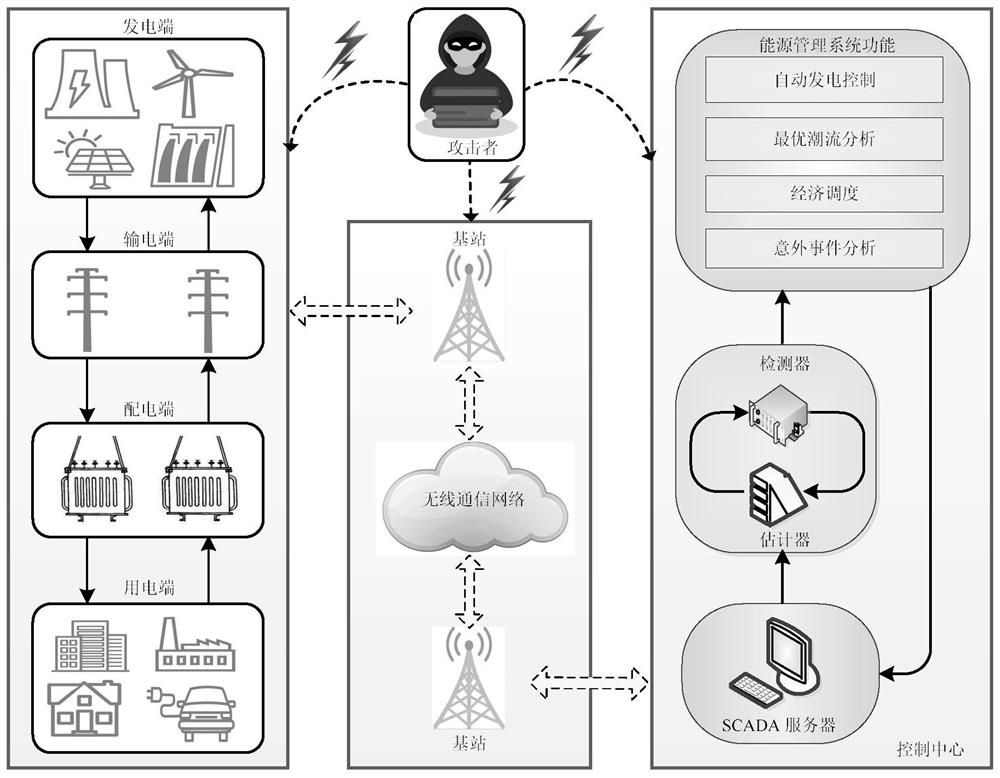
Patents
Literature
51 results about "Smart grid security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
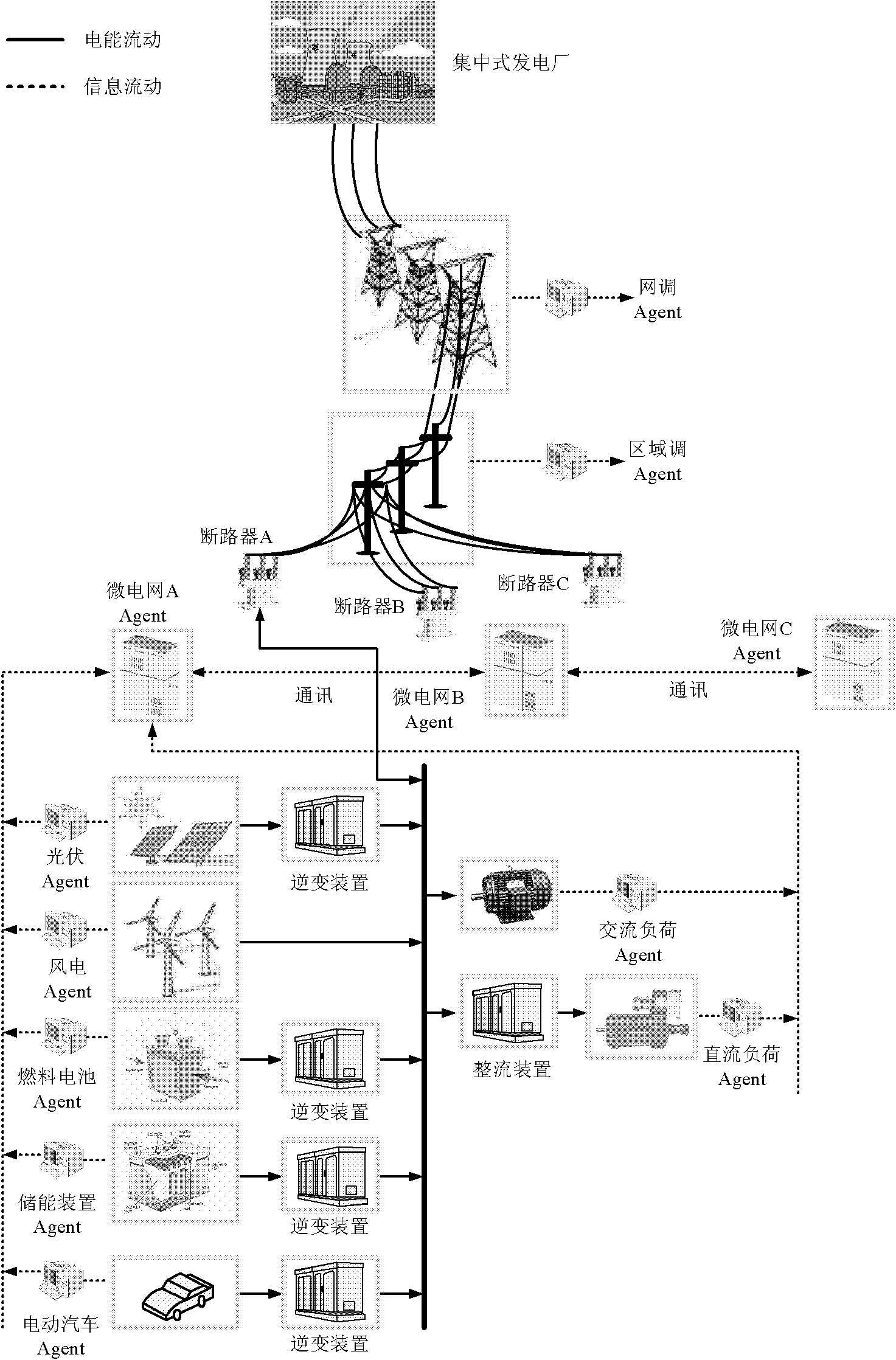
Multi-agent optimized coordination control method of electric network
InactiveCN101777769ARealize intelligent unmanned schedulingGuaranteed economic dispatchAc networks with different sources same frequencyMicrogridPower grid
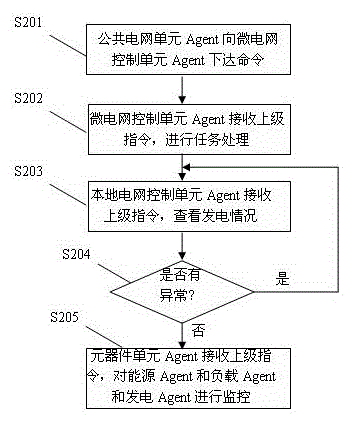
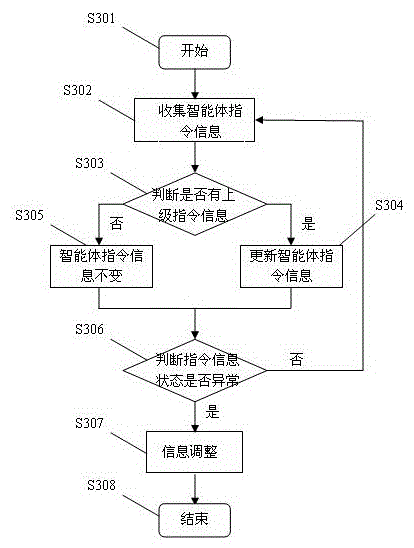
The invention relates to a multi-agent optimized coordination control method of an electric network in the technical field of electric networks, which comprises the following steps of: collecting local electric information, transmitting the local electric information to a central agent of a microgrid and issuing a control command by a local electric network to the central agent of the microgrid simultaneously; computing by a grid technology; issuing a new control command by the central agent of the microgrid and transmitting the information to a regulation agent of the local electric network by a network line simultaneously; receiving a dispatching instruction of the central agent of the microgrid by the agent of each element and carrying out logical judgment on a result executing these dispatching commands according to the collected local electric information; and meanwhile, optimizing the electric network within a control range by the regulation agent of the local electric network and controlling a computer to carry out parallel computation by the grid technology. The invention is suitable for carrying out optimal dispatching on a distributed energy resource of an intelligent electric network, can control each power supply by an optimization scheme, also enhances the operational processing time greatly and ensures that the intelligent electric network runs safely, stably and economically.
Owner:SHANGHAI JIAO TONG UNIV
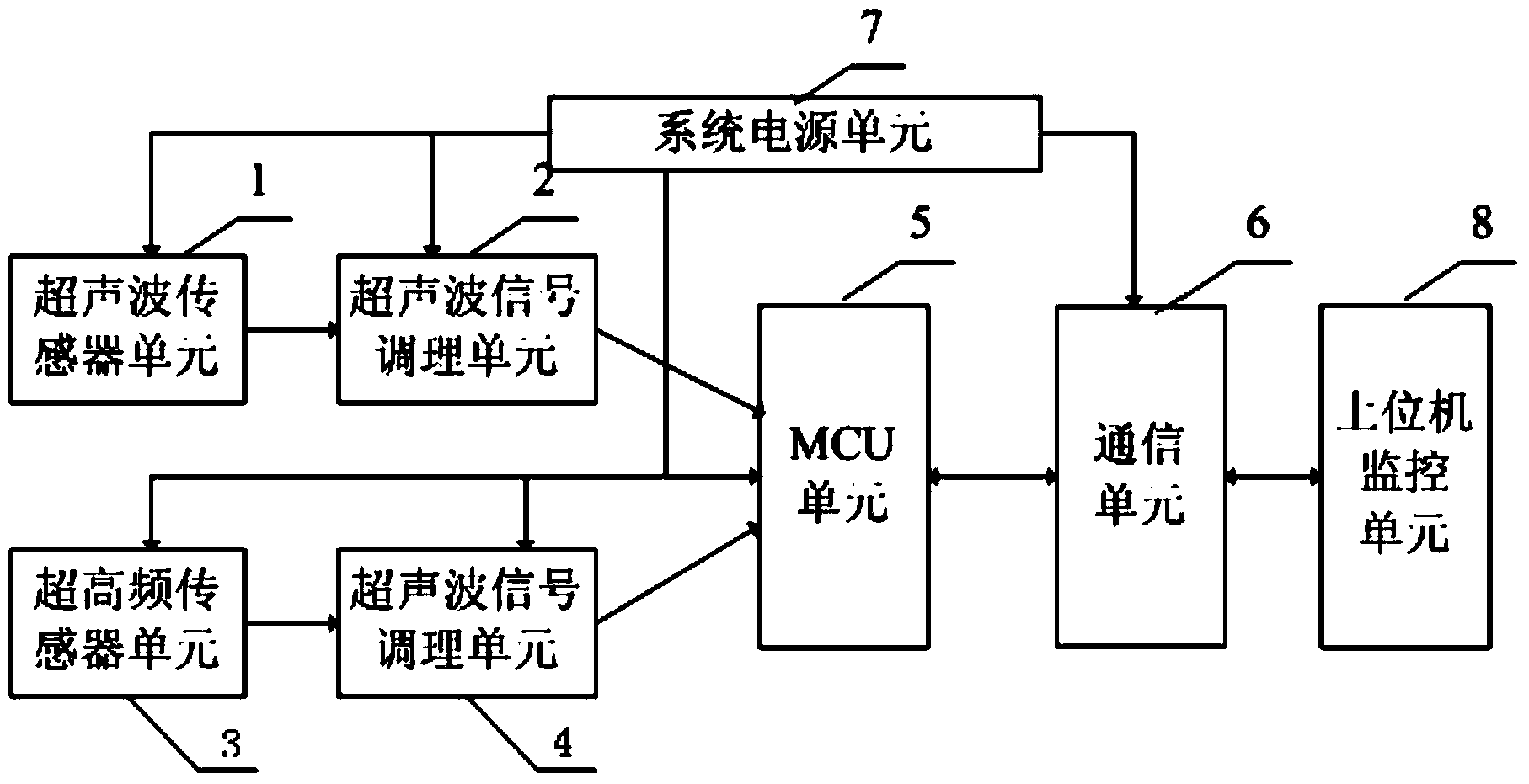
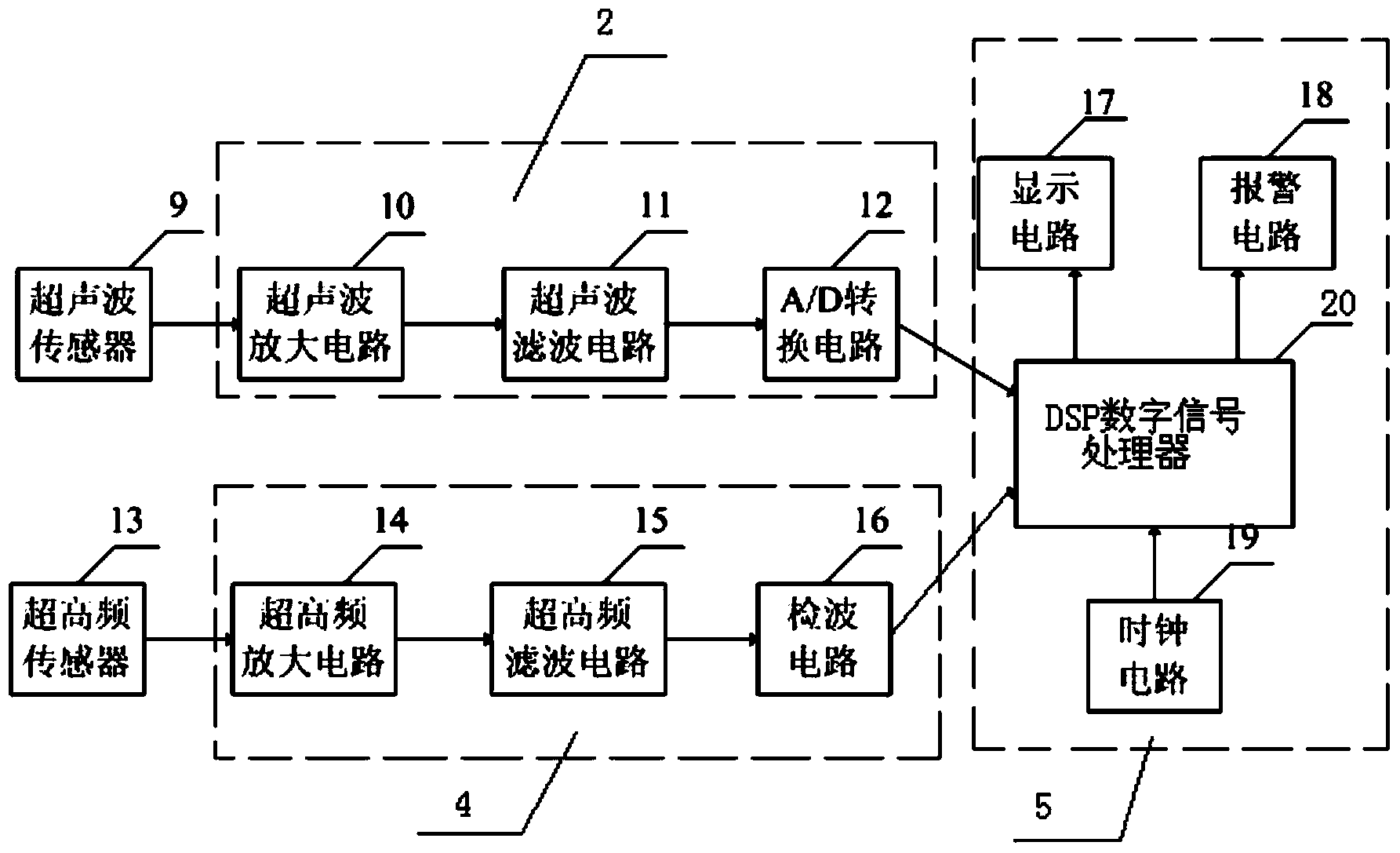
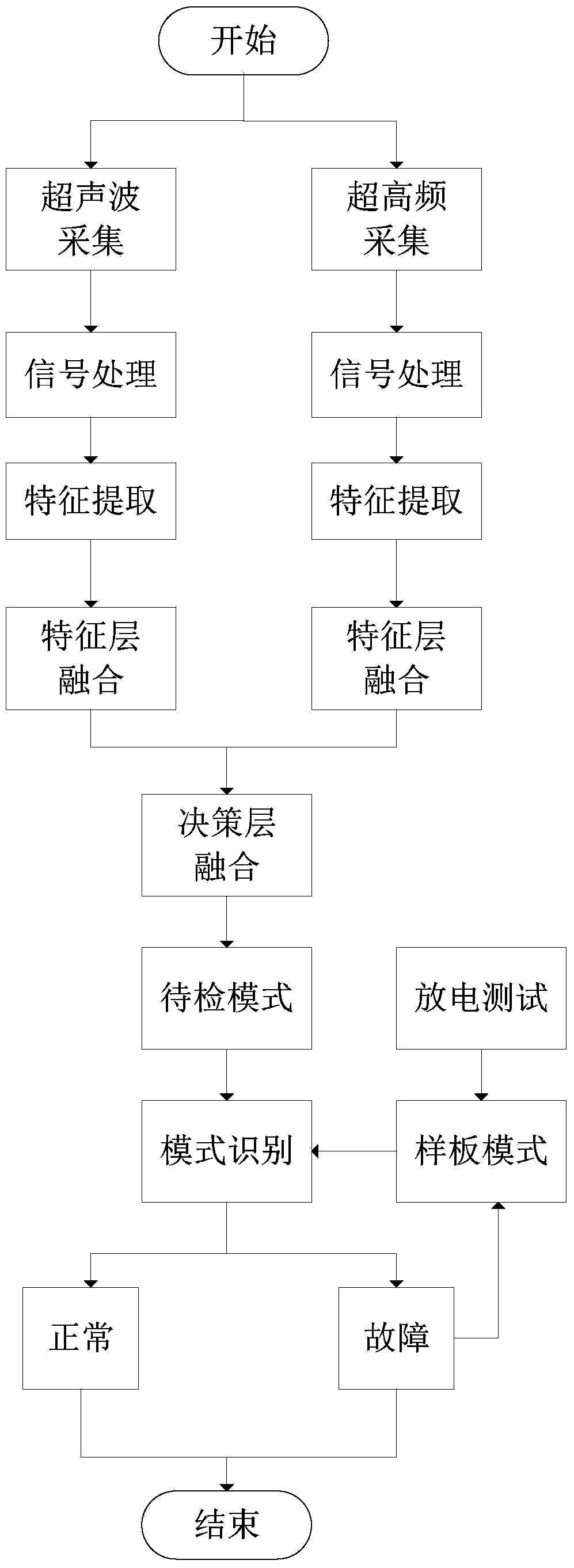
Partial discharge detecting system and method for high voltage switch cabinet
InactiveCN103454564AAvoid the disadvantages of narrow detection range, which is not conducive to the analysis of discharge informationTesting dielectric strengthEngineeringUltrahigh frequency
The invention discloses a partial discharge detecting system and method for a high voltage switch cabinet, and on-line monitoring is conducted on the intelligent high voltage switch cabinet through an acoustoelectric joint on-line monitoring system based on the information fusion technology by joint adoption of an ultrasonic monitoring method and an ultrahigh frequency monitoring method. According to the partial discharge detecting system and method for the high voltage switch cabinet, the advantages of the ultrasonic monitoring method and the ultrahigh frequency monitoring method are integrated, information fusion of a characteristic layer and a strategy layer is conducted on a discharge signal obtained through the information fusion technology, and fault diagnosis is conducted on the fused discharge information. Insulation faults and discharge situations in the intelligent high voltage switch cabinet are found in time through on-line monitoring, so that safe operation of an intelligent power grid is ensured. The partial discharge detecting system and method for the high voltage switch cabinet solve the problems in the prior art that the ultrasonic detecting range is narrow and is not favorable for analysis of the discharge information, a detecting device cannot display the discharge information on site and is not favorable for overhaul and maintenance of the working personnel, and the detecting device does not have the fault signal mode identifying function and cannot judge the situation that an interference signal causes a false alarm.
