Attack detection method and device for vehicle network, detector and storage medium
A vehicle network and attack detection technology, applied in the field of data security, can solve problems such as insufficient comprehensiveness, and achieve the effect of fast and convenient detection, direct and convenient detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
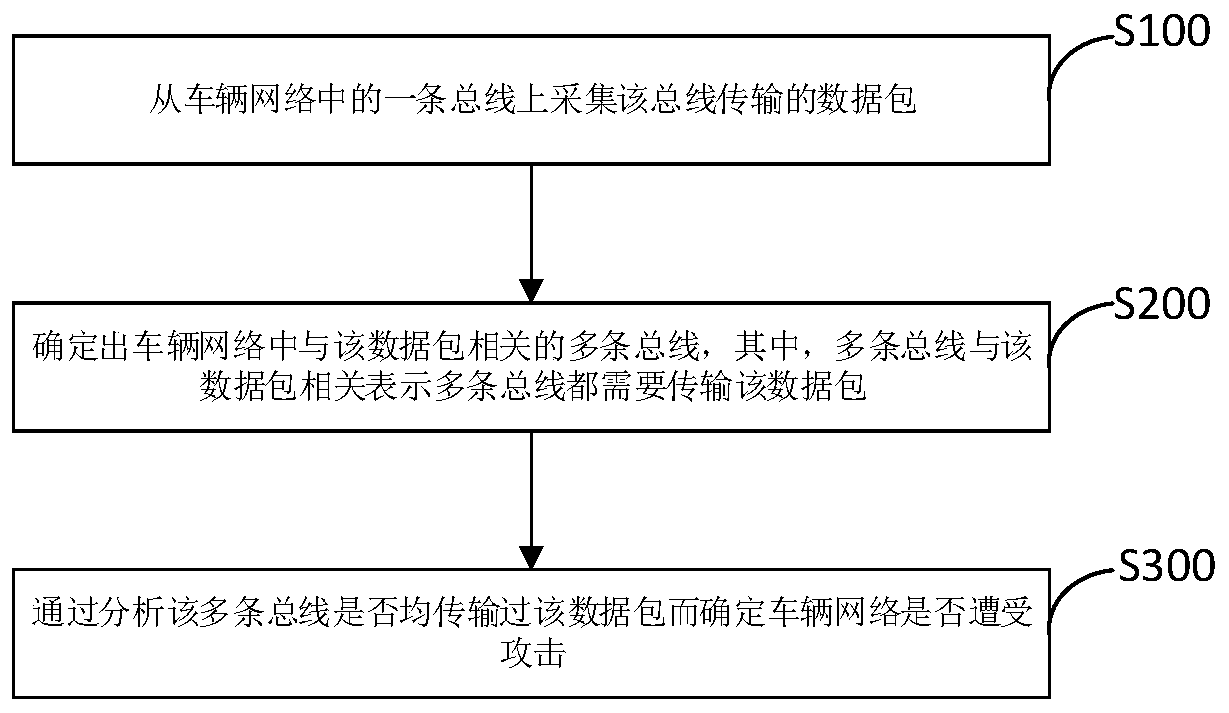
[0043] The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application.
[0044] In this embodiment, multiple buses of the vehicle can form a vehicle network, and the vehicle network can realize data interaction between various components of the vehicle itself, such as ECU (Electronic Control Unit, electronic control unit), MCU (MicrocontrollerUnit, micro control unit), etc. Alternatively, the vehicle network may be an external network in which the vehicle's communicator interacts with other vehicle's communicators or with the cloud.
