigital data processing detailsConcurrent instruction executionComputer architectureThe Internet
The invention discloses a six-level assembly line CPU based on an RISC-V instruction set. The CPU can realize an RV32I basic instruction set, a multiplication instruction and a CSR read-write instruction, and is provided with an interrupt register to suspend an assembly line; the CPU has the remarkable characteristics that the CPU has six levels of assembly line structures, namely an IF level, an FD level, a CSG level, an EXE level, an MEM level and a WB level, and has a higher dominant frequency; related circuits are designed for solving the risk problems in the assembly line; the data risk is solved by utilizing internal forward pushing, the load_use risk is solved by utilizing an assembly line pause method, and the control risk is solved by utilizing a static prediction method. The CPU has the characteristics of small area, low power consumption and multiple functions, and can be widely applied to the Internet of Things and embedded fields.
Owner:NANJING UNIV OF SCI & TECH
APT attack detection method based on event relation directed graph in network full traffic
ActiveCN113596037AEnhance correlation analysis abilityReduce the impactTransmissionHigh level techniquesDirected graphAttack
Owner:广州广电研究院有限公司
Grouping method and system based on core group mining and opinion leader identification results
ActiveCN109828998BPioneering taxonomyMeticulously dividedData processing applicationsSpecial data processing applicationsEngineeringNetwork model
The present invention provides a grouping method and system based on core group mining and opinion leader identification results, including: spreading network users into opinion leaders, de-intersecting core groups, and other users; constructing a layered spreading network model, with nodes of the above three categories In the user, the propagation behavior between users is used as the path between the