Code verification method and device
A verification method and code technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as increasing the running time of debugging code and destroying the integrity of code segments
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
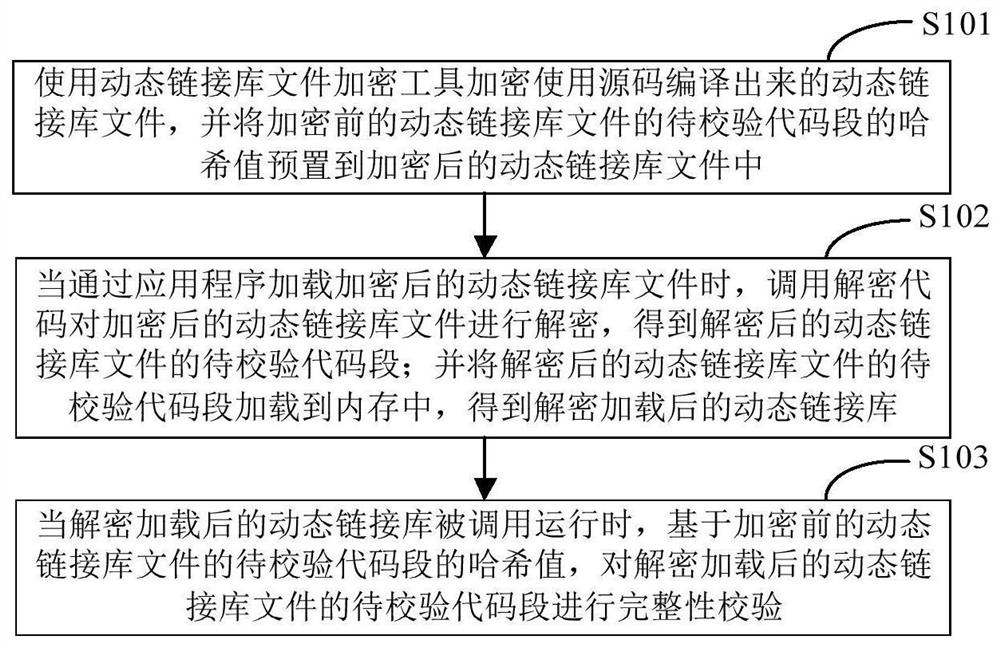
[0019] figure 1 It is a schematic flowchart of the first code verification method provided by the embodiment of the present invention. like figure 1 As shown, the code verification method may include the following steps:
[0020] Step 101, use the dynamic link library file encryption tool to encrypt the dynamic link library file compiled from the source code, and preset the hash value of the code segment to be verified in the dynamic link library file before encryption to the encrypted dynamic link library file middle.
[0021] In this step, the electronic device can use the dynamic link library file encryption tool to encrypt the dynamic link library file compiled from the source code, and preset the hash value of the code segment to be verified in the dynamic link library file before encryption to the encrypted in the dynamic link library file. Specifically, the dynamic link library file compiled using the source code includes: a file header and file content; wherein, th...
Embodiment 2
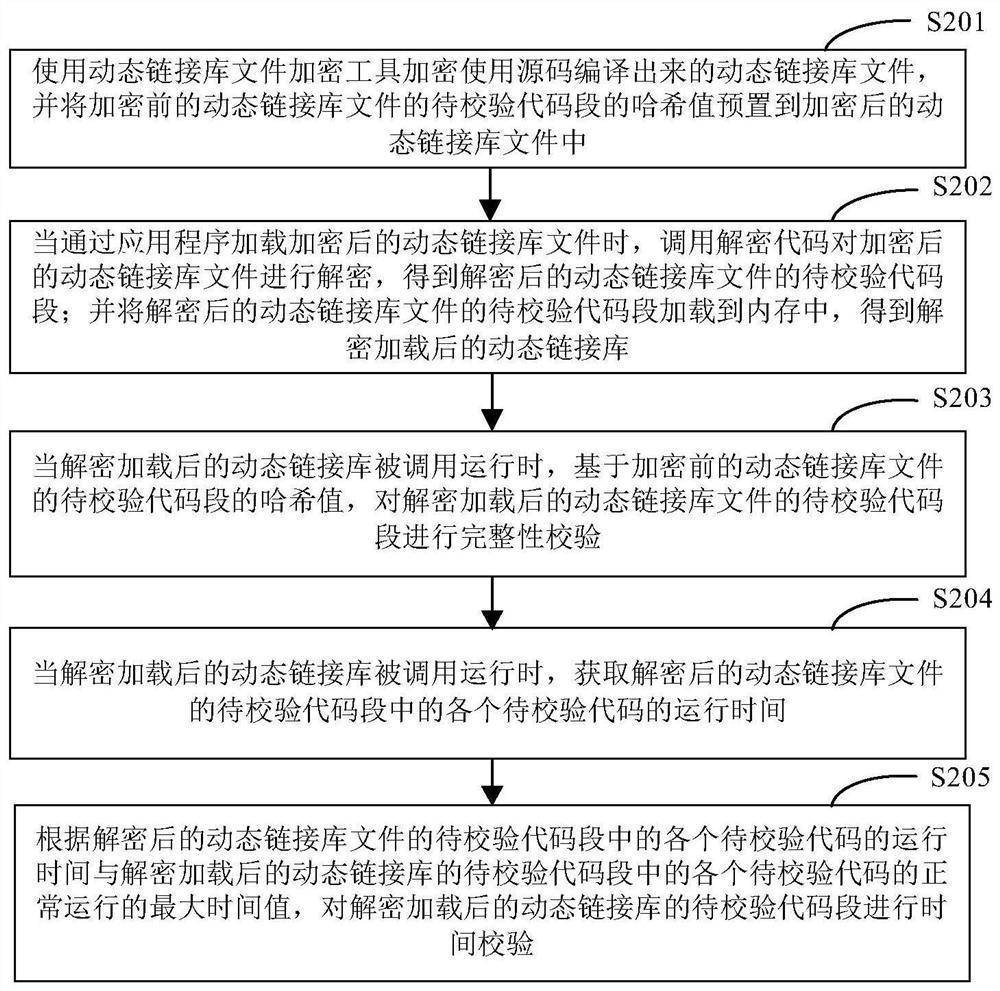
[0030] figure 2 It is a second schematic flowchart of the code verification method provided by the embodiment of the present invention. like figure 2 As shown, the code verification method may include the following steps:
