SDN (self-defending network) anomaly detection and interception method and system
An anomaly detection and anomaly technology, applied in the field of network security, can solve the problems of high bandwidth consumption, large amount of data, data paralysis, etc., to reduce the amount of data processing and improve the detection rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
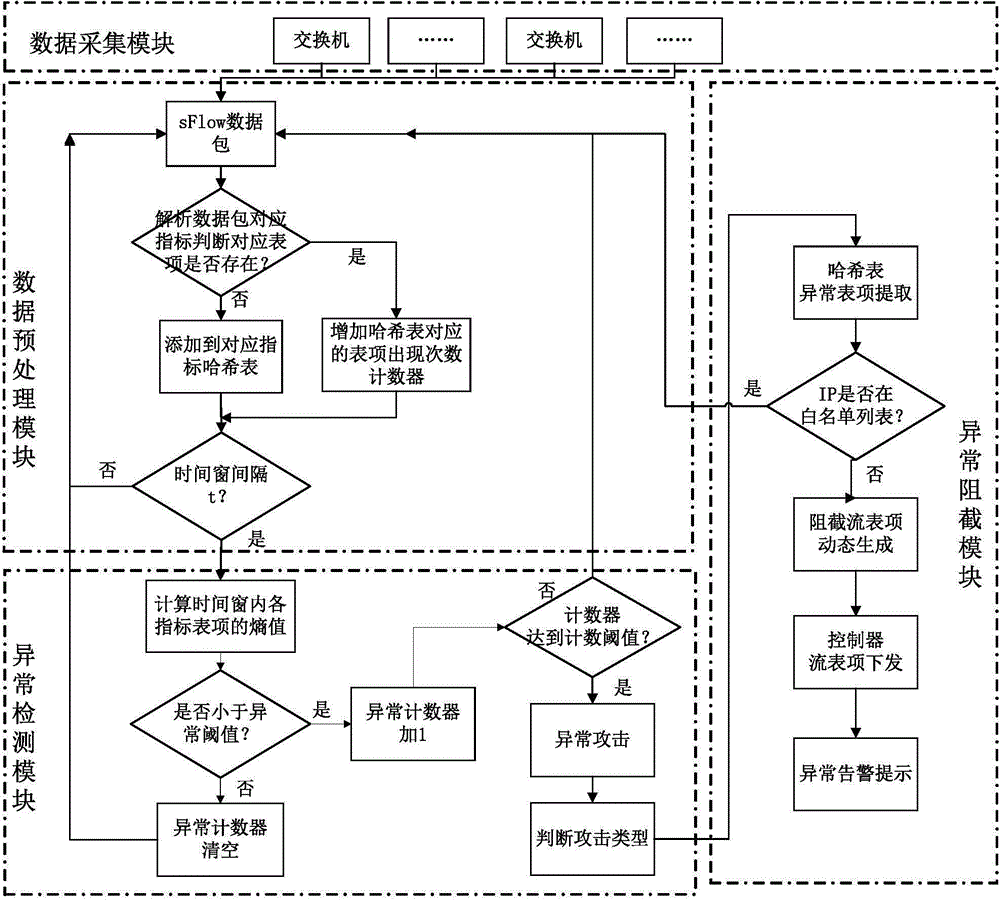
[0047] Such as figure 1 Shown, a kind of SDN anomaly detection and blocking method, described method is applied to SDN network, and described method comprises the following steps:
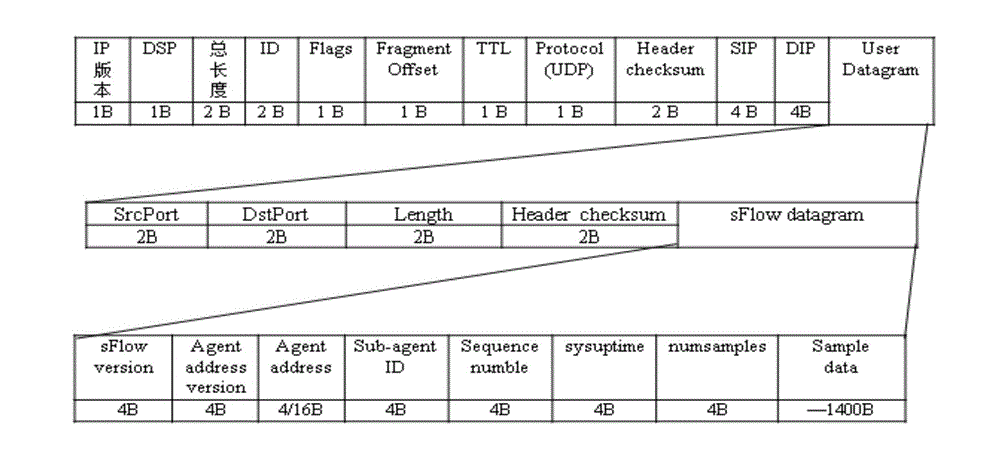
[0048] S1: Randomly sample the data flow at the port of the switch to obtain the sampled data packet;
[0049] S2: Take out the sample data in the sampling data packet, obtain multiple characteristic fields of the sample data, update the countable hash table corresponding to each characteristic field, and the value of the countable hash table is the specific value of each characteristic field in the current statistics the number of times the cycle has occurred;
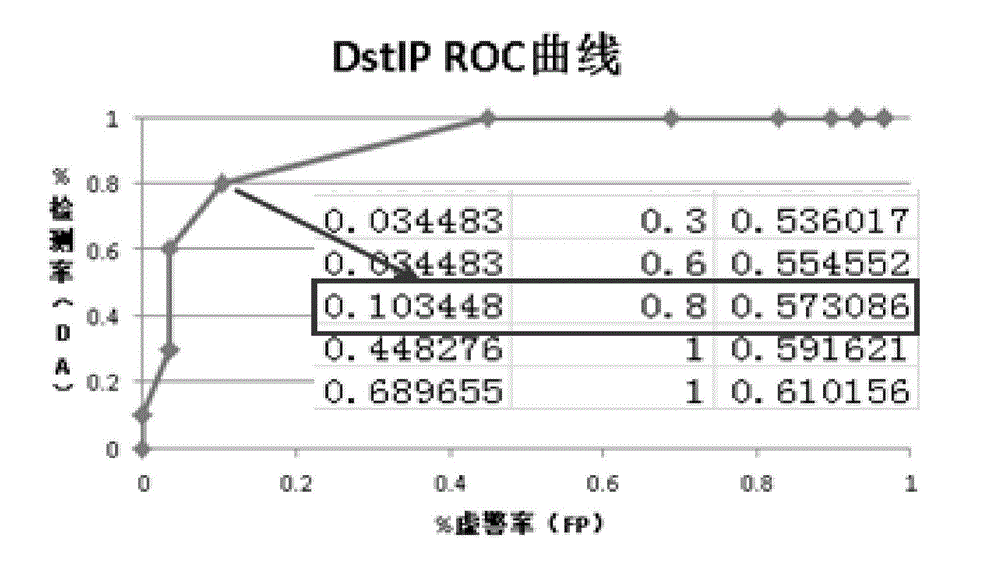
[0050] S3: At the interval of the preset time window, calculate the entropy value of the countable hash table corresponding to each feature field in the time window; if the entropy value is greater than or equal to the preset abnormal judgment threshold, clear the abnormal counter, otherwise abnormal The counter counts up by 1; if the va...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com