corresponding nodes; the different comprehensive index values of the different propagation directions of the users in the middle layer and the bottom layer are obtained through the number of propagation behaviors, and the de-intersection core group-comprehensive index value table is constructed and other users-comprehensive index value table; opinion leaders are divided into credible opinion leaders and untrustworthy opinion leaders; users within the de-intersection core group and other users are divided according to the de-intersection core group-comprehensive index value table and other users-comprehensive The index value table is grouped. The above method and system make full use of the results of core group mining and opinion leader identification to implement user grading based on event participation.
Owner:COMMUNICATION UNIVERSITY OF CHINA
Network Security Communication System Based on Blockchain Smart Contract
ActiveCN114430350BImprove securityProtection securityUser identity/authority verificationNeural architecturesCommunications systemInformation transmission
Owner:南京智人云信息技术有限公司
A method for determining the associated co-occurrence pattern of moving objects
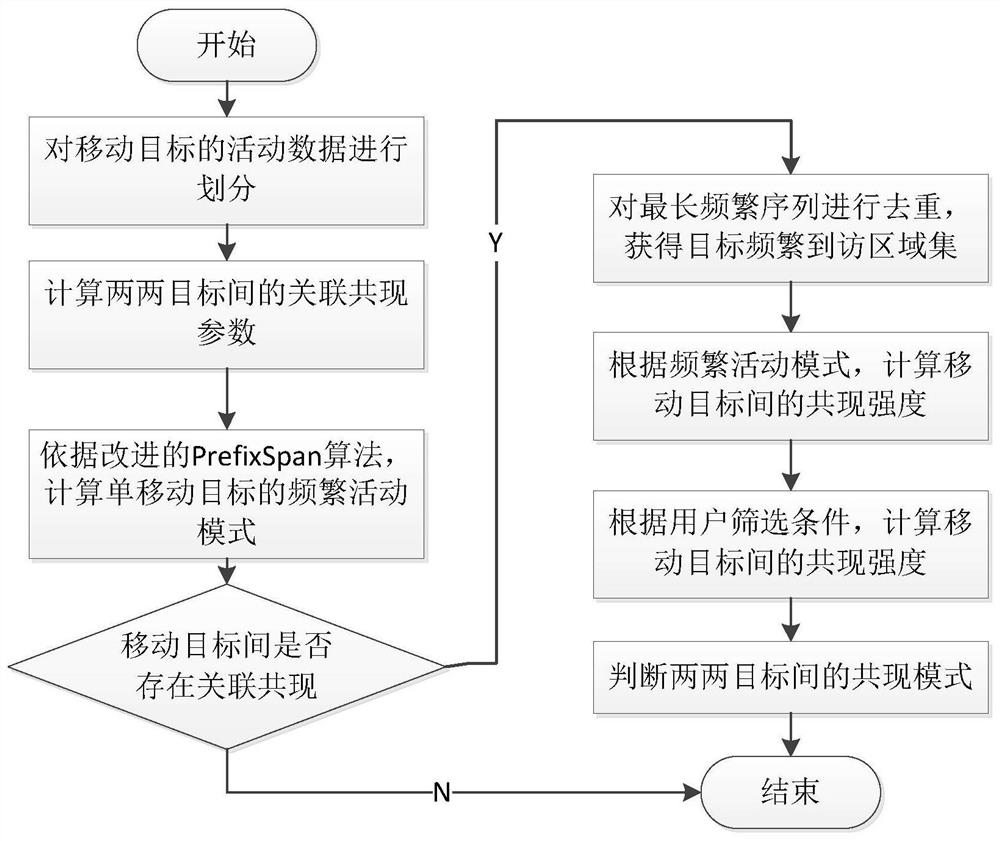
ActiveCN108170834BReduce complexityMeticulously dividedGeographical information databasesSpecial data processing applicationsComputational physicsComputer science
The present invention proposes a method for determining the associated co-occurrence pattern of a moving object, comprising the following steps: step 1, dividing the activity data of the moving object to obtain an activity data set; step 2, calculating the single moving object according to the improved PrefixSpan algorithm Frequent activity pattern; step 3, calculating the co-occurrence intensity between pairs of objects; step 4, determining the co-occurrence pattern between pairs of objects according to user screening conditions. The method for determining the correlation