Owner:JIANGSU UNIV OF SCI & TECH
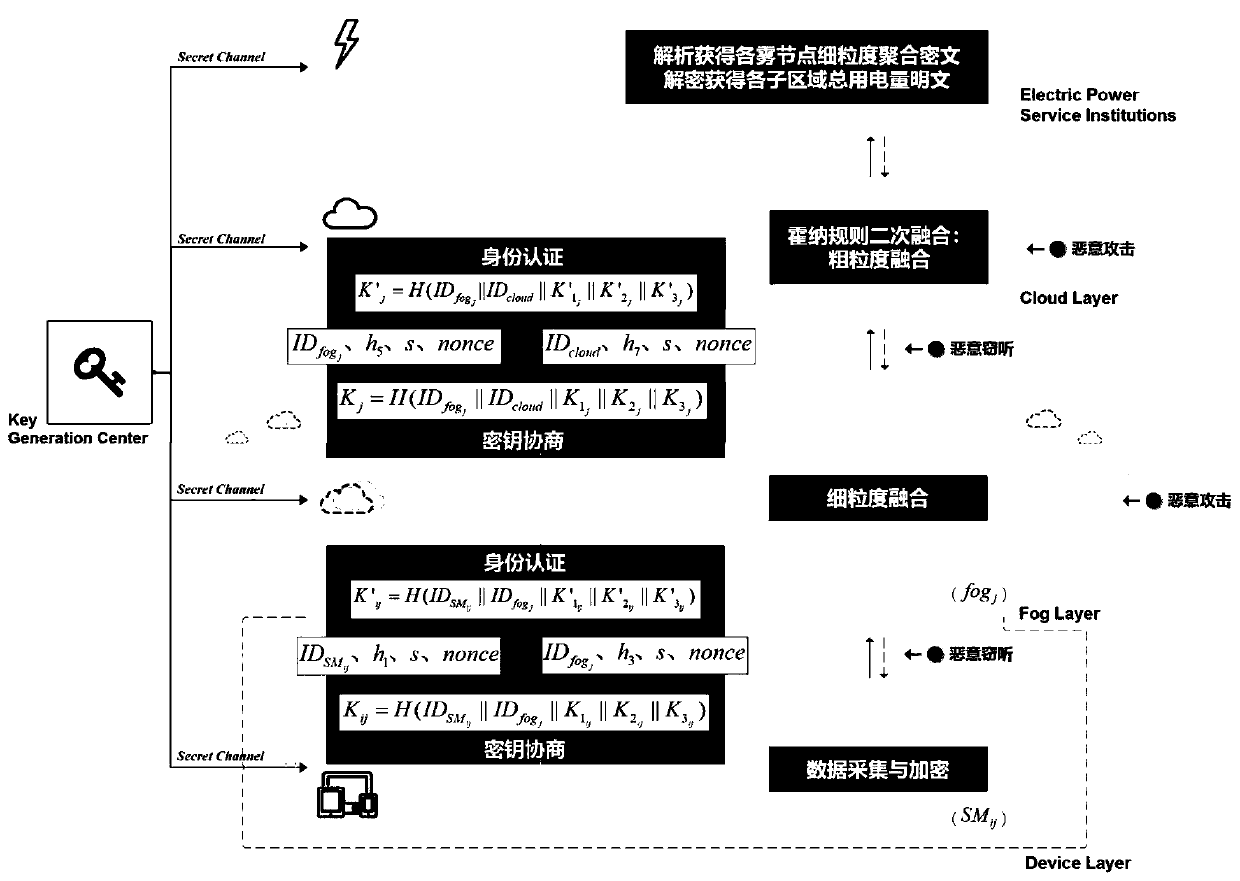
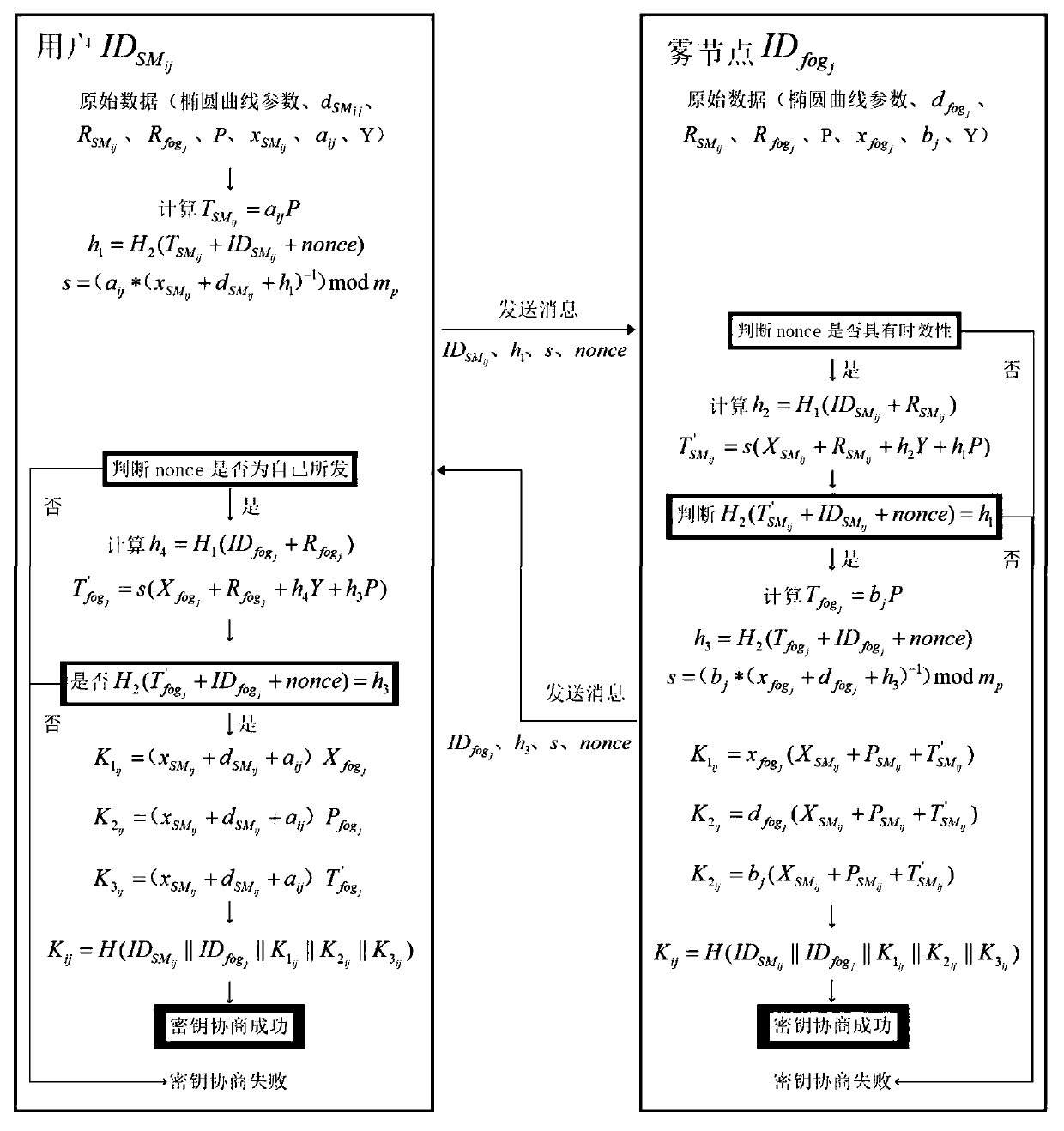
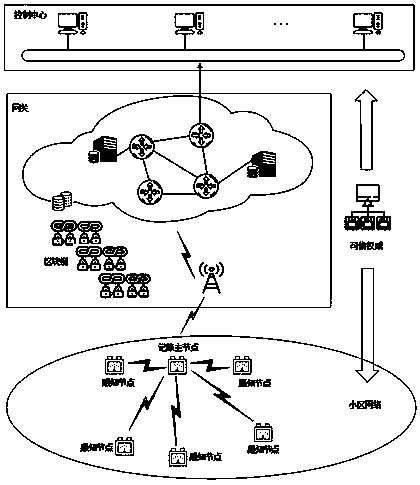
Intelligent power grid safety and privacy protection data aggregation method based on fog computing
ActiveCN110138538AIn line with regional divisionFlexible Power SchedulingKey distribution for secure communicationPublic key for secure communicationData aggregatorPrivacy protection
The invention provides an intelligent power grid security and privacy protection data aggregation method based on fog computing. The method comprises the following steps: acquiring, encrypting and uploading a user electricity consumption data report through an intelligent electric meter; performing fine-grained aggregation by using the fog nodes capable of mining local computing power and uploading the fine-grained aggregation to the cloud nodes; completing coarse-grained aggregated data through the cloud node and uploading the coarse-grained aggregated data to the electric power service mechanism; and finally collecting, processing and analyzing the coarse-grained aggregation data by a reliable power service mechanism, and generating a power dispatching scheme according to the analysis results. The method comprises the following specific steps: (1) initializing a system; (2) packaging an intelligent electric meter data report; (3) packaging a fog node fine-grained aggregation report;(4) packaging the coarse-grained aggregation report of the cloud node; and (5) reading the aggregation report by the power service mechanism. The method has the advantages that the security and integrity of user privacy data are protected, multi-resolution aggregation is carried out on the user privacy data, the transmission consumption is reduced, and flexible power dispatching is realized.
Owner:NANJING UNIV OF POSTS & TELECOMM
Intelligent power grid safety communication method based on combination cipher
ActiveCN105245326AAvoid negotiationReduce the number of saved keysPublic key for secure communicationPower gridSmart grid security
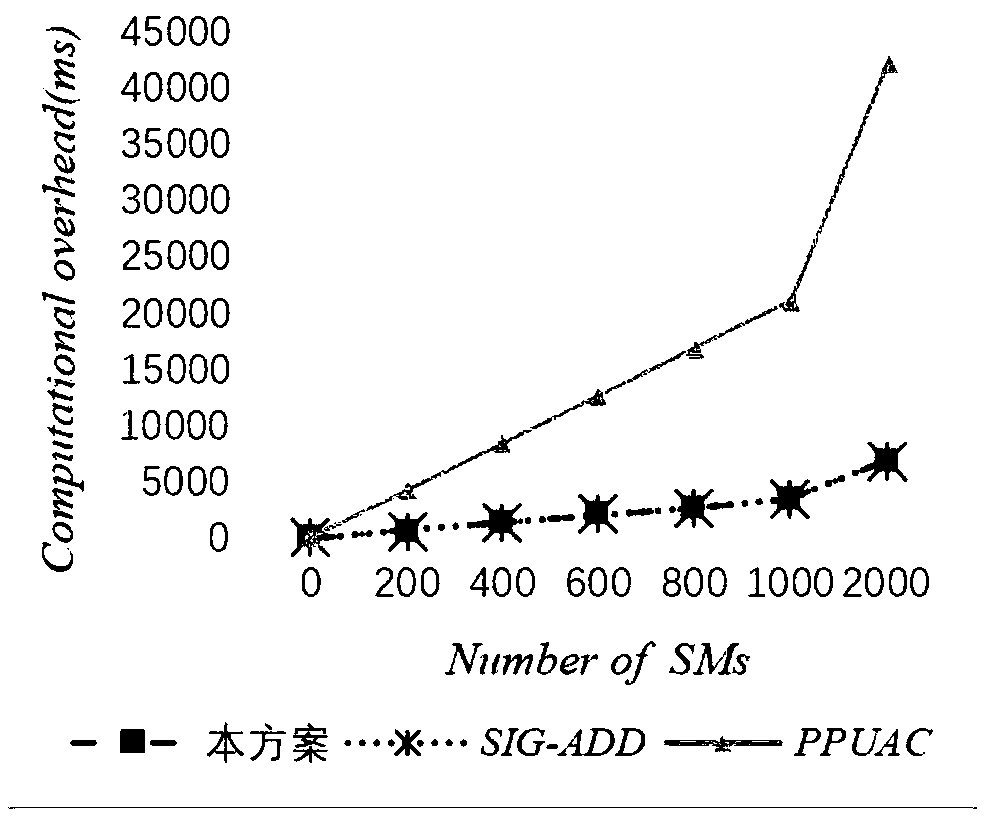
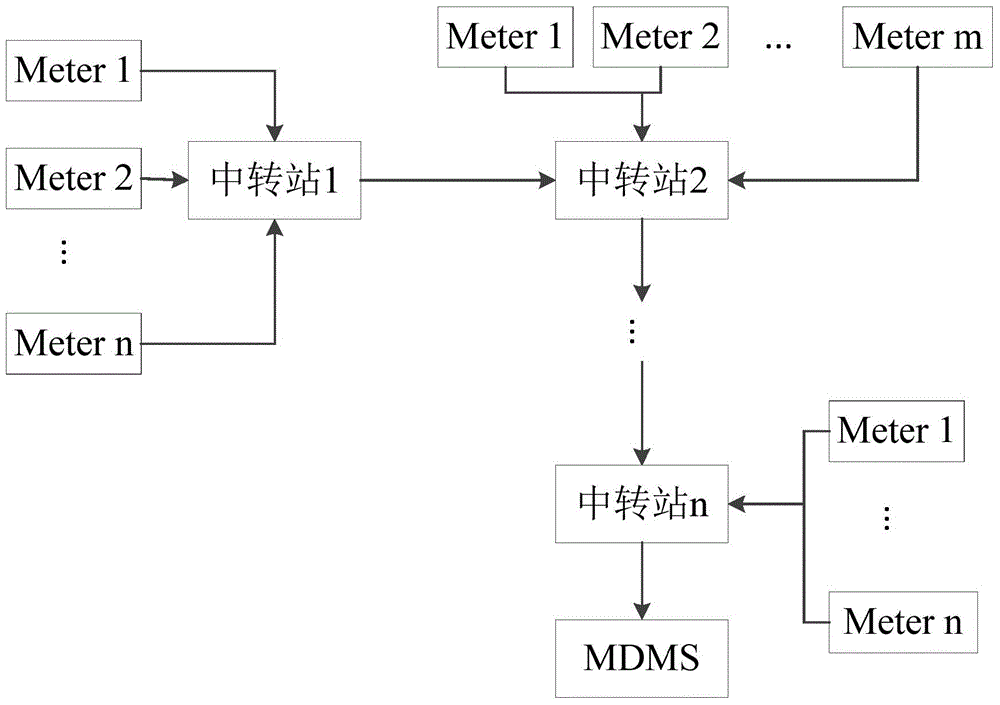
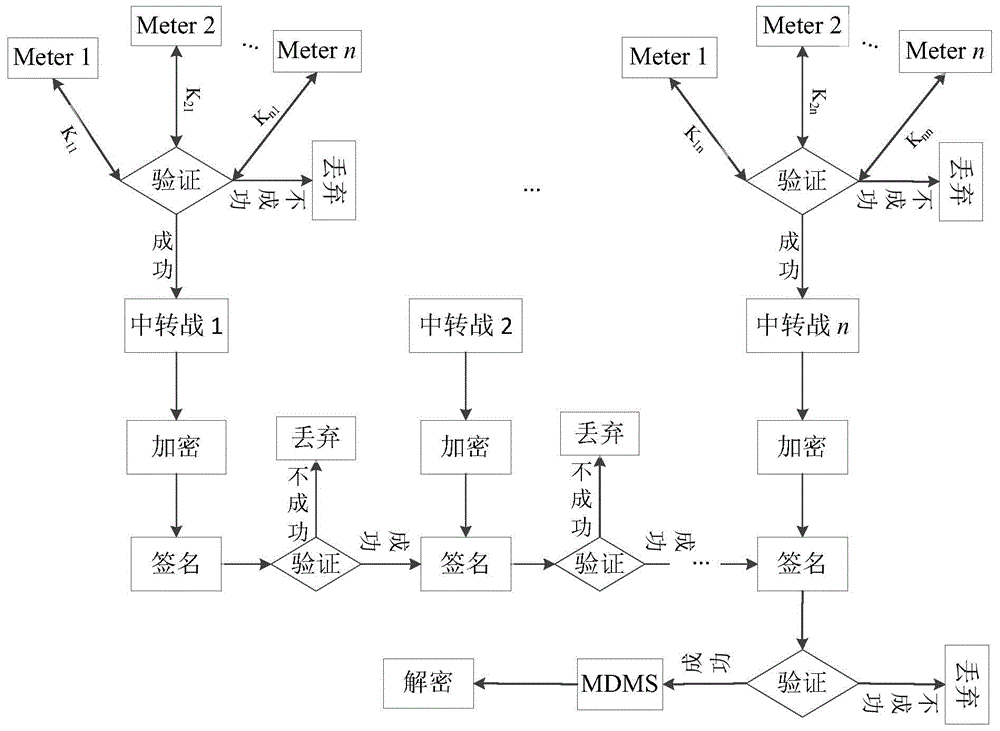
The invention discloses an intelligent power grid safety communication method based on a combination cipher. The combination cipher is adopted, one key is used for completing operation such as session key agreement, encryption and signature, and the method adopts an offline / online mode, and as for an intelligent power meter with limited storage space and limited computing power, the needed storage space can be reduced and the computing speed is enhanced. A transfer station is arranged between the intelligent power meter and a power meter data management center (MDMS), and private keys corresponding to the power meter, the transfer station and the MDMS are generated by a key generation center (PKG). A session key is firstly generated between the power meter and the transfer station, and the session key is used for realizing two-way authentication and carrying out communication. Then, a chain transmission mode is adopted, the transfer station acquires data of power meters in a governing range of the transfer station, certain safety operation is carried out, the data are then transmitted to the adjacent next transfer station, and by such analogy, the data finally reach the MDMS.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Intelligent power grid remote monitoring system based on IOS
ActiveCN104467187AStrict permission settingsClear requirementsCircuit arrangementsVideo monitoringWiring diagram
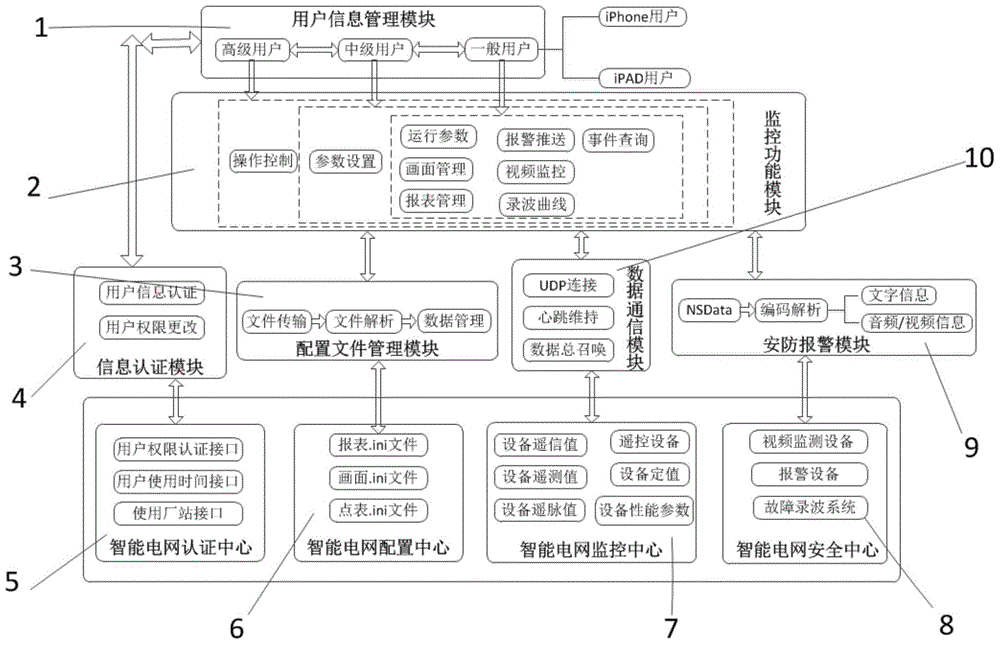
The invention discloses an intelligent power grid remote monitoring system based on an IOS. A user information management module is in communication with an intelligent power grid verification center to obtain user level information and corresponding use time limitation and permission passwords; a configuration file management module interacts with an intelligent power grid configuration center to obtain a power station wiring diagram frame configuration file, a power grid equipment operation parameter table configuration file and a power grid equipment performance report configuration file, and the obtained corresponding configuration files are analyzed into data to be used by a monitoring function module; the monitoring function module is in communication with an intelligent power grid monitoring center, and operation data such as remote signaling, remote monitoring and remote pulse, topological data and performance data of current equipment are obtained remotely; power grid on-site equipment parameters are set remotely, and related operation is carried out; a security protection and warning module can carry out video monitoring on an intelligent power grid site, and when a security protection module receives safety information sent by an intelligent power grid safety center, warning information is pushed on an IOS terminal device.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Energy-storage scheduling method and device for intelligent power grid
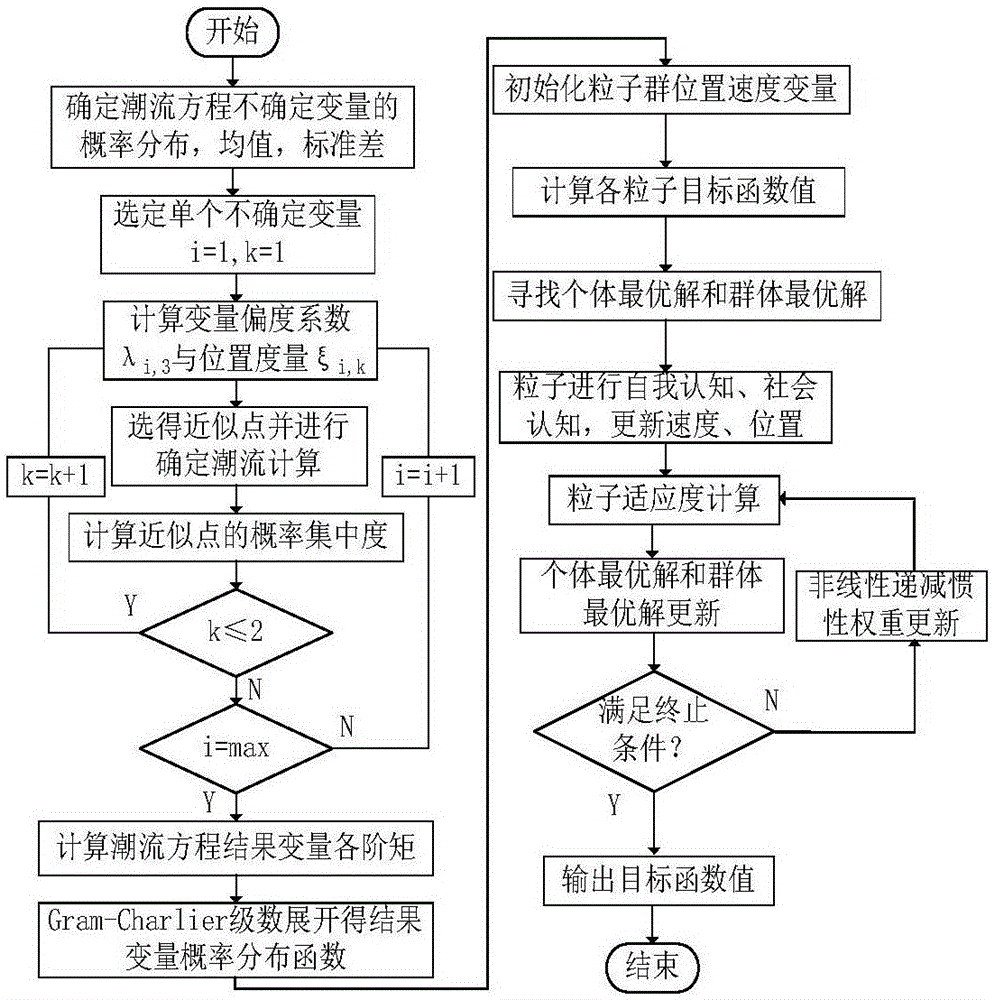
ActiveCN106253294AJump out of the suboptimal solutionGood ability to jump out of suboptimal solutionsForecastingAc network load balancingDecrease weightSeries expansion
The invention relates to an energy-storage scheduling method and device for an intelligent power grid, and the method comprises the steps: obtaining a power generator uncertainty model, a load uncertainty model and an electric car charging uncertainty model in the intelligent power grid, wherein the intelligent power grid comprises a wind power generator, an energy storage apparatus, and an electric car charging station; carrying out the stochastic load flow calculation of the intelligent power grid through employing a two-point estimation method based on a fourth-order Gram-Charlier series expansion equation, carrying out the random sampling of a stochastic load flow calculation result, and obtaining an expected load flow distribution; determining a constraint condition according to the expected load flow distribution, solving a pre-built target function through employing a particle swarm optimization algorithm based on a segmented inertia decreasing weight, and obtaining an optimal energy storage scheme meeting the constraint condition; and carrying out the scheduling of the energy storage device according to the optimal energy storage scheme. The method can effectively inhibit the uncertainty of the intelligent power grid, and enables the intelligent power grid to operate safely and stably.
