Webshell killing-free method based on random character exclusive-OR operation
A technology of random characters and characters, applied in the field of webshell avoidance based on the XOR operation of random characters, can solve the problem of reducing the attack efficiency of the attacker, and achieve the effect of improving the quality of personnel, protecting network security, and improving attack efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
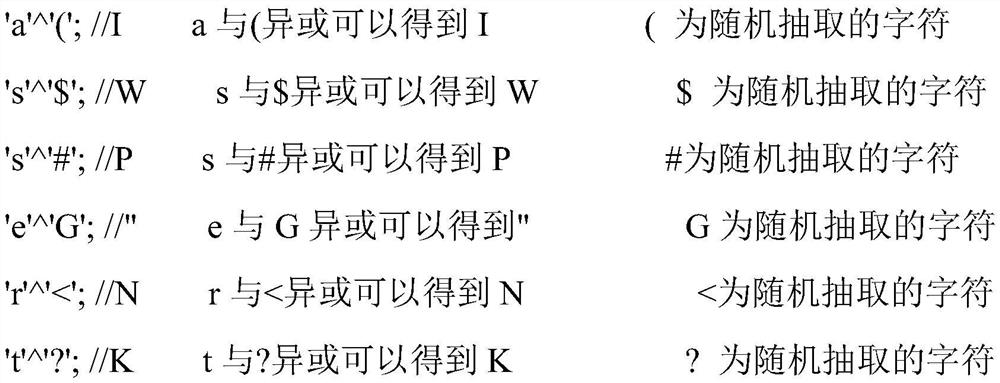
[0019] A webshell avoidance method based on XOR operation of random characters. Sensitive keywords concerned by the scanning and killing system are represented by character characters, and webshell files of PHP scripts are constructed, so that the killing system cannot obtain sensitive keywords through character kill system monitoring.
[0020] The representation characters are different from the expression characters constituting the sensitive keywords. The representation characters contain an exclusive-or relationship, and the expression characters of the sensitive keywords are obtained after the calculation of the exclusive-or relationship in the representation characters.
[0021] The anti-virus system refers to anti-virus software or website application-level intrusion prevention system. During the defense process, anti-virus software usually checks sensitive keywords. If there are sensitive keywords in the file, it is considered that there is a network security risk, and...
Embodiment 2
[0052] A webshell avoidance method based on XOR operation of random characters, other features are the same as in Embodiment 1, the difference lies in: the way of constructing webshell avoidance file through XOR operation is different.
[0053] Each character in the sensitive keyword is obtained by XORing the characters. Taking eval as an example, in this embodiment, two character representations of "e", "v", "a", and "l" that can be obtained through XOR operation are randomly selected sequentially to construct a PHP webshell file.
[0054] Since there are multiple groups of character pairs that can obtain "e" through XOR operations, and multiple groups of character pairs that can obtain "v" through XOR operations, ..., therefore, the method of constructing sensitive keywords expressed through XOR relations There are many kinds, and there is randomness. Therefore, the forms of the PHP webshell files constructed at different times are various, and there is diversity and random...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com