Safe access method and system of network ports
A network port and secure access technology, applied in the field of information security software, can solve problems such as inconvenient access, inaccessibility, and inability to access TCP3389 port, etc., and achieve the effect of reducing network security risks and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The technical solution of the present invention will be specifically described below in conjunction with the accompanying drawings.
[0022] The invention provides a method for securely accessing a network port, comprising the following steps:
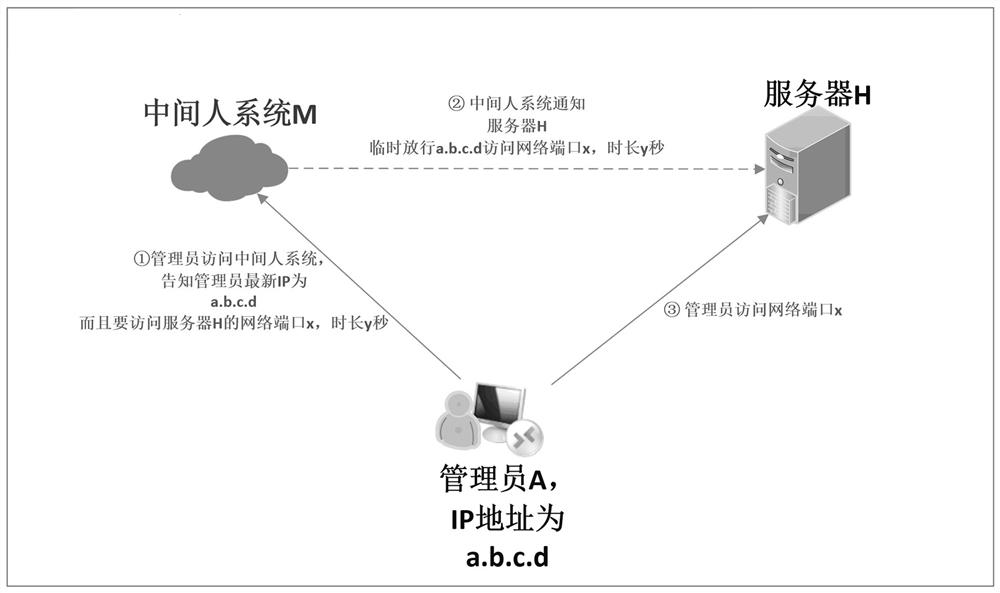
[0023] Step S1, providing server H and intermediary system M;
[0024] Step S2, a network filter driver is installed on the server H to protect the specified network port on the server H, the network filter driver refuses any IP access to these protected network ports by default, only when the middleman system M When a notification is sent, the network filter driver temporarily allows the IP required by the notification to access the network port required by the notification;
[0025] Step S3, the administrator A visits the intermediary system M, and requests the intermediary system M to send a notice to the network filter driver on the server H to temporarily allow the corresponding IP address of the administrator A to access ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com