Owner:FOSHAN POWER SUPPLY BUREAU GUANGDONG POWER GRID
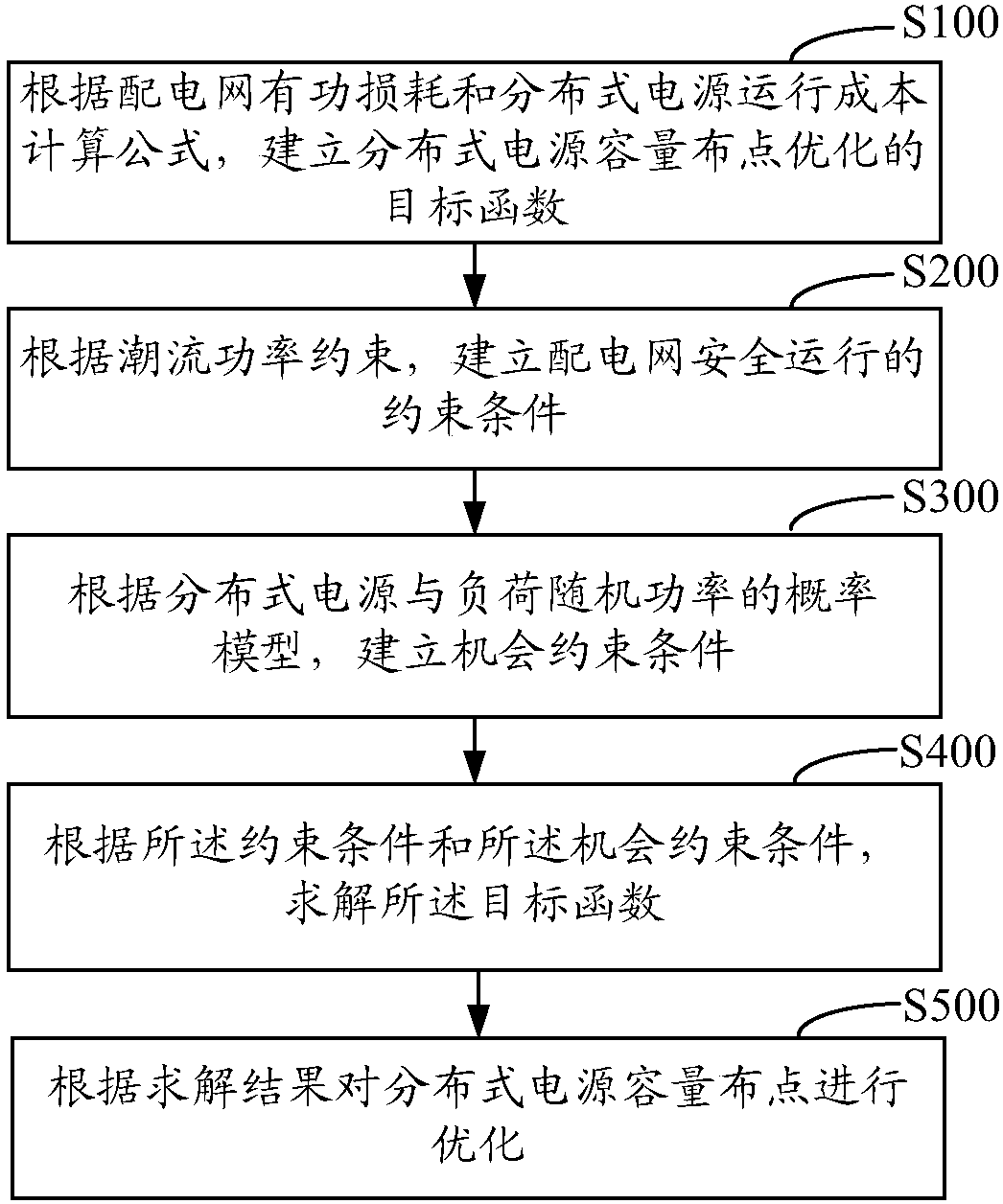
Fuzzy chance constraint planning method and system for distributed power supply capacity distribution points of distribution network
ActiveCN107069814ASolving Uncertain Joint Programming ProblemsSolving Joint Optimization ProblemsSingle network parallel feeding arrangementsNew energyPower grid
The invention relates to a fuzzy chance constraint planning method and system for distributed power supply capacity distribution points of a distribution network. The method comprises the steps of establishing a distributed power supply capacity distribution point optimization target function according to active loss and a distributed type power supply operating cost calculation formula of the distribution network; establishing a distribution network safety operation constraint condition according to a flow power constraint; establishing a chance constraint condition according to a probability model of the distributed power supply and load random power; solving the target function according to the constraint condition and the change constraint condition; and performing optimization on the distributed power supply capacity distribution points according to the solving result, so that the uncertainty jointed planning problem of the distributed power supply capacity distribution points can be well solved. By means of converting an inequality constraint condition into the change constraint condition higher than certain confidence level, compromise between the target function optimum and the constraint conditions can be achieved, so that the problem existing in jointed optimization of the distributed power supply capacity distribution points of the distribution network can be well solved; and therefore, reliable technological support can be provided for distributed new energy power generation and safety operation of the intelligent power grid.
Owner:GUANGDONG POWER GRID CO LTD DONGGUAN POWER SUPPLY BUREAU
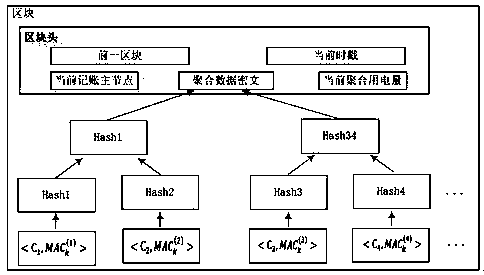
Intelligent power grid security data aggregation method and system based on block chain technology
ActiveCN110120868AIntegrity guaranteedProtect power consumption privacy informationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesConfidentialityData aggregator
The invention discloses an intelligent power grid security data aggregation method and system based on a block chain technology. A credible authority is responsible for managing and distributing secret information of all other entities; a control center is responsible for integrating, processing and analyzing periodic time sequence data of the cell network nodes and providing comprehensive and reliable intelligent services; agateway is responsible for aggregating the data submitted by the user; a sensing nodes are responsible for collecting data in real time and forwarding the data to the control center. The method includes a system initialization stage; a data collection stage; a security data aggregation stage; an accounting node selection stage; a new block generation stage; a block verification stage; and a decision support stage. On the basis of deeply researching and analyzing the existing application achievements of the block chain technology in the field of smart power grid application, the smart power grid security data aggregation method and system based on the block chain technology are realized, and meanwhile, the user privacy is protected and the confidentiality and integrity of communication data are ensured.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
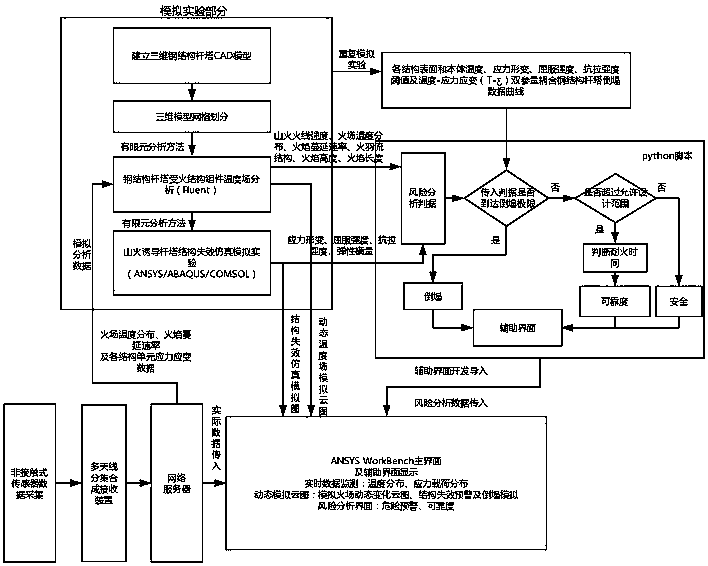
Simulation and safety early warning method for mountain fire induced steel structure tower structure failure
ActiveCN109492925ADisplay propertiesTimely display warning informationDesign optimisation/simulationResourcesElement analysisFire resistance
The invention relates to a simulation and safety early warning method for mountain fire induced steel structure tower structure failure. Based on a distributed non-contact sensor, a multi-antenna diversity into receiving mode and a remote server, the time-varying space temperature field of mountain fire is analyzed by Fluent; structural fire resistance inspection is carried out by using nonlinearfinite element analysis tools such as ANSYS / ABAQUS / COMSOL; and the two models are coupled, dynamic simulation, threshold comparison and image fitting are carried out, and a theoretical calculation, nonlinear finite element simulation and data analysis model for steel structure tower fire resistance characteristic and gradual change stress loss, stress deformation and collapse danger level judgmentis established. The method has the advantages that guidance is provided for planning, design and operation maintenance of power transmission line steel structure towers with various tower shapes andvarious voltage grades, and safe operation and structure failure early warning of the steel structure towers and an intelligent power grid are achieved.
Owner:NANJING UNIV OF TECH
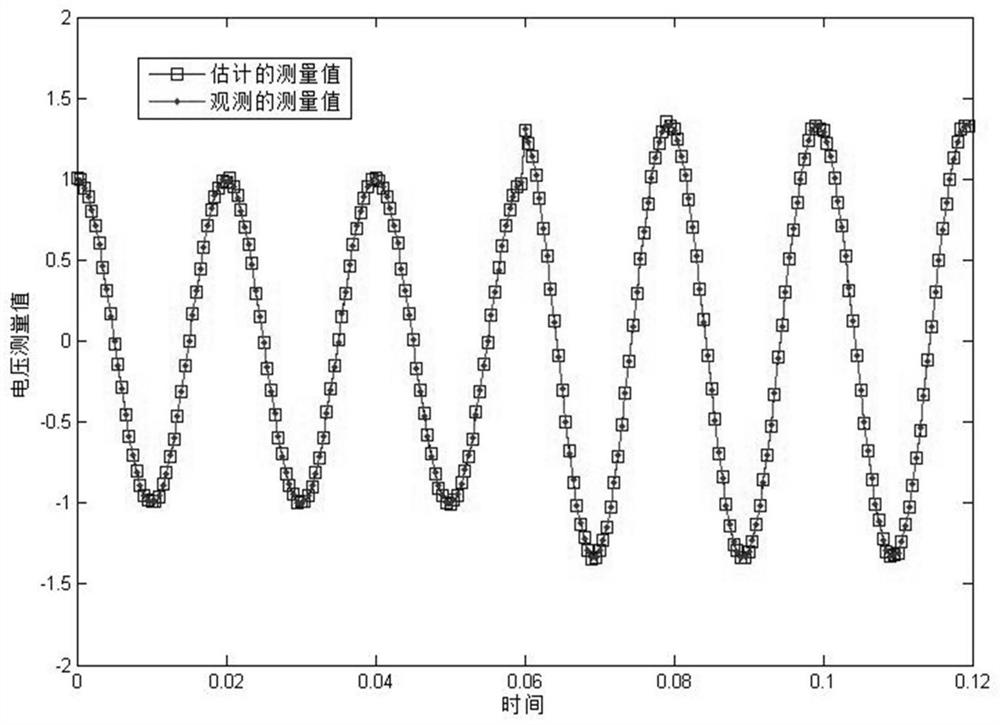
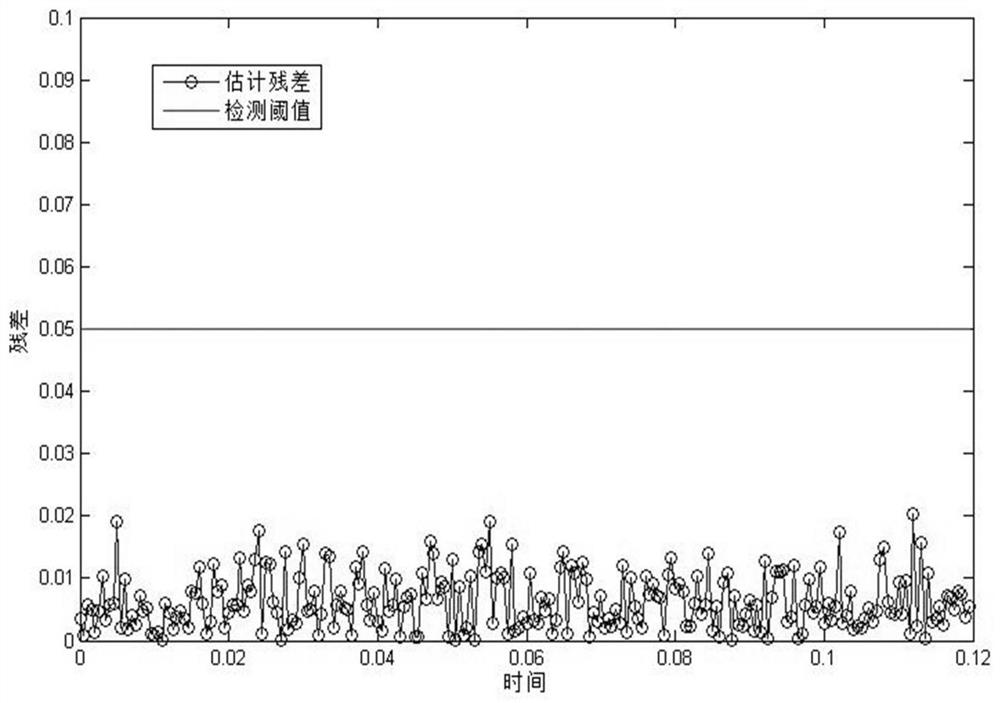
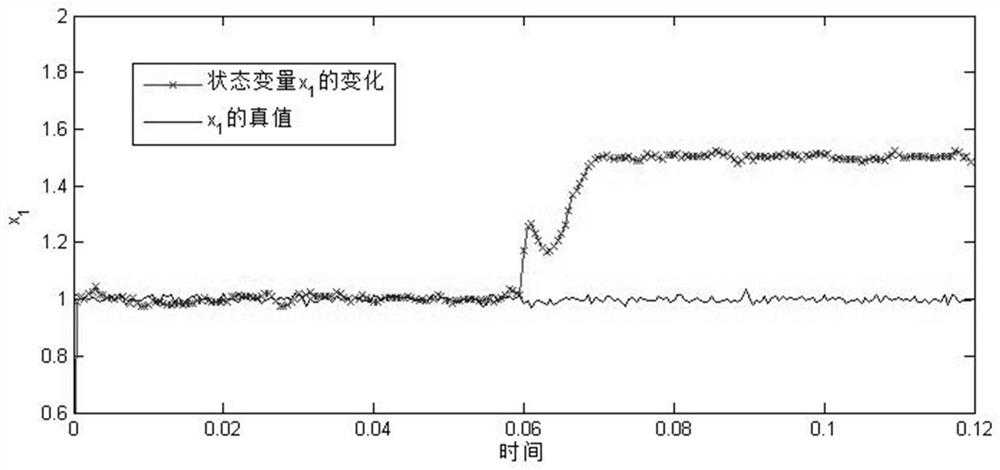
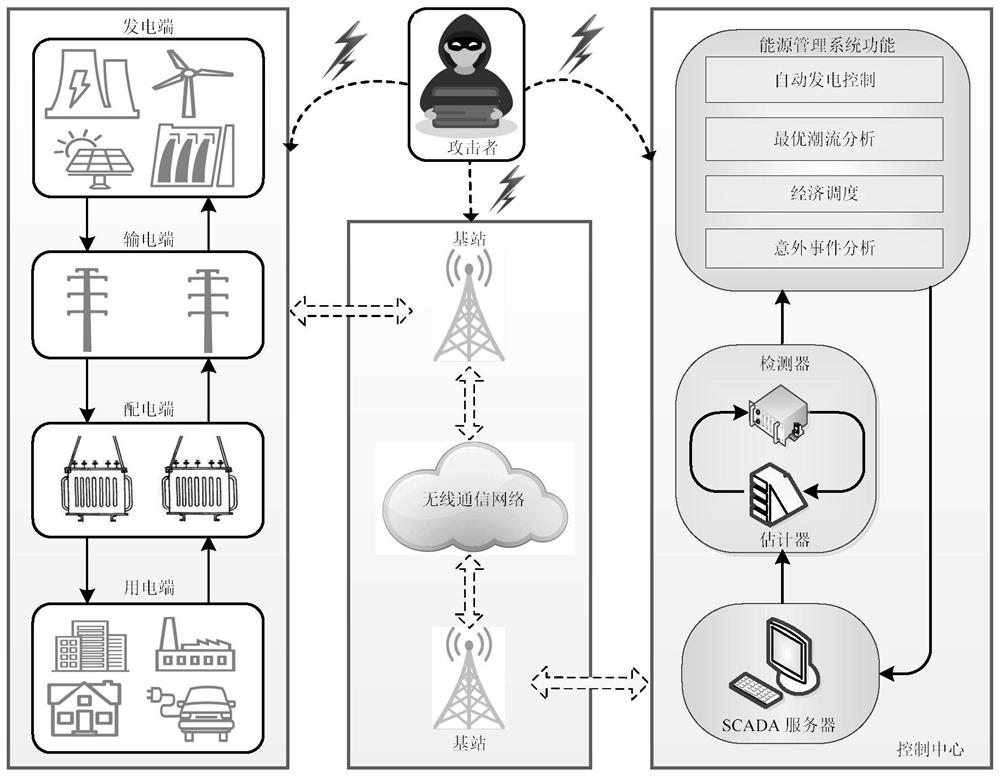
Error data injection attack robustness detection method based on state estimation deviation
PendingCN111723366AResponse in real timeImprove robustnessPlatform integrity maintainanceComplex mathematical operationsAlgorithmPower grid
The invention relates to an intelligent power grid safety technology, in particular to an error data injection attack robustness detection method based on state estimation deviation. The method comprises four steps of static weighted least square state estimation, dynamic state estimation of an additionally introduced Kalman estimator, enhancement of dynamic estimation robustness and inspection ofestimation performance consistency. According to the method, the concealment characteristic of the error data injection attack in the smart power grid is comprehensively considered, based on an original static state estimator based on weighted least squares, and according to the characteristic that an additionally introduced Kalman estimator has a transfer characteristic for a historical state ofa system and an exponential weight function can be adaptively changed according to attack intensity, the deviation of the estimated performances of the two estimators is used as an index for measuring the detection performance, so that the effective detection of the error data injection attack with the hidden characteristic in the intelligent power grid is realized.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
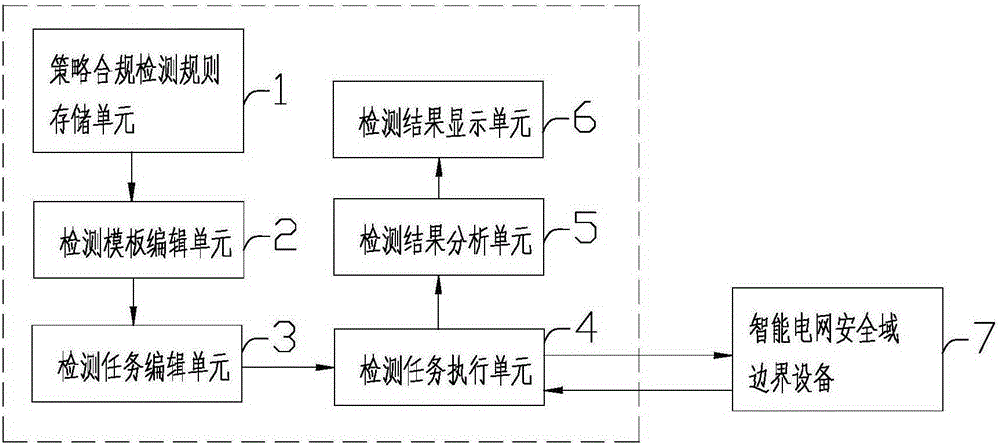
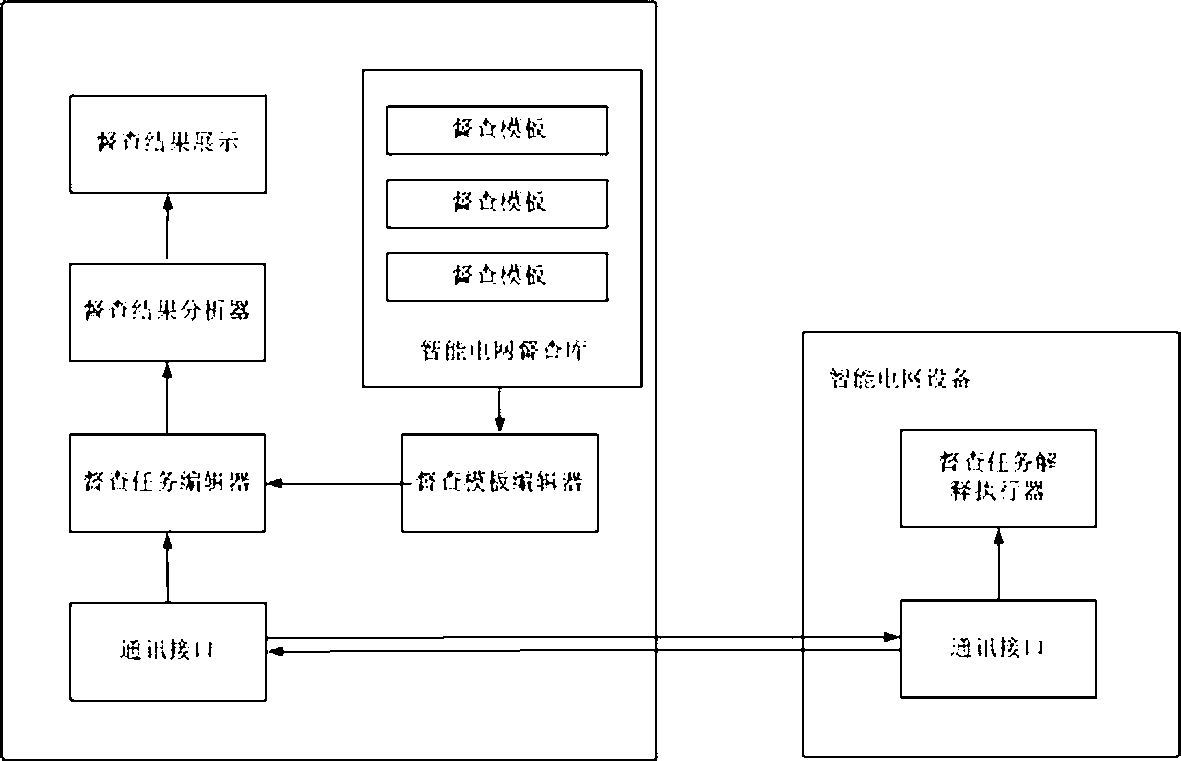
System and method for management and control of access control policy of security domain boundary equipment of smart grid
The invention provides a system for management and control of an access control policy of security domain boundary equipment of a smart grid. The system comprises a strategy compliance detection rule storage unit, a detection template editing unit, a detection task editing unit, a detection task execution unit, a detection result analysis unit and a detection result display unit. According to the system and the method, security detection templates for different types of security domain boundary equipment of the smart grid can be defined quickly and accurately, and the detection templates for new intelligent security domain boundary equipment needing to be introduced in the future introduced of the smart grid can be also subjected to customization of the security detection templates through the system, so that the security detection range of the security domain boundary equipment of the smart grid and the flexibility for making a security detection rule are greatly improved, and the security detection task can be quickly issued to the appointed security domain boundary equipment of the smart grid for collecting the scattered configuration information of the security domain boundary equipment of the smart grid through a structural data format.
