Embedded terminal software code vulnerability detection method and device based on model inspection
An embedded terminal and vulnerability detection technology, which is applied to computer security devices, instruments, electrical digital data processing, etc., can solve problems such as inability to apply embedded terminal software codes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
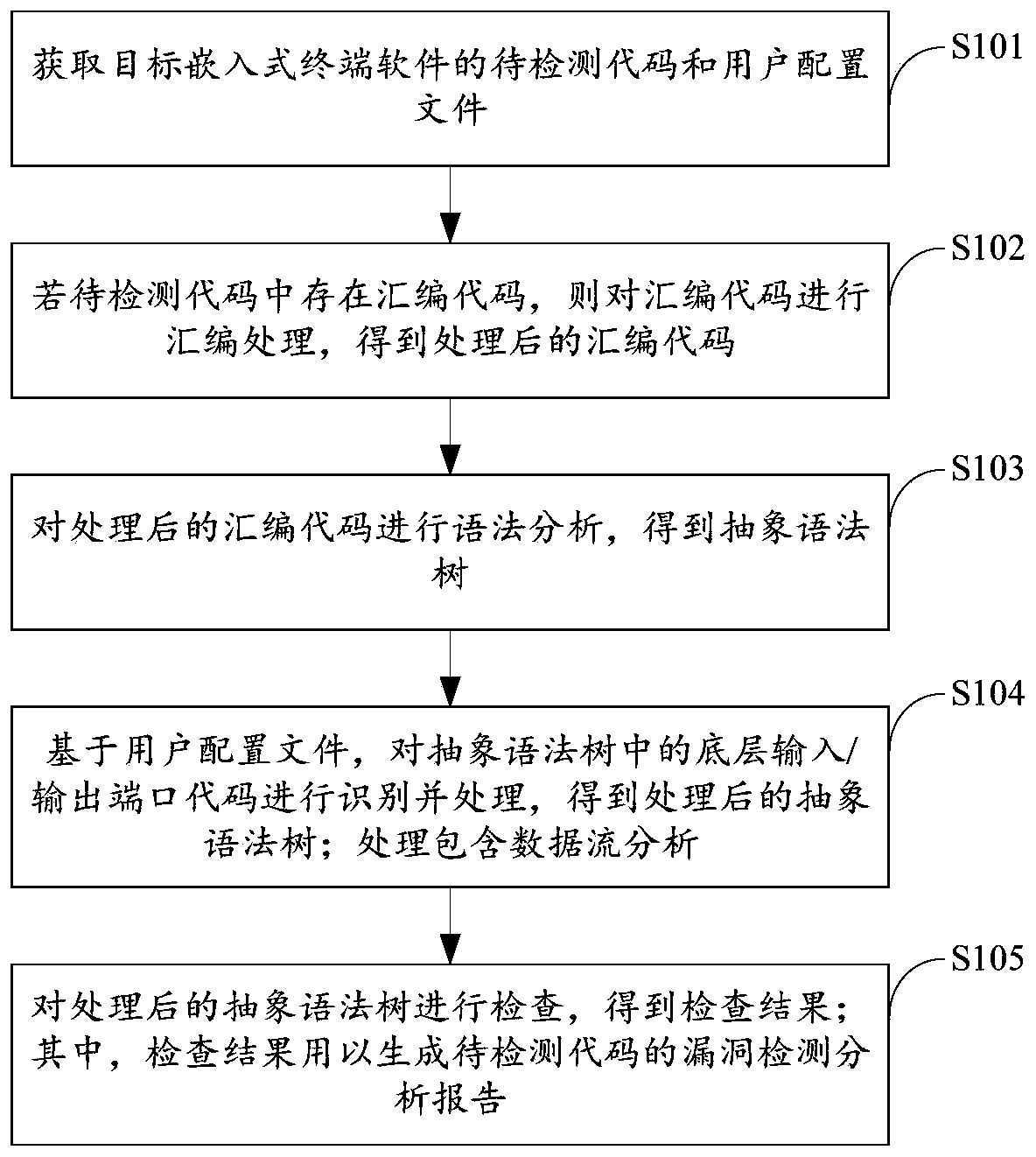
[0040] When the embodiment of the present invention carries out code analysis to the embedded terminal software, research and summarize two characteristics that the embedded terminal software is different from ordinary software: (1) there may be inline assembly code; (2) there may be Direct interaction of I / O. The embodiments of the present invention deal with the above-mentioned characteristics of embedded terminal software in a targeted manner, and the purpose is to provide a vulnerability detection method suitable for embedded terminals. It should be noted that the steps shown in the flowcharts of the accompanying drawings may be performed in a computer system, such as a set of computer-executable instructions, and that although a logical order is shown in the flowcharts, in some cases, The steps shown or described may be performed in an order different than here.
