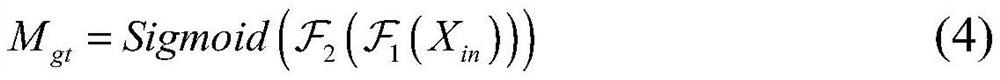Image tampering detection method, terminal equipment and storage medium
A tampering detection and image technology, applied in image enhancement, image analysis, image data processing and other directions, can solve the problems of accuracy limitation, weak positioning ability, inappropriate tampering detection, etc., to achieve the effect of improving performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
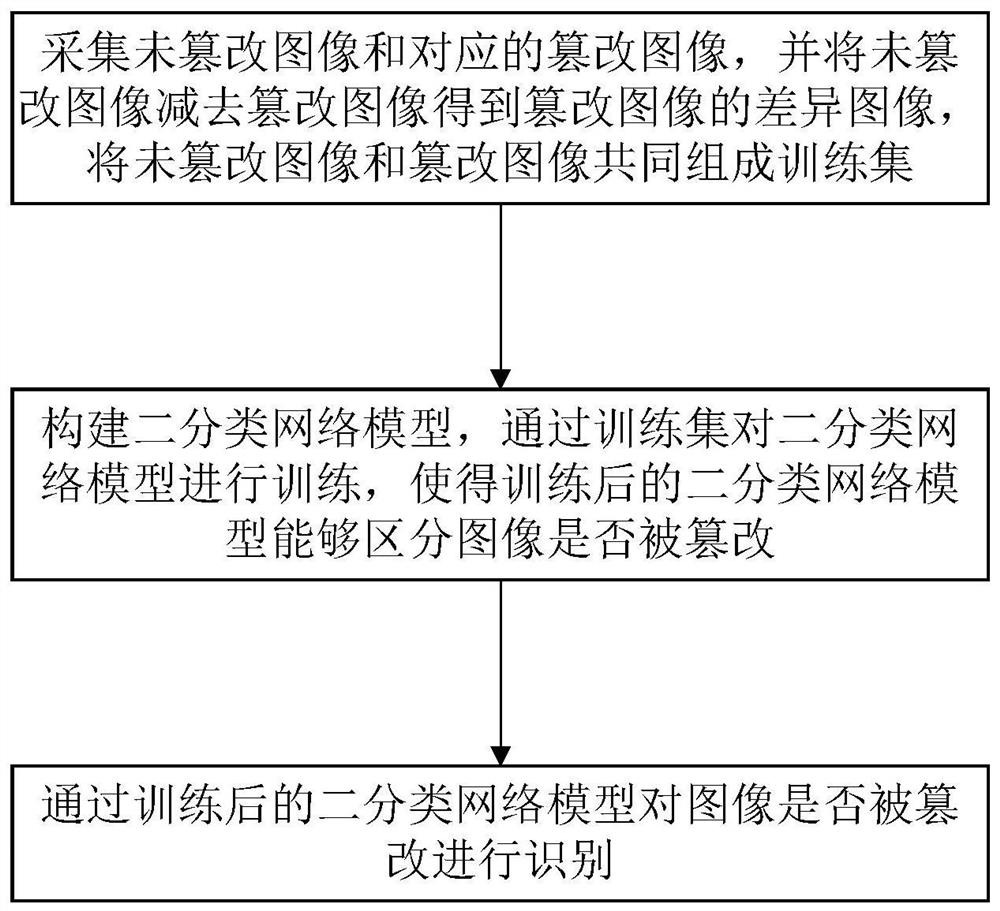
[0031] An embodiment of the present invention provides a method for detecting image tampering, such as figure 1 As shown, the method includes the following steps:
[0032] S1: Collect the untampered image and the corresponding tampered image, subtract the tampered image from the untampered image to obtain the difference image of the tampered image, and combine the untampered image and the tampered image together to form a training set.
[0033] In order to improve the generalization ability of the model, so that the model learns the discriminative features that can better identify the untampered image and the tampered image, in this embodiment, the tampered image uses a variety of tampering methods, such as face attribute operation, copy-paste, human Face synthesis, identity transformation, etc., make the training set contain many different types of tampered images.
[0034] In this embodiment, the difference image is generated in the following manner:
[0035] Use the face ...
Embodiment 2
[0071] The present invention also provides an image tampering detection terminal device, including a memory, a processor, and a computer program stored in the memory and operable on the processor, and the present invention is realized when the processor executes the computer program Steps in the above method embodiment of Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com