co-occurrence pattern of the moving target in the present invention provides a method for determining the correlation co-occurrence pattern that comprehensively considers the frequent pattern of the moving target itself and the co-occurrence intensity between targets, and the result has a higher credibility.
Owner:NANJING UNIV OF SCI & TECH
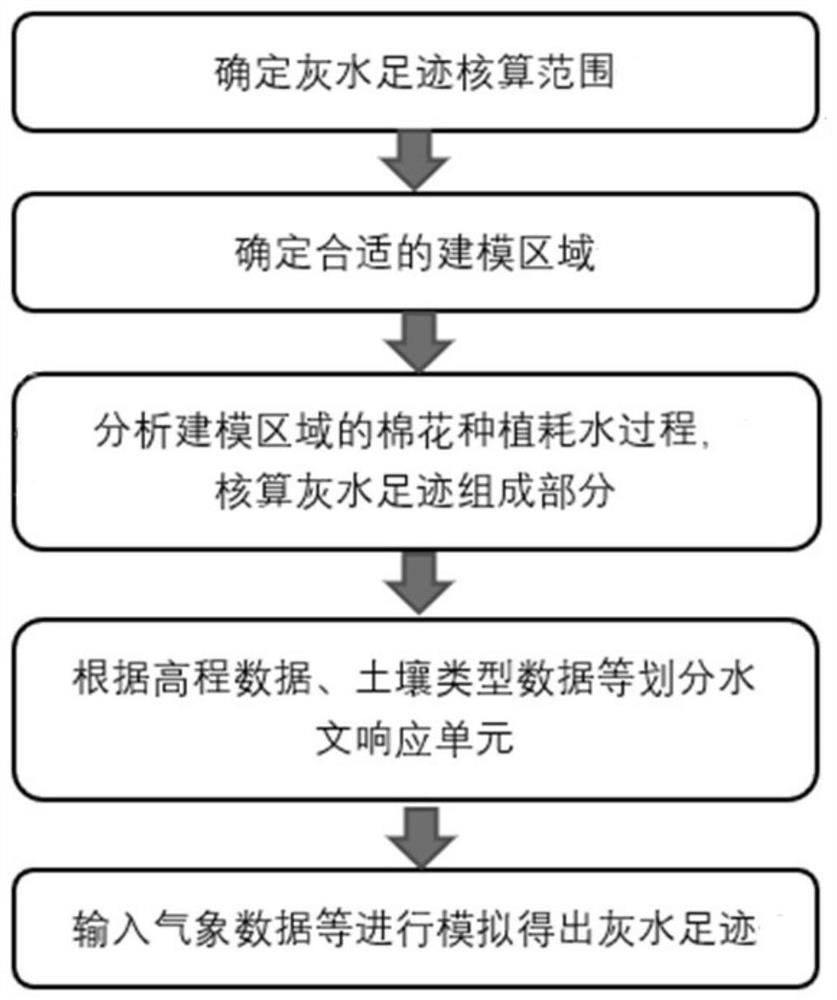
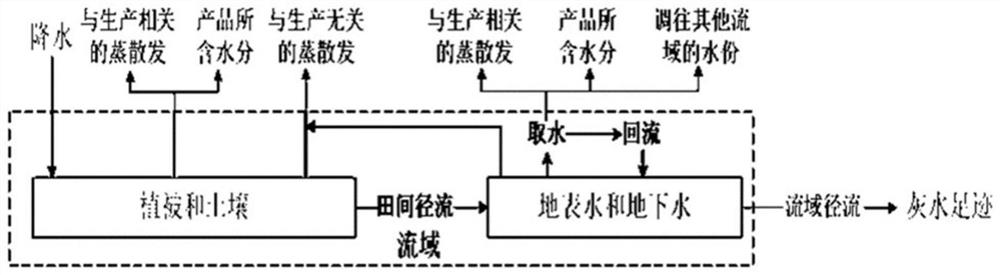
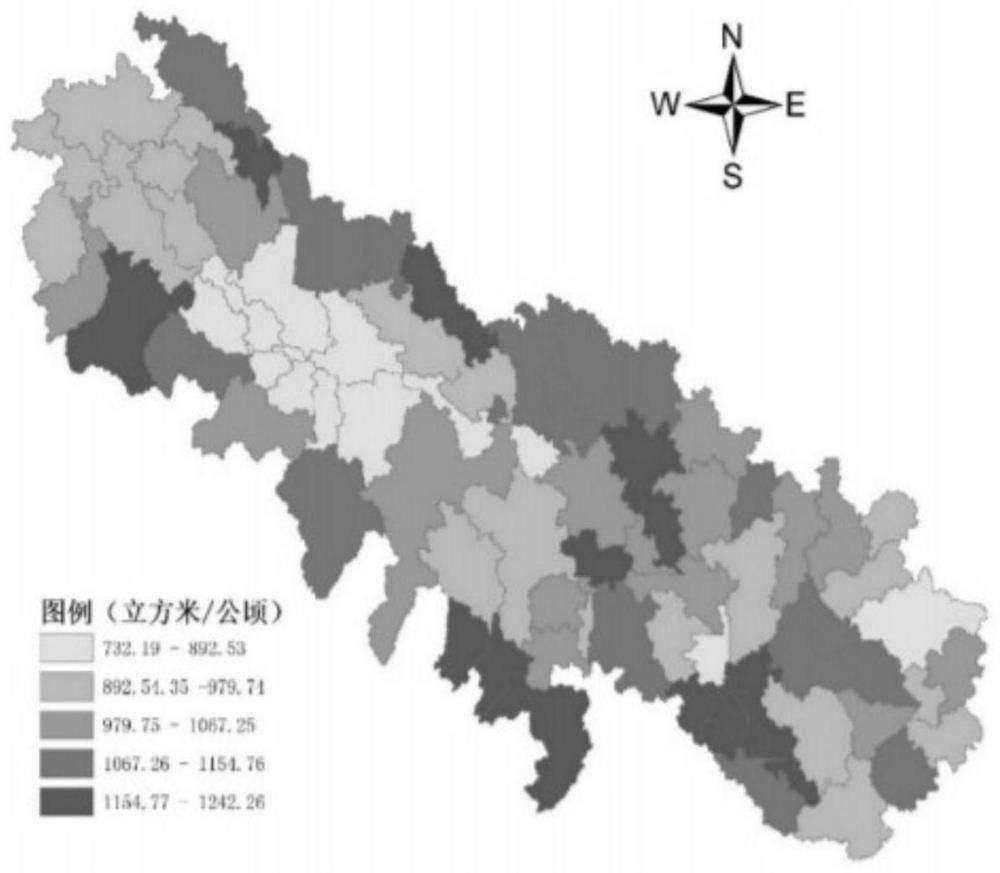
SWAT-based gray water footprint calculation method for cotton
InactiveCN113468744AMeticulously dividedImprove calculation accuracyDesign optimisation/simulationSpecial data processing applicationsSoil typeSoil science
The invention discloses an SWAT-based gray water footprint calculation method for cotton. The method comprises the following steps of: determining a grey water footprint accounting range of a to-be-studied area by looking up cotton planting distribution data in the to-be-studied area; determining a proper modeling area within the grey water footprint accounting range; analyzing the water consumption process of cotton planting in the modeling area, and accounting gray water footprint components; collecting elevation data, soil type data, land utilization data, local meteorological and hydrological data and farmland management operation data of the modeling area according to grey water footprint components, inputting the data into SWAT, and dividing a hydrological response unit; and inputting meteorological data, crop management operation and other attributes into the hydrological response unit, constructing a grey water footprint quantitative model of cotton in the to-be-studied area by utilizing SWAT, calibrating and simulating for one year, and calculating the grey water footprint of cotton in the to-be-studied area by taking different substances as indexes. According to the method, the accurate grey water footprint of cotton in the to-be-studied area can be obtained.