[0041] figure 1 It is a flow chart of a method for detecting vulnerabilities in embedded terminal software ...
Embodiment 2
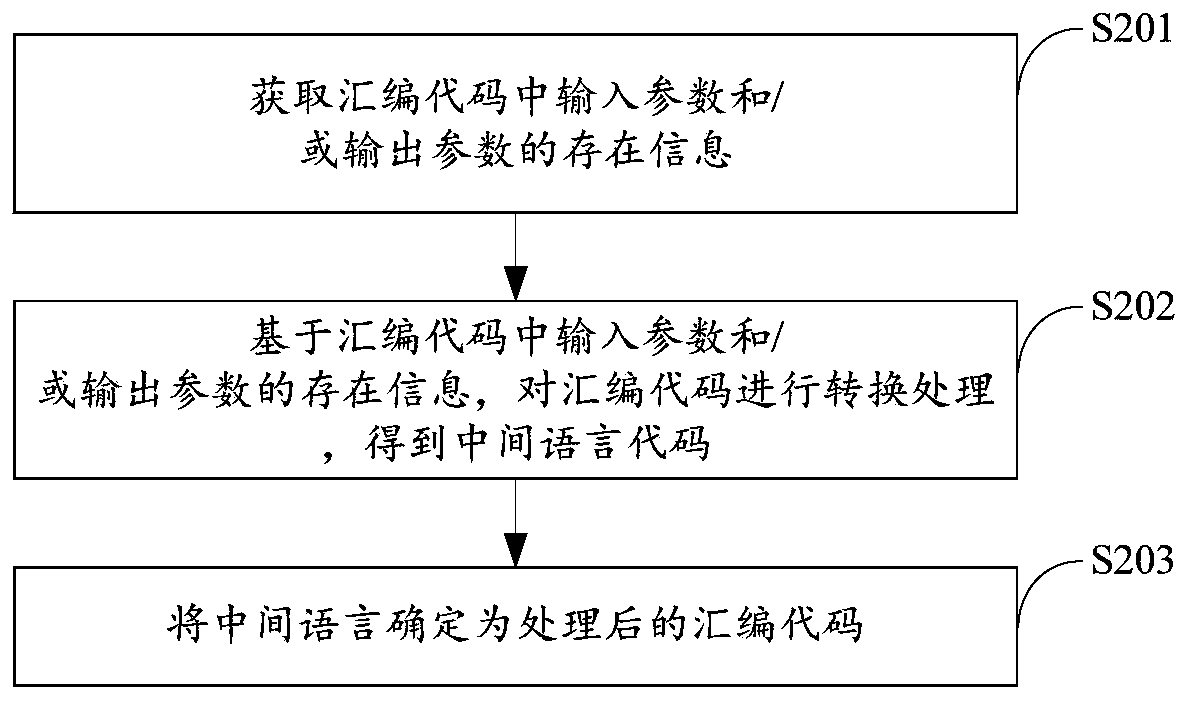
[0082] The above embodiments can realize the vulnerability detection of embedded terminal software codes. However, the embodiment of the present invention is a detailed description of the above-mentioned embodiments. In this embodiment, the flowchart of the embedded terminal software code vulnerability detection method based on model checking can also be as follows Figure 4 As shown, it mainly includes the static analysis module and the model checking module, and according to the two characteristics of the embedded terminal of the power grid, the traditional static analysis method and the model checking method are improved, and the inline assembly processing module and the underlying I / O processing module, the above two modules designed can make it process the code to be detected including inline assembly code and underlying I / O interaction in the grid embedded terminal software code.
[0083] Specifically, such as Figure 5 As shown, the embodiment of the present inventio...