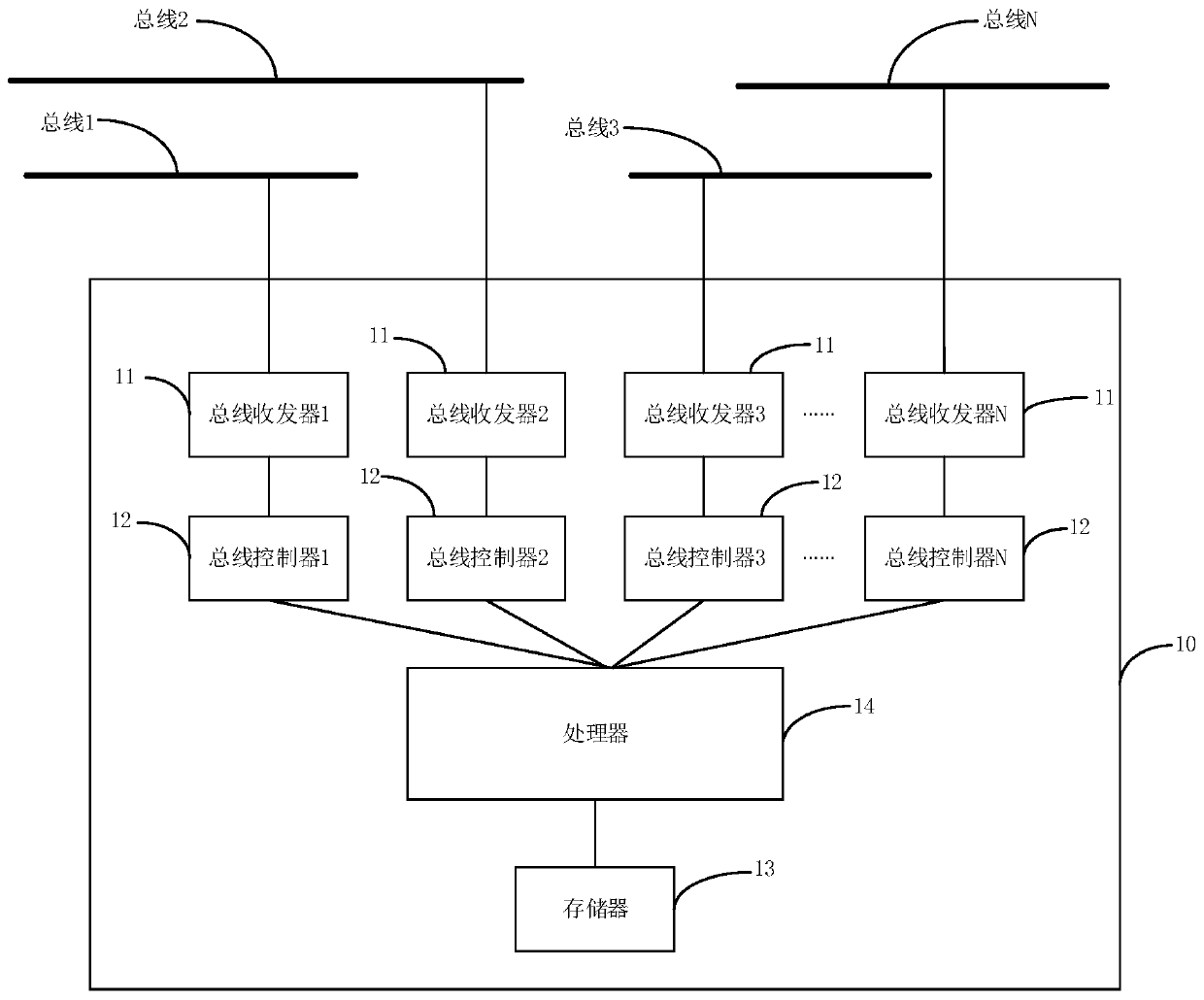
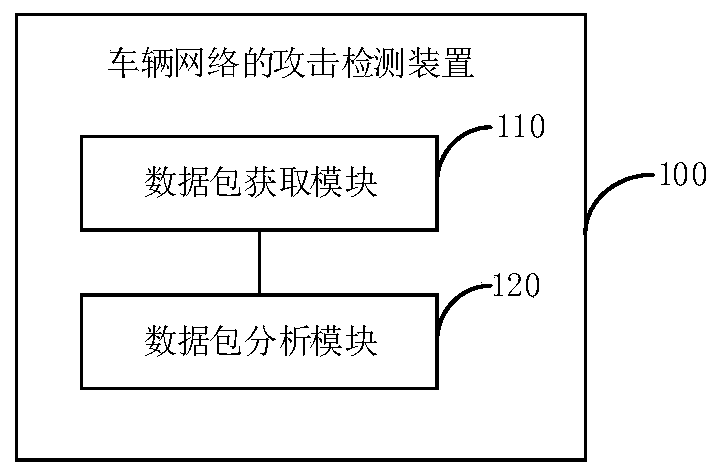
[0045] see figure 1 , the embodiment of the present application provides a detector 10, which can be deployed in the vehicle network of the vehicle, so as to detect whether the vehicle network is under attack to test.
[0046] Specifically, the detector 10 may include: a plurality of bus transceivers 11, a plurality of bus controllers 12 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com