Owner:TIANJIN UNIV
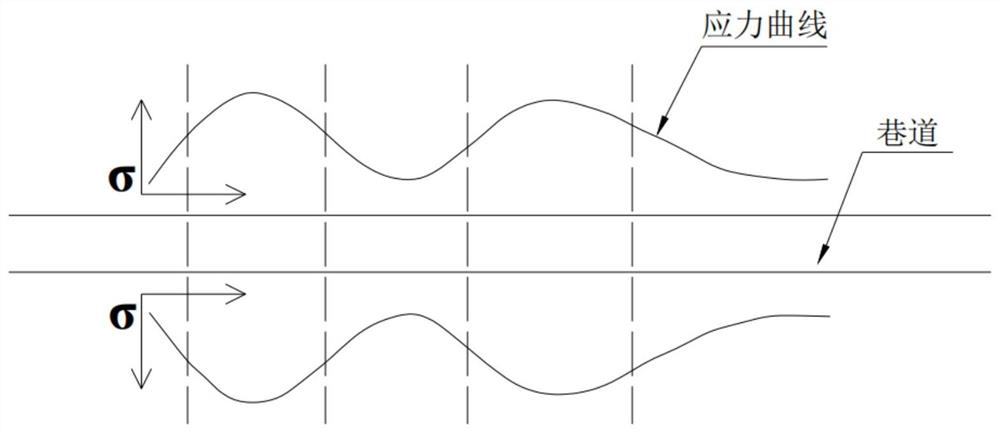
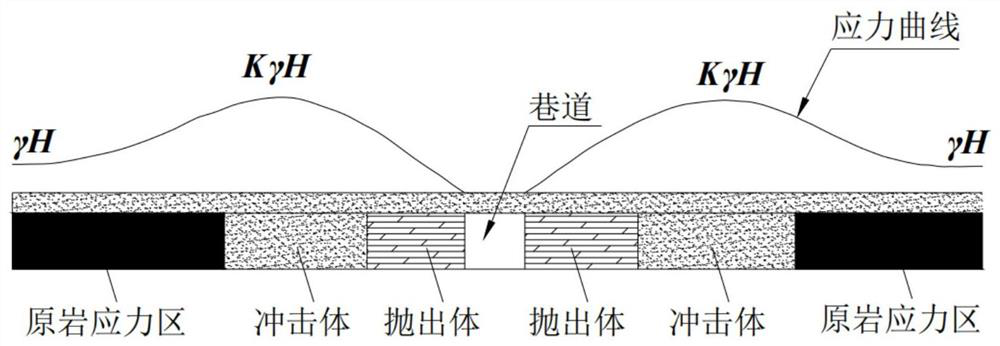
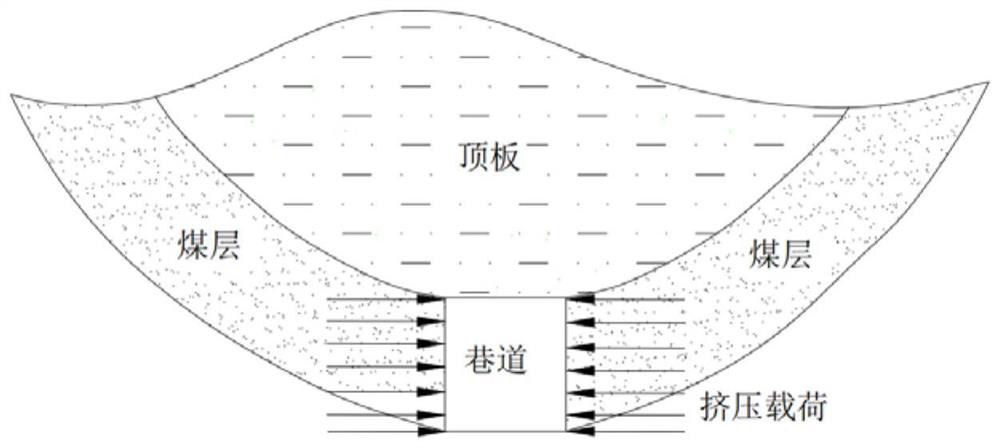
Roadway axial full-length impact risk evaluation and risk solving method based on momentum principle
ActiveCN113719318AEasy to implementHigh efficiency of crisis reliefMining devicesStructural engineeringControl theory
The invention provides a roadway axial full-length impact risk evaluation and risk solving method based on a momentum principle. The method comprises the following steps: selecting a detection point at the side part of a roadway; if the detection point is a special high-stress concentration area, judging that the detection point is a high-impact dangerous point; if the detection point is a general high stress concentration area, measuring the width of a throwing body at the detection point; and according to the negative correlation between the width of the throwing body and the impact danger, judging the danger level of the detection point. After the technical scheme is adopted, compared with the prior art, the method has the advantages that more detailed impact danger area division can be carried out in the whole axial direction of the roadway, the high-impact danger point can be accurately positioned, the roadway rock burst prevention and control problem is more focused and clear, the roadway rock burst prevention and control workload is greatly reduced, and the anti-impact cost is effectively reduced.
