Alarm method, device, equipment and storage medium
A technology of alarm level and alarm situation, applied in the network field, can solve the problem of large resource consumption of the cloud platform, achieve the effect of reducing the amount of data processing, reducing the amount of calculation, and improving timeliness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
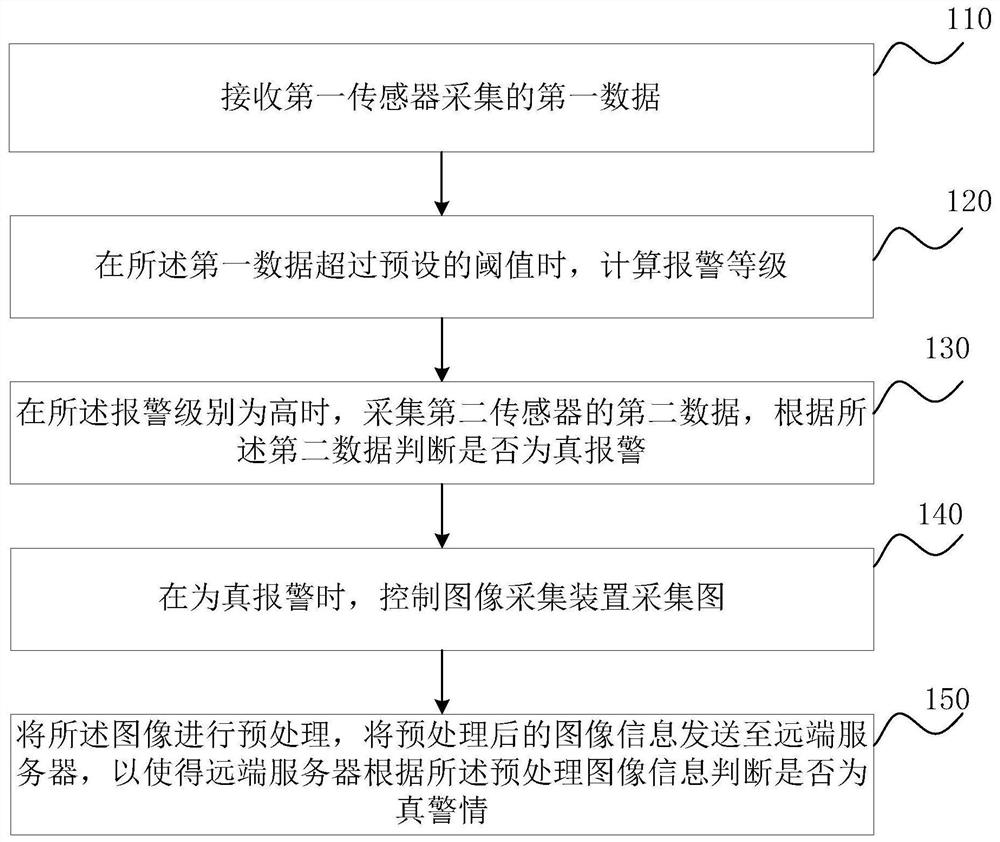
[0067] figure 1 It is a schematic flow chart of the alarm method provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of identifying and alarming complex scenes. This method can be executed by the alarm device and can be integrated in various sensors and image acquisition devices. In the terminal, the specific steps are as follows:
[0068] S110. Receive first data collected by a first sensor.
[0069] The alarm method provided in this embodiment can be applied to a variety of complex application scenarios, especially various scenarios that require a variety of detection data to cooperate with images to effectively identify whether to alarm or not. Wherein, the sensor may include: entity sensor data for measuring various physical quantities.
[0070] In this embodiment, the alarm method provided above can be applied to at least the following application scenarios:
[0071] For restricted areas, especially areas involving personal d...
Embodiment 2
[0096] figure 2 It is a schematic flowchart of the alarm method provided by Embodiment 2 of the present invention. This embodiment is optimized based on the above embodiments. In this embodiment, the image information is optimized as: image data and statistical analysis data; correspondingly, the preprocessed image is sent to the remote server , the specific optimization is: when a network failure occurs, the preprocessed image data is added with a priority identification bit, and when the network is restored, the data with the priority identification bit is sent preferentially.