Embodiment 3
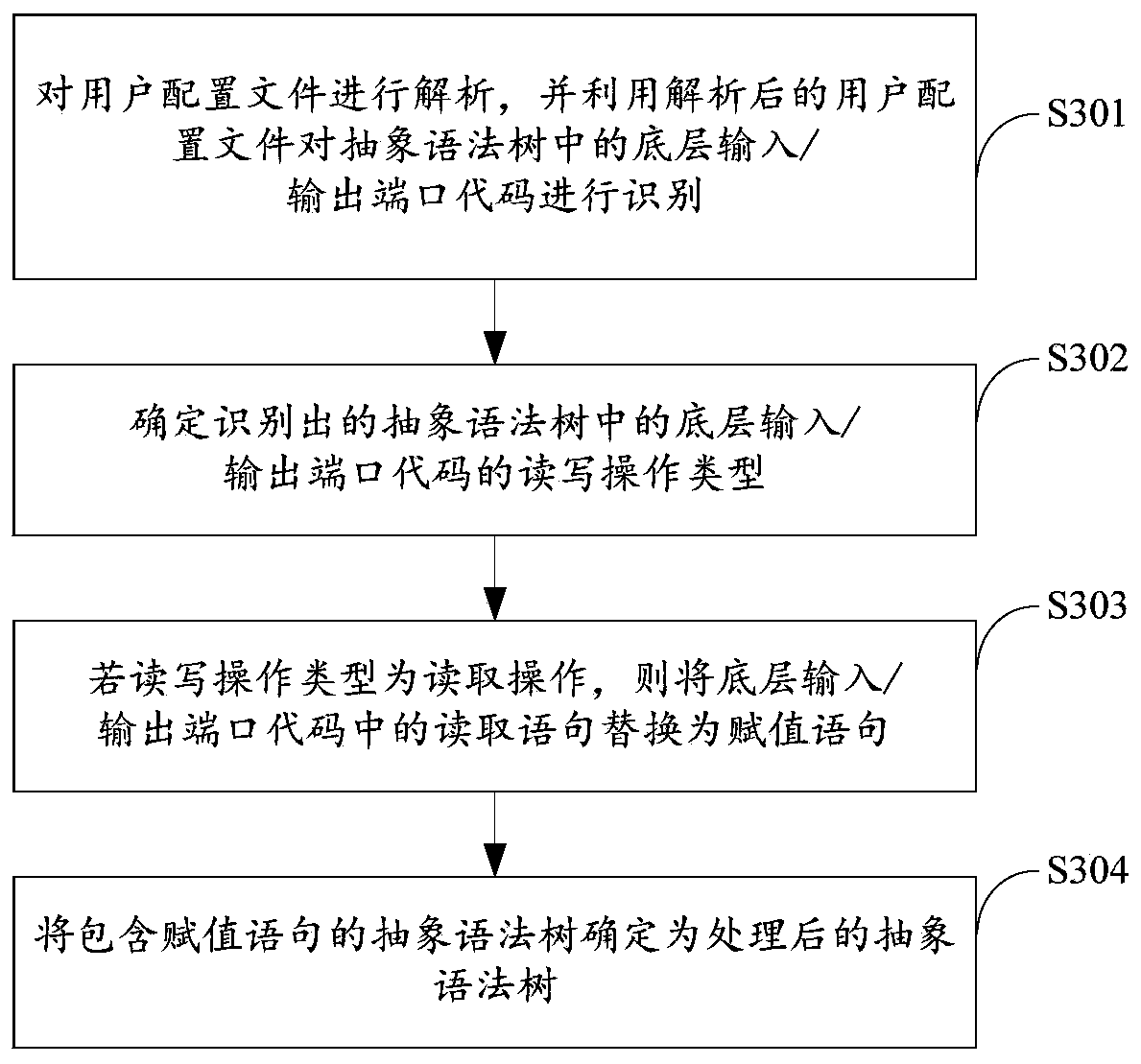
[0102] The above two embodiments can realize the vulnerability detection of the embedded terminal software code. However, the embodiment of the present invention is a detailed description of a method for detecting vulnerabilities in embedded terminal software codes. Figure 11 It is a flow chart of another model-checking-based embedded terminal software code vulnerability detection method provided by the embodiment of the present invention. The specific steps of the model-based embedded terminal software code vulnerability detection method are as follows:
[0103] Step 1, input the code to be detected, and set the user configuration file;
[0104] Step 2, preprocessing the code to be detected is mainly to remove redundant line breaks, tabs and comments in the code, and process header files, macro definitions and conditional compilation;
[0105] Step 3, use the static analysis module to statically analyze the preprocessed code to be detected and establish an AST model, the sp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com