Method of selecting software files
A file and selected technology, applied in software engineering design, software maintenance/management, program code conversion, etc., can solve the problems of security-sensitive code hiding security-sensitive information, security-sensitive code confusion, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] As used hereinafter, unless expressly stated otherwise, the following terms have the following meanings. The term "metric" refers to a value representing the degree to which the inspected code satisfies some evaluation criteria.
[0047] The term "obfuscation" refers to the transformation of program code in order to hide the original intent of the code, for example by adding complexity. Obfuscation can be measured by computing a suitable metric for the code being obfuscated.
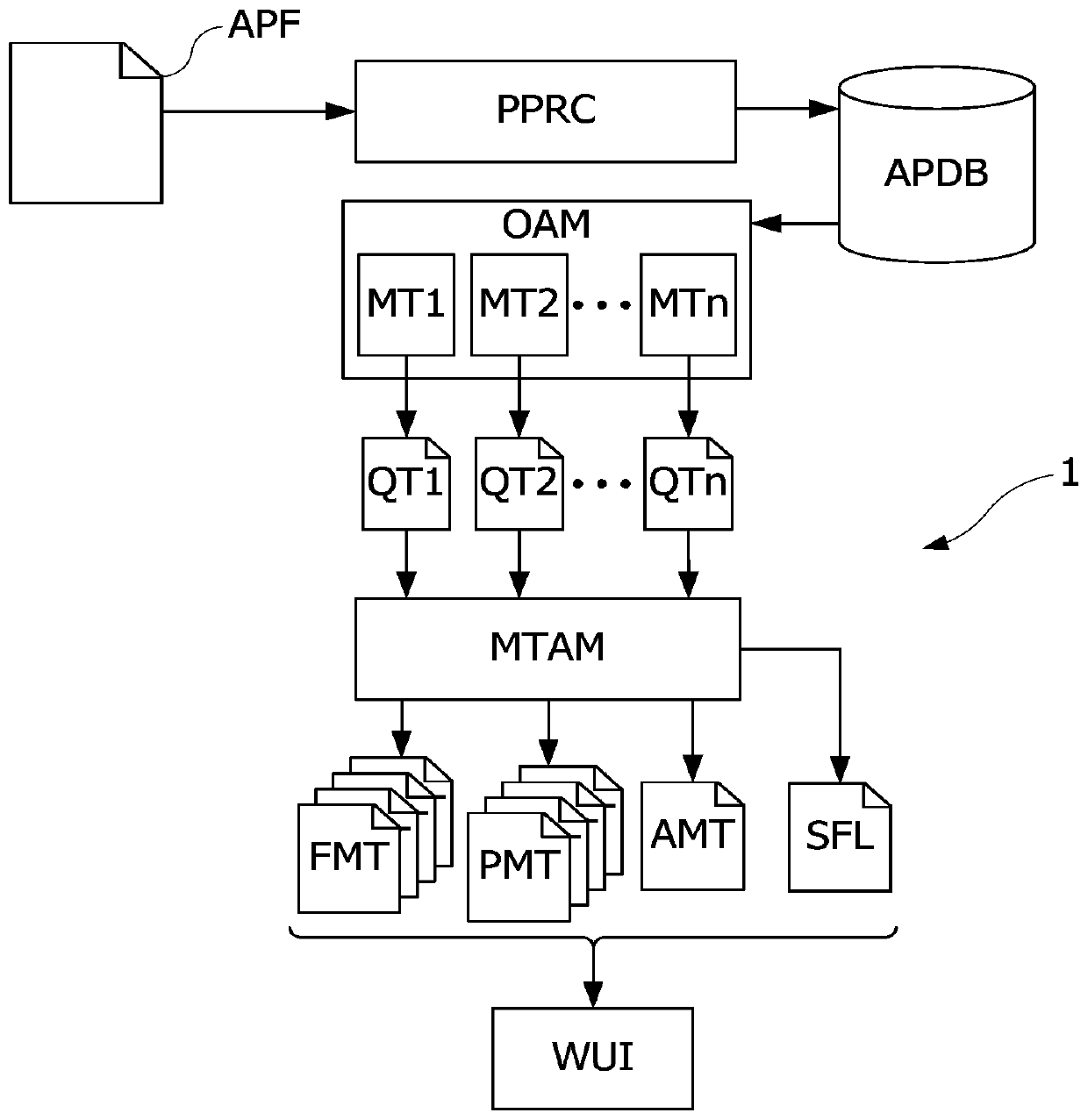
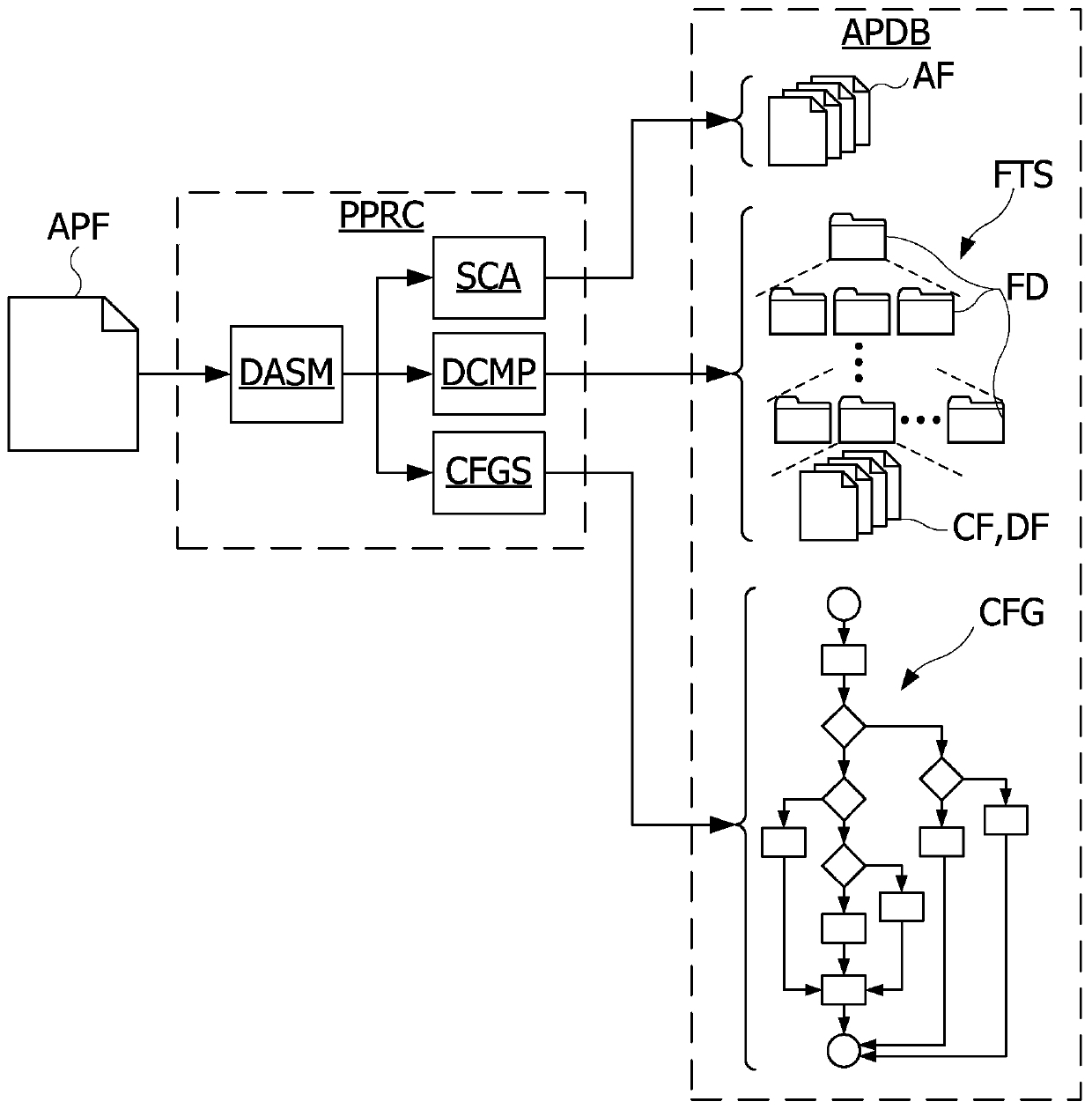
[0048] figure 1 A computer system 1 designed for analyzing software applications according to an embodiment is shown. The system 1 is configured to determine the degree of obfuscation of the software parts of the application and thus select and / or identify files with an insufficient degree of obfuscation with respect to the security sensitivity of the operation implemented by the respective software part. System 1 includes a preprocessing module PPRC, an obfuscation analysis module OAM and a me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com