Owner:STATE GRID CORP OF CHINA +1
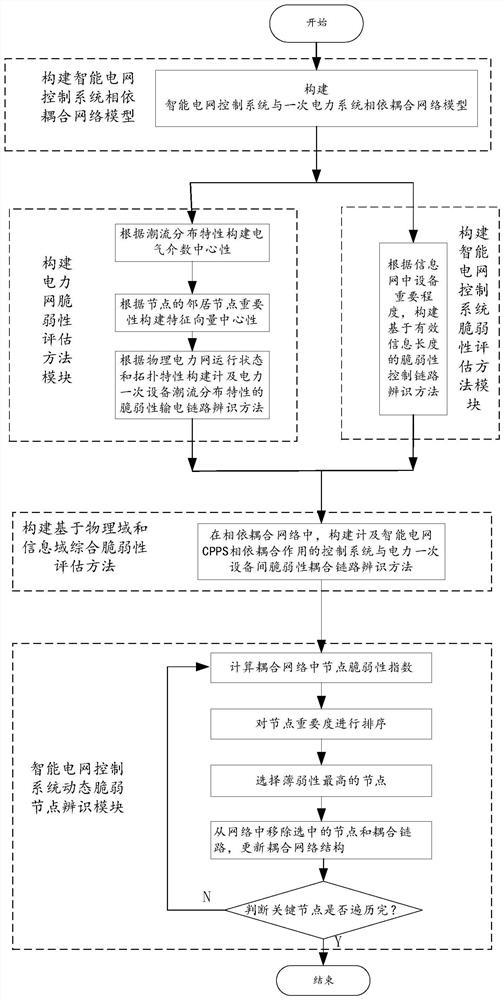
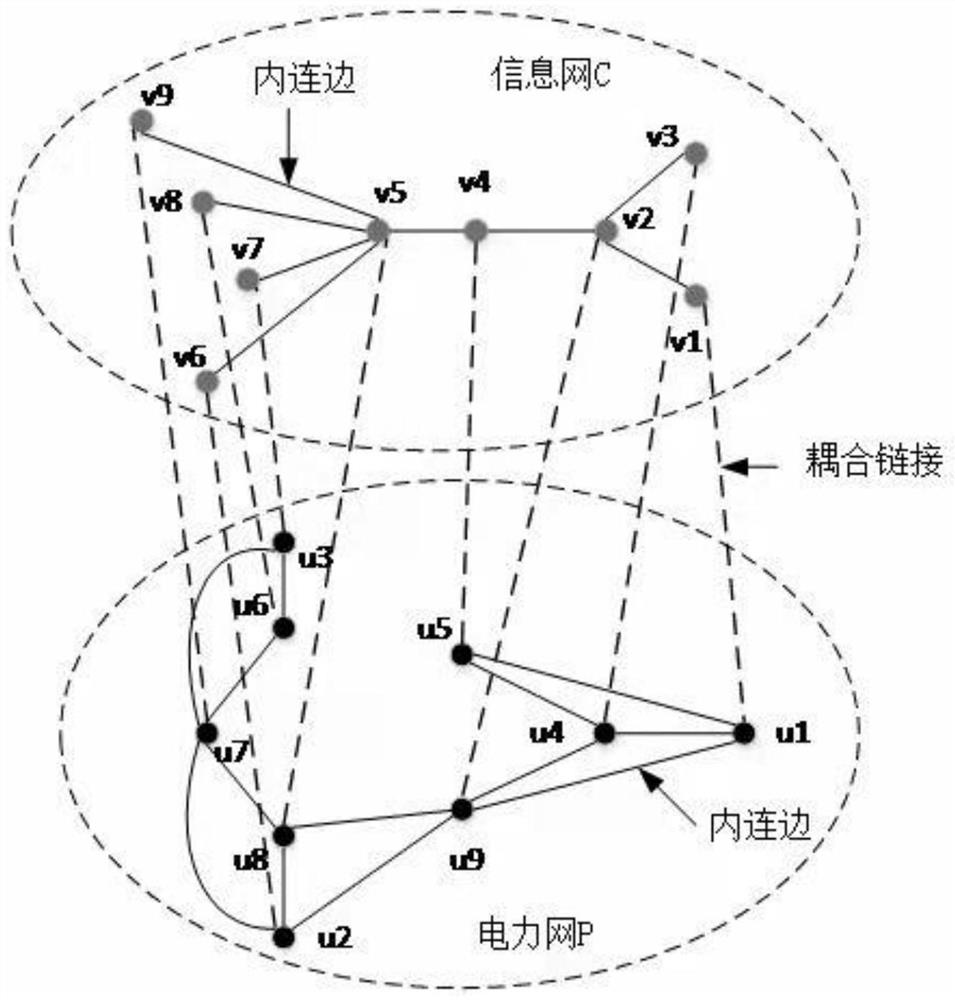
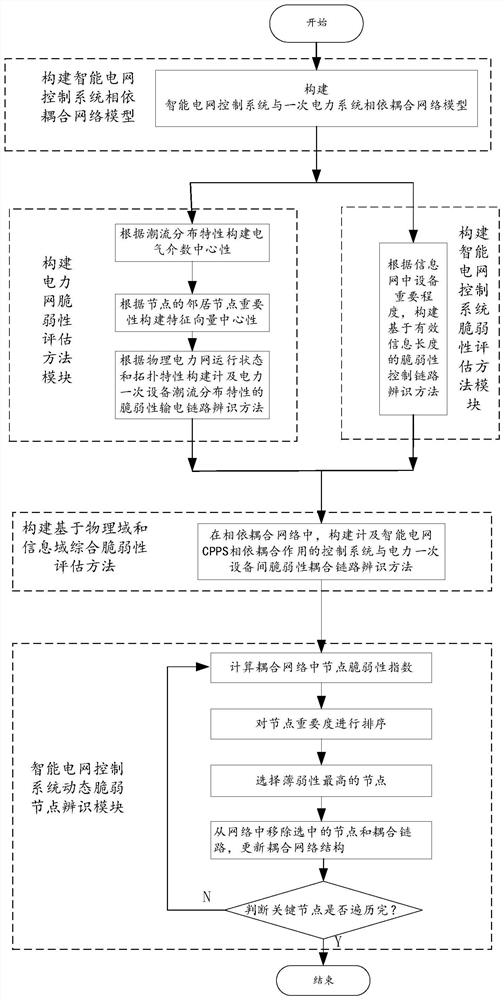
Method for identifying vulnerable coupling link between power grid control system and power primary equipment
PendingCN114124728AIn line with actual operating conditionsEffectively combine the characteristics of power flow distributionForecastingTransmissionControl systemInformation networks
The invention relates to the field of safe and reliable operation guarantee of an intelligent power grid, and discloses a method for identifying a vulnerability coupling link between a power grid control system and power primary equipment, which comprises the following steps of: 1, establishing a network model for the dependent coupling of the intelligent power grid control system and the power primary equipment, and the network model comprises a power network and an information network; step 2, constructing a vulnerability identification method based on node centrality so as to obtain a node electrical centrality index between nodes in the power network and a proximity centrality index of effective information length between the nodes in the information network; step 3, calculating a comprehensive risk measurement index DLCC (Pi, Ci) based on a power network-information network; and step 4, calculating the comprehensive risk measurement index DLCC (Pi, Ci), finding out the key vulnerability coupling link of the power network-information network and removing the key vulnerability coupling link. According to the method, the robustness of the intelligent power grid control system is improved to the maximum extent, and the probability of cascade faults is reduced.
Owner:STATE GRID SICHUAN ECONOMIC RES INST
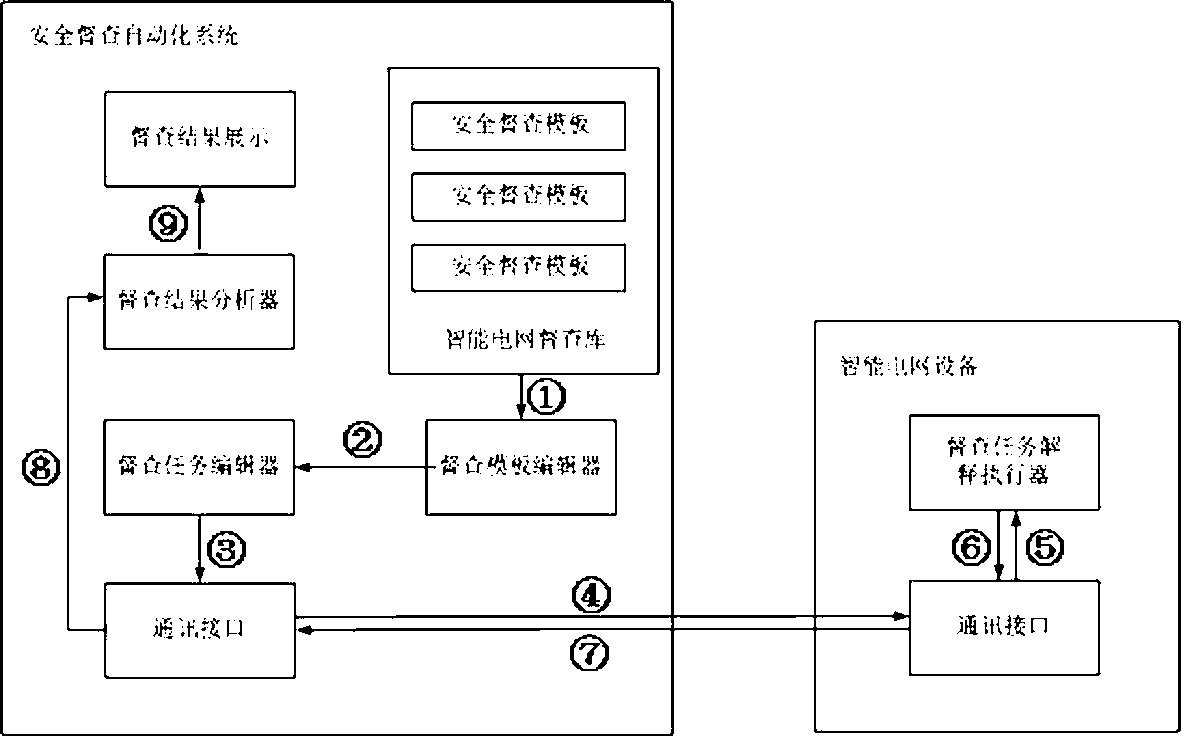
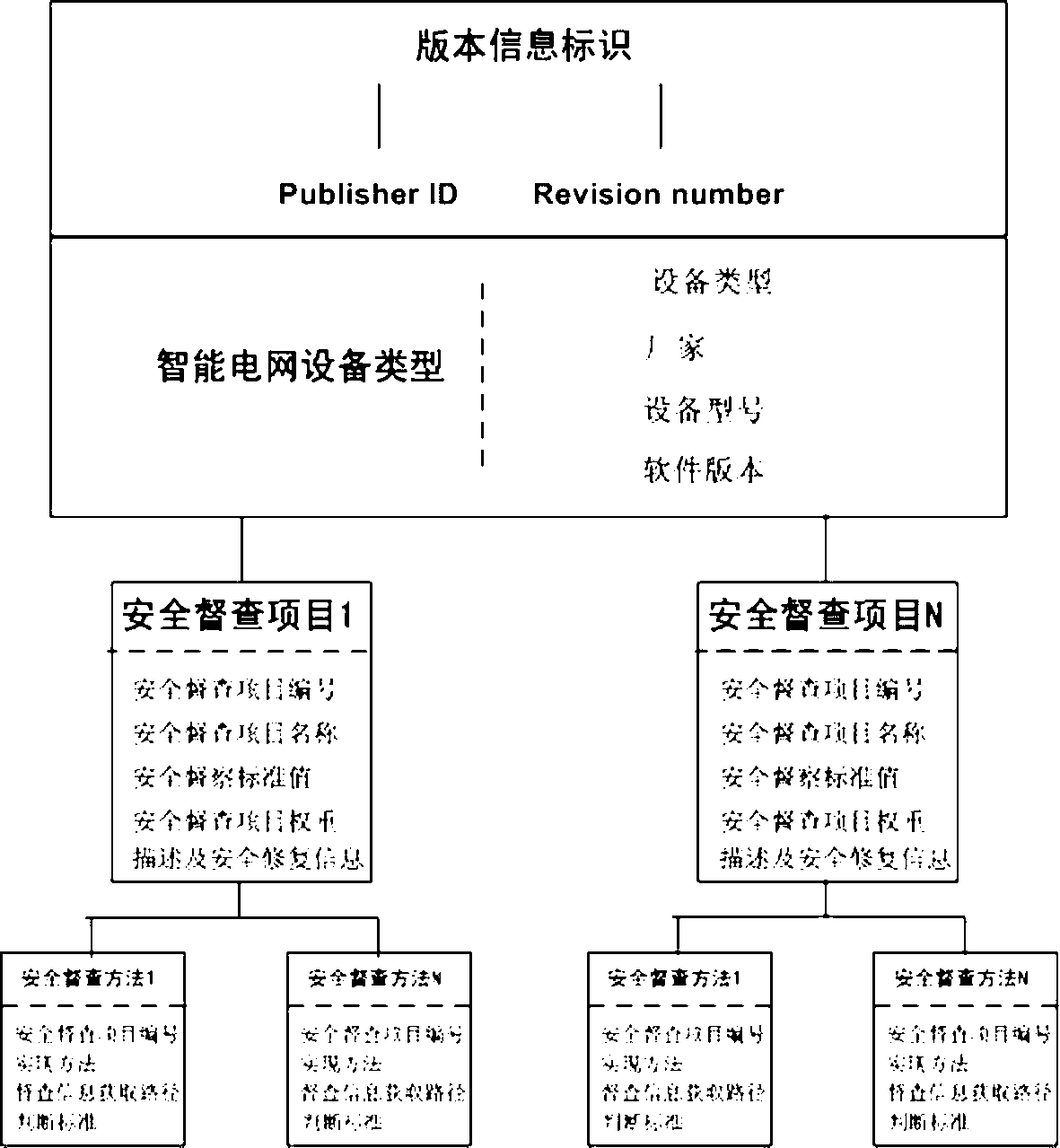
Smart grid security supervising and examining automatic system
InactiveCN103268569AQuick definitionPrecise definitionData processing applicationsConsequence analysisCommunication interface
Disclosed is a smart grid security supervising and examining automatic system. The smart grid security supervising and examining automatic system comprises a smart grid supervising and examining base, a supervising and examining template editor, a supervising and examining task editor, a supervising and examining task actuator, a supervising and examining result analysis device, a communication interface and supervising and examining result display. The smart grid security supervising and examining automatic system has the advantages of being capable of fast and accurately defining safety supervising and examining templates regarding all kinds of smart grid devices, supervising and examining safety templates of new smart grid devices to be introduced in the future can also be customized according to a standard protocol, and therefore the smart grid security supervising and examining automatic system greatly improves the safety supervising and examining range of the smart grid device and flexibility of customizing of the supervising and examining safety templates of the new smart grid devices, and fast issues safety supervising and examining tasks to appointed smart grid devices so as to achieve the purpose of collecting scattered smart grid device configuration information through structuralized data formats.
Owner:STATE GRID HUBEI ELECTRIC POWER COMPANY INFORMATION & TELECOMM +1
System and method for security defense of embedded terminal
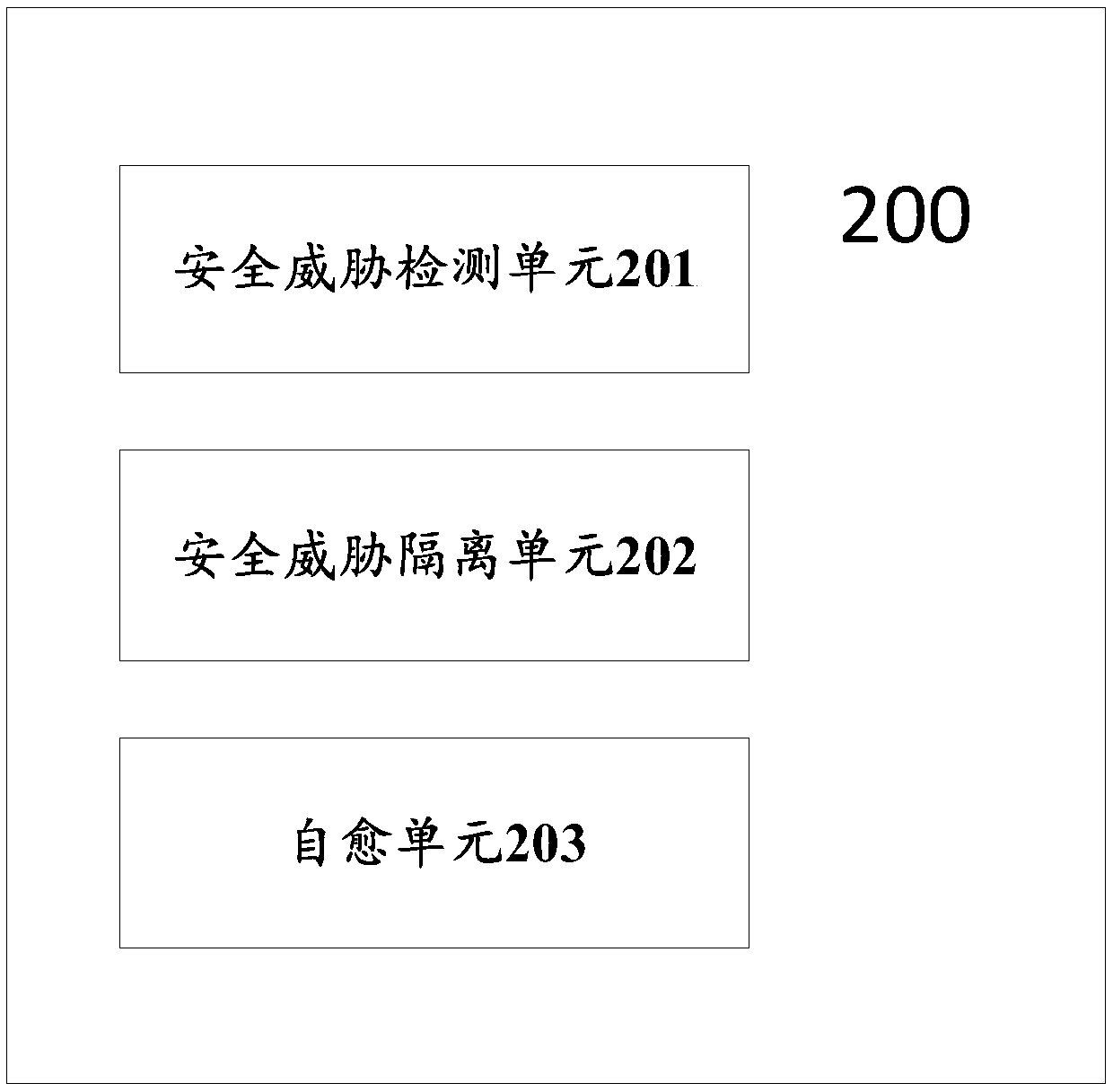
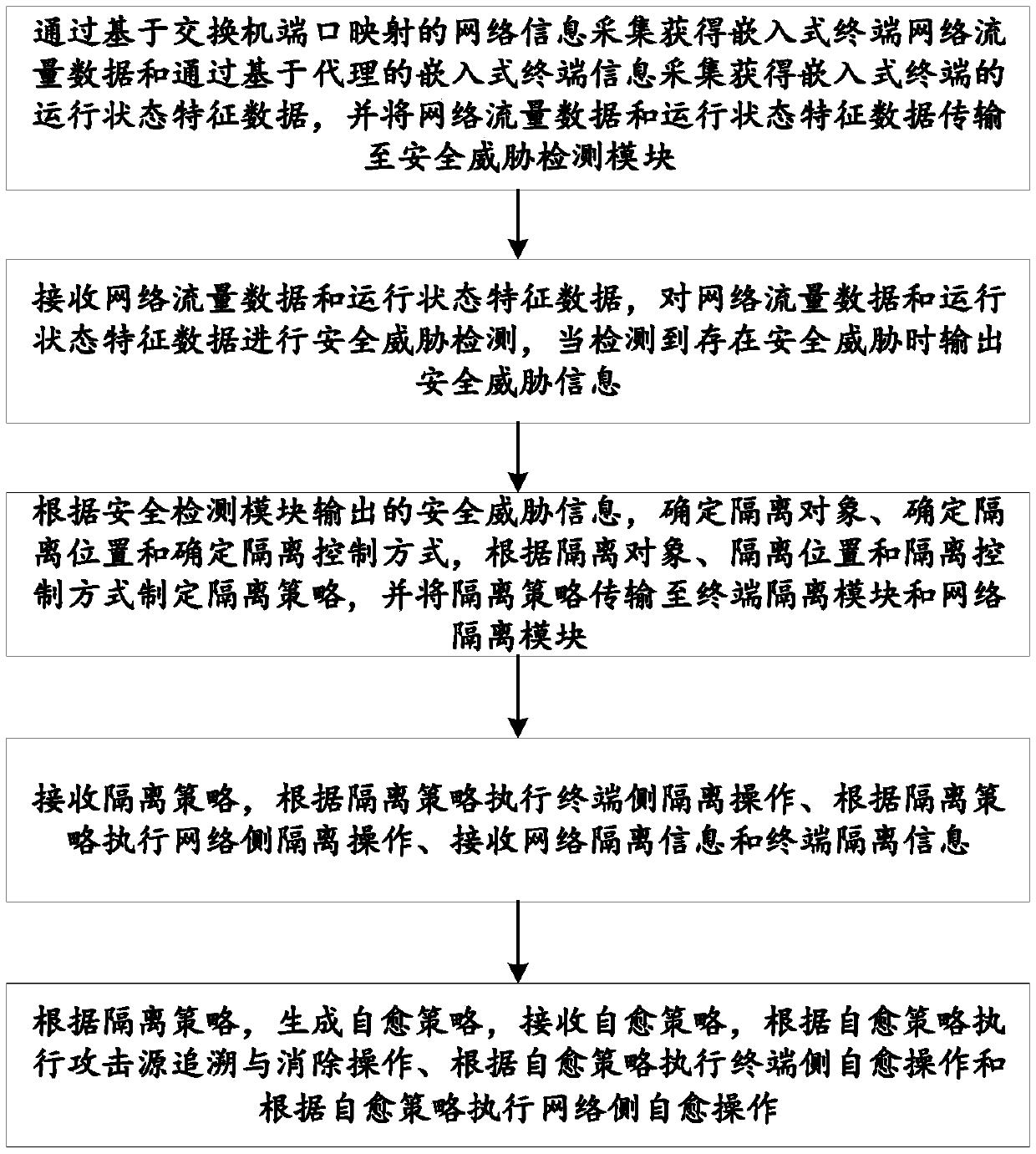
ActiveCN109660550AGuaranteed uptimeData switching networksInformation technology support systemSelf-healingSource tracing
The invention discloses a system and method for security defense of an embedded terminal and belongs to the technical field of smart power network security. The system comprises a security threat detection unit which comprises a distributed data collection module and a security threat detection module; a security threat isolation unit which comprises an isolation policy making module, a terminal isolation module and a network isolation module; and a self-healing unit which receives network isolation information and terminal isolation information, and comprises a self-healing policy making module, an attack source tracing and elimination module, a terminal self-healing module and a network self-healing module. According to the system and the method, when a power network embedded terminal suffers from a security threat, the terminal is enabled to recover to a normal operation state timely and effectively, and further, secure and reliable operation of a power industrial control system areensured.