Owner:CHINA COAL RES INST +1
Reversible information hiding method and system based on image texture guide prediction
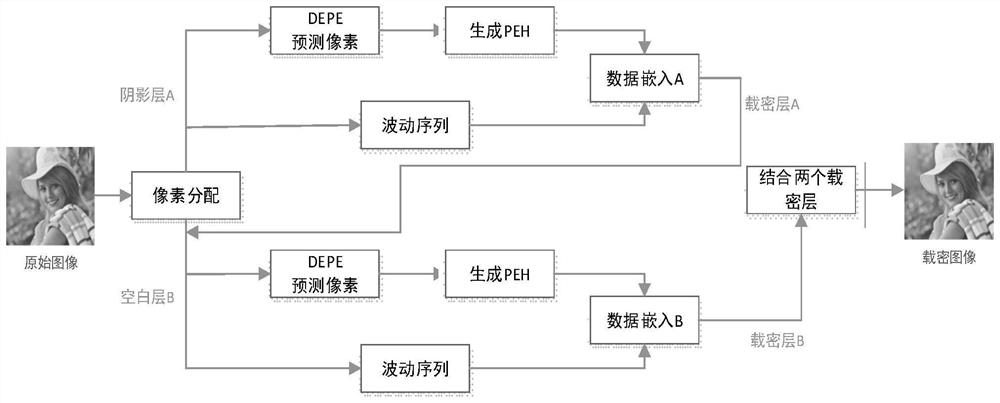
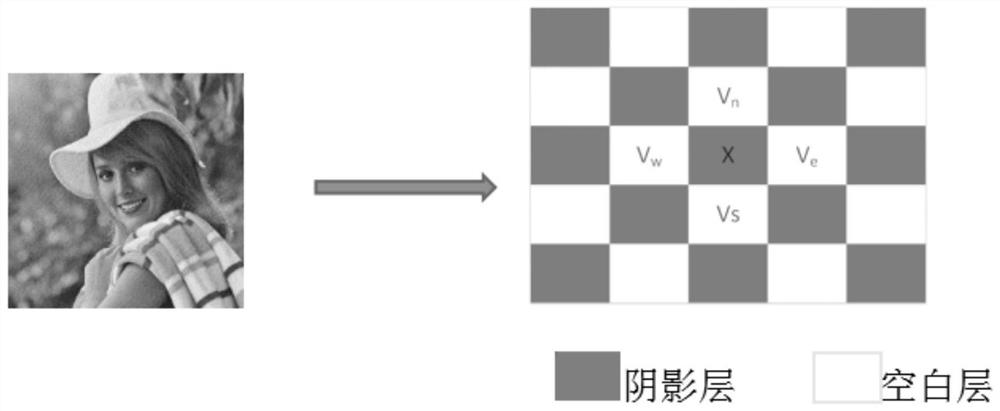
PendingCN114565499AThe predicted value is accurateEasy to embedImage analysisImage data processing detailsComputer graphics (images)Information hiding
The invention belongs to the technical field of reversible information hiding, and provides a reversible information hiding method and system based on image texture guide prediction. The method comprises the following steps: distributing image pixels according to a chessboard type pattern, and dividing the image pixels into a shadow layer and a blank layer; calculating prediction errors and fluctuation values of all pixels of the shadow layer, and constructing a prediction error histogram of the shadow layer; calculating prediction errors and fluctuation values of all pixels of the blank layer, and constructing a prediction error histogram of the blank layer; obtaining a dense shadow layer according to the prediction error histogram of the shadow layer and the fluctuation sequence of the shadow layer; obtaining a secret-carrying blank layer according to the prediction error histogram of the blank layer and the fluctuation sequence of the blank layer; and combining the secret-carrying layer shadow layer and the secret-carrying layer blank layer to obtain a secret-carrying image.
Owner:SHANDONG NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com