Authentication method for remote vehicle control
A technology of identity authentication and vehicle control, applied in the field of identity authentication of remote vehicle control, can solve problems such as denial of service attacks, data delays, etc., and achieve the effect of reliable identity authentication and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] In order to explain the content, structural characteristics, the purpose and effect of the realization of the invention in detail, the following combines the implementation method and the attachment is described in detail.
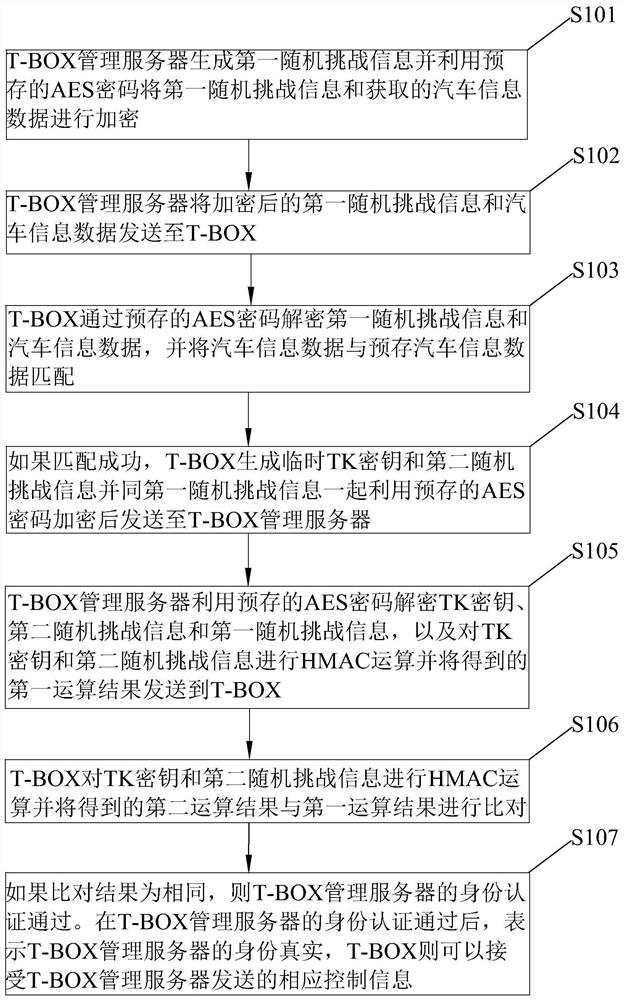
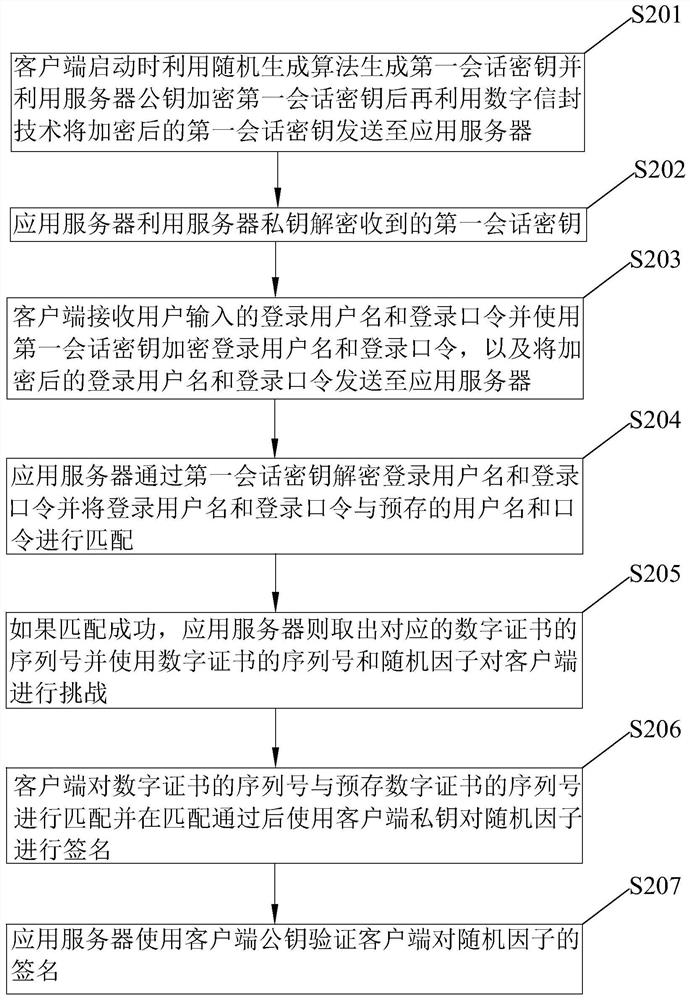
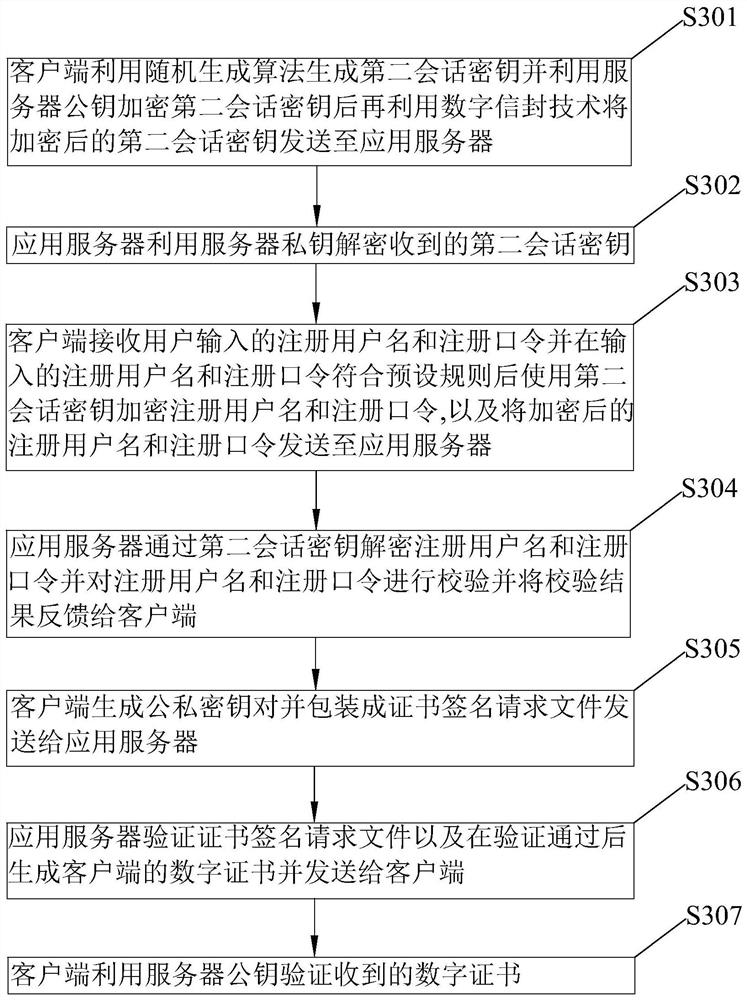
[0040] See figure 1 and Figure 4 The present invention disclose a method of identity authentication for remote vehicle control, including the following steps:
[0041] S101, T -BOX management server 60 generates the first random challenge information and uses the pre -stored AES password to encrypt the first random challenge information and the obtained car information data.
[0042] S102, T -BOX management server 60 sends the encrypted first random challenge information and car information data to T -BOX 70.
[0043] S103, T -BOX 70 Decryage the first random challenge information and car information data through the pre -stored AES password, and match the car information data with the pre -stored car information data.
[0044] S104, if the matching is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com