Owner:CHINA ELECTRIC POWER RES INST +3
Intelligent power grid line state error data injection attack detector and detection method
ActiveCN108683642ALower latencyInjection detection works wellCharacter and pattern recognitionData switching networksElectrical resistance and conductanceData aggregator
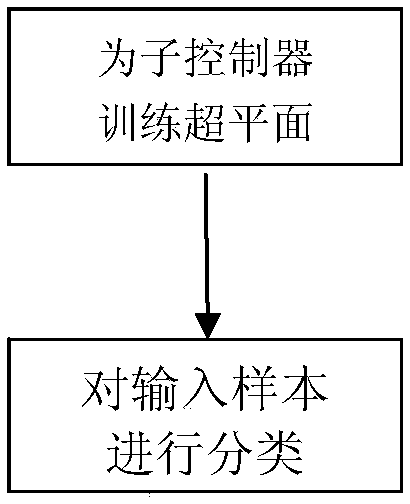
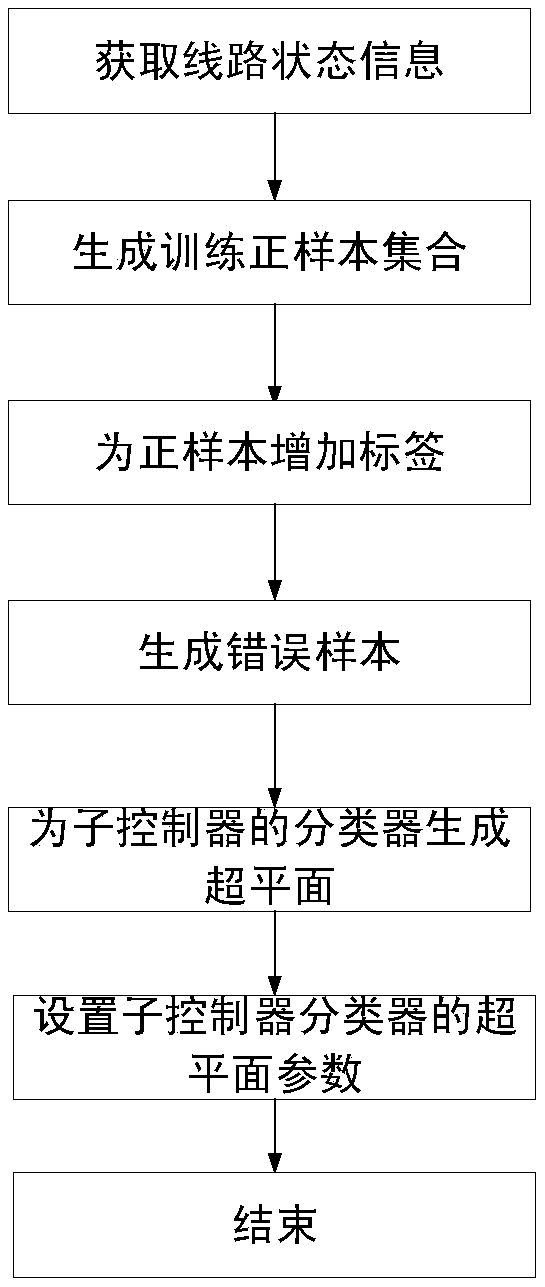
The invention relates to an intelligent power grid line state error data injection attack detector and detection method, and belongs to the field of intelligent power grid safety detection application. The detector is composed of four parts of a detector data collector, a line identifier, a data aggregator and a classifier. Compared with the conventional detector, the detector can be installed oneach sub-controller of the intelligent power grid. The computing resource, the storage resource and the communication resource of the sub-controllers are fully utilized to design a distributed detector framework. Each sub-controller is provided with an independent detector for judging error data injection. The characteristic of limited computing capacity of the sub-controllers is considered, the training process of the classifier is transferred to the central controller and each sub-controller only requires to classify the data. Meanwhile, the related six-dimensional arrays are selected to generate the sample points to act as the input of abnormity detection according to the inherent attribute of the line, i.e. the characteristic of constant resistance.
Owner:湖南中科智云科技有限公司
Electric power Internet of Things terminal equipment side channel safety monitoring method based on adversarial reinforcement learning
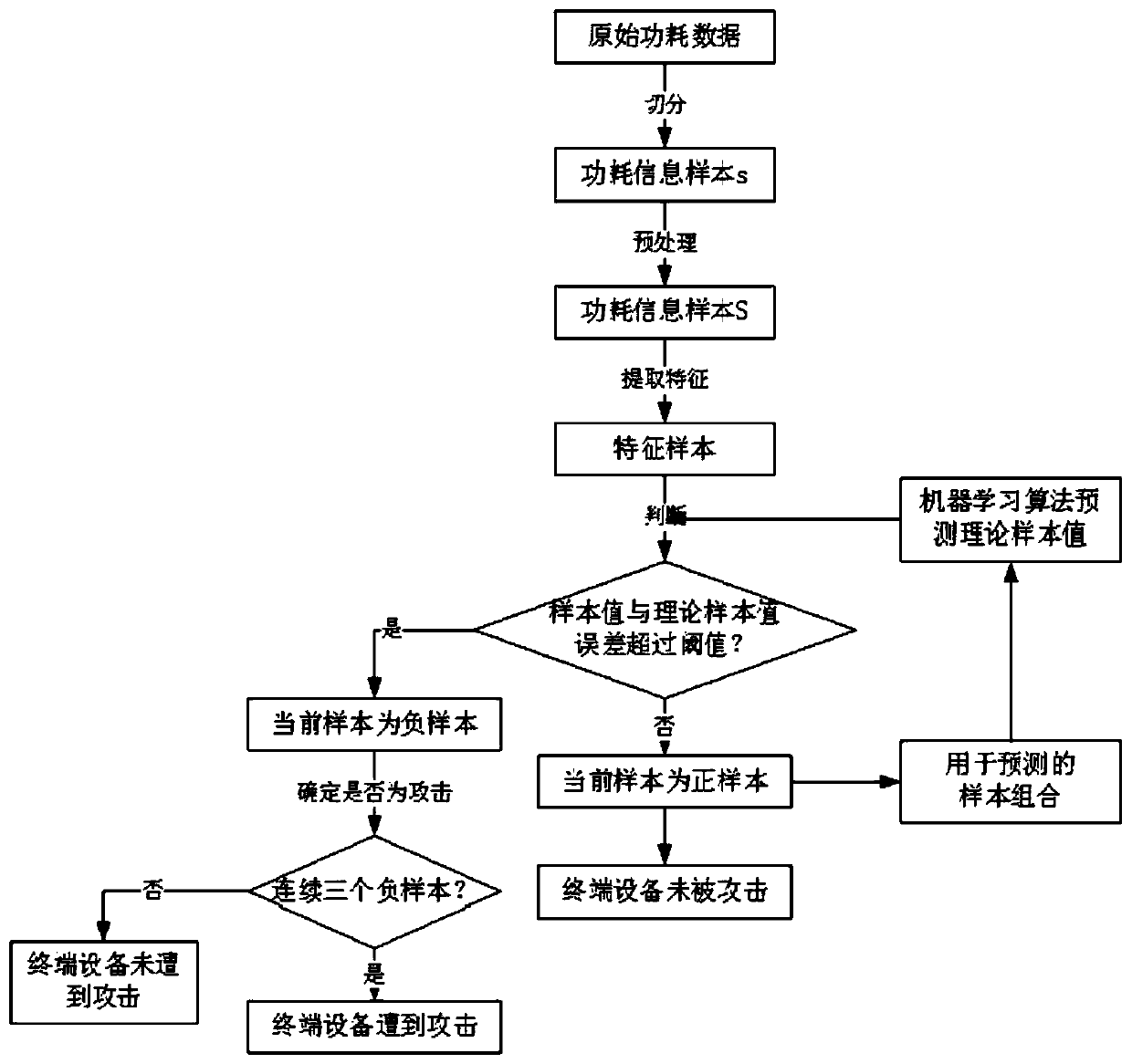
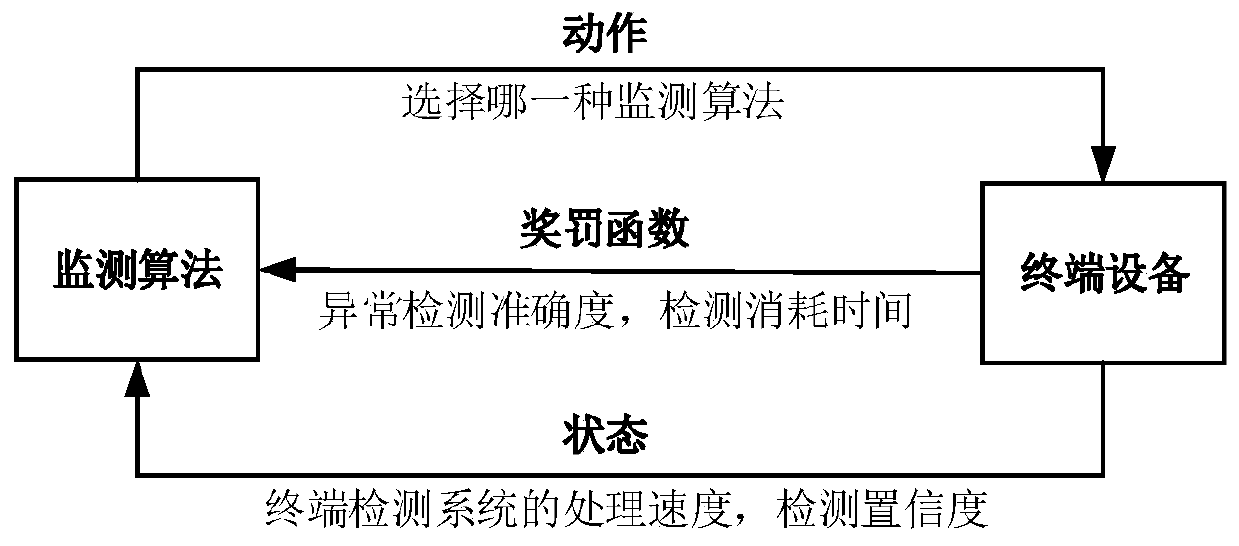
ActiveCN110971677AReduce distractionsInformativeData switching networksStatistical analysisEngineering
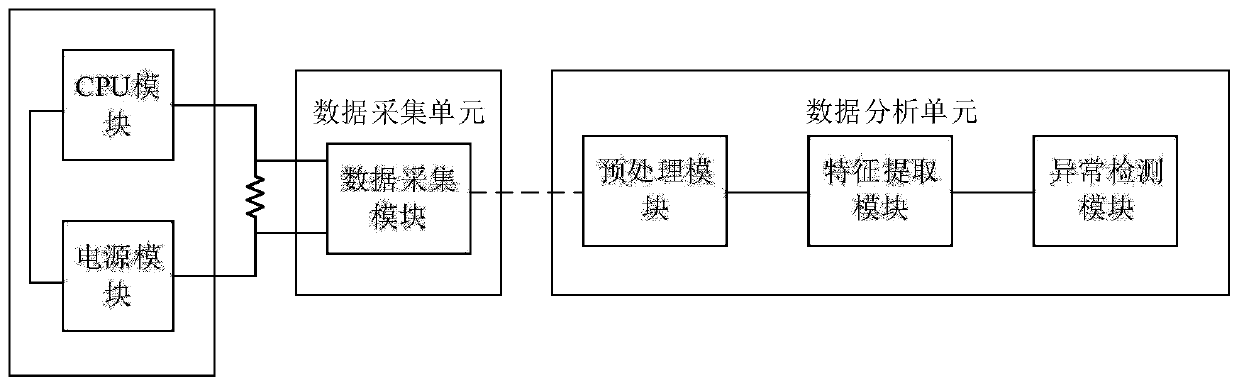
The invention discloses an electric power Internet of Things terminal equipment side channel safety monitoring method based on adversarial reinforcement learning, and belongs to the field of intelligent power grid safety. The method comprises the following steps: performing preprocessing and statistical analysis on power consumption side channel information of terminal equipment, determining a feature combination related to the change of the working state of the terminal equipment, and taking preprocessed side channel features as the input of an anomaly monitoring model; using historical sidechannel data of the terminal equipment in a normal working state as a normal sample to be input into the anomaly monitoring model; and training a single-classification-based exception monitoring modelin various normal working states, and verifying the effectiveness and performance of the terminal equipment exception monitoring model based on the side channel information through new terminal equipment exception state data. In the actual monitoring process, an anomaly monitoring agent is adopted to automatically select a single anomaly monitoring model execution program, adaptive adjustment ofalgorithm complexity is achieved, accuracy and rapidity are both considered, and the safety performance of the electric power Internet of Things terminal equipment is improved.
Owner:JILIN ELECTRIC POWER RES INST +3
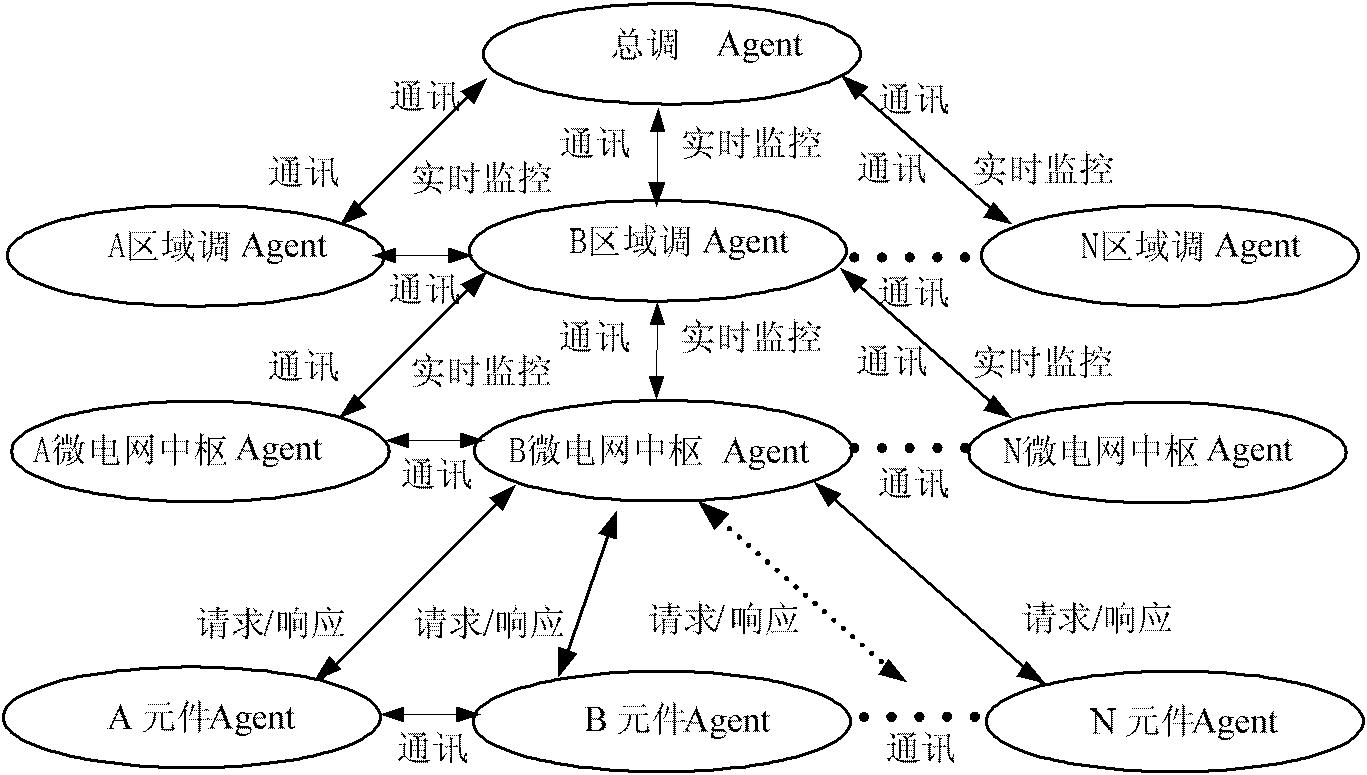
Micro-grid multi-agent control system and method
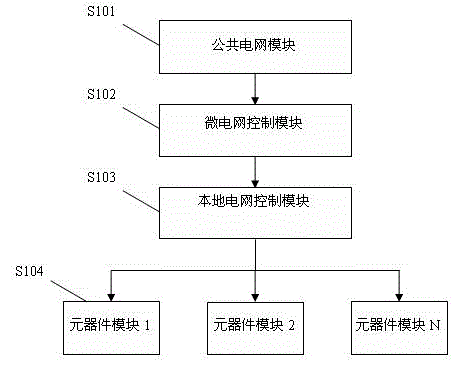
InactiveCN104932304AEfficient managementRealize intelligent operationProgramme control in sequence/logic controllersPower gridComputer module
The invention relates to a micro-grid multi-agent control system and method. The system comprises a public power grid module, a micro-grid control module, a local power grid control module and component and part modules. The micro power sources in the micro-grid can be effectively managed by the system, and multiple types of energy of the power grid can be scheduled so that intelligent operation of the micro-grid can be realized, and safe, stable and economical operation of the intelligent power grid can be guaranteed.
