Application layer traffic speed limiting method, terminal equipment and storage medium
An application layer and flow technology, applied in the field of communication, can solve problems such as inability to protect bandwidth, waste human resources, affect applications, etc., and achieve the effect of preventing network storms and protecting bandwidth resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
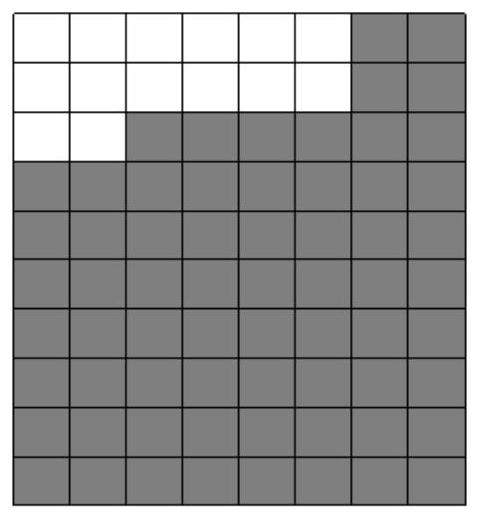
[0026] In this embodiment, the allowed bandwidth is divided into multiple shares, and each share represents a bandwidth of 1 KB. Such as figure 1 As shown, the allowable bandwidth is divided into 80 parts, that is, 8*10 squares, white means used, gray means idle, then from figure 1 It can be obtained from , the system speed limit is 80KB / s, 14KB has been used, and one unit corresponds to 1KB.
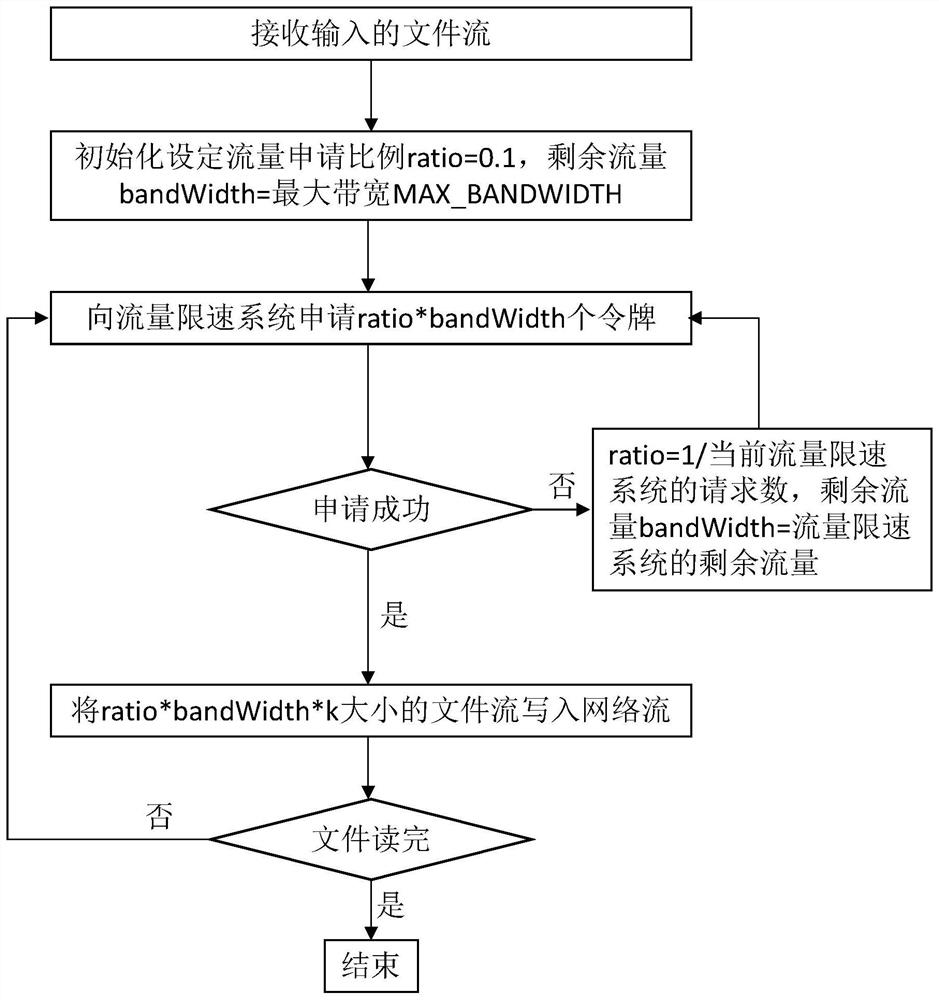
[0027] The traffic used when the application layer transfers files needs to apply for a token first, and then apply for a buffer according to the number of tokens when the token application is successful, and then flush the bit stream of the buffer to the network output stream.
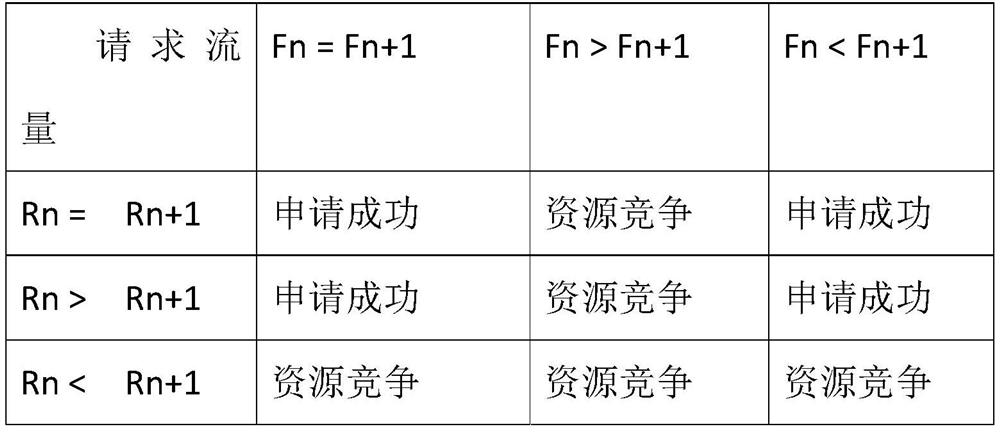
[0028] In order to make full use of the bandwidth, the number of tokens applied for each time is not fixed. The number of tokens applied for is mainly determined by two values, namely: a. the maximum value maxBandwith allowed by the flow rate limiting system; b. the application buffer size, buffer A zone that...
Embodiment 2
[0057] The present invention also provides an application-layer flow rate limiting terminal device, including a memory, a processor, and a computer program stored in the memory and operable on the processor, and the computer program is implemented when the processor executes the computer program. Steps in the above method embodiment of Embodiment 1 of the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com