[0031] Step 201, use the dynamic link library file encryption tool to encrypt the dynamic link library file compiled from the source code, and preset the hash value of the code segment to be verified in the dynamic link library file before encryption to the encrypted dynamic link library file middle.
[0032] Step 202, when the encrypted dynamic link library file is loaded through the application program, the decryption code is called to decrypt the encrypted dynamic link library file, and the code segment to be verified of the decrypted dynamic link library file is obtained; and the decrypted The code segment to be verified of the dynamic link library file is loaded into the memory, and the decrypted and loaded dynamic link library is obtained.
[00...
Embodiment 3
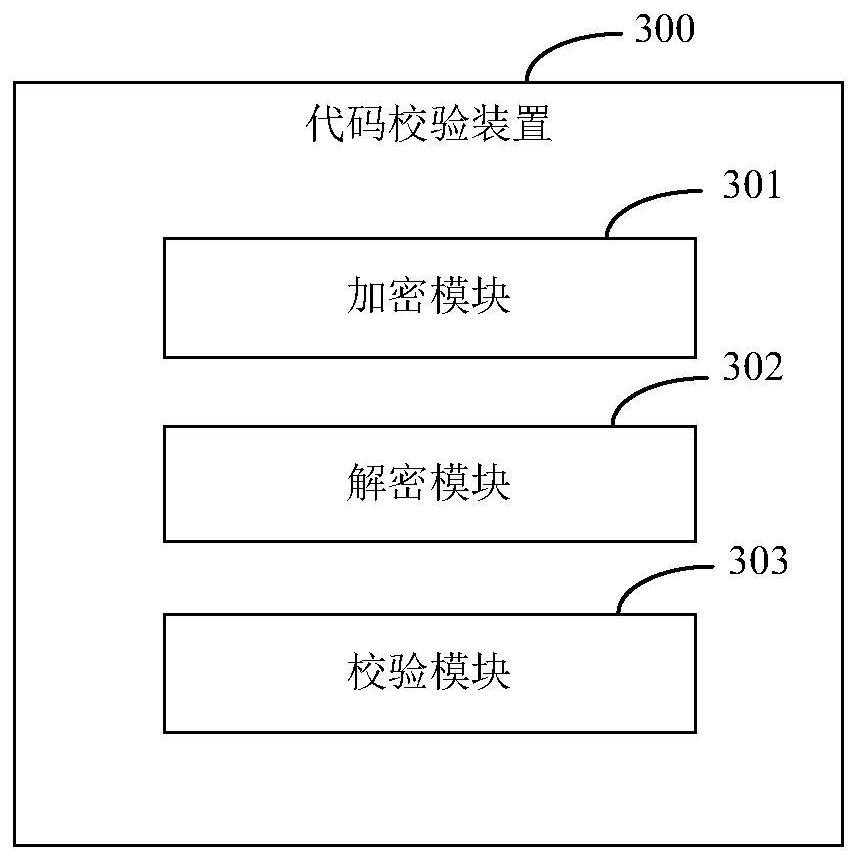
[0042] image 3 It is a schematic structural diagram of a code verification device provided by Embodiment 3 of the present invention. like image 3 As shown, the code verification device includes: an encryption module 301, a decryption module 302 and a verification module 303; wherein,
[0043] The encryption module 301 is configured to use the dynamic link library file encryption tool to encrypt the dynamic link library file compiled from the source code, and preset the hash value of the code segment to be verified in the dynamic link library file before encryption to after encryption In the dynamic link library file;
[0044] The decryption module 302 is configured to call a decryption code to decrypt the encrypted dynamic link library file when the encrypted dynamic link library file is loaded by an application program, so as to obtain the waiting list of the decrypted dynamic link library file. Verifying the code segment; and loading the code segment to be verified of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com