Owner:CHANGCHUN INST OF TECH
Method and system for monitoring operation state of power grid embedded terminal equipment
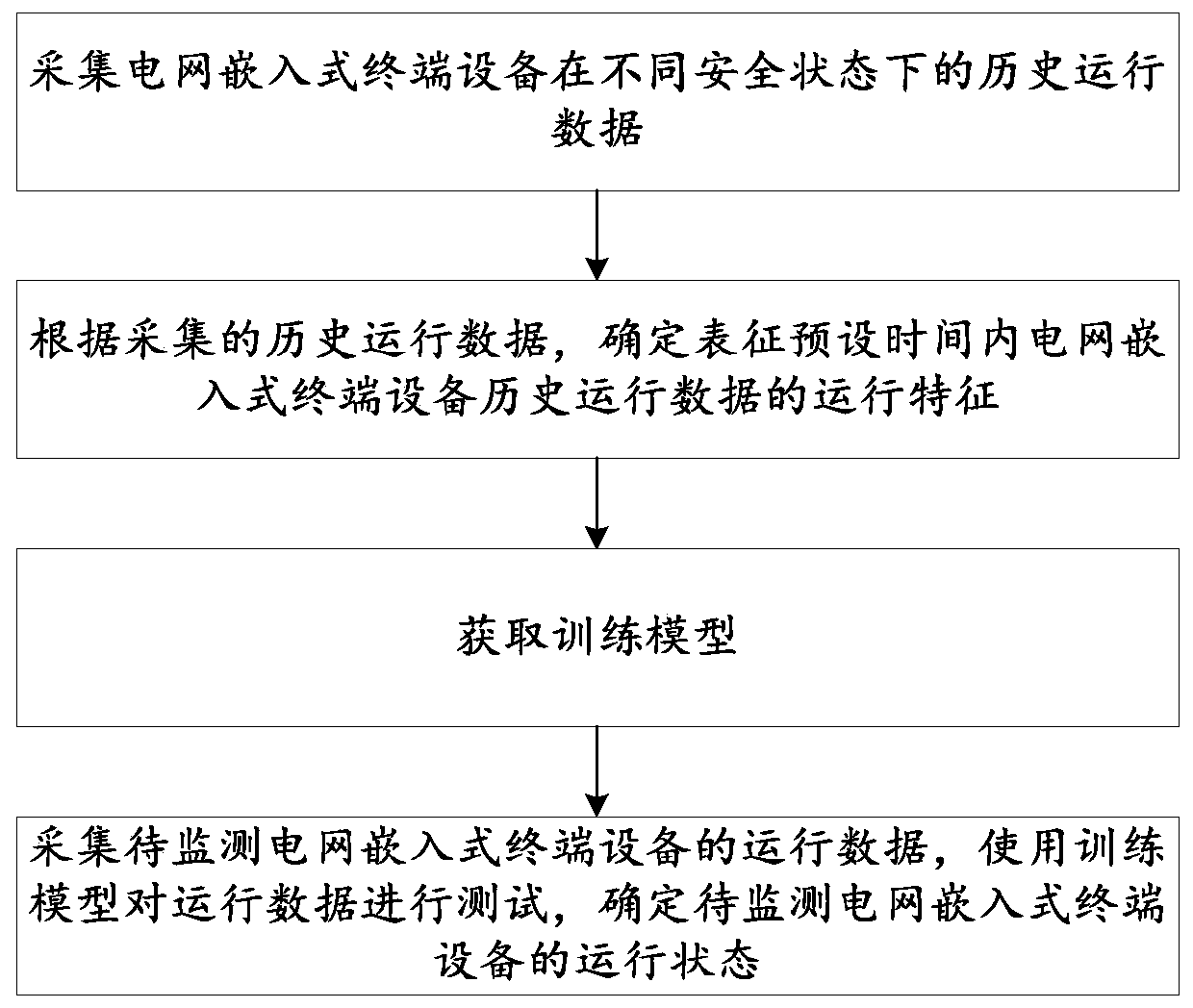
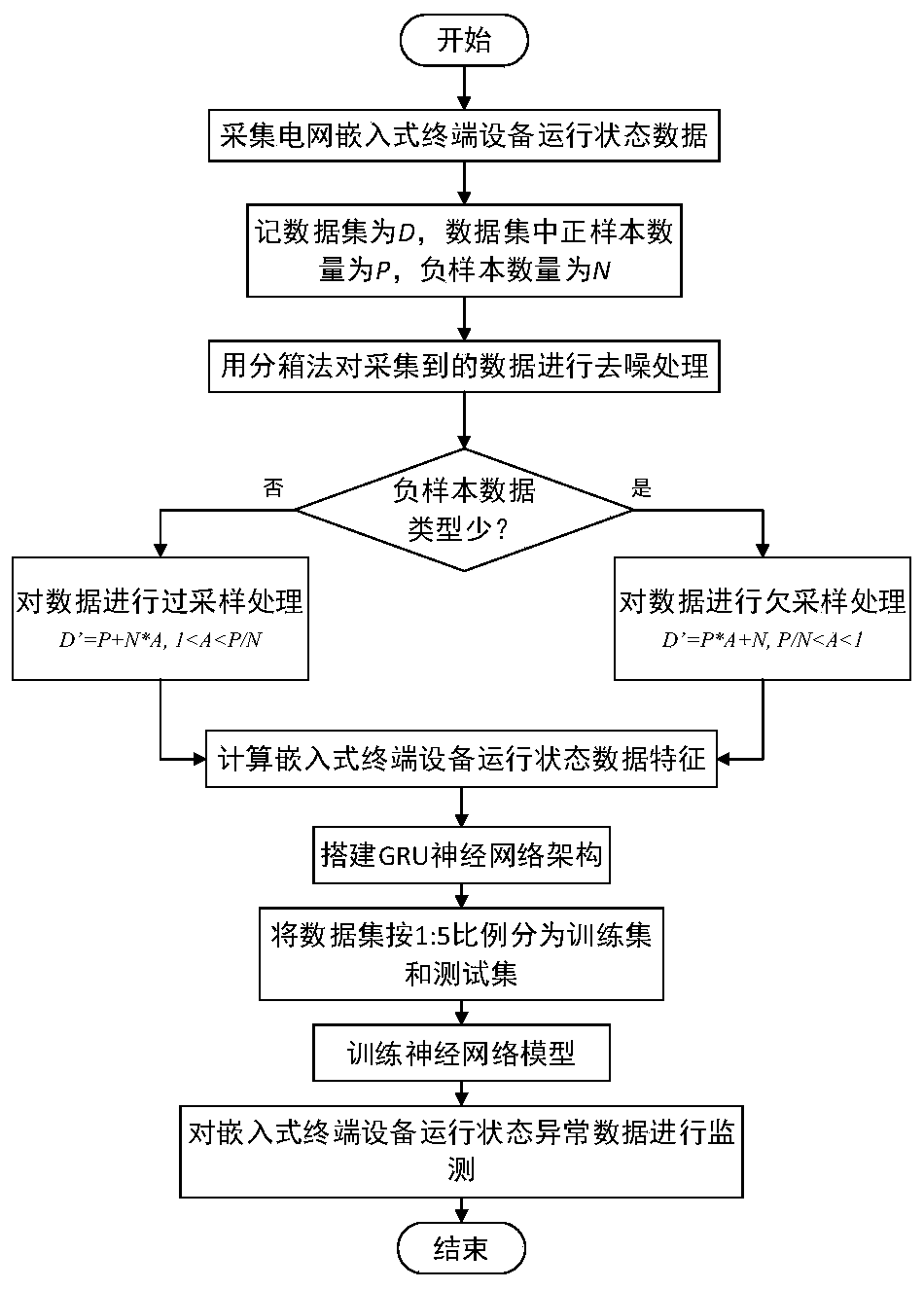
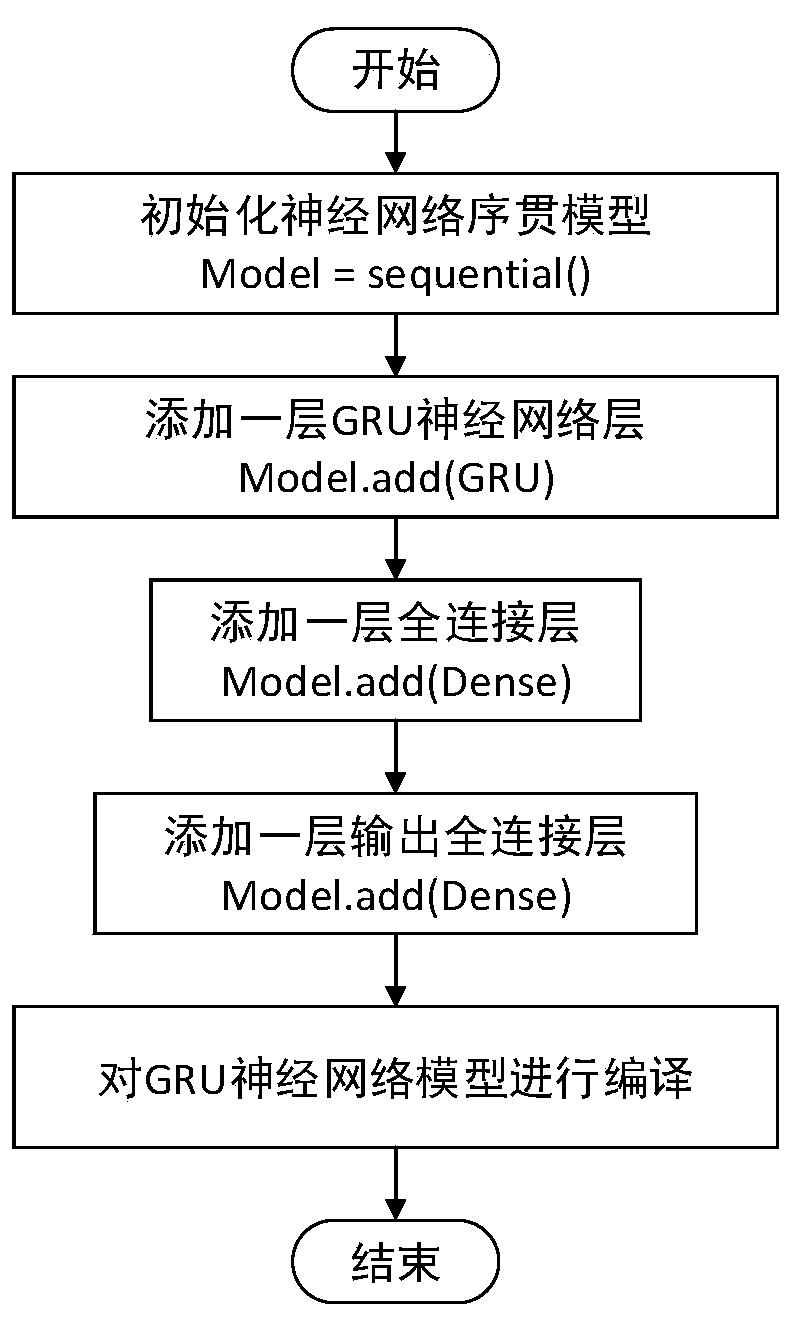
PendingCN111383128AImprove accuracyImprove robustnessData processing applicationsNeural architecturesTerminal equipmentPower grid
The invention discloses a method and system for monitoring the operation state of power grid embedded terminal equipment, and belongs to the technical field of intelligent power grid safety. The method comprises the following steps: acquiring historical operation data of the power grid embedded terminal equipment in different safety states; according to the collected historical operation data, determining operation characteristics representing the historical operation data of the power grid embedded terminal equipment in preset time; constructing a GRU neural network architecture according tothe operation features, dividing historical operation data into a training set and a test set, and inputting the training set and the test set into the GRU neural network architecture for training toobtain a training model; and acquiring operation data of the to-be-monitored power grid embedded terminal device, testing the operation data by using the training model, and determining an operation state of the to-be-monitored power grid embedded terminal device. According to the method, the accuracy of identifying the operation state of the power grid embedded terminal equipment is higher, and the robustness is higher.
Owner:CHINA ELECTRIC POWER RES INST +3
Power grid embedded terminal safety monitoring method and system based on side channel
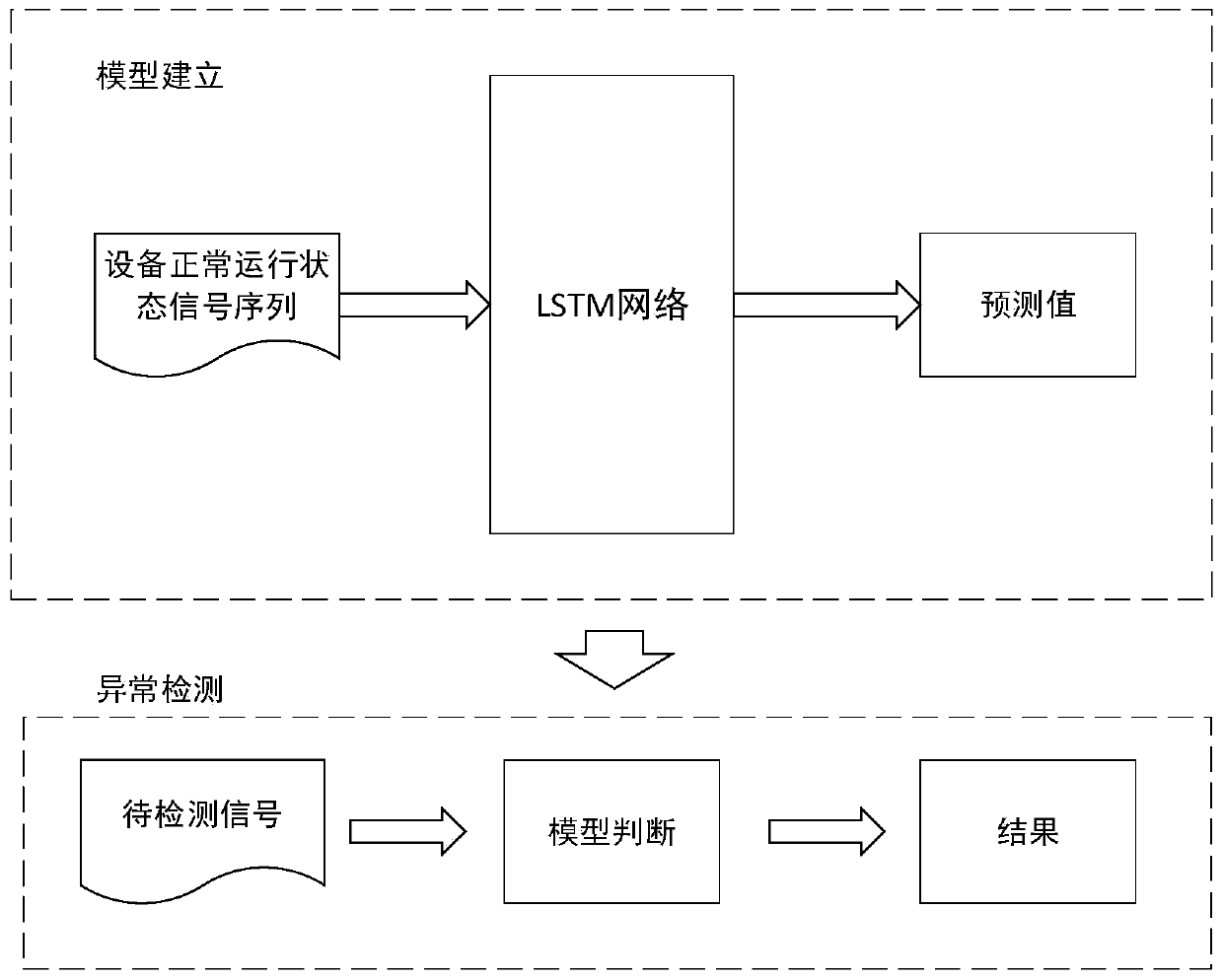
InactiveCN111030299AImprove securityMonitor running statusCharacter and pattern recognitionNeural architecturesState predictionData pre-processing
The invention discloses a power grid embedded terminal safety monitoring method and system based on a side channel, and belongs to the field of intelligent power grid safety. The method comprises thesteps of equipment operation state information acquisition, data preprocessing, feature extraction, equipment normal operation state model establishment, equipment next operation state prediction andequipment operation state anomaly detection. The operation state information of power grid embedded terminal equipment is classified, the power consumption is selected as state information when the equipment operates, and the operation state of the equipment is monitored in real time and compared with a normal operation state model of the equipment for analysis, so that whether the equipment operates abnormally or not is judged. According to the invention, the operation state of the power grid embedded terminal equipment can be monitored, and the safety performance of the terminal equipment isimproved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
Intelligent power grid safety communication method based on combined password
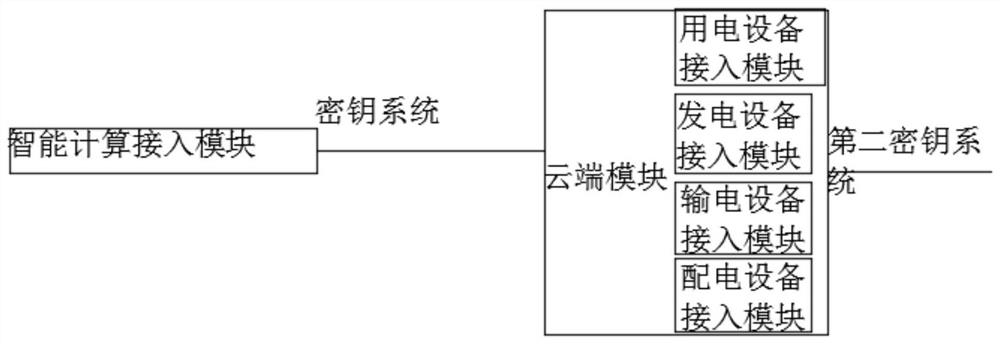
PendingCN112511490ASecure transmissionAchieve reliabilityKey distribution for secure communicationCircuit arrangementsSmart grid communicationConfidentiality
The invention relates to the technical field of telecommunication, in particular to an intelligent power grid safety communication method based on a combined password. The system comprises a pluralityof transfer stations, each transfer station is provided with an intelligent computing access module and a cloud module connected with the intelligent computing access module, and the intelligent computing access modules are used for acquiring information of power generation equipment, power transmission equipment, power distribution equipment and power utilization equipment and interacting the acquired information with the cloud modules. Each intelligent computing access module is correspondingly provided with a secret key system, and the cloud module is further connected with a second secretkey system. The method has the beneficial effects that the reliability, integrity, confidentiality and non-repudiation of information transmission are realized; the public key cryptosystem is used inthe smart power grid, so that the authentication and confidentiality of smart power grid communication are ensured, and the number of secret keys stored in the smart power grid is effectively reduced.
Owner:苏州达塔库自动化科技有限公司
Service regulation and control network security and credibility auditing method and system suitable for 5G network
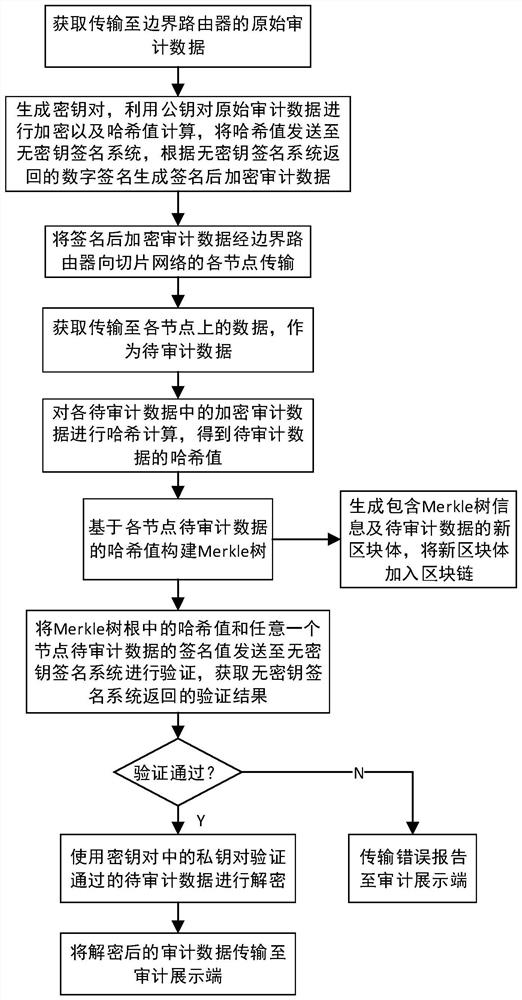
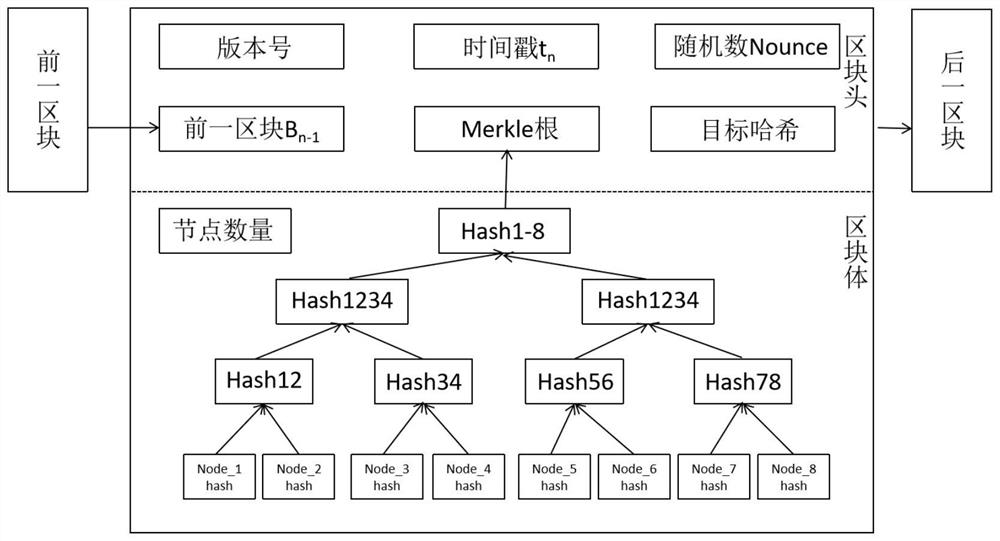
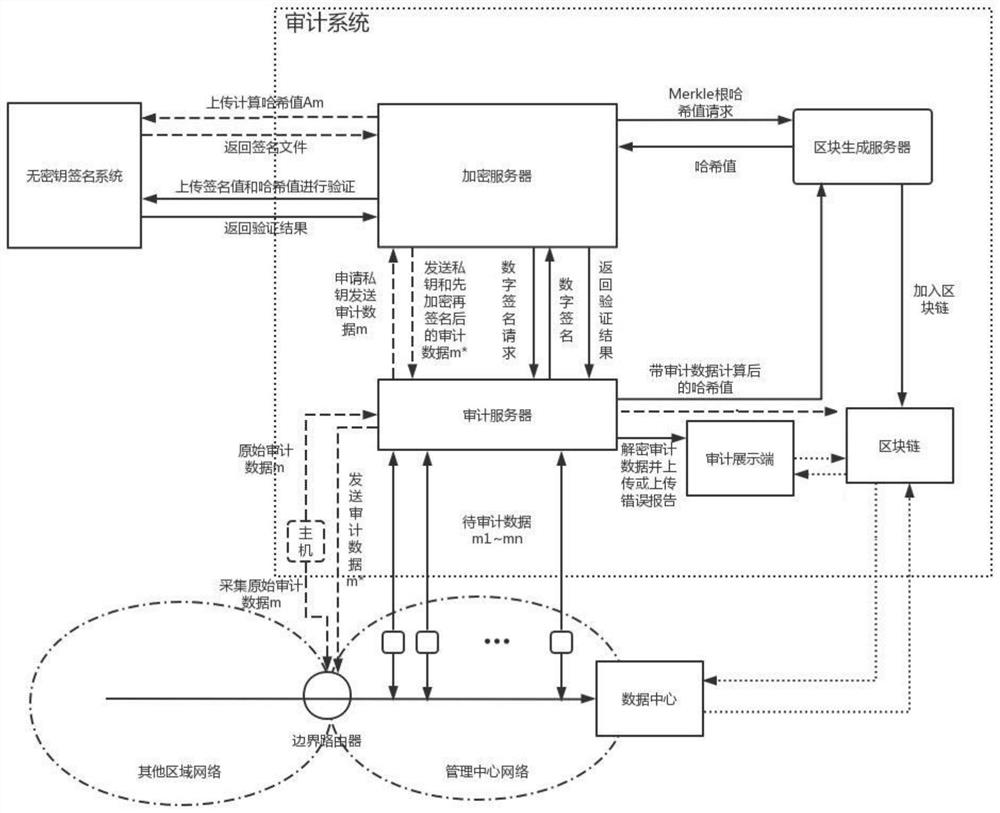
PendingCN114885325AQuick verificationGuaranteed privacySecurity arrangementInformation technology support systemTree rootEngineering
The invention discloses a regulation and control service network security credible auditing method and system suitable for a 5G network, and relates to the technical field of smart power grid security, and the method comprises the steps: obtaining original auditing data, carrying out the encryption and signature processing, and generating signed encrypted auditing data; transmitting the signed encrypted auditing data to each node of the management center slice network, and obtaining to-be-audited data transmitted to each node; performing hash calculation on the encrypted audit data in the to-be-audited data to obtain hash values; constructing a Merkle tree on the basis of the obtained hash value; acquiring a hash value in the Merkle tree root and a signature value in the to-be-audited data on any node, performing verification processing, and if verification is passed, decrypting encrypted audit data in the to-be-audited data to obtain original audit data and outputting the original audit data; and if the verification is not passed, outputting auditing error information. According to the method, the credibility and tamper-proofing of the network audit data can be ensured, and the accuracy and consistency of node data are ensured.
