Fraudulent user detection model construction method based on graph attention network
A technology for detecting models and construction methods, applied in biological neural network models, neural learning methods, neural architectures, etc., can solve the problem of inability to further extract structural information, inability to automatically select user feature combinations, inability to extract global information about user-related information, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] In order to make the purpose of the present invention, technical solutions and advantages clearer, the present invention will be further described in detail below in conjunction with the examples:
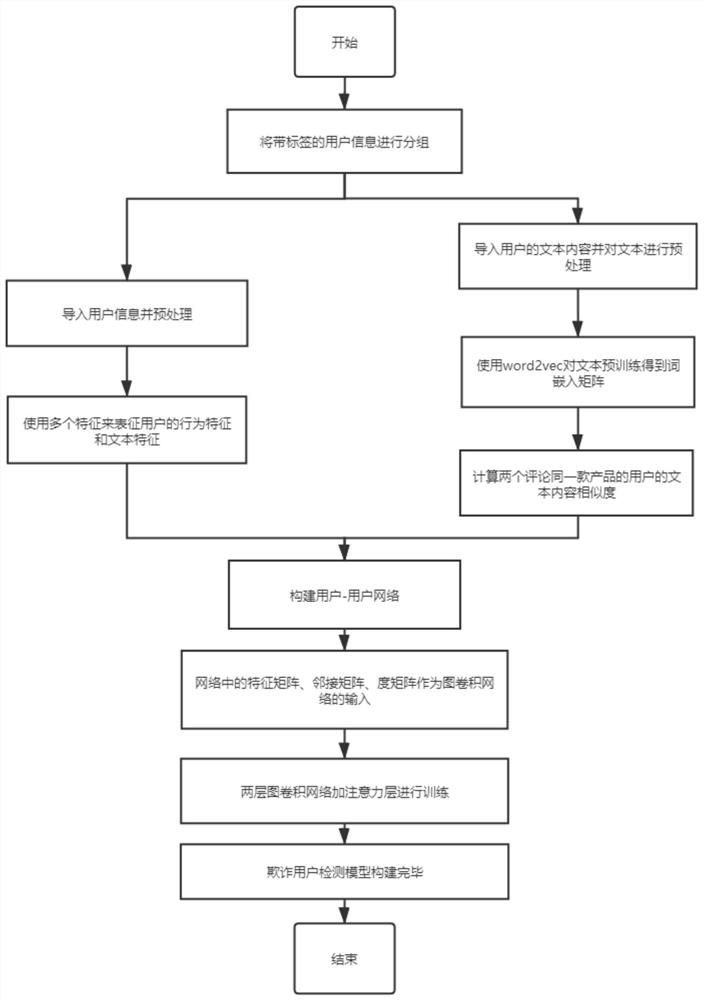
[0057] A method for constructing a fraudulent user detection model based on a graph attention network, comprising the following steps:
[0058] Step 1) Group all the information in the labeled user information dataset by product, and generate a dataset whose fields are product id, comment user id, and comment content.
[0059] Step 2) Import user information and perform preprocessing, use several features to describe the user's behavioral features and text features, so as to represent the user's commenting behavior.
[0060] Step 21) process the user information data set in step 1), extract 8 user behavior features and 4 text features, including the following steps Table 1 and Table 2;
[0061] Table 1: Based on user behavior characteristics
[0062] feature de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com