[0097] Correspondingly, the alarm method provided in this embodiment specifically includes:
[0098] S210. Receive first data collected by a first sensor.
[0099] S220. When the first data exceeds a preset threshold, calculate an alarm level.
[0100] S230. When the alarm level is high, collect second data from a second sensor, and judge whether it is a true alarm according to the second data. ...
Embodiment 3
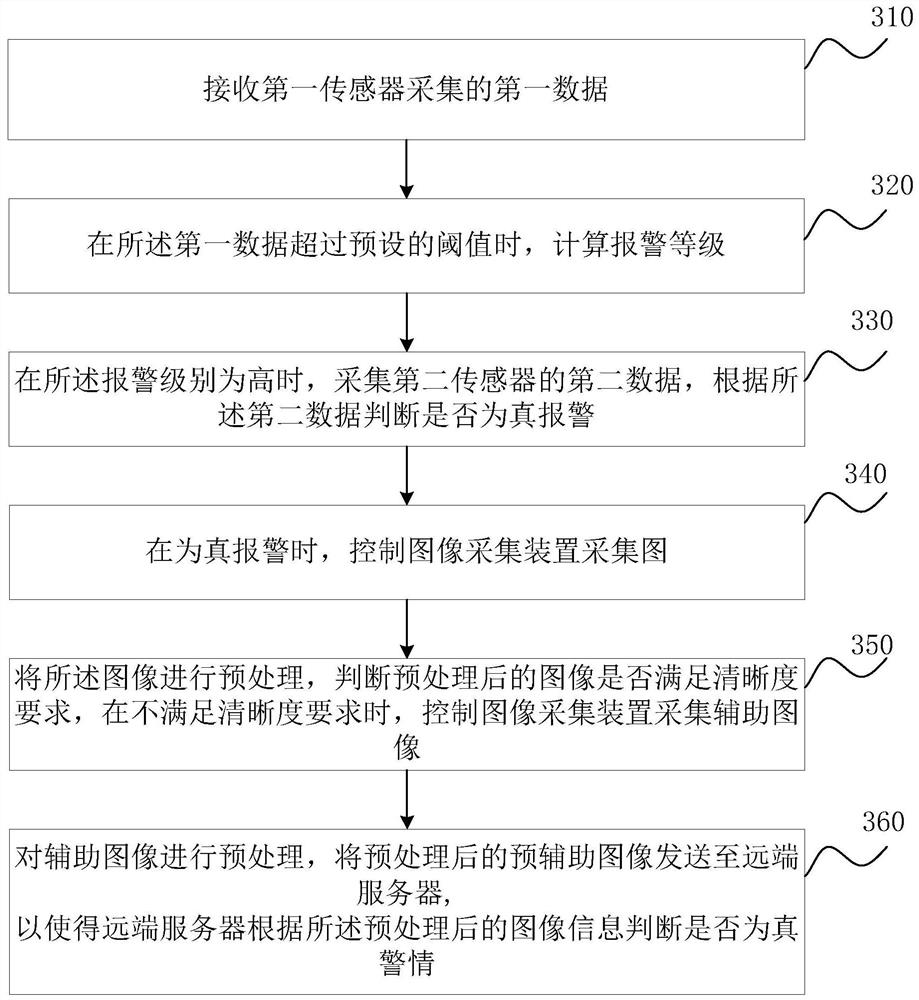
[0110] image 3 It is a schematic flowchart of the alarm method provided by Embodiment 3 of the present invention. This embodiment is optimized based on the above embodiments. In this embodiment, the preprocessed image information is sent to the remote server, and the specific optimization is as follows: determine whether the preprocessed image meets the definition requirement, When the definition requirement is not met, the image acquisition device is controlled again to collect auxiliary images; the auxiliary images are preprocessed, and the preprocessed images and auxiliary images are sent to the remote server.
[0111] Correspondingly, the alarm method provided in this embodiment specifically includes:
[0112] S310. Receive first data collected by a first sensor.
[0113] S320. When the first data exceeds a preset threshold, calculate an alarm level.
[0114] S330. When the alarm level is high, collect second data from a second sensor, and judge whether it is a true al...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com