Owner:STATE GRID ELECTRIC POWER RES INST +3
Intrusion detection method and system based on IEC61850 SV message operation situation model
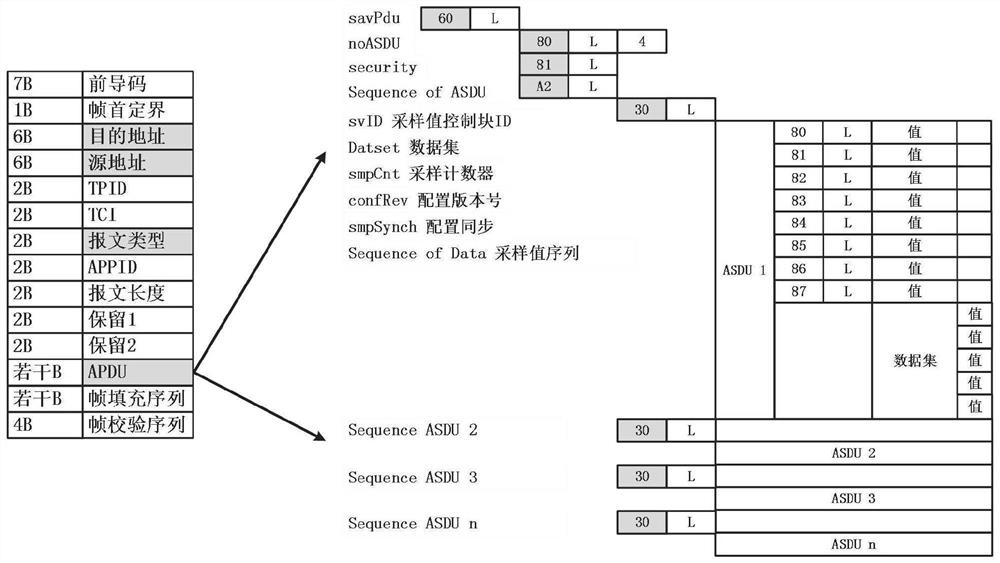
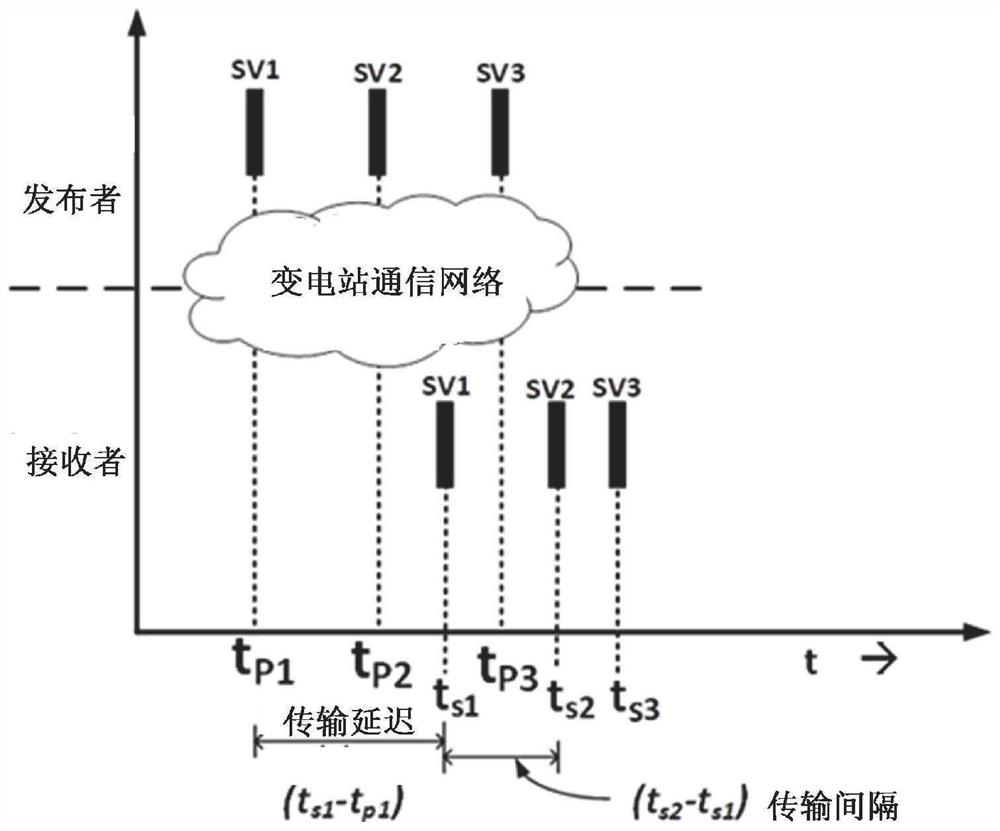
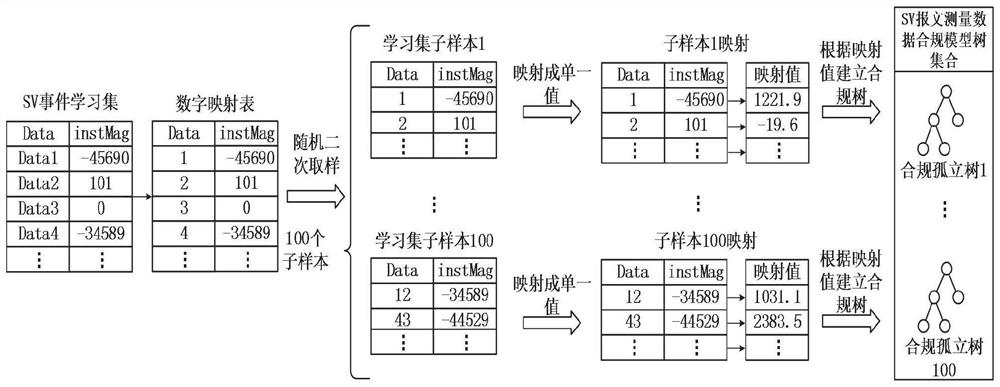
PendingCN114697081ARealize real-time detectionAddress limitationsMachine learningSecuring communicationSmart substationPower grid
The invention relates to the technical field of intelligent power grid safety, and discloses an intrusion detection method and system based on an IEC61850 SV message operation situation model, and the method comprises the steps: collecting various measurement value data in an SV message at each position in an intelligent substation system in a certain time period, providing the data for a machine learning algorithm for training and learning, and employing a machine learning technology to achieve the intrusion detection of the SV message at each position in the intelligent substation system. And constructing a data compliance model of the power grid system based on an SV message measurement value by learning the power grid behavior of a normal SV data message. The data compliance model constructed by using the measured value data of the SV message is used for detecting the abnormal SV message of the IEC61850 system, and real-time detection of various intrusion behaviors is realized. Compared with the prior art, the method has the advantages that the limitation and the inapplicability of the IEC62351 in the actual use process are solved.
Owner:国网江苏省电力有限公司淮安供电分公司 +2
Error data injection attack defense method based on PMU deployment in smart power grid
The invention relates to an intelligent power grid safety technology, in particular to an error data injection attack defense method based on PMU deployment in an intelligent power grid. The method comprises three stages of a new low-overhead hybrid attack mechanism, PMU pre-deployment of fragile nodes and PMU-based greedy strategy deployment of the whole network. In a stage of a new low-overheadhybrid attack mechanism, an attacker can attack a bus with low smart grid connectivity with low overhead to cause an error state estimation result. In a PMU pre-deployment stage of a fragile node, firstly, a bus which is most easily attacked is protected through PMU deployment. And in a PMU greedy strategy-based deployment stage of the whole network, according to the current attack vector, a PMU device is deployed on a bus capable of protecting the maximum number of measurement values in each round of deployment until the whole power grid is completely observable. According to the defense method provided by the invention, the attack overhead of an attacker is increased, and the deployment iteration process is reduced; after deployment is completed, effective defense of an error data injection attack is realized.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
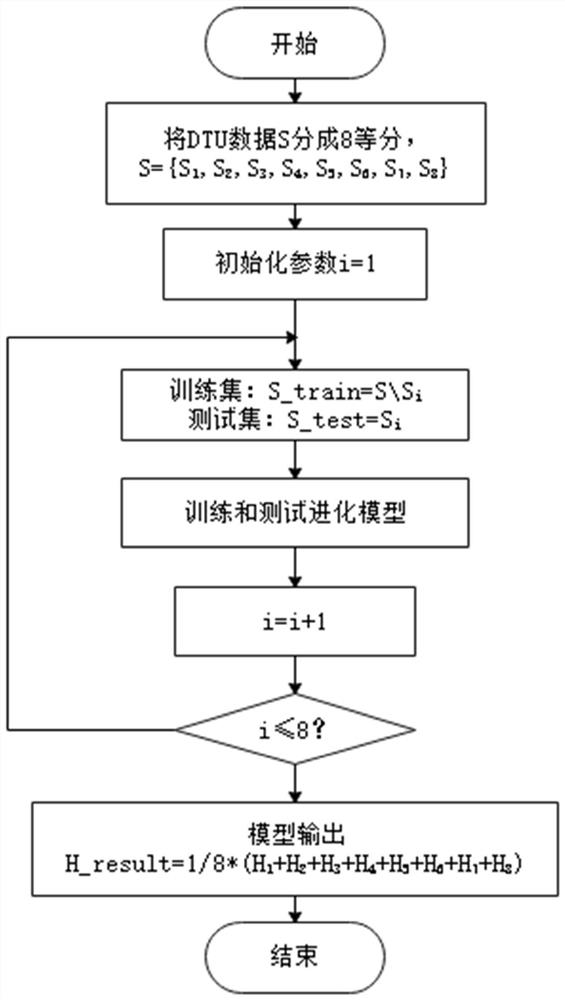
Method and system for intrusion detection of distribution terminal unit (DTU) based on machine learning
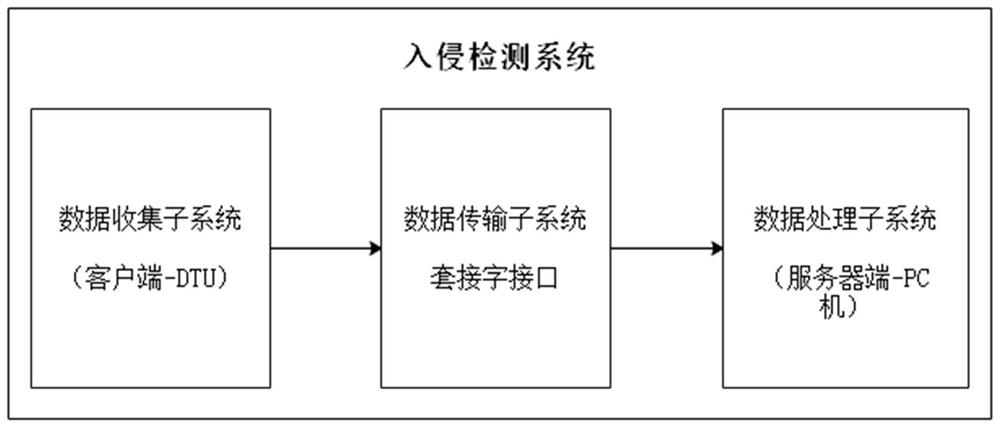
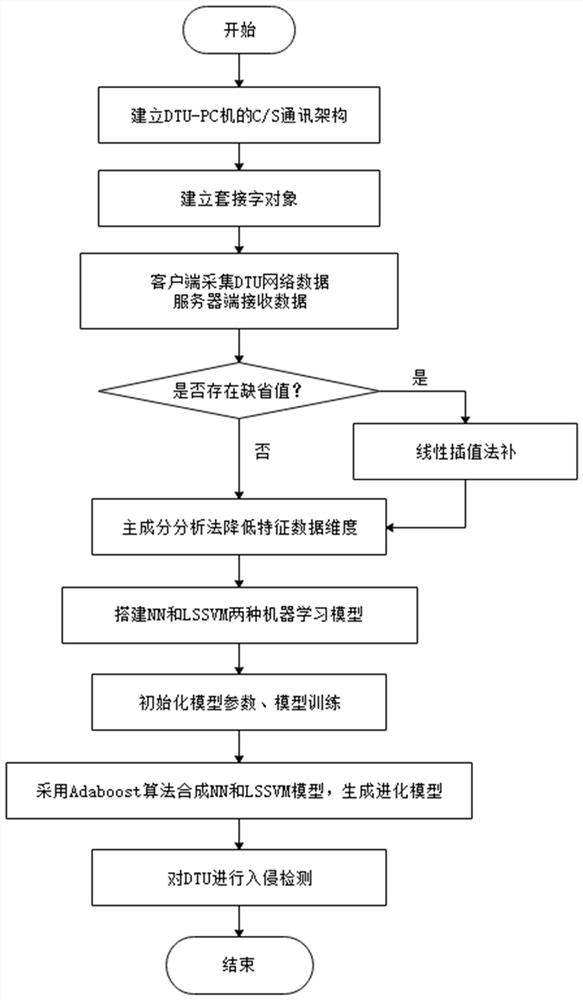
ActiveCN112187820AShort answer structureFast operationCharacter and pattern recognitionNeural architecturesPrincipal component analysisLeast squares support vector machine
The invention discloses a method and system for intrusion detection of a DTU based on machine learning, belonging to the field of intelligent power grid security. The method comprises the following steps: port identification, data acquisition, transmission, data processing and dimension reduction of the DTU, construction of a classifier based on a neural network and a least square support vector machine, an intrusion behavior detection experiment of the DTU, and timely sounding of an alarm when abnormity occurs. According to the invention, high-dimensional feature data are reduced by adoptinga principal component analysis method, and then a model is established by utilizing features after dimension reduction; secondly, dual verification is performed by adopting the least square support vector machine and a neural network algorithm so as to improve detection accuracy and reduce a false alarm rate; and finally, the framework of the intrusion detection system adopts a modular design, sothe system is suitable for intrusion detection in the field of intelligent power grids, and is good in portability and universality.
Owner:SHENZHEN POWER SUPPLY BUREAU +2
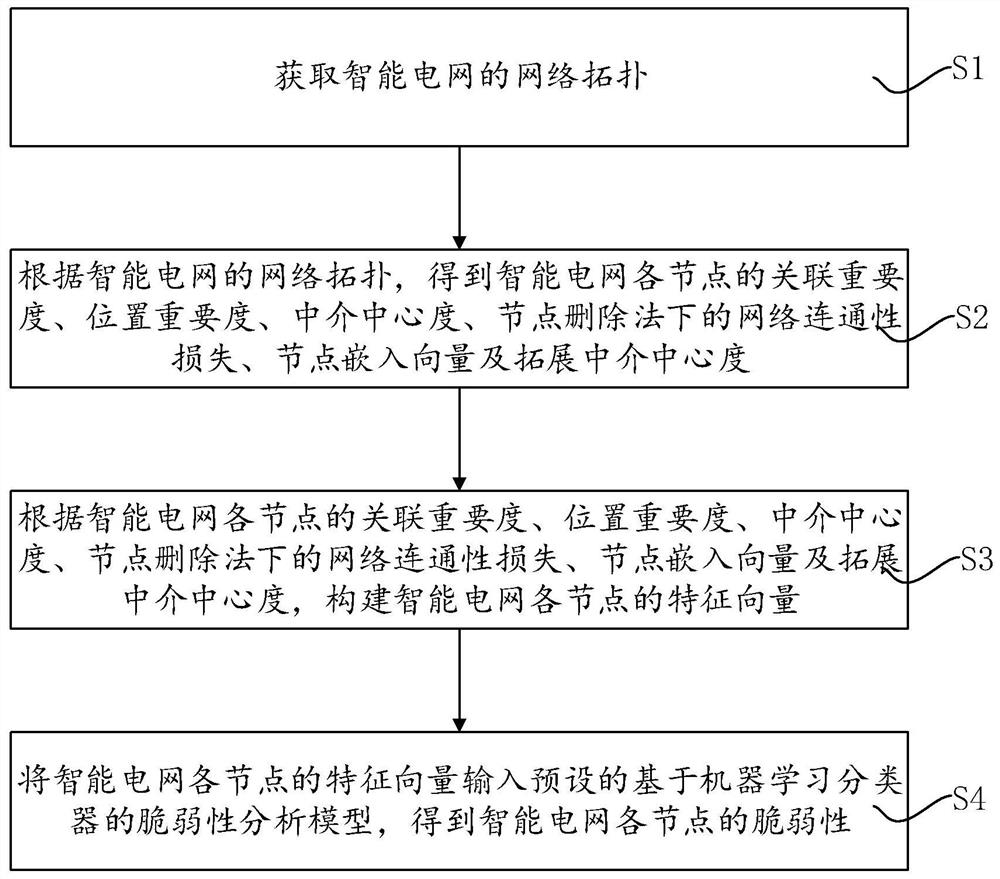
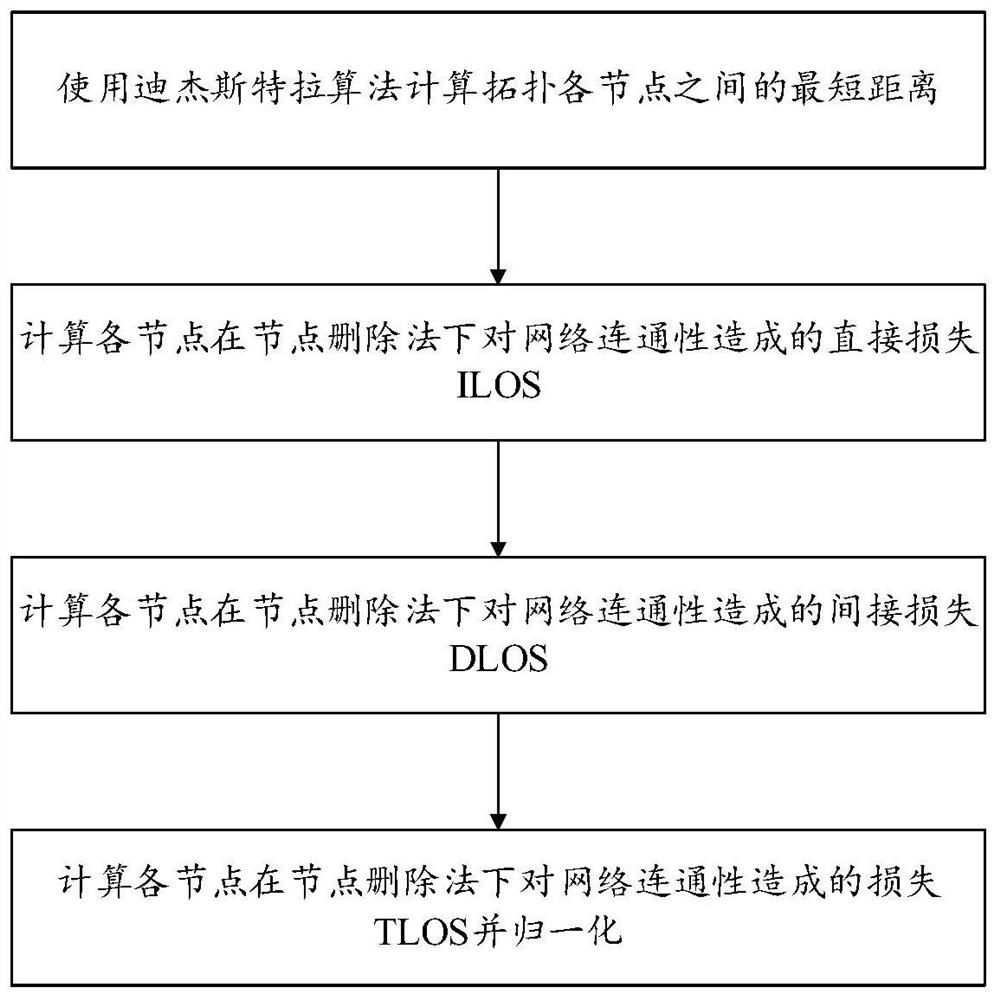
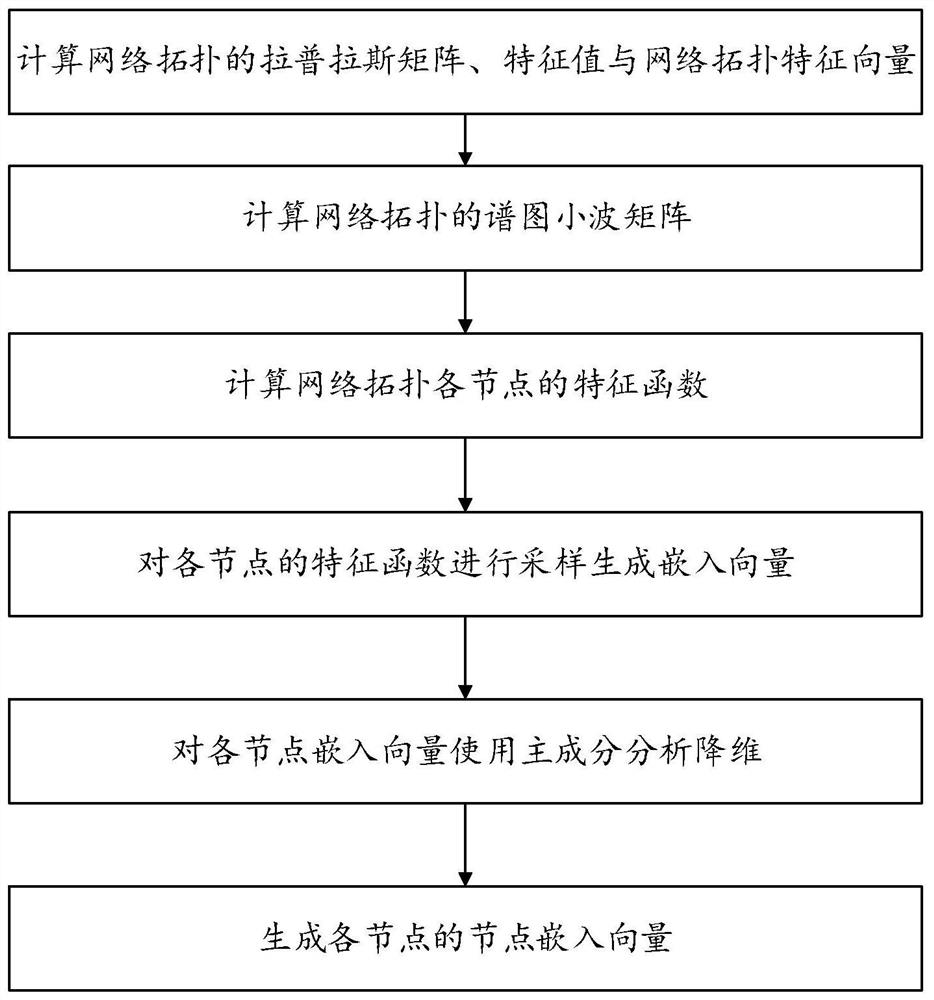
Smart power grid node vulnerability assessment method, system and device, and storage medium
PendingCN113094975AVulnerability responseComprehensive and precise analysisCharacter and pattern recognitionDesign optimisation/simulationComputation complexityPower grid
The invention belongs to the field of smart power grid safety, and discloses a smart power grid node vulnerability assessment method, system and device, and a storage medium, and the method comprises the steps: obtaining the network topology of a smart power grid; according to the network topology of the smart power grid, obtaining the association importance, the position importance, the mediation centrality, the network connectivity loss under a node deletion method, the node embedding vector and the expansion mediation centrality of each node of the smart power grid; according to the association importance degree, the position importance degree and the mediation centrality of each node of the smart power grid, the network connectivity loss under a node deletion method, the node embedding vector and the expansion mediation centrality, constructing a feature vector of each node of the smart power grid; and inputting the feature vector of each node of the smart power grid into a preset vulnerability analysis model based on a machine learning classifier to obtain the vulnerability of each node of the smart power grid. The analysis accuracy of the node vulnerability is greatly improved, the method does not depend on a complex fault model any more, the expansibility is very high, and the calculation complexity is reduced.
