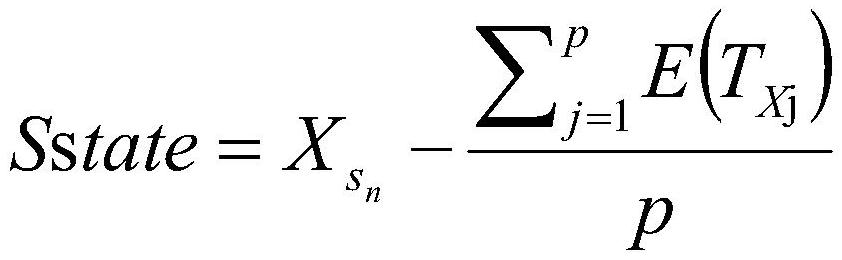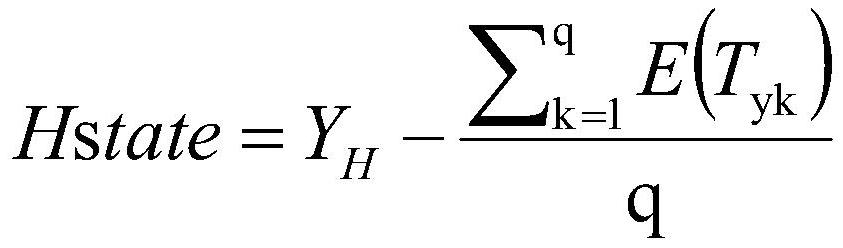Detection method for selfish mining behaviors on workproof mechanism block chain
A technology of proof mechanism and detection method, which is applied in the field of blockchain network, can solve the problems of wasting computing power, declining income of honest miners, increasing costs, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] In order to make the objectives, technical solutions, and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with specific embodiments and with reference to the accompanying drawings. It should be understood that these descriptions are only exemplary and not intended to limit the scope of the present invention. In addition, in the following description, descriptions of well-known structures and technologies are omitted to avoid unnecessarily obscuring the concept of the present invention.
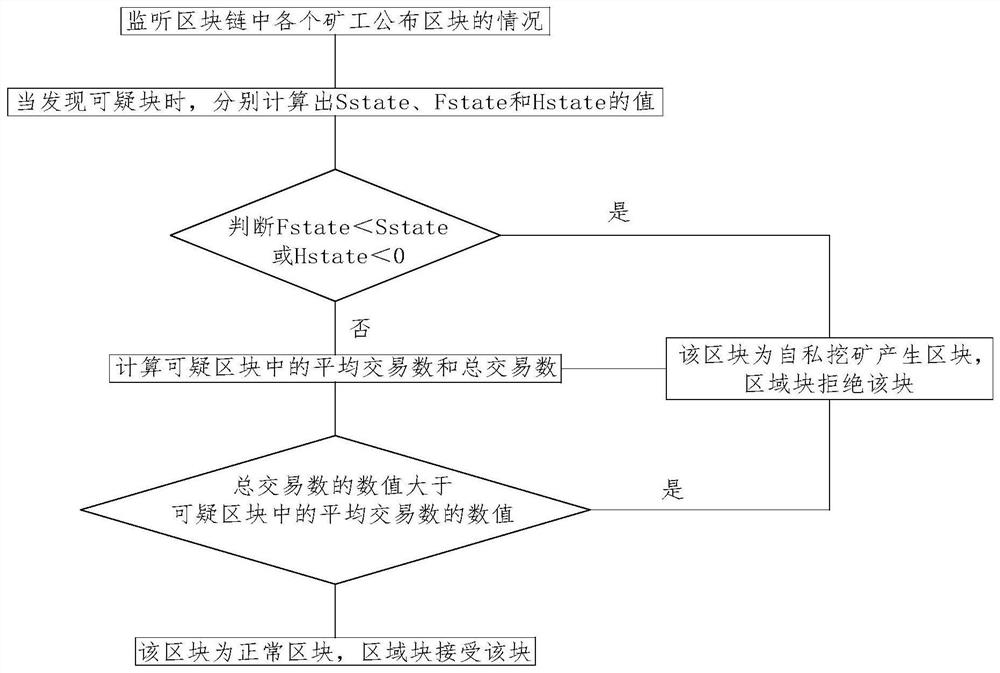
[0045] Such as figure 1 As shown, the detection method for selfish mining behavior on the blockchain of the proof-of-work mechanism proposed by the present invention includes the following specific steps:
[0046] S1. Monitor the status of the block announced by each miner in the blockchain;
[0047] S2. When it is monitored that miner A has announced a chain whose block height is at least two blocks higher than tha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com