Owner:XI AN JIAOTONG UNIV
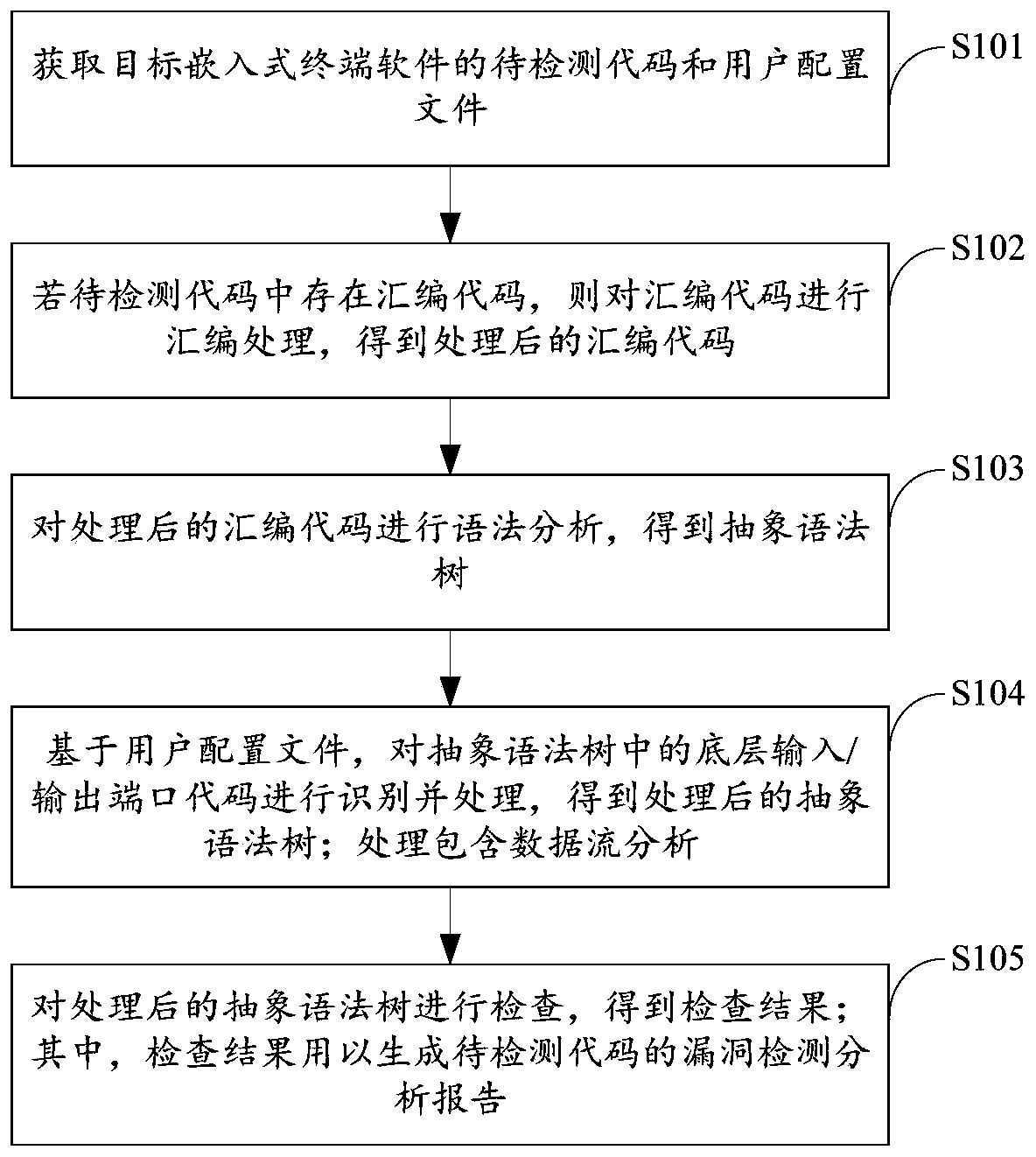
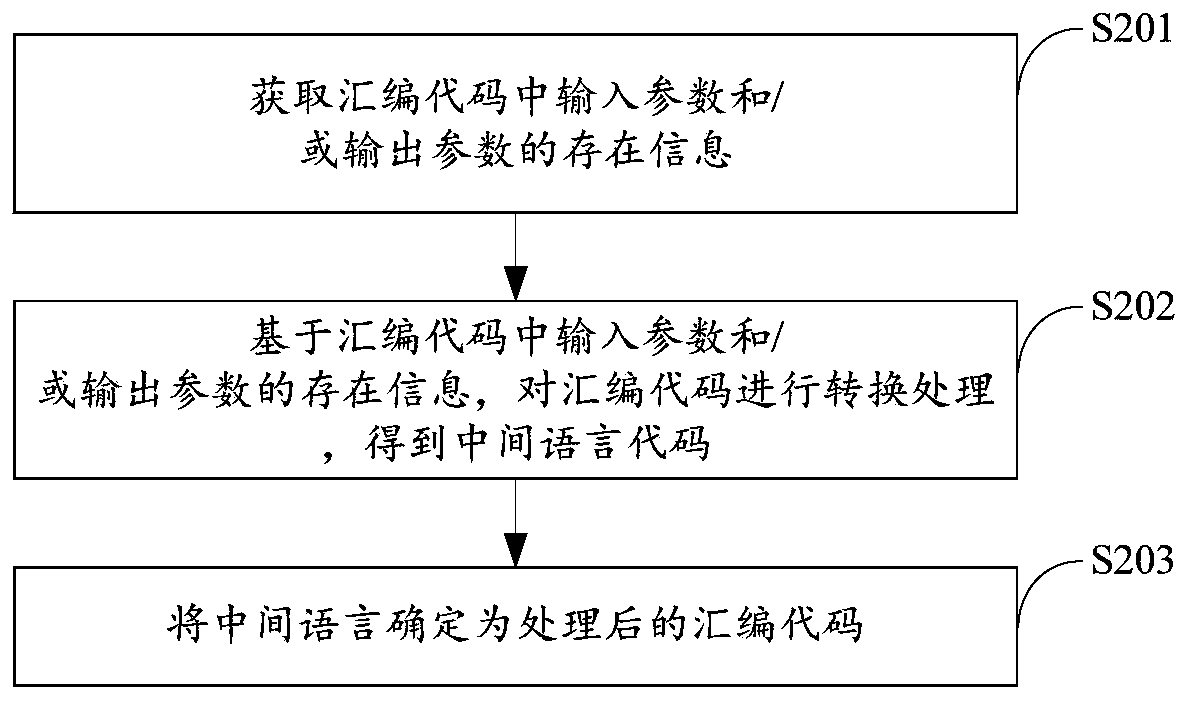
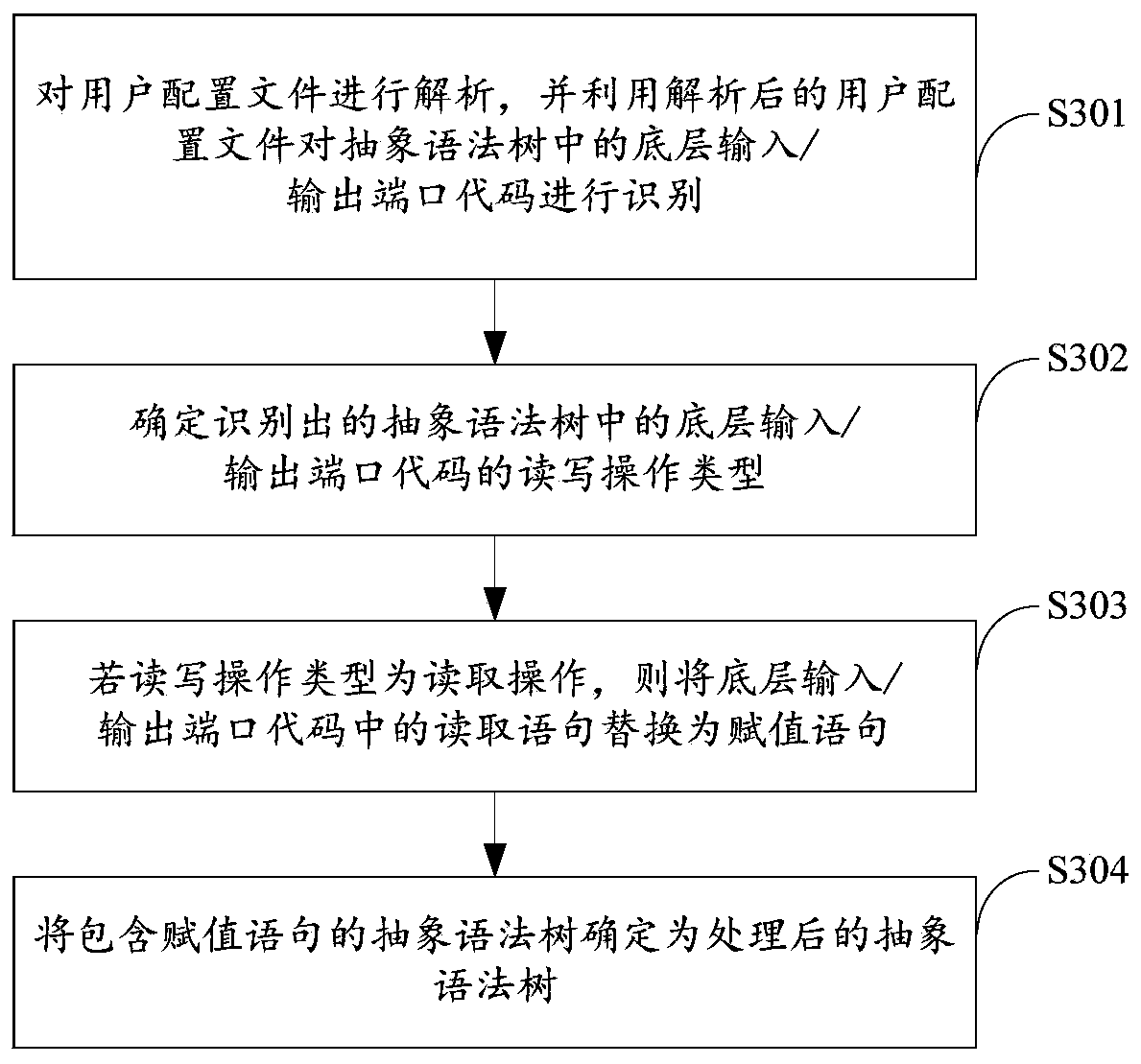
Embedded terminal software code vulnerability detection method and device based on model inspection
ActiveCN111552968AVulnerability detection worksPlatform integrity maintainanceEnergy efficient computingData streamAbstract syntax tree
The invention provides an embedded terminal software code vulnerability detection method and device based on model check, and relates to the technical field of intelligent power grid security. The method comprises the steps: firstly obtaining a to-be-detected code and a user configuration file of target embedded terminal software; if the assembly code exists in the to-be-detected code, performingassembly processing on the assembly code to obtain a processed assembly code; carrying out grammatical analysis on the processed assembly code to obtain an abstract syntax tree; based on the user configuration file, identifying and processing a bottom layer input / output port code in the abstract syntax tree to obtain a processed abstract syntax tree; wherein the processing comprises data flow analysis; and finally, checking the processed abstract syntax tree to obtain a checking result. The check result is used for generating a vulnerability detection analysis report of the to-be-detected code. The technical problem that an existing vulnerability detection method is only suitable for common software and cannot be suitable for embedded terminal software codes is solved.
Owner:CHINA ELECTRIC POWER RES INST +3
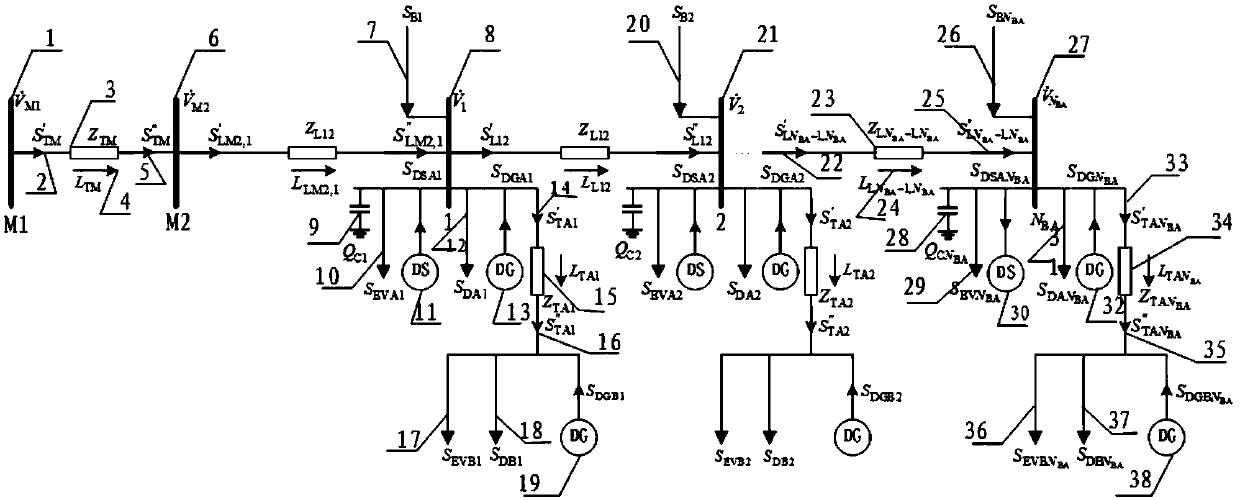
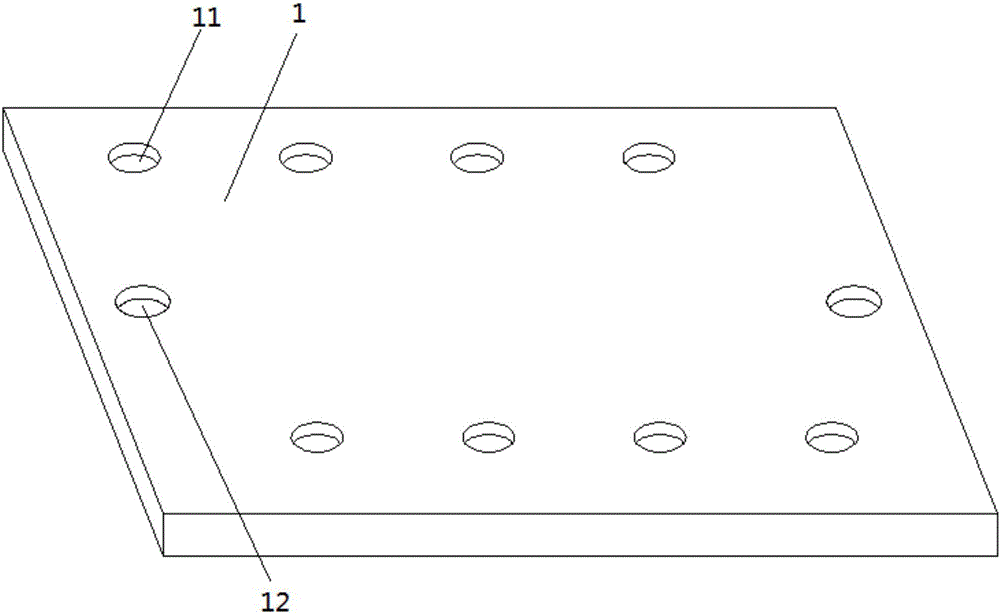
Intelligent electric network safe transmission electric pole tower
InactiveCN106711631AIncrease the effective contact areaReduce drag effectTowersConnection contact member materialElectrical resistance and conductanceIron powder
The invention discloses an intelligent electric network safe transmission electric pole tower, which comprises a pasting plate, a pole tower main body and an inclined monitor, wherein the pasting plate is a square plate; the device is characterized in that a protection device consisting of a magnetic ring and a water proof sealing disc is arranged in a grounding hole and a support frame hole, so that the performance influence due to water entering the grounding hole or the support frame hole can be avoided; the vicious pulling of a jacking screw bolt and a grounding module can be avoided through the arrangement of the magnetic ring; the self safety is improved; fine iron powder coats the surface of the grounding module, so that the effective contact area of the grounding module and the ground can be greatly increased; in addition, a whole with good contact with the ground can be formed; further, the contact resistance of the grounding module and the ground is greatly reduced, so that the resistance reduction effect of the grounding module is sufficiently achieved; the use area of a grounding device is greatly reduced; the inclination condition of the pole tower main body in the installation process is monitored by the inclined monitor; when the tower body is inclined, a remote warning signal is sent out in time to notify staff in an electric power department; the normal operation of a whole electric network is effectively ensured.
Owner:HEFEI LONGTUTEM INFORMATION TECH CO LTD
Multi-agent optimized coordination control method of electric network
InactiveCN101777769BRealize intelligent unmanned schedulingGuaranteed economic dispatchAc networks with different sources same frequencyMicrogridPower grid
The invention relates to a multi-agent optimized coordination control method of an electric network in the technical field of electric networks, which comprises the following steps of: collecting local electric information, transmitting the local electric information to a central agent of a microgrid and issuing a control command by a local electric network to the central agent of the microgrid simultaneously; computing by a grid technology; issuing a new control command by the central agent of the microgrid and transmitting the information to a regulation agent of the local electric network by a network line simultaneously; receiving a dispatching instruction of the central agent of the microgrid by the agent of each element and carrying out logical judgment on a result executing these dispatching commands according to the collected local electric information; and meanwhile, optimizing the electric network within a control range by the regulation agent of the local electric network and controlling a computer to carry out parallel computation by the grid technology. The invention is suitable for carrying out optimal dispatching on a distributed energy resource of an intelligent electric network, can control each power supply by an optimization scheme, also enhances the operational processing time greatly and ensures that the intelligent electric network runs safely, stably andeconomically.
Owner:SHANGHAI JIAOTONG UNIV
A threshold proxy signature method without trusted pkg based on smart grid identity security
ActiveCN104079412BImprove execution efficiencyWith confidentialityUser identity/authority verificationPrecomputationIdentifiability
Provided is a trusted PKG-free threshold proxy signature method based on the identity safety of a smart power grid. According to the signature method, a signer interacts with a PKG and then obtains a private key pair (xid, yid) and a public key pair (Xid, Yid) of the PKG; proxy signers are authorized according to a verifiable secret sharing scheme, and it is supposed that P1, P2, ... , Pt are the t proxy signers, the t proxy signers will cooperate to generate a proxy signature of a message m; each proxy signer Pi generates a proxy signature part and sends the proxy signature part to a verifier C, and if all the proxy signature parts pass verification, the C combines the proxy signature parts into a valid threshold proxy signature. The method has higher execution efficiency due to many steps of precomputation and guarantees the security features of privacy, proxy protection, unforgeability, non-repudiation, strong identifiability and the like of the valid threshold proxy signature.
Owner:GANSU ELECTRIC POWER DESIGN INST
False data injection attack defense method based on pmu deployment in smart grid
The invention relates to smart grid security technology, in particular to a method for defending against wrong data injection attacks based on PMU deployment in the smart grid. The method includes three stages: a new low-overhead hybrid attack mechanism, PMU pre-deployment on vulnerable nodes, and PMU-based greedy strategy deployment for the entire network. In the stage of the new low-overhead hybrid attack mechanism, the attacker can use lower overhead to attack the busbar with a small connection degree of the smart grid to cause wrong state estimation results. In the PMU pre-deployment phase of vulnerable nodes, the most vulnerable bus is firstly protected through PMU deployment. In the deployment phase of the entire network based on the PMU greedy strategy, according to the current attack vector, a PMU device is deployed on the busbar that can protect the maximum number of measured values in each round of deployment until the entire power grid is fully observable. The defense method proposed by the invention enables the attacker to increase the attack cost, and at the same time reduces the deployment iterative process, and realizes the effective defense against the wrong data injection attack after the deployment is completed.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com